Presentation - robbins.UOPX.CMGT400.LECTURE.WEEK04
advertisement

CMGT/400
Intro to Information Assurance & Security
Philip Robbins – May 29, 2013 (Week 4)
University of Phoenix Mililani Campus
Agenda: Week 4
•
•
•
•
Individual Assignment #2 Due
Grade Quiz #3
Class Videos
Week 4
- Cryptography
Week 1 & 2 Review
•
•
•
•
•
•
•
•
Why is information important?
What are the Information Security Services?
What is Information Assurance?
What is a Denial-of-Service attack?
What is SSL?
How is JavaScript a security risk?
Name a dangerous programming error?
Why is port 20/21 considered a security risk?
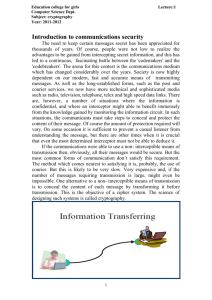
Cryptography
• Cryptology comes from “Crypto”
- Meaning: To Hide
Definition: The science of hiding communications.
• Why?
- Protect email, PII, transactions & data.
• Cryptographic systems use
- Codes: “secret keys”
- Ciphers: hiding the true meaning of a message
Cryptography
• Confidentiality
- The process of protecting plaintext messages
from monitoring or eavesdropping.
- Cryptography v.s. Encryption??
Cryptography
• Basic Elements of Cryptography
- Algorithm
- Key
- Data
Cryptography
• Basic Elements: Algorithm
- Describes the process (instruction set) involved
in producing a desired output.
- In the case of Cryptography what is our desired
output?
Encryption / ciphertext / Confidentiality
- Does more Complexity = (mean) more Security?
Cryptography
• Non-reputation
- Sender can’t deny sending a message.
• Authentication
- Associated with confirming a user’s identity
- Also associated with message encryption
Cryptography
• Authentication
Data Origin: Identifying the transmitting node in a
communications channel.
Digital Signatures
- Uses Hash Function & Encryption together
Digital Certificates
- Ensure identity of remote computer
- Who are you sending your information to?
Cryptography
• Substitution Algorithm
- Caesar’s Cipher
- Rotate (shift) alphabet
Key?
Key Length?
- Easy to decipher (common words, i.e. “the”)
Cryptography
• Transposition Algorithm
- Encryption by changing position of plaintext.
- Rail Fence Cipher
DATA: 'WE ARE DISCOVERED. FLEE AT ONCE‘
KEY: 3 ‘Rails’ (rows)
CIPHERTEXT:
Cryptography
• Running Key Cipher
- Clever use of components in the world
- Example: Newspaper Page #, Word #
• Concealment Cipher
- A message (hidden) within a message
- Example: Key = Every 3rd word.
- Not actually encrypted – just hidden.
• Stenography
- Security through obscurity.
- Not recommended as encryption substitute.
Cryptography
• Vernam Cipher
- Gilbert Vernam
- 1917
- Uses a basic Boolean XOR Function!!
Logic Gate Symbol
Truth Table
Cryptography
• Stream Cipher: Dividing the message into bits for
processing (Encrypting data one bit at a time).
Cryptography
• Block Cipher: Dividing the message into blocks
for processing.
1 Block
Cryptography
• Stream v.s. Block Cipher
Cryptography
• Key & Algorithm Relationship
- Algorithm’s are static mathematic functions.
- Algorithm does not change; the key does.
- The purpose of a key is to add randomization.
- The key is a group of instructions for the
algorithms.
- Larger key space means better security:
128 bit = 2^128 = 3.4 x 10^38 keys
- Processing power can brute force keys < 128 bit
Cryptography
• Key & Algorithm Relationship
Cryptography
• Symmetric Key Algorithm
- The same key is used to encipher plaintext to
produce cipher text
Plaintext ⊕ Key = Ciphertext
*and to*
- decipher cipher text to yield the original plaintext
Ciphertext ⊕ Key = Plaintext
Cryptography
• Symmetric Key Algorithm
- How is confidentiality maintained?
Cryptography
• Symmetric Key Algorithm
- Advantages
Fast
Hard to break if large key is used.
- Disadvantages
Only provides for confidentiality
Key Management
Distribution
Cryptography
• Symmetric Key Algorithm
- Disadvantages
Key Management
Assume you wanted to communicate with 10 other
people while ensuring confidentiality.
How many keys would you need?
# of communication
channels
= n(n-1)/2
Cryptography
• Symmetric Key Algorithm
- Disadvantages (Most serious deficiency)
Distribution
How would we transfer symmetric keys securely?
What if someone is monitoring comms?
If sent in cleartext someone can intercept.
Cryptography
• Asymmetric Encryption
- One key is required to encrypt.
Plaintext ⊕ Public Key = Ciphertext
*and*
- another key is required to decrypt.
Ciphertext ⊕ Private Key = Plaintext
• Key Pair {Public Key, Private Key}
Cryptography
• Asymmetric Key Algorithm
given to anyone
kept secret
Cryptography
• Asymmetric Encryption
- SENDER
Messages are encrypted with the public key.
The public key can be given to anyone.
- RECIEVER
Only the matching private key will decrypt it.
The private key is kept secret.
Cryptography
• Asymmetric Encryption
- It should not be possible to get a key pair’s
private key from the public key.
- Anyone with a private key can generate its public
pair.
- This is done using one-way functions.
