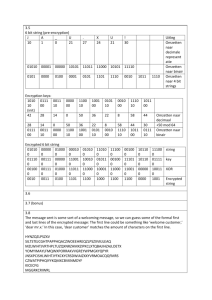
IA Book v0.1.4
advertisement

Principles of Information Assurance Corey Schou Dan Shoemaker Copyright 2003 Introduction to Information Assurance (CDS) ___________________________________ 17 McCumber Model (CDS) _________________________________________________________ 17 International View (DAN) ________________________________________________________ 17 BS 7799 (DAN) ________________________________________________________________________ 17 ISO 17799 (DAN) ______________________________________________________________________ 17 Assurance Management __________________________________________________________ 17 Confidentiality (CDS) (0011) _____________________________________________________________ 17 Integrity (CDS) (0011)___________________________________________________________________ 17 Availability (CDS) (0011) ________________________________________________________________ 17 Access Control (0010) _______________________________________________________ 18 Access Control Administration (0010) ______________________________________________ 18 Centralized Systems (0010) _______________________________________________________________ 18 Diameter (0010) ______________________________________________________________________ 18 RADIUS (0010) ______________________________________________________________________ 18 TACAC (0010) ______________________________________________________________________ 18 Decentralized Systems (0010) _____________________________________________________________ 18 Access Control Models and Techniques (0010) _______________________________________ 18 Categories of Access Control (0011) ________________________________________________________ 18 System Access Controls (0011) __________________________________________________________ 18 Data Access Controls (0011) ____________________________________________________________ 18 Access Control Techniques (0010) _________________________________________________________ 18 Capability Tables and ACL (0010) _______________________________________________________ 18 Content Dependent Access Control (0010) _________________________________________________ 18 Restricted Interfaces (0010) _____________________________________________________________ 18 DAC (0010) ___________________________________________________________________________ 18 MAC (0010)___________________________________________________________________________ 18 RBAC (0010) __________________________________________________________________________ 18 Concepts of Access Control (0011) _________________________________________________ 18 Control Types (0011) ____________________________________________________________________ 18 Access Control Services (0011) ____________________________________________________________ 18 Identification and Authentication (0010) ____________________________________________ 18 Authentication (0010) ___________________________________________________________________ 18 Biometrics (0010) ____________________________________________________________________ 18 Cognitive Password (0010) _____________________________________________________________ 18 Cryptographic Keys (0010) _____________________________________________________________ 18 Memory Cards (0010) _________________________________________________________________ 18 One Time Passwords (0010) ____________________________________________________________ 18 Passphrase (0010) ____________________________________________________________________ 18 Passwords (0010) _____________________________________________________________________ 18 Smart Cards (0010) ___________________________________________________________________ 18 Authorization (0010) ____________________________________________________________________ 18 Stage Setting __________________________________________________________________________ 18 Intrusion Detection Systems (0010) (0100) ___________________________________________ 18 Behavior Based (0010) __________________________________________________________________ 18 Host Based (0010) ______________________________________________________________________ 18 Network Based (0010) ___________________________________________________________________ 18 Signature Based (0010) __________________________________________________________________ 18 Pros and Cons (0010)____________________________________________________________________ 18 Single Sign-On Technology (0010) _________________________________________________ 18 Directory Services (0010) ________________________________________________________________ 18 KERBEROS (0010) _____________________________________________________________________ 18 SESAME (0010) _______________________________________________________________________ 18 Thin Clients? (0010) ____________________________________________________________________ 18 Unauthorized Access Control and Attacks (0010) _____________________________________ 18 Unauthorized Disclosure of Information (0010) _______________________________________________ 18 Emanation Security (WAP and TEMPEST) (0010) ____________________________________________ 18 Attack Types (0010) ____________________________________________________________________ 18 Network Attacks _____________________________________________________________________ 19 Syn Flood _________________________________________________________________________ 19 ICMP Flood _______________________________________________________________________ 19 UDP Flood ________________________________________________________________________ 19 SMURF __________________________________________________________________________ 19 Fraggle ___________________________________________________________________________ 19 Teardrop __________________________________________________________________________ 19 Spoofing __________________________________________________________________________ 19 Penetration Testing (Right Place?) (0010) ____________________________________________________ 19 Applications and Systems Development (0010) ___________________________________ 20 Knowledge Based Systems and Intelligence (0010) (0011) ______________________________ 20 Artificial Neural Network (0010) (IGGY) ____________________________________________________ 20 Expert Systems (0010) ___________________________________________________________________ 20 Application Security Controls _____________________________________________________ 20 Abstraction (0011) ______________________________________________________________________ 20 Accountability (0011) ___________________________________________________________________ 20 Data Hiding (0011) _____________________________________________________________________ 20 Defense in Depth (0011) _________________________________________________________________ 20 Hardware Segmentation (0011) ____________________________________________________________ 20 Process Isolation (0011)__________________________________________________________________ 20 Reference Monitor (0011) ________________________________________________________________ 20 Security Kernel (0011)___________________________________________________________________ 20 Separation of Privilege (0011) _____________________________________________________________ 20 Service Level Agreements (0011) __________________________________________________________ 20 Supervisor and User Modes (0011) _________________________________________________________ 20 System High Mode (0011) ________________________________________________________________ 20 Data and Information Security (0011) (CDS) ________________________________________ 20 Primary Storage (0011) __________________________________________________________________ 20 Real and Virtual (0011) __________________________________________________________________ 20 Secondary Storage (0011) ________________________________________________________________ 20 Databases (0010) ________________________________________________________________ 20 Aggregation and Inference (0010) __________________________________________________________ 20 Concurrency Issues (0010) _______________________________________________________________ 20 Data Mine (0010) _______________________________________________________________________ 20 Data Warehouse (0010) __________________________________________________________________ 20 Database Interface Languages (0010) _______________________________________________________ 20 Database Security ______________________________________________________________________ 20 Distributed Data Model (0010) ____________________________________________________________ 20 Hierarchical Database (0010) _____________________________________________________________ 20 Network Database Management System (0010) _______________________________________________ 20 Object Oriented Database (0010)___________________________________________________________ 20 Relational Data Model (0010) _____________________________________________________________ 20 Database Dictionary (0010) _____________________________________________________________ 20 Structured Query Language (0010) _______________________________________________________ 20 Distributed Computing (0010) _____________________________________________________ 20 Distributed Applications (0011) ___________________________________________________________ 20 Agents (0011) _______________________________________________________________________ 20 Applets (0011) _______________________________________________________________________ 20 Security in Distributed Systems (0011) ____________________________________________________ 20 Examples to Discuss (CDS) _______________________________________________________________ 20 ActiveX (0010) ______________________________________________________________________ 21 CGI (0010) __________________________________________________________________________ 21 COM an DCOM (0010) ________________________________________________________________ 21 Cookies (0010)_______________________________________________________________________ 21 Enterprise Java Bean (0010) ____________________________________________________________ 21 Java Applet (0010) ____________________________________________________________________ 21 OLE (0010) _________________________________________________________________________ 21 ORB and CORBA (0010) ______________________________________________________________ 21 Malicious Actions (0010) _________________________________________________________ 21 Brute Force (0011) ______________________________________________________________________ 