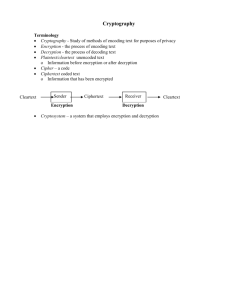
Generic encryption
advertisement
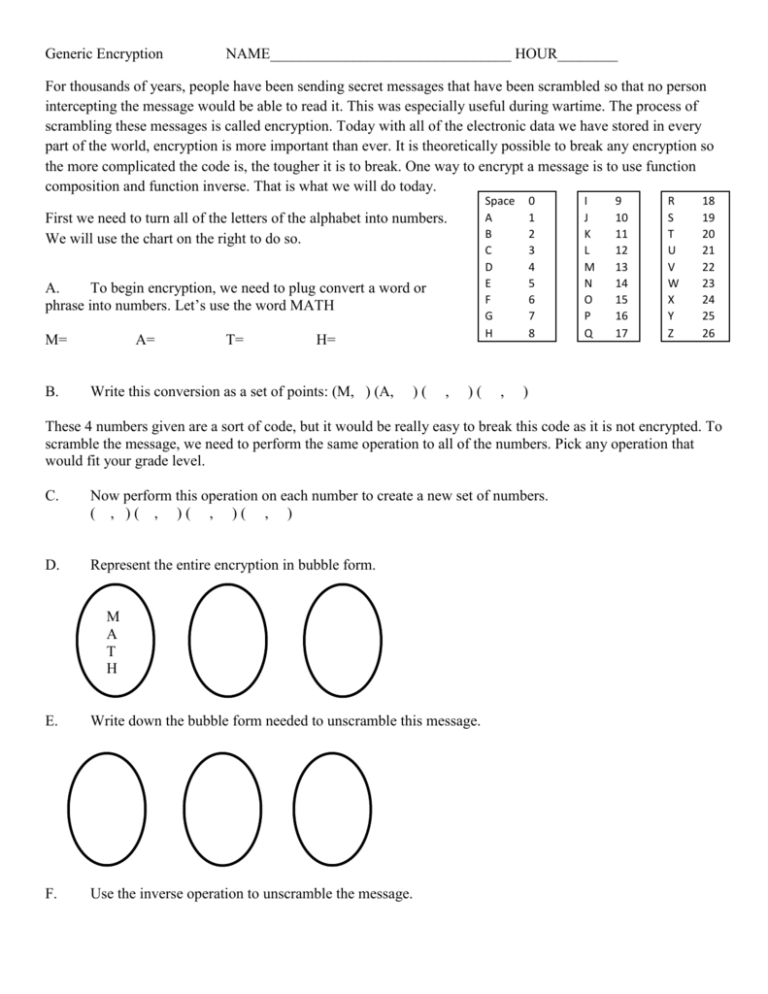
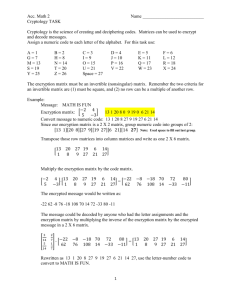
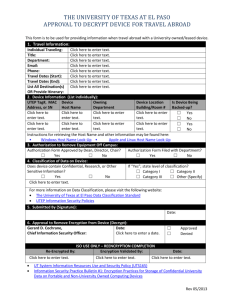
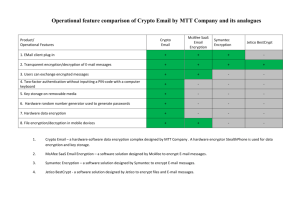
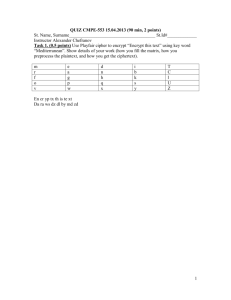
Generic Encryption NAME________________________________ HOUR________ For thousands of years, people have been sending secret messages that have been scrambled so that no person intercepting the message would be able to read it. This was especially useful during wartime. The process of scrambling these messages is called encryption. Today with all of the electronic data we have stored in every part of the world, encryption is more important than ever. It is theoretically possible to break any encryption so the more complicated the code is, the tougher it is to break. One way to encrypt a message is to use function composition and function inverse. That is what we will do today. Space A B C D E F G H First we need to turn all of the letters of the alphabet into numbers. We will use the chart on the right to do so. A. To begin encryption, we need to plug convert a word or phrase into numbers. Let’s use the word MATH M= B. A= T= H= Write this conversion as a set of points: (M, ) (A, )( , )( , 0 1 2 3 4 5 6 7 8 I J K L M N O P Q 9 10 11 12 13 14 15 16 17 R S T U V W X Y Z 18 19 20 21 22 23 24 25 26 ) These 4 numbers given are a sort of code, but it would be really easy to break this code as it is not encrypted. To scramble the message, we need to perform the same operation to all of the numbers. Pick any operation that would fit your grade level. C. Now perform this operation on each number to create a new set of numbers. ( , )( , )( , )( , ) D. Represent the entire encryption in bubble form. M A T H E. Write down the bubble form needed to unscramble this message. F. Use the inverse operation to unscramble the message. G. Convert each of the phrases below into numbers MR WHITE IS COOL ( , )( , )( , ( , )( , )( , ( , )( , )( , ( , ) H. )( )( )( , , , )( )( )( , , , ) ) ) YEAH RIGHT ( , )( , )( ( , )( , )( , , )( )( , , )( )( , , ) ) Now encrypt the message using an operation of your choosing __ __ __ __ __ __ __ __ __ __ __ __ __ __ __ __ I. What do we need to decrypt the message? J. Now decrypt each message __ __ __ __ __ __ __ __ __ __ Space A B C D E F G H 0 1 2 3 4 5 6 7 8 I J K L M N O P Q 9 10 11 12 13 14 15 16 17 R S T U V W X Y Z 18 19 20 21 22 23 24 25 26 K. Create your own phrase and choose an operation; then encrypt your message. You will then give your code and your operation to a member of the class. Operation:______________ Message: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Numbers: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Code: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ L. Create a second phrase and choose a different operation; then encrypt your message. You will then give your code and your operation to a member of the class. Operation:______________ Message: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Numbers: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Code: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ M. Get a code and an operation from a class member and decode the message Operation:______________ Code: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Numbers: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Message: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ N. Get a second code and an operation from a different class member and decode the message Operation:______________ Code: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Numbers: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ Message: ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___ ___