Go_Networks_Security
advertisement

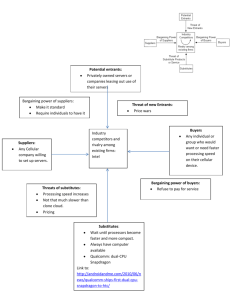
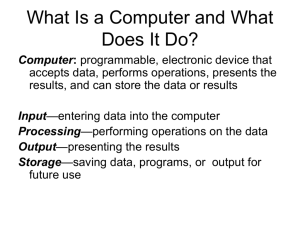
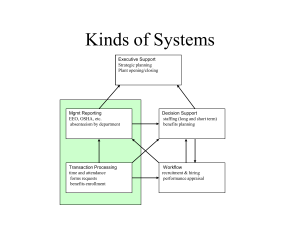
Technology In Action Chapter 12 Computer Networks & Security • • • • • • Advantages of a network Client/server and peer-to-peer networks Classifications of client/server networks Client/server network components Types of servers Network topologies NEXT SLIDE 1 Technology In Action Chapter 12 Topics • • • • • Types of transmission media Network software Network adapters Moving data in a client/server network Securing networks NEXT SLIDE 2 Technology In Action Chapter 12 Networking Advantages • Networks: – Increase productivity – Enable the sharing of resources – Facilitate Internet connectivity NEXT SLIDE 3 Technology In Action Chapter 12 Client/Server Networks • Server based network: – Clients – Servers • Data flows efficiently • Servers respond to requests from clients • Servers perform specific tasks • Scalable network NEXT SLIDE 4 Technology In Action Chapter 12 • Classifications of Client/Server Networks LAN: – Local area network – Computers linked together over a small geographic region • WAN: – Wide area network – Computers linked together over large diverse geographic locations • MAN: – Metropolitan area network – Computers linked together within a city or NEXT county SLIDE 5 Technology In Action Chapter 12 Classifications of Client/Server Networks • PAN: – Personal area network – Wireless devices connected in close proximity to each other • Intranet: – Private corporate network NEXT SLIDE 6 Technology In Action Chapter 12 Constructing Client/Server Networks • • • • • • Servers Network topologies Transmission media Network operating system (NOS) Network adapters Network navigation devices 7 Technology In Action Chapter 12 Network Security • Authentication: – User ID and password used to access the network • Access privileges: – Enable access to certain network systems • Physical protection measures: – Restrict physical access to sensitive network equipment – Magnetic card readers – Biometric access devices NEXT SLIDE 24 Technology In Action Chapter 12 Network Security • Firewalls: – Prevent access to the network by unauthorized users – Composed of software and/or hardware – Screens and validates data packets – Bastion host/proxy server NEXT SLIDE 25