21 Denial of Service (0010) _________________________________________________________________ 21 Distributed Denial of Service ____________________________________________________________ 21 Dictionary attack (0011) _________________________________________________________________ 21 Eavesdropping (0011) ___________________________________________________________________ 21 Hidden Code (0011)_____________________________________________________________________ 21 Inference (0011)________________________________________________________________________ 21 Logic Bomb (0010) _____________________________________________________________________ 21 Pseudo Flaw (0011) _____________________________________________________________________ 21 Remote Maintenance (0011) ______________________________________________________________ 21 Smurf Attacks (0010)____________________________________________________________________ 21 Sniffing (0011)_________________________________________________________________________ 21 Social Engineering (0011) ________________________________________________________________ 21 Timing Attacks (0010) ___________________________________________________________________ 21 Traffic Analysis (0011) __________________________________________________________________ 21 Trojan Horse (0010)_____________________________________________________________________ 21 Virus (0010) ___________________________________________________________________________ 21 Worm (0010) __________________________________________________________________________ 21 Object Oriented Environments and Principles (0010) _________________________________ 21 Abstraction (0010) ______________________________________________________________________ 21 Application Threat(s (0010) _______________________________________________________________ 21 Classes and Objects (0010) _______________________________________________________________ 21 Polyinstantiation (0010) __________________________________________________________________ 21 Polymorphism (0010) ___________________________________________________________________ 21 Project development (0010) _______________________________________________________ 21 Software Lifecycle (0010) ________________________________________________________________ 21 Software Development Models (0010) ______________________________________________________ 21 Acceptance Testing (0010) _____________________________________________________________ 22 Accreditation (0011) __________________________________________________________________ 22 Certification (0011) ___________________________________________________________________ 22 Change Management (0011) ____________________________________________________________ 22 Code (0011) _________________________________________________________________________ 22 Code Review (0011) __________________________________________________________________ 22 Conceptual definition (0011) ____________________________________________________________ 22 Configuration Management (0011) _______________________________________________________ 22 Design (0011) _______________________________________________________________________ 22 Disposal (0010) ______________________________________________________________________ 22 Functional Design Analysis and Planning (0010) ____________________________________________ 22 Functional Requirements (0011) _________________________________________________________ 22 Functional Specifications (0011) _________________________________________________________ 22 Implementation (0010) ________________________________________________________________ 22 Maintenance (0010) (0011) _____________________________________________________________ 22 Operations (0010) ____________________________________________________________________ 22 Project Initiation (0010) ________________________________________________________________ 22 Software Development (0010) ___________________________________________________________ 22 System Design Specification (0010) ______________________________________________________ 22 System Test (0011) ___________________________________________________________________ 22 Writing Secure Code (???) ________________________________________________________ 22 Awareness, Training and Education (CDS/VIC) __________________________________ 23 Tools (CDS) ____________________________________________________________________ 23 Standards _____________________________________________________________________________ 23 Cryptography (0100) (0010) Stuff from my book? _________________________________ 24 Cryptography Defined ___________________________________________________________ 24 Classes of Ciphers ______________________________________________________________________ 24 Cipher Types (0010) ____________________________________________________________________ 24 Asymmetric Cryptography (0010) ________________________________________________________ 24 Block Cipher (0010) __________________________________________________________________ 24 Kerckhoff Principle (0010) _____________________________________________________________ 24 Key Escrow (0010) ___________________________________________________________________ 24 Stream Cipher (0010)__________________________________________________________________ 24 Substitution Cipher (0010) ______________________________________________________________ 24 Symmetric Cryptography (0010) _________________________________________________________ 24 Transposition Cipher (0010) ____________________________________________________________ 24 Key Clusters (0011) _____________________________________________________________________ 24 Encryption and Decryption (0011) _________________________________________________________ 24 Work Factor Force times effort and work (0011) ______________________________________________ 24 Message Authentication __________________________________________________________ 25 Digital Signatures ______________________________________________________________________ 25 Message Digests _______________________________________________________________________ 25 Non Repudiation _______________________________________________________________________ 25 Attacks (0010) __________________________________________________________________ 24 Adaptive Chosen Plaintext Attack (0010) ____________________________________________________ 24 Analytic Attack (0010) (0011) _____________________________________________________________ 24 Brute Force (0011) ______________________________________________________________________ 24 Implementation Attacks (0011) ____________________________________________________________ 24 Known Plaintext Attack (0010) ____________________________________________________________ 24 Man in the Middle Attack (0010) __________________________________________________________ 24 Statistical Attacks (0011) _________________________________________________________________ 24 Specific Methods of Attack _______________________________________________________________ 24 Chosen Ciphertext Attack (0010) ________________________________________________________ 24 Chosen Plaintext Attack (0010) __________________________________________________________ 24 Ciphertext – Only Attack (0010) _________________________________________________________ 24 Key Issues (0011)________________________________________________________________ 25 Key Change (0011) _____________________________________________________________________ 25 Key Control (0011) _____________________________________________________________________ 25 Key Disposal (0011) ____________________________________________________________________ 25 Key Distribution (0011) __________________________________________________________________ 25 Key Generation (0011) __________________________________________________________________ 25 Key Installation (0011) __________________________________________________________________ 25 Key Escrow and Recovery (0011) __________________________________________________________ 25 Key Storage (0011) _____________________________________________________________________ 25 Cryptographic Applications (0010) _________________________________________________ 24 Encryption at Different Layers (0010) _______________________________________________________ 24 One Time Pad (0010) ____________________________________________________________________ 24 Public Key Infrastructure (PKI) (0010) ______________________________________________________ 24 Certificate Revocation List (CRL) (0010) __________________________________________________ 24 Certification Authority (CA) (0010) ______________________________________________________ 24 PKI Steps (0010) _____________________________________________________________________ 24 Registration Authority (0010) ___________________________________________________________ 24 Cryptographic Protocols (0010) ___________________________________________________ 24 Internet Security (0010) __________________________________________________________________ 24 HTTPS (0010) _______________________________________________________________________ 24 IPSec (0010) ________________________________________________________________________ 24 S/MIME (0010) ______________________________________________________________________ 24 Secure Hypertext Transfer Protocol (S-HTTP) (0010) ________________________________________ 24 Secure Sockets Layer (SSL) (0010) _______________________________________________________ 24 SET (0010)__________________________________________________________________________ 24 SSH2 (0010) ________________________________________________________________________ 24 Message Security Protocol (MSP) (0010) ____________________________________________________ 24 Pretty Good Privacy (PGP) (0010) _________________________________________________________ 24 Privacy Enhanced Mail (PEM) (0010)_______________________________________________________ 24 Cryptography Definitions (0010) ___________________________________________________ 24 Attacks (0010) _________________________________________________________________________ 25 Keys and Text (0010) ___________________________________________________________________ 25 Keyspace (0010) _______________________________________________________________________ 25 Spy Cipher (0010) ______________________________________________________________________ 25 Steganography (0010) ___________________________________________________________________ 25 Strength of Crypto Systems (0010) _________________________________________________________ 25 Hybrid