The Hidden Art of Steganography - Department of Computer Science
advertisement

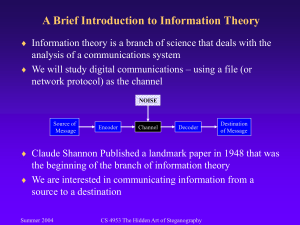
The Hidden Art of Steganography What is hiding in your picture? Summer 2005 CS 4953 The Hidden Art of Steganography The Hidden Art of Steganography What is hiding in your picture? Summer 2005 CS 4953 The Hidden Art of Steganography The Hidden Art of Steganography What is hiding in your picture? Summer 2005 CS 4953 The Hidden Art of Steganography Information Hiding Information Hiding is a branch of computer science that deals with concealing the existence of a message It is related to cryptography whose intent is to render messages unreadable except by the intended recipients It employs technologies from numerous science disciplines: – – – – – Digital Signal Processing (Images, Audio, Video) Cryptography Information Theory\Coding Theory Data Compression Human Visual/Auditory perception There are four primary sub-disciplines of Information Hiding – – – – Steganography Watermarking Covert Channels Anonymity Summer 2005 CS 4953 The Hidden Art of Steganography Information Hiding F. A. P. Petitcolas, R. J. Anderson, M. G. Kuhn, “Information Hiding – A Survey”, Proceedings of the IEEE, special issue on protection of multimedia content, 87(7):1062-1078, July 1999 Summer 2005 CS 4953 The Hidden Art of Steganography Fields Applied to Information Hiding Information Theory/Coding Theory Digital Signal Processing – Discrete Fourier Transform/Discrete Cosine Transform – Image/Audio/Video Processing Data Compression Cryptographic Principles Discrete Math Cryptographic Hashing Data Networks The Human Visual System/Human Auditory System – Capabilities and limitations Summer 2005 CS 4953 The Hidden Art of Steganography Basic Terminology The data to be hidden: – – – – Plaintext (from cryptography) Secret message Stego-message Embedded data The data which will have a stego-message embedded in it: – – – – Covertext Cover-Object Cover-Image\Cover-Audio\Cover-Video Target file Summer 2005 CS 4953 The Hidden Art of Steganography Basic Terminology The key used to make the stego-message secure – Stego-Key – Secret Key – Key The file with the steganography-message embedded – Stegotext (ciphertext in cryptography) – Stego-Object – Stego-Image\Stego-Audio\Stego-Video Summer 2005 CS 4953 The Hidden Art of Steganography Basic Terminology Alice and Bob – Classical names given to the parties wishing to communicate Sometimes, you may have a Carol and a Dave Eve, an adversary, can listen to but not modify or forge a message – (think passive eavesdropping) Wendy the Warden, another adversary, can monitor, modify, or forge a message – A passive warden simply listens (like Eve) – An active warden may modify a message – A malicious warden may forge a fake message Summer 2005 CS 4953 The Hidden Art of Steganography History of Steganography The concept of message hiding is not new – it’s been around for centuries – A Greek shaved the head of a slave, wrote a message, then waited for the hair to grow back before sending the slave to his destination – Steganography (in the form of invisible ink) was used by Washington in the Revolutionary War – Prior to the Civil War, quilts were sewn with special patterns to tell escaping slaves which direction to go and what to do – During WWI there was a cable the read, “Father is dead.” Suspecting a hidden meaning, the censor changed it to “Father is deceased” which caused the reply, “Is Father dead or deceased?” – During WWII chess by mail was banned, crossword puzzles examined, stamps were removed and replaced by ones of equal value – In the 1980’s, some of Margaret Thatcher’s cabinet documents were leaked to the press. She ordered that the word processors being used by government employees, encode their identity in the word spacing of the documents Summer 2005 CS 4953 The Hidden Art of Steganography Steganography Steganography literally means “covered writing” – A stegosaurus has a covered back Steganography’s primary goal is to hide data within some other data such that the hidden data cannot be detected even if it is being sought Secondary goals: – prevent extraction from the cover file without destroying the cover – prevent destruction of the stego-message without destroying the cover Most frequently, steganography is applied to images, but many other data or file types are possible – – – – Audio Video Text Executable programs Summer 2005 CS 4953 The Hidden Art of Steganography Watermarking Watermarking is very similar to steganography in that one of its goals is to not be detected However, it’s primary goal is to not be able to be extracted or destroyed (at least not without destroying the cover too) Typically, watermarking is designed to protect intellectual property rights for images, sounds, and video – If it’s easily removed or destroyed, those rights cannot be protected Even if it’s not detectable, an adversary could suspect that a work (of art) could have a watermark and so take steps to destroy it – There is a popular program called StirMark which does just that For some applications watermarks may be visible May be used to fingerprint a particular file and detect changes – Make it tamper proof Used to prove ownership So far, to my knowledge, no one has invented a watermarking system that is good enough to hold up in court Summer 2005 CS 4953 The Hidden Art of Steganography Covert Channels Covert channels are communication paths that were neither designed nor intended to transfer information For example, the telephone was designed to allow voice communication – information could be conveyed by letting it ring a certain number of times – The time differences between successive phone calls could be used – You could use a mobile phone and call from different locations – the street names convey the message Unused bits in the TCP/IP protocol headers can be used to carry information Hiding data in an image, then sending that image to someone else could also be considered a covert channel Summer 2005 CS 4953 The Hidden Art of Steganography Anonymity Anonymity is about concealing the sender and receiver of messages This is the least studied sub-discipline of information hiding Summer 2005 CS 4953 The Hidden Art of Steganography Steganalysis Steganalysis is the detection of data that has been hidden It is a cat and mouse game – as one group of researchers come up with better ways to hide stuff, another group figures out how to detect it or perhaps just destroy it In the summer course last year, one student thought he had a hiding system that was undetectable – His lab partner wrote