Encryption Methods and algorithms
advertisement

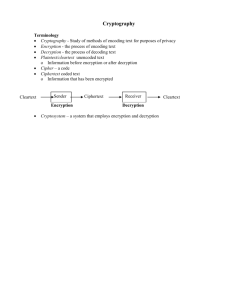
David Froot How do we transmit information and data, especially over the internet, in a way that is secure and unreadable by anyone but the sender and recipient? Encryption is simply the process of transforming information, such as plain text or numbers, using an algorithm. Only those with the algorithm can decipher the encrypted information, and even a relatively simple encryption technique can be difficult to decode without the key. Original encryption methods were simple. For example a note would be encrypted using a new alphabet. A letter shift was a common method: ABCDEFGHIJKLMNOPQRSTUVWXYZ ABCDEFGHIJKLMNOPQRSTUVWXYZ A is now represented by an E, B by an F, etc. “The Quick Brown Fox” becomes “Xli Uymgo Fvsar Isb” But: This simple cipher is easily cracked by powerful computers This cipher requires both the sender and recipient have the decipher – but you cannot transmit encrypted data to someone who doesn’t already have the cipher code. If both sender and recipient have the hashing algorithm key, called symmetric key encryption, then data can be sent safely. Key encryptions are based on the idea of “hash values” and “hashing algorithms” It would be impossible to determine from the hash value that the input was 10,667 and the algorithm was a multiplication of 143. Even this incredibly simple algorithm is hard to break. Modern algorithms are more complex and produce 128 bit hash values which have 3,402,823,669,209,384,634,633,746,074,300,000,000,000,0 00,000,000,000,000,000,000,000,000 combinations and makes the hashing algorithm impossible to compute. What is both the sender and recipient don’t have the key? We need a way of encrypting and decrypting without sharing a key. Today, the standard practice is called Public Key Encryption and uses a pair of two keys. One key is privately held by one person, and the other key is publicly known. The public key can encrypt data but not decrypt it. Likewise the private key can decrypt data but not encrypt it. Two keys are generated. If Bob wants to sent secure data to Alice, he encrypts using Alice’s public key. Then only Alice can decrypt with her private key. Source: http://en.wikipedia.org/wi ki/Public-key_cryptography But how are these keys generated? And what mathematical algorithms allow you to encrypt but not decrypt and vice versa? A simple multiplication function like the above hashing algorithm clearly doesn’t work. What does? Source: http://www.freesoft.org/CIE/Topics/144.htm We start with a new number system called a modulus. This is simply a number system that repeats after exceeding its maximum value, in this case 15, but can be any number at all. It forms a “loop” rather than a traditional number “line”. Arithmetic is performed relatively normally. Modulus’ have a few special properties which are used to solve the encryption problem. The most important is called the Euler Totient function, which says that for any number x, and a special number q(m): q(m) x The =x value of q(m) is derived from the the modulus limiting number, i.e. 15. When the modulus limiting number m is the product of two prime numbers p and q, then: q(m) = (p-1)(q-1)+1 q(m) So can be rewritten as 2 factors: zy = q(m) for any value x, we can raise it to a power z: xz which becomes essentially a “random” number. Only when (xz)y does it return the original value x. If x is any number we wish to encrypt, then we can call z the public key, and y the private key. A simple example: 2 prime numbers 3 and 11: m = 33 Q(m) = (3-1)(11-1)+1 = 21 (factors 3 and 7) If we want to encrypt the number 20 with public key: 203 = 8000 = 14 in mod 33. Given a value 14, we need the private key (7) to decrypt this number. The public key (3) does nothing to help decrypt 14. 147 = (203)7 = 105413504 = 20 in mod 33 This simple example demonstrates the concept but is easy for a computer to decode. For large values of m, solutions are nearly impossible to compute because even though the value of m is known, no efficient algorithms exist to determine prime factors of a very large number. Even if q(m) were computed, the factors chosen for y and z are arbitrary and difficult to compute. http://computer.howstuffworks.com/encrypt ion2.htm http://en.wikipedia.org/wiki/Encryption http://www.freesoft.org/CIE/Topics/144.ht m http://en.wikipedia.org/wiki/Publickey_cryptography http://en.wikipedia.org/wiki/Blowfish_(ciph er)