Mobile Device Detection & Theft Prevention System
advertisement

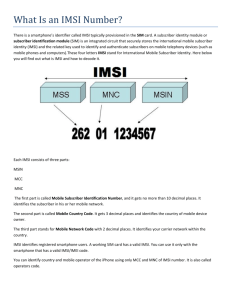
Automatic Device Detection and Central Equipment Identification Registration System Context Lost and Stolen Phones As smartphones have become more sophisticated and more expensive, they are also unfortunately more attractive to thieves. Recent years have seen an increased need for a tool to combat handset theft. The number of smartphones (iPhones and Androids) in use increases every day and they present a target for criminal activities not only for their high “resale” value, but also for the information that they contain. The smartphone has become our sole companion and often is used to contain banking information, address books, and a myriad of potentially useful information to the criminal mind. As the number of mobile devices and messaging users continue to grow, they become an ever increasing target for fraudulent and criminal activities. The following statistics give an indication of the magnitude of the problem: Crimes involving cell phones now comprise 40 percent of thefts in major American cities Over half of Miami citizens, about 52%, have lost their phone or had it stolen 56% of us misplace our cell phone or laptop each month 113 cell phones are lost or stolen every minute in the U.S. 120,000 cell phones are lost annually in Chicago taxi cabs 25% of Americans lose or damage their cell phone each year Every day US$7 million worth of phones are lost globally Big Brother, Theft - At any one time, your mobile network operator (MNO) knows where you are. So can the law authorities. Operators and law authorities can use the technology outlined in this document to track your phone, including right down to where you are standing. Scary? Probably, if you’re a terrorist, a law authority knowing where you are is not an ideal situation to find yourself in. But if your phone has been stolen, then it just might be comforting to know that blocking the device means that no one will be able to use your handset. What is a Fake Phone? Counterfeit phones are handsets that are usually copies of leading brands or models (iPhone, Samsung etc). They are more often than not imported illegally into a country and sold at discount prices, thus avoiding associated customs duties and standards verification. Identifying a fake phone - Every genuine mobile phone has a unique serial number (IMEI) to register it to a carrier network, whereas counterfeits often have cloned or invalid IMEI numbers. The International Mobile Station Equipment Identity or IMEI is a 15 digit number to identify mobile phones (including brand and model). The IMEI number is used by a GSM network to identify valid devices and therefore can be used for preventing a stolen phone from accessing that network. For example, if a mobile phone is stolen, the owner can call his or her network provider and instruct them to "blacklist" the phone using its IMEI number. This renders the phone useless on that network and sometimes other networks too, whether or not the phone's SIM is changed. The IMEI is only used for identifying the device and has no permanent or semi-permanent relationship to the subscriber. Instead, the subscriber is identified by transmission of an IMSI number, which is stored on a SIM card that can (in theory) be transferred to any handset. However, many network and security features are enabled by knowing the current device being used by a subscriber. Criminals have been able to change the IMEI of mobile handsets fairly easily using a data cable (to connect the handsets to a PC) and specialized software. Because of this and of the abundance and high price of mobile handsets, theft has hit epidemic levels in many parts of the world. To determine whether a phone is fake or not dial *#06#. This number works for all devices. Unfortunately, even ‘fake’ phones have an IMEI number (often cloned), so this is not an entirely effective way of establishing whether the phone is a fake or not, it requires further identification as outlined in this document. Impact of counterfeit phones - They are often made with cheap sub-standard materials and have been shown to contain dangerous levels of metals and chemicals like lead, often up to 40 times higher than industry standards. These substandard devices run on inferior operating systems and there have been reports of fraudulent applications which, when downloaded, collect and send the subscribers sensitive and personal data to criminal gangs. Because these phones are made from sub-standard materials and are not tested for compliance with industry and national standards, they suffer frequent call dropouts and put a strain on the mobile networks by degrading coverage, call quality and mobile internet speeds for all users. Research has found that network coverage was significantly reduced as more substandard devices connected to the network, which created coverage black-spots that could only be fixed by installing 80% more base stations. US$6 billion a year drain on global economy - According to the Mobile Manufacturers Forum (MMF) black-market sales of counterfeit and substandard cell phones is a US$6 billion a year problem. Research predicts sales in excess of 200 million counterfeit or substandard mobile devices in 2015 through visible retail sites, with many more expected to be sold in unofficial retail outlets, online auction websites and in local black markets. Counterfeit phones destined for foreign countries are smuggled over lax borders where they bypass government taxes, circumventing safety checks and regulations. This represents a massive financial loss for governments and the mobile phone industry. The MMF conducted an analysis which shows in India alone counterfeits make up more than 20% of the mobile phone market. This is costing the industry US$1.5 billion annually in lost sales and the government is deprived of $85 million in direct tax losses and around $460 million in indirect tax losses. To achieve better control over the devices that are used in a country requires the