Small Commercial Sales Guide

TLS Webinar
1
Safeguarding Our Email
Via TLS
Presented by:
Jim Rogers, Director of Distribution Technology, The Hartford
Tim Woodcock, President, Courtesy Computers
Jeff Yates, Executive Director, Agents Council for Technology
Agenda
2
Submit questions via the Question & Answer Log
First 30 Minutes:
eMail Usage
Security - Why you should care
Benefits
Resources
Q&A –
Second 30 Minutes:
TLS Configuration of MS Exchange 2003 & 2007
Q&A
Background
3
Email has become a major component in every day agency/carrier business interactions.
Mail sent over the Internet is typically unprotected
The need to protect email continues to grow
The use of, and reliance on, email within core business workflows will continue to increase
4
Why Protect e-Mail?
e-Mail often contains sensitive customer information
Required by business contract
Is easily accessible to prying eyes on the Internet
Mandated by regulation
Existing Regulations and Standards
Gramm-Leach-Bliley Act (GLBA) Standards for Safeguarding Customer Info.
non-public personal information (NPPI) in paper, electronic, or other form
NPII: personally identifiable information provided by a consumer or resulting from a transaction for a consumer
written information security program to address internal/external risks
physical, technical and administrative safeguards
oversee service providers
Security Breach Notification Laws (Various states)
first/last name and SSN/drivers license/state ID/financial account + password
when not encrypted
must notify any resident of the state of a breach without unreasonable delay
Payment Card Industry Data Security Standards (PCI-DSS)
cardholder data
certification of compliance with PCI-DSS depending upon level of merchant
firewall, encryption in storage/transmission, antivirus, etc.
assign individual user IDs
5
Recent Regulatory Developments
Nevada 597.970
“Restrictions on transfer of personal information through electronic transmission”
Massachusetts 201 CMR 17.00
“Standards for The Protection of Personal Information of Residents of the Commonwealth”
California Department of Motor Vehicles
“On-Line DMV Special Permit Program”
6
Ohio Department of Insurance Proposed Rule 3901-1-66
“Breach of Security Reporting Requirements”
TLS: Transport Layer Security
7
Provides secure e-Mail communications across the Internet through a standardized, secure, and non-proprietary mechanism
Eliminates the “drawbacks” that plague the commonly used tools and services
Is built-in to most modern e-Mail systems and just needs to be “turned on” by your technology professional
How Does TLS Work ?
8
At transmission time, TLS creates an encrypted communication session between email servers
The eMail is then sent through a protected “tunnel”
The servers de-crypt the message and send it along to the client
Encrypted
Agency
Partner
Carrier
Client Client
9
Transport Layer Security: TLS
Encrypted Message
“$erm840 kkfd8820& l1k6ss”
“My ssn is: 999 65 9999” Safe/Secure
Standard Protocol
Available on most email systems
Transparent to end-users
Eliminates the need for hosted services
Negligible cost
“My ssn is: 999 65 9999”
Benefits of TLS
Provides the confidentiality of emails across the Internet
Requires no changes to the client
Is a standards-based protocol that is implemented on most e-Mail gateways and appliances
It’s free, no additional licensing is needed. Security certificate is required.
10
How Do I Get TLS ?
TLS is a standards-based protocol enabled on most serverbased email systems
Talk with your system support staff or e-Mail service provider
Most agencies that have an up-to-date in-house mail server are TLS capable. Agencies with a hosted Microsoft
Exchange server are TLS capable. Those with hosted email using hotmail, gmail, and yahoo are not currently TLS capable
11
Detecting TLS
How do you determine if TLS is active….
Talk to the email server administrator
Some email contains a tag line if sent via TLS…. at the bottom of the email
More on this in our technical discussion
12
Carriers supporting TLS
13
Allied/Nationwide
Chubb
Cincinnati
CNA
EMC
Harleysville
The Hartford,
Liberty Agency Markets
MetLife – MetLife Auto & Home
OneBeacon
Progressive
Summit Holdings
Travelers
Westfield
W.R. Berkley Companies
Note: for updated list of carriers supporting TLS see “Agency Security” Section of www.independentagent.com/act or ask you carrier
Additional Considerations
14
Important to have your technical support implement TLS
Your technical support can tell you which of your carriers and clients are enabled for TLS
If using an external spam/anti-virus filter, you need to make sure it is enabled for TLS
Many hosted email solutions are not enabled for TLS
(e.g., hotmail, gmail, yahoo)
You also need to make sure that the connections between your email server and your remote computers and mobile devices are encrypted
Use your real-time tools wherever possible to transmit client personal information because it is encrypted
If TLS or Real Time not available, send application information using a password protected pdf or zip file
15
Feedback - TLS Article
16
Feedback - FAQs
17
TLS Links
ACT Web site for TLS Article,FAQs, & TLS enabled carriers http://www.iiaba.net/na/16_AgentsCouncilForTechnology/NA2
0070710103244?ContentPreference=NA&ActiveState=AZ&
ContentLevel1=ACT&ContentLevel2=&ContentLevel3=&Ac tiveTab=NA&StartRow=0
Technical Links http://msexchangeteam.com/archive/2006/10/04/429090.aspx
http://technet.microsoft.com/enus/library/bb430753(EXCHG.80).aspx
18
Questions so far ???
