detailed risk assessment report
advertisement

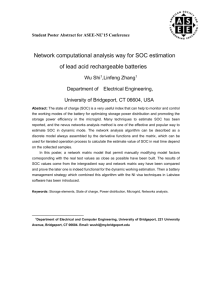
DETAILED RISK ASSESSMENT REPORT Executive Summary During the period May 22, 2015 to June 8, 2015 a detailed inventory of information assets and an information security risk assessment were performed in Company ABC. ABC is an information Technology and Service Consulting organization specializing providing its customers with inclusive technology solutions, including, software licenses, hardware products and IT services. The register creation and risk assessment identified a number of average risk items that should be addressed by the management. DETAILED ASSESSMENT 1. Introduction 1.1 Purpose The aim of carrying out the asset registration and the risk assessment was to identify risks and susceptible elements of Security Operations Centre’s (SOC) Information Security Management System (ISMS). Firstly, a risk register was drawn to allow the assessment team take scope of all the information assets at ABC Company. Components in the SOC department were analysed in order to determine the level of security each boosted. Following that, this assessment will be used to come up with a risk mitigation and treatment plan for each affected asset and their respective department. Several items in the centre stood out as high risk. These are database indexes, stored procedures and general administration style. 1.2. Scope of this risk assessment Page 1 SOC’s information Security Management System is composed of several components. The tables are used for data storage. This data regards SOC’s employees’ personally identifiable information such as names, training needs, certifications, appraisal performance metrics, reward scheme points. Indexes in the SOC are used to make the process of data retrieval quicker. The indexes have unique values for their unique keys. Views are used to create pre built queries and canned controls to allow the administrators and SOC system developers quickly avoid tabulated data getting complicated at the relationship level. Stored Procedures are programs developed by SOC engineers using Oracle’s PL/SQL to loop through records faster and more efficiently. The Procedures allow the administrator conduct if-then logic, traverse record by record and call special built in functions to aid in complex database calculations. Triggers are orders executed when important events for instance update of metrics records is done or a deletion of a record is made. The scope of the risk assessment includes all the above elements. Additional components are stateless firewalls that currently exist, web applications and operating systems (Windows 7 Enterprise/ OS). All these form part of the scope for analysing risk in the SOC database and the entire department. 2. Risk Assessment Approach 2.1 Participants Role Participant System owner ####### System custodian Jane Doe Page 2 Chief SOC Database administrator Jane Doe Security administrator John Doe Risk assessment team Author, author, author 2.2 Techniques used Technique Description Questionnaire The team customized the NIST questionnaire template from http://csrc.nist.gov/publications/nistpubs/index.html. Assessment Tools The team used nmap and AppScan to test security and system’s configurations. Vulnerability Sources Several vulnerability sources were utilized including the following: Microsoft Security Advisories (www.microsoft.com/security) NIST I-CAT vulnerability database (http://icat.nist.gov) Review of documentation SANS Top 20 (http://www.sans.org/top20/) The risk assessment team reviewed ISMS security policies, system documentation, network diagrams and operational manuals for each asset. Site visit The group carried out a site visit to the organisation Page 3 and reviewed the SOC system components while performing control tests. The team conducted interviews to certify Interviews information from other sources. Among those interviewed include SOC manager, SOC engineers and SOC database administrators. 2.3 Risk Model To determine the risk associated with each information asset in the organization, the assessment team used the following model: Risk rating =Current probability x Unit impact To calculate above, the risk rating was automated in an Excel function for each test asset. 2.3.1 Threat Probability Likelihood Definition Very likely considered to have chance of occurring every month (up to 100% probability) High considered to have chance of occurring once within the next two months or up to six times a year (up to 50% probability in next month) Moderate considered to have chance of occurring once within the next six months or up to twice a year (up to17% probability) Page 4 Low considered to have chance of occurring once within the next year or up to twice within two years (up to 8% probability) Very low considered to have a chance of occurring once within the next two years (up to 4% probability) 2.3.2 Unit Impact Impact Definition Critical (100%) Either: sustained or ongoing negative national media publicity; or financial loss or impact exceeding £1m for Unit; or majority of Unit affected for more than 1 month Major (80%) Either: one-off negative national media publicity; or financial loss or impact from £100k - £1m for Unit; or majority of Unit affected for up to 1 month Moderate (62%) Either: negative national media publicity likely but