Approaches (0010) ________________________________________________________ 25 Asymmetric Algorithm (0010) ____________________________________________________________ 25 Diffie Hellman Key Exchange (0010) _____________________________________________________ 25 El Gamal (0010)______________________________________________________________________ 25 Elliptic Curve Cryptosystems (ECC) (0010) ________________________________________________ 25 Data Encryption (0010) __________________________________________________________________ 25 Key Management (0010) _________________________________________________________________ 25 Security Goals (0010) ___________________________________________________________________ 25 Symmetric Algorithms (0010) _____________________________________________________________ 25 Advanced Encryption Standard (AES) (0010) _______________________________________________ 25 DES (0010) _________________________________________________________________________ 25 Triple DES (0010) ____________________________________________________________________ 25 Message Integrity and Digital Signatures (0010) ______________________________________ 25 Electronic Signaling (0010) _______________________________________________________________ 25 DSS? (0010)_________________________________________________________________________ 25 Message Authentication Code (0010) _______________________________________________________ 25 Message Integrity (0010) _________________________________________________________________ 25 Attacks on Hashing Functions (0010) _____________________________________________________ 25 Hashing Algorithms (0010) _____________________________________________________________ 25 One Way Hash (0010) _________________________________________________________________ 25 Disaster Recovery (DRP) and Business Continuity (BCP) (0010) (DAN?) _____________ 26 A Background for DRP and BCP (0011) ____________________________________________ 26 Classes of Disasters (0011) _______________________________________________________________ 26 Natural Disaster (0011) ________________________________________________________________ 26 Man Made Disaster (0011) _____________________________________________________________ 26 Disaster Recovery vs. Business Continuity (0010) (0011) _______________________________________ 26 BCP Keeps Ops Running (0011) _________________________________________________________ 26 DRP Restores Normal OPS (0011) _______________________________________________________ 26 Commonality (0011) __________________________________________________________________ 26 Identify Critical Business Functions (0011) ______________________________________________ 26 Identify Experts (0011) ______________________________________________________________ 26 Identify Possible Disaster Scenarios (0011) ______________________________________________ 26 BCP Development (0011) _________________________________________________________ 26 Backups and Off-Site Storage (0011) _______________________________________________________ 26 Document Strategy (0011) ________________________________________________________________ 26 Documentation (0011) ___________________________________________________________________ 26 Emergency Response (0011) ______________________________________________________________ 26 External Communications (0011) __________________________________________________________ 26 Fire Protection (0011) ___________________________________________________________________ 26 Identify Success Factors (0011) ____________________________________________________________ 26 Logistics and Supplies (0011) _____________________________________________________________ 26 Maintain the Plan (0011) _________________________________________________________________ 26 Organization awareness and Training (0011) _________________________________________________ 26 Personnel Notification (0011) _____________________________________________________________ 26 Project Team Management (0011)__________________________________________________________ 26 Senior Management Involvement (0011) ____________________________________________________ 26 Senior Management Support (0011) ________________________________________________________ 26 Simplify Critical Functions (0011) _________________________________________________________ 26 Software Escrow Agreements (0011) _______________________________________________________ 26 Utilities (0011) _________________________________________________________________________ 26 Backups and Off-Site Facilities (0010) ______________________________________________ 26 Backup Facility Alternatives (0010) ________________________________________________________ 26 Hot site (0010) _______________________________________________________________________ 26 Cold site (0010) ______________________________________________________________________ 26 Warm site (0010) _____________________________________________________________________ 26 Choosing a Software Backup Storage Facility (0010) ___________________________________________ 26 Employees and Working Environment (0010) ________________________________________________ 26 Business Impact Analysis (0010) ___________________________________________________ 26 Criticality Assessment (0011) _____________________________________________________________ 26 Defining the Resource Requirements (0011) __________________________________________________ 26 Identifying Key Players (0011) ____________________________________________________________ 26 Setting Maximum Tolerable Downtime (0011) ________________________________________________ 26 Threats (0011) (0010) ___________________________________________________________________ 26 Vulnerability Assessment (0011) ___________________________________________________________ 26 DRP and BCP Objectives (0010) ___________________________________________________ 26 Documentation (0010) ___________________________________________________________________ 26 Emergency Response (0010) ______________________________________________________________ 26 Maintenance (0010) _____________________________________________________________________ 26 Phase Breakdown (0010) _________________________________________________________________ 26 Prevention (0010) ______________________________________________________________________ 27 Recovery and Restoration (0010) __________________________________________________________ 27 Testing and Drills (0010) _________________________________________________________________ 27 DRP Development (0011) _________________________________________________________ 27 Facilitate External Communication (0011) ___________________________________________________ 27 Maintain Physical Security (0011)__________________________________________________________ 27 Personnel Identification (0011) ____________________________________________________________ 27 Prepare for Emergency Response (0011)_____________________________________________________ 27 Test Recovery Plan ______________________________________________________________ 27 Test Continuity Plan _____________________________________________________________ 27 Product Life Cycle (0010) ________________________________________________________ 27 Project Initiation Phase (0010) ____________________________________________________ 27 Threats (0010) __________________________________________________________________ 27 Law, Investigation, and Ethics (0010) __________________________________________ 28 Types of Law (0011) _____________________________________________________________ 28 Common Law _________________________________________________________________________ 28 Constitutional Law ______________________________________________________________________ 28 International Law _______________________________________________ Error! Bookmark not defined. Computer Crime Investigation (0010) ______________________________________________ 28 Admissibility of Evidence (0010) __________________________________________________________ 28 Collecting Evidence (0010) _______________________________________________________________ 28 Enticement and Entrapment (0010) _________________________________________________________ 28 Evidence Types (0010) __________________________________________________________________ 28 Best Evidence _______________________________________________________________________ 28 Hearsay Evidence ____________________________________________________________________ 28 Secondary Evidence ___________________________________________________________________ 28 Forensics (0010) _______________________________________________________________________ 28 Incident Handling (0010) _________________________________________________________________ 28 Incident Response Plan (0010) ____________________________________________________________ 28 Incident Response Team (0010) ___________________________________________________________ 28 Search and Seizure (0010) ________________________________________________________________ 29 Trial (0010) ___________________________________________________________________________ 29 Who should Perform Investigation (0010) ____________________________________________________ 29 Ethics (0010) ___________________________________________________________________ 29 General Ethics Discussion ________________________________________________________________ 29 Computer Ethics Institute ________________________________________________________________ 29 Internet Activities Board _________________________________________________________________ 29 ISC2 _________________________________________________________________________________ 29 Types of Attacks ________________________________________________________________ 29 Hacking (0010) ________________________________________________________________________ 29 Terrorist Attacks _______________________________________________________________________ 29 Military Attacks ________________________________________________________________________ 29 Intelligence Attacks _____________________________________________________________________ 29 Financial Attacks _______________________________________________________________________ 29 Business Attacks _______________________________________________________________________ 29 Grudge Attacks ________________________________________________________________________ 29 Recreation ____________________________________________________________________________ 29 Tools ________________________________________________________________________________ 29 Data Diddling ________________________________________________________________________ 29 Dumpster Diving _____________________________________________________________________ 29 Excessive Privilege ___________________________________________________________________ 29 IP Spoofing _________________________________________________________________________ 29 Password Sniffing ____________________________________________________________________ 29 Salami _____________________________________________________________________________ 29 Social Engineering ____________________________________________________________________ 29 Wiretapping _________________________________________________________________________ 29 Prosecution Problems ____________________________________________________________ 29 Investigation __________________________________________________________________________ 29 Evidence ___________________________________________________________________________ 29 Conducting Investigation _______________________________________________________________ 29 Incident Handling and Response _________________________________________________________ 29 What does an attacker look like? __________________________________________________ 29 Hackers (0011)_________________________________________________________________________ 29 Script Kiddies (0011) ____________________________________________________________________ 29 Virus Writers (0011) ____________________________________________________________________ 29 Phreakers (0011) _______________________________________________________________________ 29 Organization Liabilities and Ramifications (0010) ____________________________________ 29 Legal Liability _________________________________________________________________________ 29 Employee Suits ______________________________________________________________________ 29 Downstream Liability _________________________________________________________________ 29 Privacy Issues _________________________________________________________________________ 29 Electronic Communicat9ion Privacy Act of 1986 ____________________________________________ 29 Employee Monitoring _________________________________________________________________ 29 Gramm Leach Bliley Act 1999 __________________________________________________________ 29 Health Insurance Portability and Accountability Act (HIPPA) __________________________________ 29 Privacy Act of 1974 ___________________________________________________________________ 29 Transborder Information Flow ___________________________________________________________ 29 Security Principles ______________________________________________________________________ 29 Types of Law (0010) _____________________________________________________________ 29 International Laws ______________________________________________________________________ 28 Australia ____________________________________________________________________________ 28 United Kingdom _____________________________________________________________________ 28 Netherlands _________________________________________________________________________ 28 Administrative Law _____________________________________________________________________ 28 Civil Law _____________________________________________________________________________ 28 Criminal Law __________________________________________________________________________ 28 18 US Code 1029 (Credit Card Fraud) ____________________________________________________ 28 18 US Code 1030 (Computer Fraud and abuse) _____________________________________________ 28 18 US Code 2319 (Copyrights) __________________________________________________________ 28 18 US Code 2511 (Interception) _________________________________________________________ 28 18 US Code 2701 (Access to Electronic Info) _______________________________________________ 28 Child Pornography ____________________________________________________________________ 28 Computer Security Act of 1987 __________________________________________________________ 28 Mail Fraud __________________________________________________________________________ 28 Patriot Act __________________________________________________________________________ 28 Wire Fraud __________________________________________________________________________ 28 Federal Policies ________________________________________________________________________ 28 Computer Fraud and Abuse Act 1986 _____________________________________________________ 28 Economic Espionage act of 1996 _________________________________________________________ 28 Federal Sentencing Guidelines __________________________________________________________ 28 State Laws ____________________________________________________________________________ 28 Texas ______________________________________________________________________________ 28 Georgia ____________________________________________________________________________ 28 Florida _____________________________________________________________________________ 28 Maryland ___________________________________________________________________________ 28 Intellectual Property_____________________________________________________________________ 28 Copyright ___________________________________________________________________________ 28 Patent ______________________________________________________________________________ 28 Trade Secret _________________________________________________________________________ 28 Trademark __________________________________________________________________________ 28 Software Piracy ________________________________________________________________________ 28 Operations Security (0010) ___________________________________________________ 30 A General Concept (0011) ________________________________________________________ 30 Anti Virus Management (0011) ____________________________________________________________ 30 Backup of Critical Information (0011) ______________________________________________________ 30 Need to know (0011) ____________________________________________________________________ 30 Least Privilege (0011) ___________________________________________________________________ 30 Privileged Functions (0011) _______________________________________________________________ 30 Privacy (0011) _________________________________________________________________________ 30 Legal Requirements (0011) _______________________________________________________________ 30 Illegal Activities (0011) __________________________________________________________________ 30 Records Retention (0011) ________________________________________________________________ 30 Handling Sensitive Information (0011) ______________________________________________________ 30 Configuration Management and Media Control (0010) ________________________________ 30 Data Controls (Input and Output) __________________________________________________________ 30 Media Controls ________________________________________________________________________ 30 Operations Control (0010) ________________________________________________________ 30 Administrative Control __________________________________________________________________ 30 Clipping levels _______________________________________________________________________ 30 Job Rotation _________________________________________________________________________ 30 Least Privilege _______________________________________________________________________ 30 Mandatory Vacations __________________________________________________________________ 30 Need to Know _______________________________________________________________________ 30 Separation of Duties___________________________________________________________________ 30 Control Categories ______________________________________________________________________ 30 Due Care _____________________________________________________________________________ 30 Reacting to failures and recovering (0010) ___________________________________________ 30 Trusted Recovery (0010) _________________________________________________________________ 30 Operational Responsibility _______________________________________________________ 30 Deviation from Standards ________________________________________________________________ 30 Unscheduled Initial Program Loads _________________________________________________________ 30 Unusual or Unexplained Occurrence ________________________________________________________ 30 Software Backups (0010) _________________________________________________________ 30 Backups ______________________________________________________________________________ 30 Network Availability ____________________________________________________________________ 30 Physical Security (0010) _____________________________________________________ 31 Location Selection _______________________________________________________________ 31 Choose a Secure Location ________________________________________________________________ 31 Designate a Security Facility ______________________________________________________________ 31 Electrical Power and Environmental Issues (0010) ____________________________________ 31 Environmental Consideration (0010) ________________________________________________________ 31 Power Interference (0010) ________________________________________________________________ 31 UPS (0010) ___________________________________________________________________________ 31 Ventilation (0010) ______________________________________________________________________ 31 Water, Steam and Gas (0010) _____________________________________________________________ 31 Fire Detection and Suppression (0010) ______________________________________________ 31 Emergency Response (0010) ______________________________________________________________ 31 Fire Detection (0010) ____________________________________________________________________ 31 Fire Extinguishing Issues (0010) ___________________________________________________________ 31 Fire Prevention (0010) ___________________________________________________________________ 31 Fire Suppression(0010) __________________________________________________________________ 31 Fire Types (0010) ______________________________________________________________________ 31 Halon (0010) __________________________________________________________________________ 31 Water Sprinkler (0010) __________________________________________________________________ 31 Perimeter Security (0010) ________________________________________________________ 31 Entrance Protection (0010) _______________________________________________________________ 31 Facility Access (0010) ___________________________________________________________________ 31 Fencing (0010) _________________________________________________________________________ 31 Intrusion Detection (0010) ________________________________________________________________ 31 Lighting (0010) ________________________________________________________________________ 31 Locks (0010) __________________________________________________________________________ 31 Surveillance Devices (0010) ______________________________________________________________ 31 Physical Security Controls (0010) __________________________________________________ 31 Computing Area (0010) __________________________________________________________________ 31 Facility Construction (0010) ______________________________________________________________ 31 Facility Location (0010) _________________________________________________________________ 31 Hardware Backup (0010) _________________________________________________________________ 31 Security Management Practices (0010) _________________________________________ 32 Security Audit __________________________________________________________________ 32 Audit Trails ___________________________________________________________________________ 32 Anatomy of an Audit Record ____________________________________________________________ 32 Types of Audit Trail __________________________________________________________________ 32 Finding Trouble in Logs _______________________________________________________________ 32 Problem Management and Audit Trail _____________________________________________________ 32 Retaining Audit Logs __________________________________________________________________ 32 Protection of Audit Logs _______________________________________________________________ 32 Monitoring ____________________________________________________________________________ 32 Facilities Monitoring __________________________________________________________________ 32 Intrusion Detection ___________________________________________________________________ 32 Keystroke Monitoring _________________________________________________________________ 32 Penetration Testing ___________________________________________________________________ 32 Responding to Events _________________________________________________________________ 32 CERT? ___________________________________________________________________________ 32 Traffic and Trends Analysis _____________________________________________________________ 32 Violation Analysis ____________________________________________________________________ 32 Employee Management (0010) ____________________________________________________ 32 Operational and Administrative Controls (0011) _______________________________________________ 32 Background Checking (0011) ___________________________________________________________ 32 Background Checks and Security Clearance (0011) __________________________________________ 32 Employment Agreements (0011) _________________________________________________________ 32 Hiring and Termination Practice (0011) ___________________________________________________ 32 Job Description (0011) _________________________________________________________________ 32 Job Requirements (0011) _______________________________________________________________ 32 Job Rotation (0011) ___________________________________________________________________ 32 Job Specifications (0011) _______________________________________________________________ 32 Roles and Responsibilities (0011) ________________________________________________________ 32 Separation of Duties (0011) _____________________________________________________________ 32 Information Classification (0010) __________________________________________________ 32 Government vs Commercial model (CDS) ___________________________________________________ 32 Commercial Data Classification (0011) ____________________________________________________ 32 Governmental Data Classification (0011) __________________________________________________ 32 Management Responsibilities (0010) ________________________________________________ 32 Risk Calculation (0010) __________________________________________________________ 32 Dealing with Risk (0010) _________________________________________________________________ 32 Quantitative and Qualitative (0010) _________________________________________________________ 32 Selection of Countermeasures (0010) _______________________________________________________ 32 Risk Management (0010) _________________________________________________________ 32 Risk Analysis (0010) ____________________________________________________________________ 32 Risk Control (0011) _____________________________________________________________________ 32 Risk Identification (0011) ________________________________________________________________ 32 Roles and Responsibilities (0010) __________________________________________________ 32 DAA – need better name (CDS) ___________________________________________________________ 32 Data Custodian (0010) ___________________________________________________________________ 32 Data Owner (0010) _____________________________________________________________________ 32 ISSO (CDS) ___________________________________________________________________________ 32 Security Auditor (0010) __________________________________________________________________ 33 System Certifier (CDS) __________________________________________________________________ 33 Systems Administrator (CDS) _____________________________________________________________ 33 User (0010) ___________________________________________________________________________ 33 Security Control Types (0010) _____________________________________________________ 33 Administrative Controls (0011) ____________________________________________________________ 33 Change Controls (0011) __________________________________________________________________ 33 Media Controls (0011) ___________________________________________________________________ 33 Privileged Entity Controls (0011) __________________________________________________________ 33 Resource Protection (0011) _______________________________________________________________ 33 Trusted Recovery (0011) _________________________________________________________________ 33 Security Policies and Supporting Counterparts (0010) _________________________________ 33 Baselines (0010) _______________________________________________________________________ 33 Guidelines (0010) ______________________________________________________________________ 33 Procedures (0010) ______________________________________________________________________ 33 Security Policy (0010) ___________________________________________________________________ 33 Standards (0010) _______________________________________________________________________ 33 Threats (0010) (0011) Countermeasures_____________________________________________ 33 Employee Sabotage (0011) _______________________________________________________________ 33 Errors and Omissions (0011) ______________________________________________________________ 33 Fraud (0011) __________________________________________________________________________ 33 Hackers and Crackers (0011) ______________________________________________________________ 33 Industrial Espionage (0011) _______________________________________________________________ 33 Loss of Physical and Infrastructure Support (0011) ____________________________________________ 33 Malicious Code (0011) __________________________________________________________________ 33 Theft (0011) ___________________________________________________________________________ 33 Security Models and Architecture (0010) ________________________________________ 34 Architecture (0011) ______________________________________________________________ 34 Open and Closed Systems (0011) __________________________________________________________ 34 Protection Rings (0011) __________________________________________________________________ 34 Recovery Procedures (0011) ______________________________________________________________ 34 Security Modes (0011)___________________________________________________________________ 34 Trusted Security Base (0011)______________________________________________________________ 34 Operations Systems Security Mechanisms (0010) _____________________________________ 34 Process Isolation (0010)__________________________________________________________________ 34 Protection Rings (0010) __________________________________________________________________ 34 Reference Monitor (0010) ________________________________________________________________ 34 Security Kernel (0010)___________________________________________________________________ 34 Trusted Computing Base (0010) ___________________________________________________________ 34 Virtual Machine (0010) __________________________________________________________________ 34 Security Evaluation Criteria (0010) ________________________________________________ 34 Certification vs Accreditation (0010) (0011) __________________________________________________ 34 DITSCAP (0011) _____________________________________________________________________ 34 NIACAP (0011) ______________________________________________________________________ 34 Evaluation (0010) ______________________________________________________________________ 34 BS 7799 (DAN) ______________________________________________________________________ 34 Common Criteria (0010) (0011) _________________________________________________________ 34 European Information Technology Security Evaluation Criteria (ITSEC) (0011) ___________________ 34 Information Technology Security Evaluation Criteria (0010) ___________________________________ 34 ISO 17788 (DAN) ____________________________________________________________________ 34 Rainbow Series (OBE but..) (0010) _______________________________________________________ 34 Trusted Computer System Evaluation Criteria (0010) (0011) ___________________________________ 34 Trusted Network Interpretation (0011) ____________________________________________________ 34 Security Models (0010) Some Belong in Access Control? _______________________________ 34 Integrity VS Privacy Which model is which (CDS) ____________________________________________ 34 Access Matrix (0010) (0011) ______________________________________________________________ 34 Bell – LaPadula (0010) __________________________________________________________________ 34 Biba (0010) ___________________________________________________________________________ 34 Brewer and Nash Model (0010) ____________________________________________________________ 34 Clark – Wilson (0010) ___________________________________________________________________ 34 Graham – Denning (0010) ________________________________________________________________ 34 Harrison – Ruszzo – Ulman (0010) _________________________________________________________ 34 Information Flow Model (0010) ___________________________________________________________ 34 Non-Interference (0010) _________________________________________________________________ 34 State Machines (0010) ___________________________________________________________________ 34 Take Grant (0011) ______________________________________________________________________ 34 System Components (0010) (See the Big Computer) Early chapter? _____________________ 34 Central Processing Unit (0010) ____________________________________________________________ 34 Data Access Storage (0010) _______________________________________________________________ 34 Firmware _____________________________________________________________________________ 34 General Architecture of Systems (Von Neumann Bit) (0010) _____________________________________ 34 Hardware _____________________________________________________________________________ 34 ISO Model 7 layer ? (CDS) _______________________________________________________________ 34 Operating States (0010) __________________________________________________________________ 34 Pointers etc (CDS) ______________________________________________________________________ 34 Processing Instructions (0010) _____________________________________________________________ 35 Software ______________________________________________________________________________ 35 Storage and Memory Types (0010) _________________________________________________________ 35 Virtual Storage (0010) ___________________________________________________________________ 35 Telecommunications and Network Security (0010) ________________________________ 36 Network Types (0011)____________________________________________________________ 36 Local Area (0011) ______________________________________________________________________ 36 Wide Area (0011) ______________________________________________________________________ 36 Cables and Data Transmission Types (0010) _________________________________________ 36 802-11 (CDS)__________________________________________________________________________ 36 Asynchronous and Synchronous (0010) _____________________________________________________ 36 Broadband and Base band (0010) __________________________________________________________ 36 Cable Issues (0010) _____________________________________________________________________ 36 Coaxial Cable (0010) ____________________________________________________________________ 36 Fiber (0010) ___________________________________________________________________________ 36 Fire Ratings (0010) _____________________________________________________________________ 36 Microwave (CDS) ______________________________________________________________________ 36 Signals (0010) _________________________________________________________________________ 36 Transmission Methods (0010) _____________________________________________________________ 36 Twisted Pair Cable (0010) ________________________________________________________________ 36 Fault Tolerance Methods and Mechanisms (0010) ____________________________________ 36 RAID (0010) __________________________________________________________________________ 36 Clustering (0010) _______________________________________________________________________ 36 Backup (0010) _________________________________________________________________________ 36 LAN Technologies (0010) _________________________________________________________ 36 Media Access Technologies (0010) _________________________________________________________ 36 Ethernet (0010) ______________________________________________________________________ 36 Polling (0010)) _______________________________________________________________________ 36 Token (0010) ________________________________________________________________________ 36 Network Topologies (0010) _______________________________________________________________ 36 Bus (0010) __________________________________________________________________________ 36 Ring (0010) _________________________________________________________________________ 36 Star (0010) __________________________________________________________________________ 36 Protocols (0010)________________________________________________________________________ 36 Address Resolution Protocol (ARP) (0010) _________________________________________________ 36 Boot Protocol (0010) __________________________________________________________________ 36 Internet Control Message Protocol (ICMP) (0010) ___________________________________________ 36 Reverse Address Resolution Protocol (RARP) (0010) ________________________________________ 36 Network Devices and Services (0010) _______________________________________________ 36 Bridge (0010) __________________________________________________________________________ 36 Brouter (0010) _________________________________________________________________________ 36 Firewalls (0010) ________________________________________________________________________ 36 Administration (0010) _________________________________________________________________ 36 Architecture (0010) ___________________________________________________________________ 36 Packet Filter (0010) ___________________________________________________________________ 36 Proxy Firewall (0010) _________________________________________________________________ 36 State Firewall (0010) __________________________________________________________________ 36 Gateway (0010) ________________________________________________________________________ 36 Network Services (0010) _________________________________________________________________ 36 DNS (0010) _________________________________________________________________________ 36 NAT (0010) _________________________________________________________________________ 36 Remote Connection (0010) _______________________________________________________________ 36 CHAP (0010) ________________________________________________________________________ 37 EAP (0010) _________________________________________________________________________ 37 PAP (0010) _________________________________________________________________________ 37 PPP (0010) __________________________________________________________________________ 37 SLIP (0010) _________________________________________________________________________ 37 Repeater (0010) ________________________________________________________________________ 37 Router (0010) __________________________________________________________________________ 37 Switches (0010) ________________________________________________________________________ 37 VLAN (0010)________________________________________________________________________ 37 VPN (0010) ___________________________________________________________________________ 37 IPSec (0010) ________________________________________________________________________ 37 L2TP (0010)_________________________________________________________________________ 37 PPTP (0010)_________________________________________________________________________ 37 Remote Access Methods and Technologies (0010) _____________________________________ 37 Remote Access (0010) ___________________________________________________________________ 37 Wireless Technology (0010) ______________________________________________________________ 37 Access Points (0010) __________________________________________________________________ 37 OSA and SKA (0010) _________________________________________________________________ 37 Spread Spectrum (0010) _______________________________________________________________ 37 SSID (0010) _________________________________________________________________________ 37 WAP (0010) _________________________________________________________________________ 37 Telecommunications _____________________________________________________________ 37 Cell Phone Clone (0010) _________________________________________________________________ 37 E-Mail Security (0011) __________________________________________________________________ 37 E-mail Monitoring (CDS) ______________________________________________________________ 37 E-mail Storage (CDS) _________________________________________________________________ 37 E-mail Privacy (CDS) _________________________________________________________________ 37 Facsimile Security (0011) ________________________________________________________________ 37 PBX Threat (0010)______________________________________________________________________ 37 PBX Fraud (0011) ____________________________________________________________________ 37 PBX Abuse (0011) ____________________________________________________________________ 37 TCP/IP Model (0010) ____________________________________________________________ 37 Extranets (0010)________________________________________________________________________ 37 Internet Protocol (0010) __________________________________________________________________ 37 Intranets (0010) ________________________________________________________________________ 37 ISO/OSI Seven Layers (0011) _____________________________________________________________ 37 Physical Layer _______________________________________________________________________ 37 Data Link ___________________________________________________________________________ 37 Network ____________________________________________________________________________ 37 Transport ___________________________________________________________________________ 37 Session _____________________________________________________________________________ 37 Presentation _________________________________________________________________________ 37 Application _________________________________________________________________________ 37 Networks (0010) _______________________________________________________________________ 37 Telecommunications Protocols and Devices (0010) ____________________________________ 37 ATM (0010) ___________________________________________________________________________ 37 Cable Modems (0010) ___________________________________________________________________ 37 CSU/DSU (0010) _______________________________________________________________________ 37 Dedicated Link (0010) ___________________________________________________________________ 37 DSL (0010) ___________________________________________________________________________ 