19
How to Configure TLS
• Will cover how to procure SSL Certificates
• Representative purposes only and steps here may not be suitable for all environments
• Will cover Exchange 2003 and 2007
• If you are on a different platform, please consult your technical support
Several Sources for Security Certificates certificate authority ( CA )
-an entity that issues digital certificates
Verisign http://www.verisign.com
Network Solutions http://www.networksolutions.com
GoDaddy http://www.godaddy.com
Comodo http://www.comodo.com/
Digi-Sign http://www.digi-sign.com
HOW TO: Use Certificates with Virtual Servers in Exchange Server http://support.microsoft.com/kb/319574/
20
21
WindowsITPro MS Exchange Server Poll
Difference between Exchange 2003 & 2007
22
Exchange 2003
• requires a valid X.509 server certificate
(suitable for TLS usage)
• DOES NOT support ‘Opportunistic TLS’
• Requires to manually configure TLS (minimum 6 steps)
• Difficult to monitor TLS transmit-receive success/failures
Exchange 2007
• requires a valid X.509 server certificate
(suitable for TLS usage)
• ‘Opportunistic TLS is automatically enabled
(by default)
• Easy to monitor TLS transmit-receive success/failures
• Greater Message Control with Robust ‘Transport Rules’ Features
• Block, Bounce, Copy, append, Send to Archive, Quarantine
TLS Enabling Process with Exchange 2003
Initial 7 Step Process for ‘Server to Server’ TLS
1. Configure an additional IP Address
2. Configure the Default SMTP Virtual Server (VS)
3. Create & Configure the Secure SMTP VS
4. Configure Secure SMTP VS to use certificate
5. Set TLS encryption levels for the Secure SMTP VS
6. Create & Configure the Secure SMTP Connector
7. Notify sending party (carrier) of second SMTP VS IP address
23
Note: Repeat steps 6 & 7 for each remote domain server you wish to communicate with, utilizing TLS
24
Configuring an Additional IP Address
25
Configuring the Default SMTP VS
26
Creating and Configuring the Secure SMTP VS
27
Creating and Configuring the Secure SMTP VS
28
Creating and Configuring the Secure SMTP VS
29
Configure Secure SMTP VS to use a certificate
30
Configure Secure SMTP VS to use a certificate
31
Configure Secure SMTP VS to use a certificate
32
Set TLS encryption levels for the
Secure SMTP Virtual Server
33
Set TLS encryption levels for the
Secure SMTP Virtual Server
34
Set TLS encryption levels for the
Secure SMTP Virtual Server
Creating and Configuring the
Secure SMTP Connector
35
Creating and Configuring the
Secure SMTP Connector
36
Creating and Configuring the
Secure SMTP Connector
37
Creating and Configuring the
Secure SMTP Connector
38
39
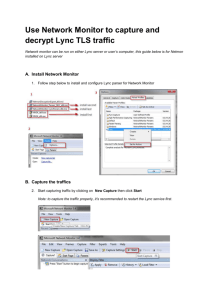
Verifying TLS is ‘Active’ with MS Office 2007
40
Questions
Follow Up
• Follow up email with our email addresses
• PowerPoint & Recording of presentation posted on “Agency Security/Customer Privacy” link at www.independentagent.com/act
• See more detailed info about security & privacy laws and regulations in the Appendix section of the posted PowerPoint
• Next scheduled TLS Webinar—June 23, 2009,
1:30-2:30 PM eastern time
Appendices
Details on State Security Regulations
Nevada 597.970
Who it applies to: “a business in this state”
What information it applies to: first/last name and SSN/drivers license/state ID/financial account + password when not encrypted
Examples: tax ID of small businesses, commercial fleet drivers’ license numbers
What is required: Encryption of electronic transmission, except facsimiles
What this means: Organizations doing business in or with other organizations in Nevada must support encryption if sharing data through e-mail, web sites, batch file transfers (FTP), Real Time, file uploads, wireless, web conferencing, etc.