a statistical analysis program that exposed the hidden message – The first student modified his program to defeat the attack – His lab partner modified his analyzer and still found the message Summer 2005 CS 4953 The Hidden Art of Steganography Wisdom from Cryptography One of the main principals of cryptography applies to steganography as well It is a simple concept, yet many repeatedly ignore or dismiss it The premise from which to measure a secure steganographic system is to assume that the opponent knows the system being employed, yet still cannot find any evidence of a hidden message – Kerchoff’s Principle: the system should not depend on secrecy and should be able to fall into enemy hands without disadvantage – The ONLY way to find any evidence of a message is with the key – Many systems have relied on the “Security by Obscurity” premise and many have failed – those that have not have been lucky • CSS for DVD, RIAA digital watermarking, Adobe e-books, SDMI Summer 2005 CS 4953 The Hidden Art of Steganography Wisdom from Cryptography Often designers think (erroneously) that “They’ll never think of this.” – yet, the designer did??? – A criminal would never think to look in a flower pot for the house key • Nooooo! Even in military situations, equipment is captured or bought If the security depends on the secrecy of the algorithm, once it is compromised, the entire system is compromised - forever If a key is compromised, only that message is compromised A secure system will not rely on keeping the algorithm secret, just the key The same premise holds true for a steganography system – Do NOT depend on the secrecy of your algorithm for security! Summer 2005 CS 4953 The Hidden Art of Steganography Applications of Information Hiding Covert military communications Covert police communications – Criminals have learned that police are nearby when they hear encrypted communications, so they abate their activity for the moment – A steganographic system would prevent this detection Digital Rights Management – protecting intellectual property such as images, music, electronic books, etc. Embedding textual data in medical images would better ensure that the picture belongs to a particular patient – This technique could apply to personal pictures, sounds, and movies Tamper proofing – ensuring a data file has not been changed Communicating in an oppressive country w/o free speech Summer 2005 CS 4953 The Hidden Art of Steganography Nefarious Applications of Information Hiding You won’t find these applications in the book – – – – – money laundering drug running child pornography spying (good or bad depending upon which side you’re on!) terrorism Unfortunately, these uses are also possible The technology itself isn’t bad, but like many things, it can be (and is) abused Since there are nefarious uses, law enforcement and the military is also interested in understanding hiding techniques and detecting hidden data There are some projects right here at UTSA that have done research for the Air Force Summer 2005 CS 4953 The Hidden Art of Steganography Goals of Information Hiding - Security It is secure if it cannot be removed even with full knowledge of the embedding algorithm without knowledge of the secret key Can it be detected by human perception? (Invisibility) – See distortion/noise in an image – Hear distortion/noise in speech or music? Can it be detected by statistical analysis? (Undetectability) Does it leave easily detectable signatures? Levels of Failure: – Detection - Proof of existence of message – Extraction – removing without destroying the cover – Destruction – destroying the message without destroying the cover Summer 2005 CS 4953 The Hidden Art of Steganography Goals of Information Hiding - Capacity How much data can a cover image hold? – There is a physical limit (unless the cover file size is increased) – There is a limit as to when the data will be noticeable Typically, as more capacity is used, the lower the security and robustness Summer 2005 CS 4953 The Hidden Art of Steganography Goals of Information Hiding – Robustness How well does the data maintain integrity in the face of modifications? The modifications we are concerned with are quite common – Images: blurring, sharpening, scaling, cropping, contrast, gamma, brightness, rotation, skewing, recoloring, printing/copying/scanning, etc. – Audio: filtering (think bass/treble), volume adjustment, stereo to mono, etc. – Video: any image/audio modification, add/delete frames, temporal adjustments, frame swapping, frame averaging – Also: lossy compression, A/D and D/A conversion, and sophisticated attacks Robustness is achieved through redundant encoding of the message which reduces the capacity Summer 2005 CS 4953 The Hidden Art of Steganography Steganographic Hiding Techniques Substitution systems – Put message in redundant or noisy parts of cover Transform domain techniques – Embed information in the transform space Spread spectrum techniques – Message is spread across frequency spectrum of cover Statistical methods – Alter some statistical properties of the cover Distortion techniques – Store message by distorting the cover slightly and detecting the change from the original Cover generation methods – Encode information in the way a cover is created Summer 2005 CS 4953 The Hidden Art of Steganography Steganographic Techniques - Substitution Replace information in the cover with the stego-message The most common method is to replace the Least Significant Bit (LSB) Each pixel in the mandrill image is composed of 8 bits and so have a range of values from zero (black) to 255 (white) – The “sports enthusiast” was hidden by replacing the 4 least significant bits – You might be tempted to think, “That’s half the information!” – No, it is 1/16 the information – not noticeable to us Other images with more solid backgrounds would NOT provide the same level of imperceptibility – To maximize capacity while maintaining imperceptibility, you need to analyze the cover image Summer 2005 CS 4953 The Hidden Art of Steganography Steganographic Techniques - Substitution You can see some of the distortion caused by the mandrill image (Again, 4 bits were used) Summer 2005 CS 4953 The Hidden Art of Steganography Steganographic Techniques - Substitution Using a solid white or black cover is NOT very good Summer 2005 CS 4953 The Hidden Art of Steganography Steganographic Techniques - Substitution Here is a progression of hiding in the mandrill image Summer 2005 CS 4953 The Hidden Art of Steganography Questions and/or Comments Summer 2005 CS 4953 The Hidden Art of Steganography