controllable; or financial loss or impact from £20k - £100k for Unit; or part of Unit affected on on-going basis Minor (25%) Either: negative publicity limited to Unit; or financial loss or impact from £1k £20k for Unit; or small part of Unit affected on on-going basis Insignificant (1%) Either: negative publicity limited to part of Unit; or financial loss or impact up to £1k for Unit; or individuals within Unit affected for very short period Page 5 Following the tabulation, risk rating was determined as follows: Unit Impact Threat Insignificant Minor Moderate Major Critical Probability (1%) (25%) (62%) (80%) (100%) Low Risk Medium Risk High Risk High Risk High Risk 100%x1%=1% 100%x25%=25% 100%x62%=62% 100%x80%=80% 100%x100%=100% High Low Risk Medium Risk Medium Risk Medium Risk Medium Risk (50%) 50%x1%=0.5% 50%x25%=12.5% 50%x62%=31% 50%x80%=40% 50%x100%=50% Moderate Low Risk Low Risk Medium Risk Medium Risk Medium Risk (17%) 17%x1%=0.2% 17%x25%=4.3% 17%x62%=10.5% 17%x80%=13.6% 17%x100%=17% Medium Low Risk Low Risk Low Risk Low Risk Low Risk (8%) 8%x1%=0.1% 8%x25%=2% 8%x62%=5% 8%x80%=6.4% 8%x100%=8% Low Low Risk Low Risk Low Risk Low Risk Low Risk (4%) 4%x1%=0.04% 4%x25%=1% 4%x62%=2.5% 4%x80%=3.2% 4%x100%=4% Very Likely (100%) Risk Scale: Low (1 to 10); Medium (>10 to 50); High (>50 to 100) 3.0 System Characterisation 3.1 Technology Components Component Description Applications In house developed server pages, using Oracle XE Database Oracle XE Operating System Windows 7 Enterprise OS Page 6 Protocols Open DataBase Connectivity for Communications (ODBC) among the SOC databases. 3.2 Data used by Information assets Data Non physical information Description Includes o forms o processes o databases including names addresses recruitment documentation Photograph Ethnicity Serial umbers tags Information on physical asset and hardware Includes o Biometric devices o Multifactor o Wired and wireless corporate network o Encrypted USBs o Encryptors o Storage devices Software Include o Standard applications Include o Managerial secure room o Secure computer with a hardened OS and disable disk and flash drives o Cellular signal blocker o Motion and camera detectors o Access control facilities Visitors badge Fingerprint scanners Pulse scanner Secure key cabinets o Grid and alternative power sources o Fire suppressants including Argon gas Dry sprinkler Fire doors Services data Page 7 o o o Personally identifiable information o o o o o o o Carefully located data buildings Includes Database on all employees Name Address (current and previous) Phone Number Database of SOC employees All communication assets such as fax and mobile phones Archived information Contingent arrangements Archives Disaster mitigation strategies Configuration databases 3.3 Flow diagram The diagram below illustrates the information security management system components as information assets in the SOC section of ABC that relates and interacts in the intra-organization sphere. The SOC database is the central information asset in the Security Operations Centre department. The databases may be considered as an entire back end service from the entire organization’s point of view. PERSONALL Y IDENTIFIABLE INFORMATION SECURITY OPERATIONS CENTRE’S DATABASE FINANCIAL RECORDS JOB DESCCRPTION AND SPECFICATION DEVEOPLMENTA AND TRAINING PROGRAM Page 8 BACK OFFICE: DATABASE ADMIN BACK OFFICE: DATABASE AADMIN PERFORMANCE METRICS 4. Vulnerability Statement The team identified the following likely liabilities: Vulnerability Description Confidentiality With a bit of technical knowledge, non cleared employees/ staff working at the Security Operations Centre with an ill motive may be able to eavesdrop on sensitive information they are not cleared for Non repudiation The front end hubs at the SOC have weak passwords. Attackers could exploit this weakness and issue ill instructions to unwary network users by usurping the role of network managers. Authentication The SOC database cross check employed is lacking. The only check existent is password authentication. No biometric devices, tokens and usernames are used to ascertain the administrators’ credentials Data availability Data served by the communication assets that support the SOC databases is not available in a secure manner. Malicious people with descriptors may be able to wiretap and eaves drop both confidential and non confidential communications since the current level of encryption is outdated Data integrity Data bases at SOC have non encrypted data due to their separation from the public network, data integrity and system information may be Page 9 compromised by infection of viruses or malicious scripts. The viruses may the buffer flow vulnerability. These may be then used to spy or commit industrial espionage Data Leaks While the SOC databases is not connected to any public network, internet based threats are still posed. The network interface of the databases may be compromised by hackers if they manage to capture this traffic. Theft Disgruntled insiders are likely to steal archived information for profit, revenge or for money. This more so happens where the archives aren’t encrypted. Hopscotch Were the records in the database to fall in the hands of a cyber criminal, hopscotch may be committed where the perpetrator digs deep by playing the game of leverage for bigger attacks until he/she reaches