Effective Date: October 1, 2008
Security controls to consider : email……..TLS*, proprietary solutions web site, Real Time…SSL batch file transfers.…PGP, SFTP, VPN fileuploads….PGP, SFTP, FTPS, other wireless….802.11i, LEAP, WPA2 enterprise web conferencing….SSL
For more information see http://na.iiaa.org/ACT/downloads/ACT_TLS_FAQ.doc
Massachusetts
201 CMR 17.00
Who it applies to : all “entities” that own, license, store or maintain personal information about a resident of
Massachusetts
What information it applies to: first/last name + SSN/drivers license/state ID/financial account - password when not encrypted of any resident of the state
Examples:
Insureds, claimants, employees Applications for insurance, claims, premium payments, claim payments, personnel records, etc.
What is required:
• Designating someone to maintain a comprehensive written security program
• Assessing internal and external risks to electronic and paper records
• Imposing disciplinary measures for violations of the security program
• Other common elements of a security program: monitoring, updating safeguards, annual review of program, etc.
Massachusetts
201 CMR 17.00
New items of note:
• Security of paper and electronic records taken off site
• Assigning unique user IDs and securing passwords
• Terminating logon accounts and passwords of terminated employees
• Contractually requiring vendors to comply with these requirements
• Limiting time this information is retained (records management)
• Documenting breaches and conducting post-incident reviews of incidents
• Encryption of portable devices required (laptops, PDA’s, phones, Blackberries, CD,
DVD, USB drives)
• Encryption of transmitted information where feasible
• Reasonably update firewalls and patching of systems connected to the Internet
Effective Date: January 1, 2010
Massachusetts
201 CMR 17.00
What this means for our industry / security controls:
• Agents, carriers and vendors must have a formal security program including specific physical, technical and administrative security measures, including third party oversight and management of portable devices
• Increased need for carriers and vendors to modify their systems, web sites, and Real Time interfaces to support industry standards for user administration and password management in agencies
• Implementation of TLS where technically feasible
• Organizations must have security staff or consultants available for administration of firewalls and patching of servers and workstations
For more information see : http://www.mass.gov/Eoca/docs/idtheft/201CMR17amended.pdf
California
DMV
Who it applies to:
• Entities that provide access to entities that are authorized DMV “requestors”
• Entities that access DMV information on behalf of authorized “requestors”
What information it applies to:
• Personnel information provided by the DMV
• Examples: MVR (CLUE, scoring, resident addresses)
What is required:
• Various requirements depending upon the circumstances. For example….
Those organizations with direct access to DMV systems and information must:
• lockdown servers
• user accounts must lock out after 5 unsuccessful logon attempts
• users must select their own passwords and expire within 90 days
• potential security incidents must be reported within 1 business day to the DMV
Those permitting direct electronic access to information must identify the account
ID’s being used for that access so that it can be programmed into the system
California
DMV
Individuals with access to DMV information must sign a security agreement form
(1128), even if that individual is in another organization. Agreement requires
• No password sharing
• Storing passwords in a secure place
• Any administrator or other with incidental access must sign agreement as well
What this means for our industry / security controls:
• Carriers/vendors using DMV information to provide interactive rating information to agencies, must store agency account IDs so that these IDs can be passed through their systems.
• Carriers/vendors which access this information for agencies or pass this information to agencies, must retain specific logs of all such access for 2 - 5 years
• Carriers/vendors which access this information for agencies or pass this information to agencies must provide a copy of the agency contract upon request.
Effective Date : Various (all currently in effect)
For more information see http://www.dmv.ca.gov/forms/forms_cra.htm
Ohio Dept of Insurance Proposed Rule 3901-1-66
Who it would apply to :
Regulated insurance entities including insurance agents, a property and casualty insurance company… or any other entity that requires a license… from the Superintendant of Insurance to conduct business within Ohio
What information it applies to: first/last name and SSN/drivers license/state ID/financial account when not encrypted or redacted in the file of a resident of
Ohio
Examples: Application for insurance, claims
What is required: Entity must report a security breach within 15 calendar days of discovery. Additional details may be required after initial report received.
Ohio Dept of Insurance Proposed Rule 3901-1-66
What this means for our industry /security controls:
• Modify current incident response procedures to include reporting requirements beyond those already in effect in the state
• Unclear as to who is responsible to report a breach of a carrier site at an agency or how such duplicate reports would be coordinated/reconciled
Effective Date: Rule pending