establishment of an equipment register known as the “Central Equipment Identification Register.” The N-SOFT ADD/CEIR Solution The N-SOFT solution enables the National Regulatory Authorities to collect IMSI/MSISDN/IMEI triplets from all the GSM operators in their country in real time and to analyze the subscriber and handset populations. The solution complies with the requirements of most National Regulatory Authorities in the following areas: Follow the evolution of the mobile markets in the country in real-time, through detailed and accurate statistics on the handset population. The detection of SIM card profiles and Terminal Equipment Identification details to enforce compliance with the standards and regulations pertaining to mobile devices in the country. Fight against other types of fraud, such as identity theft and eliminate illegal SIM-box operations. Fight against device theft. Prevent and eliminate threats to homeland security and other criminal activities. Detect and eliminate counterfeit, lost and stolen devices through a central registry that provides the categorization of devices that are valid and permitted access to the networks. o white, gray, black High performance access. Device information delivered in real time. System redundancy. The solution can be further linked to the worldwide GSMA database thereby allowing the sharing of similar data with authorities across the globe. The advantage being that a phone stolen in one country is identified and made known to all countries sharing the data and denied access accordingly. The GSM Association is an association of mobile operators and related companies devoted to supporting the standardization, deployment and promotion of the GSM mobile telephone system. Technical Description of the Automatic Device Detection (ADD) The N-SOFT ADD solution is made up of the following two components: The ADD/EIR network-based Equipment Identity Register, which provides services required to interrogate device attach and which can also provide new device detection and trigger external management systems The ADME (Advanced Device Management Engine), which provides customer care interface (provisioning) to the nationwide IMEI database, device profile information, reporting/statistics, interfaces to external systems such as GSMA C-EIR or GSM operators’ EIR – which can be extended to filter and build custom logic for triggers to external management systems. The following figure represents the N-SOFT solution: Figure 1: ADD solution overview Figure 2: Software architecture of the ADD solution EIR (Equipment Identification Register) The purpose of the EIR (Equipment Identification Register function) is to maintain a register of all device types that have been validated for use on the networks and to further maintain a registry of all devices that have been reported lost or stolen. A colour (white, gray or black) is assigned to the device to identify its status to connect to the network. When a GSM mobile attaches to the network its status is checked with the Registry and if valid is permitted access to the networks. If the device is lost or stolen and deemed to be invalid a report/alarm is generated and access denied. Network attachment Check_imeireq ADD/EIR Black, gray or white Figure 3 : ADD/EIR colour assignation The MAP CHECK-IMEI requests initiated by a MSC (Mobile Switching Center) is received by the ADD/EIR (Equipment Identity Register function). The ADD/EIR (Equipment Identify function) is in charge of ADD/EI validating that a handset is authorized (i.e. the handset was not stolen R or can be used by the user who is connecting). The ADD/EIR (Equipment Identify Register function) sends the CHECK-IMEI response back to the CHECKIMEI and, optionally, to the MSC. The ADD/EIR (Equipment Identify Register function) can act as an EIR – optionally, returning “white, grey or black-listed IMEI” responses to the MSC. Two methods are used to define colour response: From an internal colour table (IMEI is present and associated to a colour) From a list of users (IMSI) allowed to use the handset: The colour response is forced to black if the IMSI obtained from the CHECK-IMEI message is not included in this IMSI list. The ADD/EIR (Equipment Identify Register function) maintains white, black and gray lists of handsets and will allow handsets that are not blacklisted. It also maintains a list of authorized users per handset (IMSI restriction), if needed. The EIR feature can be turned ON or OFF depending on the needs of the Regulator. Note: With the “IMEI to IMSI restriction” feature, the ADD/EIR can optionally authorize a handset, identified by its IMEI, to be used only by a specific subscriber or a list of subscribers (identified by their IMSI). Automatic Device Detection (ADD) Process The ADD solution takes advantage of the integration and performance of the USPSS7 platform, which combines the following components in a single server: The IP-STG SFE functionality, which embeds the SS7 connectivity board and processes the low level of the signalling stack The applications server, which will process the ADD application itself and host complementary applications like DMP and EIR. The incoming MAP-CHECK-IMEI messages are received and processed by the SS7 stack; the ADD extracts the IMSI and IMEI using the TCAP API. The current IMSI/IMEI pair is compared with any previous values. As a result of the comparison, the ADD will decide if the subscriber (IMSI) is using a new device (IMEI) or not. The messages MAP-CHECK-IMEI are sent to the ADME module via the ADD module, which analyses the messages in order to detect any change of IMSI/IMEI pair. When configured like this, the MAP message is then forwarded to the EIR module. When an IMSI/IMEI pair is detected and compared to the data previously stored in the ADD module, the HLR is queried for gathering the associated MSISDN. Once this is done, all the data is recorded and the ADME is informed about the change in the MSISDN/IMSI/IMEI triplet. In-Memory Database The ADD/EIR (Automatic Device Detection function) database is