the database’s back-end SQL- injection This may be perpetrated by hackers who inject applications with malicious code and scripts as strings which are later forwarded as instances to the SQL server to parse and execute. Sub-standard key SOC’s keys are currently stored on disk drives. Despite this being a management safe management systems policy, the security of the drives has to be checked to ensure that they do not fall to the wrong hands. Database SOC’s general database vulnerability was largely culminated by this inconsistencies general factor. This problem is more administrative and less tied to the technology of databases Page 10 5. Remediation 5.1 Threat Statement Threat Source Hacker Poor administration Threat Action Unauthorized system access Password cracking Virus infection Data leaking Trojan horses Worms Social engineering Database inconsistencies Poor keys management Insider(disgruntled, Malicious script poorly trained, or careless Bugs employee ) SQL injections Black mail Data theft Browsing personally identifiable information Eaves dropping Industrial espionage Spying Denial of service Competitor Joker Page 11 Hop scotching Data theft 5.2 Risk assessment results The mitigation actions above will hopefully ensure SOC employee’s personal and sensitive information secured. The framework will form a governance policy to ensure that the stored information is handled securely, effectively efficiently and legally. Consequently, SOC will avoid consequences of going against data protection legislation and policies which range from insignificant to illegal: o Penalties for breaking data safeguarding laws can be huge such that a company way incur a fine of up to £500,000 in each instance of breach alongside accompanying sanctions. o Individual SOC employees who may be guilty of information breaches may be exposed to disciplinary action and possible suspension or dismissal o The morale and confidence of employees for the whole organization may lessen. This could be a blow to ABCs reputation and would tarnish the image of the company in the society. Consequently, the image would take a longer time to rebuild than initially. Item Observation Threat Existing Likely source/vulnerability controls hood The outbound Eaves dropping/ Limited high communications industrial espionage corroboration Number 1 are not properly checks Page 12 Impact Very high Risk Recommended rating controls 80% Adopt modern encryption keys for all outbound encrypted 2 communication The databases SQL injections, Stateful support worming, viruses firewalls High high 62% Stateless firewalls since they are more applications have secure, faster and outdated firewall require less memory protection 3 The database’s Hackers/ crackers Passwords High High 62% Require the use of administrators’ must be at special characters database have least eight with at least two weak passwords characters roman numerals long 4 Poor Database none High High 62% Ensuring that administration inconsistencies, poor proposed database keys administrative security, policies consider all foreseeable scenarios of enabling database inconsistent such as different clearance levels as in various database record stacks 5 Data leaks Network threats from none High High 62% hackers and crackers TSL or SSL encrypted communication platform 6 Enterprise SQL injections none database High High 80% Guard web-facing database nodes with Page 13 protection Stateful firewalls and test all input variables for SQL-injection in development stage 6 Poor key Lost keys and back Cabinet filed management ups Disk drives High High 62% The keys be put in protected statecan to reduce attack vulnerability 5.3 Basic Requirements The landscape of threats is ever-changing and hence information assets require to be safe guarded proactively. To realize the recommended controls, Security Operations Centre may be guided by an approach that includes assessment, expanded policy base and ongoing operations improvement. The expanded policy base involves defining an ample set of asset security roles and responsibilities. This will tackle the human aspects contributing to weakness in the ISMS. In this regard there is need for the informational security system to be completely proactive rather than geared toward occurrence detection alone. Assessments involve gauging the databases performance in regards to information assets security and comparison with optimum database standards. These assessments should range from monthly reviews to facilitate optimal performance to critical needs that have monetary/ funding implications. Ongoing operations improvements are geared to the provision of protection and monitoring of database components and intra-organizational networks linked to them. As part of this encryptors are required for all data being transmitted into SOC network. Automating sour detection of bad actors can involve a heavy investment but potentially save ABC huge amounts of finances in the future. Page 14 References Microsoft (2014). Safety and Security Centre. Retrieved May, 25, 2015 from http://www.microsoft.com/security/default.aspx National Vulnerability Database (2015) NIST. Retrieved May, 25, 2015 from http://icat.nist.gov/ SANS (2015). Critical Security Controls for Effective Cyber Defense. Retrieved May, 25, 2015 from http://www.sans.org/critical-security-controls/ Page 15