Main Y4 SemII Networ..

INSTITUTE EXAMINATIONS – ACADEMIC YEAR 2012-2013
SEMESTER II MAINEXAMINATION
FACULTY OF ENGINEERING
COMPUTER AND INFORMATION TECHNOLOGY
FOUR YEAR CEIT SEMESTER I FULL TIME
CIT3324: NETWORK SECURITY
DATE:
TIME: 2 HOURS
MAXIMUM MARKS = 60
INSTRUCTIONS
1.
This paper contains ONE (1) question in SECTION A and THREE (3) questions in
SECTION B
2.
Answer ALL questions in SECTION Aandany TWO (2) questions from SECTIONB
3.
No written materials allowed.
4.
Write all your answers in the answer booklet provided.
5.
Do not forget to write your Registration Number.
6.
Do not write any answers on this question paper.
SECTION A
Question One a) i. ii.
iii.
iv.
Mention any two network security basic components
Mention any two independent malicious softwares
Mention any two stages in worm’s development
Mention any two cryptic key systems
[1 × 2]
[1 × 2]
[1 × 2]
[1 × 2]
[1 × 2] v.
Mention anytwo elements of the security life cycle b) i. Explain the reasons why security is a crucial factor in the Internet
Environment [5] ii.
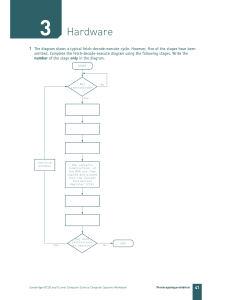
With the help of a sketch, describe a network security model iii.
Explain the operation of the trapdoormalware iv.
Describe the operation of a topological worm
[10]
[2]
[3]
SECTION B
Question One a) Describe the characteristics of the Denial of Service according to the CERT
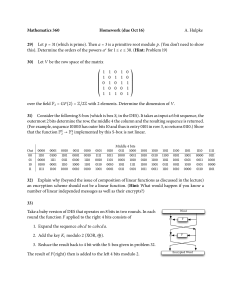
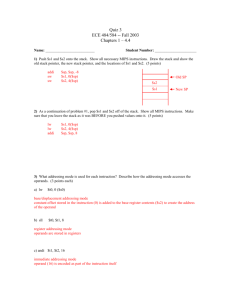
Threat model [5] b) Briefly, describe the transposition and substitution ciphers [5] c) Givenans-boxresults as in the table below, find the output for the input of
27. [10]
Middle 4 bits of input
S
5
0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 1101 1110 1111
00 0010 1100 0100 0001 0111 1010 1011 0110 1000 0101 0011 1111 1101 0000 1110 1001
Outer
01 1110 1011 0010 1100 0100 0111 1101 0001 0101 0000 1111 1010 0011 1001 1000 0110 bits
10 0100 0010 0001 1011 1010 1101 0111 1000 1111 1001 1100 0101 0110 0011 0000 1110
11 1011 1000 1100 0111 0001 1110 0010 1101 0110 1111 0000 1001 1010 0100 0101 0011
Question Two a) Discuss the major benefits of an asymmetric cryptosystem [5] b) Discuss how the public key system addresses the non-repudiation issues [5] c) Given an RSA system with two prime numbers of 47 and 71, and the public key of 79, calculate the private key [10]
Question Three a) Briefly give the meaning of firewall security system [5] b) Alice and Bob are business partners. They always correspond their business deals using the Internet, and they are looking for a network security specialist to help them with the knowledge of solutions that would best secure their online communications, because they have been alerted that Internet is a very insecure environment for communicating sensitive matters.Assuming you won this contract, propose them to use the IPSec security system and discuss its operation. [15]