in-memory-based for high performance access. The Device Detection data is stored in a table holding the IMSI, IMEI, MSISDN, update flag and timestamp. The IMSI is the table key. The update flag is set to ‘Y’ (yes) when the (IMSI, MSISDN, IMEI) triplet has been successfully sent and responded to by the ADME system. ‘N’ (no) is the default value indicating that the ADME system has not yet been successfully notified of a triplet update (a notification retry is then attempted upon the next network attachment for this user). ‘C’ (clone) indicates that the IMSIs are sharing the same IMEI (to notify the ADME when a handset is swapped back and forth between the same users). The timestamp is set when the DB record is created or updated. The IMSI, IMEI, MSISDN and update flag are stored in ASCII format. The timestamp is stored in a binary format. IMSI IMSI IMEI IMEI MSISDN MSISDN Interna tiona l M obile Subscriber Identity (1 6 digits M AX ) Interna tiona l M obile sta tion Equipment Identity (1 6 digits M AX ) M obile Sta tion Interna tiona l ISDN (1 8 digits M AX ) MDM MDM UPDATE UPDATE FLAG FLAG “ Y” “ C” “N” (1 cha r) TIMESTAMP TIMESTAMP DATE+ TIM E yea r, m onth, da y , hour, m in, sec, µs (8 bytes) Figure 4 : ADD data table format Advanced Device Management Engine (ADME)/Nationwide IMEI Database The ADME is the customer care interface component and it must interact with ADD-EIR according to the Customer Care (CC) updates. Especially, the operator is able to give information about mobile equipment status (Black, gray or white) and the ADD-EIR must update its database according to CC’s operator orders. The ADME/nationwide IMEI database module covers the following functionalities: Log-in and Search device Whitelist, Blacklist or Graylist a device Remove Status Priority of the Customer Care for a Device Enable/DisableTracing of a device View Tracing History of a device Synchronize the nationwide IMEI database with the GSMA IMEI database and the country’s GSM operators’ EIRs Pair/Un-Pair a Device with IMSI View Device Pairings. Customer Care Interface The solution offers a rich GUI for the user and administrator of the system, so that they can manage the handset population in the most efficient manner, using the following functions: Management of white/black/gray lists Activate/Deactivate the tracing of specific handsets View the tracing of the handsets for which Tracing had been turned on View historical data on the pairing IMEI/IMSI for a specific handset. Figure 5: Customer Care - Subscriber Device Management Accessing the data related to a handset and searching for it: Users can search the devices by providing various search criteria such as: IMEI IMSI MSISDN Vendor (Make) Model Status (nationwide IMEI database status, like black-, white- or graylisted for a specific IMEI) Whether the device is Trace-enabled or not Whether the device is paired with IMSIs or not Whether the Priority status is set or not. Figure 6: Real-time Subscriber Device Information The solution automatically translates the IMEI number of a specific subscriber’s mobile terminal into a Make & Model and its associated profile, by using the GSMA TAC file and the WURFL online reference information. Users can also perform bulk operations like the Black, White, Graylisting of the selected devices, “Enable or Disable” the device trace or “Clearing Colour Code” for the selected devices, by checking the check box against each device, selecting the bulk operation from the drop-down menu at the bottom of the page and then pressing the "Submit" button. Administrator Interface The solution enables the administrator to produce a large set of reports, including reports based on the IMEI, TAC Analysis, handset population analysis, etc. The Handset TAC analysis provides a flash on the percentage of handsets that have: • An unknown TAC, i.e. a TAC which cannot be correlated to any handset supplier, make or model – known usually as gray market. • A shared TAC, i.e. thepercentage of subscribers that have handsets using TAC which are shared by more than one make/model. This is quite useful when external systems need to identify the supplier of a make/model for delivering the appropriate services/content. • A distinct TAC, i.e. the percentage of subscribers having a distinct TAC. Most popular make and model: Tracks and analyzes the most popular device models in the network. Figure 7: Subscriber TAC Analysis Figure 8: Popular Handset Models Technological view The generic approach of the proposed ADD solution is based on the use of servers running the operating system Linux Red Hat. This approach provides the best performance/cost ratio for the deployment of such a solution. The high availability is based on the redundancy of all the hardware and software components of the solution. The solution has an N+1 architecture, in an active-active configuration. This means that in case of failure of a hardwareor software component, the components that are left would take over without any service interruption. The figures below summarize the typical hardware architecture proposed for the deployment of the solution made up of the following components: EIR/ADD & ADME/Nationwide IMEI Database. Figure 9: ADME/nationwide typical IMEI database hardware architecture Figure 10: EIR/ADD typical hardware architecture Sizing The sizing of the example solution is based on the estimated total number of devices for all GSM operators in a typical small country, i.e. 25 million. A single ADD platform is capable of handling traffic from all the GSM mobile operators in the typical country. Several ADD applications – one per network operator – will be set up on the platform. A duplex configuration is suggested for all components of the solution, due to the size of the total number of devices to be managed and to the expected current growth in the number of subscribers in the country. Such a configuration also helps ensure a high level of availability. The entire solution could be scaled up to cope with additional devices, if necessary, by adding software or hardware capacity.