Cryptography
• Asymmetric Key Algorithm
- Advantages
Key Management
Distribution
- Disadvantages
Can’t encrypt large amounts of data.
Cryptography
• Asymmetric Key Algorithm
- Advantages
Solves Key Management Problem!!
Assume you wanted to communicate with 10 other
people while ensuring confidentiality.
How many keys would you need now?
Cryptography
• Hashing
- Taking variable amounts
of data and compressing it
into a fixed length value,
producing unique outputs.
- A different MD5 hash would indicate
the file has been altered or corrupted.
- Message digest helps to verify integrity.
- Integrity and/or nonrepudiation
Cryptography
• Digital Signatures
- Message goes through a Hashing algorithm.
- The message digest is then encrypted with the
sender’s private key. (important: MD is encrypted
with private key; not the actual message itself)
- The receiver validates the digital signature by
decrypting it with the sender’s public key.
- Provides integrity, authenticity, and non-repudiation.
If I use my private key to encrypt something then it
proves it came from me.
Cryptography
• Digital Signatures
Cryptography
• Cryptographic Algorithms
Cryptography
• Strong Algorithms (Characteristics) Contain:
- Confusion
Complexity
Reverse Engineering process is difficult
Changing a char in plaintext doesn’t create
predictable ciphertext.
- Diffusion
Changes in plaintext creates large change in
ciphertext; avoiding discovery of key.
Cryptography
• Kerckoff’s Principal:
“…the security of a cipher system should depend
on the key and not the algorithm…”
Why would it be advantageous to release the
cipher algorithm to the public?
Break
• Let’s take a break…
Review Questions
Question #1
What is an Algorithm?
Question #1
What is an Algorithm?
Describes the process (instruction set) involved in
producing a desired output.
Question #2
What is a Cryptographic Key?
Question #2
What is a Cryptographic Key?
Piece of information that controls how the
cryptographic algorithm functions (works).
Question #3a
What is Encryption?
Question #3a
What is Encryption?
Transforming data into an unreadable format.
Question #3b
What is Cryptography?
Question #3b
What is Cryptography?
The science of hiding communications.
Question #4
What is Cryptanalysis?
Question #4
What is Cryptanalysis?
Breaking cryptography; act of obtaining plain text
from cipher text.
Question #5
Which of the following best describes obtaining
plain text from cipher text without a key?
A.
B.
C.
D.
Frequency Analysis
Cryptanalysis
Decryption
Cracking
Question #5
Which of the following best describes obtaining
plain text from cipher text without a key?
A.
B.
C.
D.
Frequency Analysis
Cryptanalysis
Decryption
Cracking
Question #6
Which of the following is a disadvantage of
symmetric key encryption?
A.
B.
C.
D.
Key Size
Speed
Key Management
Key Strength
Question #6
Which of the following is a disadvantage of
symmetric key encryption?
A.
B.
C.
D.
Key Size
Speed
Key Management
Key Strength
Question #7
Which of the following attacks requires an
attacker to obtain several encrypted messages
that have been encrypted using the same
encryption algorithm?
A.
B.
C.
D.
Known plain text attack
Cipher text attack
Clear text attack
Replay attack
Question #7
Which of the following attacks requires an
attacker to obtain several encrypted messages
that have been encrypted using the same
encryption algorithm?
A.
B.
C.
D.
Known plain text attack
Cipher text attack
Clear text attack
Replay attack
Question #8
Why does a digital signature contain a message
digest?
A.
B.
C.
D.
To detect any alteration of the message
To indicate the encryption algorithm
To confirm the identity of the sender
To enable transmission in a digital format
Question #8
Why does a digital signature contain a message
digest?
A.
B.
C.
D.
To detect any alteration of the message
To indicate the encryption algorithm
To confirm the identity of the sender
To enable transmission in a digital format
Question #8
Which is NOT a property of a one-way hash
function?
A. It converts a message of a fixed length into a
message digest of arbitrary length
B. It is computationally infeasible to construct two
messages with the same digest
C. It converts a message of arbitrary length into a
message of a fixed length
D. Given a digest value, it is computationally
infeasible to find the corresponding message
Question #8
Which is NOT a property of a one-way hash
function?
A. It converts a message of a fixed length into a
message digest of arbitrary length
B. It is computationally infeasible to construct two
messages with the same digest
C. It converts a message of arbitrary length into a
message of a fixed length
D. Given a digest value, it is computationally
infeasible to find the corresponding message
Question #9
What are the three most important functions that
digital signatures perform?
A.
B.
C.
D.
Integrity, Confidentiality, and Authorization
Integrity, Authentication, and Nonrepudiation
Authorization, Authentication, and Nonrepudiation
Authorization, Detection, and Accountability
Question #9
What are the three most important functions that
digital signatures perform?
A.
B.
C.
D.
Integrity, Confidentiality, and Authorization
Integrity, Authentication, and Nonrepudiation
Authorization, Authentication, and Nonrepudiation
Authorization, Detection, and Accountability
Question #10 (last one)
What is the result of a hash algorithm being
applied to a message?
A.
B.
C.
D.
A digital signature
A ciphertext
A message digest
A plaintext
Question #10 (last one)
What is the result of a hash algorithm being
applied to a message?
A.
B.
C.
D.
A digital signature
A ciphertext
A message digest
A plaintext
Break
• Let’s take a break…
Quiz: Week 3
• 10-15 minutes
IDV Assignment due Week #4
• Paper No. 3