37 FDDI (0010) __________________________________________________________________________ 38 Frame Relay (0010) _____________________________________________________________________ 38 HDLC (0010) __________________________________________________________________________ 38 ISDN (0010) __________________________________________________________________________ 38 Multiservice Access Technology (0010) _____________________________________________________ 38 Quality of Service (0010) ________________________________________________________________ 38 S/WAN (0010) _________________________________________________________________________ 38 SDLC (0010) __________________________________________________________________________ 38 SMDS (0010) __________________________________________________________________________ 38 SONET (0010) _________________________________________________________________________ 38 WAN Switching (0010) __________________________________________________________________ 38 X.25 (0010) ___________________________________________________________________________ 38 Items looking for home (0100) ________________________________________________ 39 CERT – Where does it go? ________________________________________________________ 39 Non-Computer FAX type stuff PBX? _______________________________________________ 39 Challenge of Survivability (0100) __________________________________________________ 39 Compare and Contrast Security and Survivability (0100) ________________________________________ 39 Define Survivability (0100) _______________________________________________________________ 39 Describe Layered approaches (0100) ________________________________________________________ 39 Identify and define the components of the Information Security Model – Security Model, Information security Properties and Security measures. (0100) ____________________________________________________ 39 Asset and Risk Management (0100) ________________________________________________ 39 Policy Formulation and Implementation (0100) ______________________________________ 39 TCP/IP Security (0100) __________________________________________________________ 39 Threats Vulnerabilities and Attacks (0100) __________________________________________ 39 Host System Hardening (0100) ____________________________________________________ 39 Secure Network Infrastructure (0100) ______________________________________________ 39 Deploying Firewalls (0100)________________________________________________________ 39 Secure Remote Access (0100) ______________________________________________________ 39 Writing a Security Plan (CDS/?) ___________________________________________________ 39 Reliability and Availability Calculations ____________________________________________ 39 MTTR _______________________________________________________________________________ 39 MTBF _______________________________________________________________________________ 39 Valuing Assets (ISSA and CDS Class Notes) _________________________________________ 39 Introduction to Information Assurance (CDS) McCumber Model (CDS) International View (DAN) BS 7799 (DAN) ISO 17799 (DAN) Assurance Management Confidentiality (CDS) (0011) Integrity (CDS) (0011) Availability (CDS) (0011) Access Control (0010) Access Control Administration (0010) Centralized Systems (0010) Diameter (0010) RADIUS (0010) TACAC (0010) Decentralized Systems (0010) Access Control Models and Techniques (0010) Categories of Access Control (0011) System Access Controls (0011) Data Access Controls (0011) Access Control Techniques (0010) Capability Tables and ACL (0010) Content Dependent Access Control (0010) Restricted Interfaces (0010) DAC (0010) MAC (0010) RBAC (0010) Concepts of Access Control (0011) Control Types (0011) Access Control Services (0011) Identification and Authentication (0010) Authentication (0010) Biometrics (0010) Cognitive Password (0010) Cryptographic Keys (0010) Memory Cards (0010) One Time Passwords (0010) Passphrase (0010) Passwords (0010) Smart Cards (0010) Authorization (0010) Stage Setting Intrusion Detection Systems (0010) (0100) Behavior Based (0010) Host Based (0010) Network Based (0010) Signature Based (0010) Pros and Cons (0010) Single Sign-On Technology (0010) Directory Services (0010) KERBEROS (0010) SESAME (0010) Thin Clients? (0010) Unauthorized Access Control and Attacks (0010) Unauthorized Disclosure of Information (0010) Emanation Security (WAP and TEMPEST) (0010) Attack Types (0010) Network Attacks Syn Flood ICMP Flood UDP Flood SMURF Fraggle Teardrop Spoofing Penetration Testing (Right Place?) (0010) Applications and Systems Development (0010) Knowledge Based Systems and Intelligence (0010) (0011) Artificial Neural Network (0010) (IGGY) Expert Systems (0010) Application Security Controls Abstraction (0011) Accountability (0011) Data Hiding (0011) Defense in Depth (0011) Hardware Segmentation (0011) Process Isolation (0011) Reference Monitor (0011) Security Kernel (0011) Separation of Privilege (0011) Service Level Agreements (0011) Supervisor and User Modes (0011) System High Mode (0011) Data and Information Security (0011) (CDS) Primary Storage (0011) Real and Virtual (0011) Secondary Storage (0011) Databases (0010) Aggregation and Inference (0010) Concurrency Issues (0010) Data Mine (0010) Data Warehouse (0010) Database Interface Languages (0010) Database Security Distributed Data Model (0010) Hierarchical Database (0010) Network Database Management System (0010) Object Oriented Database (0010) Relational Data Model (0010) Database Dictionary (0010) Structured Query Language (0010) Distributed Computing (0010) Distributed Applications (0011) Agents (0011) Applets (0011) Security in Distributed Systems (0011) Examples to Discuss (CDS) ActiveX (0010) CGI (0010) COM an DCOM (0010) Cookies (0010) Enterprise Java Bean (0010) Java Applet (0010) OLE (0010) ORB and CORBA (0010) Malicious Actions (0010) Brute Force (0011) Denial of Service (0010) Distributed Denial of Service Dictionary attack (0011) Eavesdropping (0011) Hidden Code (0011) Inference (0011) Logic Bomb (0010) Pseudo Flaw (0011) Remote Maintenance (0011) Smurf Attacks (0010) Sniffing (0011) Social Engineering (0011) Timing Attacks (0010) Traffic Analysis (0011) Trojan Horse (0010) Virus (0010) Worm (0010) Object Oriented Environments and Principles (0010) Abstraction (0010) Application Threat(s (0010) Classes and Objects (0010) Polyinstantiation (0010) Polymorphism (0010) Project development (0010) Software Lifecycle (0010) Software Development Models (0010) Acceptance Testing (0010) Accreditation (0011) Certification (0011) Change Management (0011) Code (0011) Code Review (0011) Conceptual definition (0011) Configuration Management (0011) Design (0011) Disposal (0010) Functional Design Analysis and Planning (0010) Functional Requirements (0011) Functional Specifications (0011) Implementation (0010) Maintenance (0010) (0011) Operations (0010) Project Initiation (0010) Software Development (0010) System Design Specification (0010) System Test (0011) Writing Secure Code (???) Awareness, Training and Education (CDS/VIC) Tools (CDS) Standards Cryptography (0100) (0010) Stuff from my book? Cryptography Defined Classes of Ciphers Cipher Types (0010) Asymmetric Cryptography (0010) Block Cipher (0010) Kerckhoff Principle (0010) Key Escrow (0010) Stream Cipher (0010) Substitution Cipher (0010) Symmetric Cryptography (0010) Transposition Cipher (0010) Key Clusters (0011) Encryption and Decryption (0011) Work Factor Force times effort and work (0011) Attacks (0010) Adaptive Chosen Plaintext Attack (0010) Analytic Attack (0010) (0011) Brute Force (0011) Implementation Attacks (0011) Known Plaintext Attack (0010) Man in the Middle Attack (0010) Statistical Attacks (0011) Specific Methods of Attack Chosen Ciphertext Attack (0010) Chosen Plaintext Attack (0010) Ciphertext – Only Attack (0010) Cryptographic Applications (0010) Encryption at Different Layers (0010) One Time Pad (0010) Public Key Infrastructure (PKI) (0010) Certificate Revocation List (CRL) (0010) Certification Authority (CA) (0010) PKI Steps (0010) Registration Authority (0010) Cryptographic Protocols (0010) Internet Security (0010) HTTPS (0010) IPSec (0010) S/MIME (0010) Secure Hypertext Transfer Protocol (S-HTTP) (0010) Secure Sockets Layer (SSL) (0010) SET (0010) SSH2 (0010) Message Security Protocol (MSP) (0010) Pretty Good Privacy (PGP) (0010) Privacy Enhanced Mail (PEM) (0010) Cryptography Definitions (0010) Attacks (0010) Keys and Text (0010) Keyspace (0010) Spy Cipher (0010) Steganography (0010) Strength of Crypto Systems (0010) Hybrid Approaches (0010) Asymmetric Algorithm (0010) Diffie Hellman Key Exchange (0010) El Gamal (0010) Elliptic Curve Cryptosystems (ECC) (0010) Data Encryption (0010) Key Management (0010) Security Goals (0010) Symmetric Algorithms (0010) Advanced Encryption Standard (AES) (0010) DES (0010) Triple DES (0010) Key Issues (0011) Key Change (0011) Key Control (0011) Key Disposal (0011) Key Distribution (0011) Key Generation (0011) Key Installation (0011) Key Escrow and Recovery (0011) Key Storage (0011) Message Authentication Digital Signatures Message Digests Non Repudiation Message Integrity and Digital Signatures (0010) Electronic Signaling (0010) DSS? (0010) Message Authentication Code (0010) Message Integrity (0010) Attacks on Hashing Functions (0010) Hashing Algorithms (0010) One Way Hash (0010) Disaster Recovery (DRP) and Business Continuity (BCP) (0010) (DAN?) A Background for DRP and BCP (0011) Classes of Disasters (0011) Natural Disaster (0011) Man Made Disaster (0011) Disaster Recovery vs. Business Continuity (0010) (0011) BCP Keeps Ops Running (0011) DRP Restores Normal OPS (0011) Commonality (0011) Identify Critical Business Functions (0011) Identify Experts (0011) Identify Possible Disaster Scenarios (0011) BCP Development (0011) Backups and Off-Site Storage (0011) Document Strategy (0011) Documentation (0011) Emergency Response (0011) External Communications (0011) Fire Protection (0011) Identify Success Factors (0011) Logistics and Supplies (0011) Maintain the Plan (0011) Organization awareness and Training (0011) Personnel Notification (0011) Project Team Management (0011) Senior Management Involvement (0011) Senior Management Support (0011) Simplify Critical Functions (0011) Software Escrow Agreements (0011) Utilities (0011) Backups and Off-Site Facilities (0010) Backup Facility Alternatives (0010) Hot site (0010) Cold site (0010) Warm site (0010) Choosing a Software Backup Storage Facility (0010) Employees and Working Environment (0010) Business Impact Analysis (0010) Criticality Assessment (0011) Defining the Resource Requirements (0011) Identifying Key Players (0011) Setting Maximum Tolerable Downtime (0011) Threats (0011) (0010) Vulnerability Assessment (0011) DRP and BCP Objectives (0010) Documentation (0010) Emergency Response (0010) Maintenance (0010) Phase Breakdown (0010) Prevention (0010) Recovery and Restoration (0010) Testing and Drills (0010) DRP Development (0011) Facilitate External Communication (0011) Maintain Physical Security (0011) Personnel Identification (0011) Prepare for Emergency Response (0011) Test Recovery Plan Test Continuity Plan Product Life Cycle (0010) Project Initiation Phase (0010) Threats (0010) Law, Investigation, and Ethics (0010) Types of Law (0011) (0010) Administrative Law Common Law Constitutional Law Civil Law Intellectual Property Copyright Patent Trade Secret Trademark Criminal Law 18 US Code 1029 (Credit Card Fraud) 18 US Code 1030 (Computer Fraud and abuse) 18 US Code 2319 (Copyrights) 18 US Code 2511 (Interception) 18 US Code 2701 (Access to Electronic Info) Child Pornography Computer Security Act of 1987 Mail Fraud Patriot Act Wire Fraud Federal Policies Computer Fraud and Abuse Act 1986 Economic Espionage act of 1996 Federal Sentencing Guidelines State Laws Texas Georgia Florida Maryland International Laws Australia United Kingdom Netherlands Software Piracy Computer Crime Investigation (0010) Admissibility of Evidence (0010) Collecting Evidence (0010) Enticement and Entrapment (0010) Evidence Types (0010) Best Evidence Hearsay Evidence Secondary Evidence Forensics (0010) Incident Handling (0010) Incident Response Plan (0010) Incident Response Team (0010) Search and Seizure (0010) Trial (0010) Who should Perform Investigation (0010) Ethics (0010) General Ethics Discussion Computer Ethics Institute Internet Activities Board ISC2 Types of Attacks Hacking (0010) Terrorist Attacks Military Attacks Intelligence Attacks Financial Attacks Business Attacks Grudge Attacks Recreation Tools Data Diddling Dumpster Diving Excessive Privilege IP Spoofing Password Sniffing Salami Social Engineering Wiretapping Prosecution Problems Investigation Evidence Conducting Investigation Incident Handling and Response What does an attacker look like? Hackers (0011) Script Kiddies (0011) Virus Writers (0011) Phreakers (0011) Organization Liabilities and Ramifications (0010) Legal Liability Employee Suits Downstream Liability Privacy Issues Electronic Communicat9ion Privacy Act of 1986 Employee Monitoring Gramm Leach Bliley Act 1999 Health Insurance Portability and Accountability Act (HIPPA) Privacy Act of 1974 Transborder Information Flow Security Principles Types of Law (0010) Operations Security (0010) A General Concept (0011) Anti Virus Management (0011) Backup of Critical Information (0011) Need to know (0011) Least Privilege (0011) Privileged Functions (0011) Privacy (0011) Legal Requirements (0011) Illegal Activities (0011) Records Retention (0011) Handling Sensitive Information (0011) Configuration Management and Media Control (0010) Data Controls (Input and Output) Media Controls Operations Control (0010) Administrative Control Clipping levels Job Rotation Least Privilege Mandatory Vacations Need to Know Separation of Duties Control Categories Due Care Reacting to failures and recovering (0010) Trusted Recovery (0010) Operational Responsibility Deviation from Standards Unscheduled Initial Program Loads Unusual or Unexplained Occurrence Software Backups (0010) Backups Network Availability Physical Security (0010) Location Selection Choose a Secure Location Designate a Security Facility Electrical Power and Environmental Issues (0010) Environmental Consideration (0010) Power Interference (0010) UPS (0010) Ventilation (0010) Water, Steam and Gas (0010) Fire Detection and Suppression (0010) Fire Types (0010) Fire Prevention (0010) Fire Detection (0010) Emergency Response (0010) Fire Extinguishing Issues (0010) Fire Suppression (0010) Halon (0010) Water Sprinkler (0010) Perimeter Security (0010) Facility Access (0010) Perimeter Protection (0010) Fencing (0010) Intrusion Detection (0010) Lighting (0010) Locks (0010) Surveillance Devices (0010) Physical Security Controls (0010) Computing Area (0010) Facility Construction (0010) Facility Location (0010) Hardware Backup (0010) Security Management Practices (0010) Security Audit Audit Trails Anatomy of an Audit Record Types of Audit Trail Finding Trouble in Logs Problem Management and Audit Trail Retaining Audit Logs Protection of Audit Logs Monitoring Facilities Monitoring Intrusion Detection Keystroke Monitoring Penetration Testing Responding to Events CERT? Traffic and Trends Analysis Violation Analysis Employee Management (0010) Operational and Administrative Controls (0011) Background Checking (0011) Background Checks and Security Clearance (0011) Employment Agreements (0011) Hiring and Termination Practice (0011) Job Description (0011) Job Requirements (0011) Job Rotation (0011) Job Specifications (0011) Roles and Responsibilities (0011) Separation of Duties (0011) Information Classification (0010) Government vs Commercial model (CDS) Commercial Data Classification (0011) Governmental Data Classification (0011) Management Responsibilities (0010) Risk Calculation (0010) Dealing with Risk (0010) Quantitative and Qualitative (0010) Selection of Countermeasures (0010) Risk Management (0010) Risk Analysis (0010) Risk Control (0011) Risk Identification (0011) Roles and Responsibilities (0010) DAA – need better name (CDS) Data Custodian (0010) Data Owner (0010) ISSO (CDS) Security Auditor (0010) System Certifier (CDS) Systems Administrator (CDS) User (0010) Security Control Types (0010) Administrative Controls (0011) Change Controls (0011) Media Controls (0011) Privileged Entity Controls (0011) Resource Protection (0011) Trusted Recovery (0011) Security Policies and Supporting Counterparts (0010) Baselines (0010) Guidelines (0010) Procedures (0010) Security Policy (0010) Standards (0010) Threats (0010) (0011) Countermeasures Employee Sabotage (0011) Errors and Omissions (0011) Fraud (0011) Hackers and Crackers (0011) Industrial Espionage (0011) Loss of Physical and Infrastructure Support (0011) Malicious Code (0011) Theft (0011) Security Models and Architecture (0010) Architecture (0011) Open and Closed Systems (0011) Protection Rings (0011) Recovery Procedures (0011) Security Modes (0011) Trusted Security Base (0011) Operations Systems Security Mechanisms (0010) Process Isolation (0010) Protection Rings (0010) Reference Monitor (0010) Security Kernel (0010) Trusted Computing Base (0010) Virtual Machine (0010) Security Evaluation Criteria (0010) Certification vs Accreditation (0010) (0011) DITSCAP (0011) NIACAP (0011) Evaluation (0010) BS 7799 (DAN) Common Criteria (0010) (0011) European Information Technology Security Evaluation Criteria (ITSEC) (0011) Information Technology Security Evaluation Criteria (0010) ISO 17788 (DAN) Rainbow Series (OBE but..) (0010) Trusted Computer System Evaluation Criteria (0010) (0011) Trusted Network Interpretation (0011) Security Models (0010) Some Belong in Access Control? Integrity VS Privacy Which model is which (CDS) Access Matrix (0010) (0011) Bell – LaPadula (0010) Biba (0010) Brewer and Nash Model (0010) Clark – Wilson (0010) Graham – Denning (0010) Harrison – Ruszzo – Ulman (0010) Information Flow Model (0010) Non-Interference (0010) State Machines (0010) Take Grant (0011) System Components (0010) (See the Big Computer) Early chapter? Central Processing Unit (0010) Data Access Storage (0010) Firmware General Architecture of Systems (Von Neumann Bit) (0010) Hardware ISO Model 7 layer ? (CDS) Operating States (0010) Pointers etc (CDS) Processing Instructions (0010) Software Storage and Memory Types (0010) Virtual Storage (0010) Telecommunications and Network Security (0010) Network Types (0011) Local Area (0011) Wide Area (0011) Cables and Data Transmission Types (0010) 802-11 (CDS) Asynchronous and Synchronous (0010) Broadband and Base band (0010) Cable Issues (0010) Coaxial Cable (0010) Fiber (0010) Fire Ratings (0010) Microwave (CDS) Signals (0010) Transmission Methods (0010) Twisted Pair Cable (0010) Fault Tolerance Methods and Mechanisms (0010) RAID (0010) Clustering (0010) Backup (0010) LAN Technologies (0010) Media Access Technologies (0010) Ethernet (0010) Polling (0010)) Token (0010) Network Topologies (0010) Bus (0010) Ring (0010) Star (0010) Protocols (0010) Address Resolution Protocol (ARP) (0010) Boot Protocol (0010) Internet Control Message Protocol (ICMP) (0010) Reverse Address Resolution Protocol (RARP) (0010) Network Devices and Services (0010) Bridge (0010) Brouter (0010) Firewalls (0010) Administration (0010) Architecture (0010) Packet Filter (0010) Proxy Firewall (0010) State Firewall (0010) Gateway (0010) Network Services (0010) DNS (0010) NAT (0010) Remote Connection (0010) CHAP (0010) EAP (0010) PAP (0010) PPP (0010) SLIP (0010) Repeater (0010) Router (0010) Switches (0010) VLAN (0010) VPN (0010) IPSec (0010) L2TP (0010) PPTP (0010) Remote Access Methods and Technologies (0010) Remote Access (0010) Wireless Technology (0010) Access Points (0010) OSA and SKA (0010) Spread Spectrum (0010) SSID (0010) WAP (0010) Telecommunications Cell Phone Clone (0010) E-Mail Security (0011) E-mail Monitoring (CDS) E-mail Storage (CDS) E-mail Privacy (CDS) Facsimile Security (0011) PBX Threat (0010) PBX Fraud (0011) PBX Abuse (0011) TCP/IP Model (0010) Extranets (0010) Internet Protocol (0010) Intranets (0010) ISO/OSI Seven Layers (0011) Physical Layer Data Link Network Transport Session Presentation Application Networks (0010) Telecommunications Protocols and Devices (0010) ATM (0010) Cable Modems (0010) CSU/DSU (0010) Dedicated Link (0010) DSL (0010) FDDI (0010) Frame Relay (0010) HDLC (0010) ISDN (0010) Multiservice Access Technology (0010) Quality of Service (0010) S/WAN (0010) SDLC (0010) SMDS (0010) SONET (0010) WAN Switching (0010) X.25 (0010) Items looking for home (0100) CERT – Where does it go? Non-Computer FAX type stuff PBX? Challenge of Survivability (0100) Compare and Contrast Security and Survivability (0100) Define Survivability (0100) Describe Layered approaches (0100) Identify and define the components of the Information Security Model – Security Model, Information security Properties and Security measures. (0100) Asset and Risk Management (0100) Policy Formulation and Implementation (0100) TCP/IP Security (0100) Threats Vulnerabilities and Attacks (0100) Host System Hardening (0100) Secure Network Infrastructure (0100) Deploying Firewalls (0100) Secure Remote Access (0100) Writing a Security Plan (CDS/?) Reliability and Availability Calculations MTTR MTBF Valuing Assets (ISSA and CDS Class Notes)