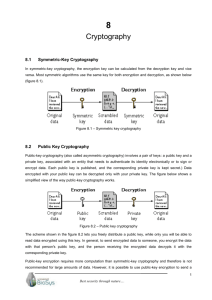
Course outline Data security and Cryptography
advertisement

School of Computer Science and Software Engineering Faculty of Information Technology Monash University, Caulfield CSE 5210 Advances in Information Security PREREQUISITES: COT 4230, COT 4350 or Introduction to data communications and introduction to database systems STREAM: Distributed Systems, Information Storage and Retrieval OBJECTIVES: On completion of this subject, the student should understand the factors influencing the security of data in distributed systems, especially transaction processing systems. OVERVIEW: The security of data is vital to the organisation owning the data. Modern transaction processing systems must also provide for the privacy of other parties to the transaction. This subject addresses these issues. TEACHING METHODS: 52 nominal hours of student contact consisting of lectures and seminars ASSESSMENT: Assignments 50%; a paper 50%. SYLLABUS: Secure computer systems. Privacy; Information Systems Security. The security requirements of parties to a transaction: privacy, proof of identity, ownership, license, signature, notarisation, date of action, certification of origination and/or receipt. Cryptology: types of cryptoanalytic attacks on a cryptosystem; cryptographic systems; protocols. Secret key systems: information theory; one time pads; DES; pseudo random number generators and other current developments. Public key systems: one way functions; public-key distribution; RSA cryptosystems; discrete logarithm systems; zero knowledge proofs and other current developments. Applications: open channel key exchange; digital signature; user identification; electronic funds transfer; the electronic wallet; traceable versus untraceable EFT; contract negotiation and signature; smart card applications. REFERENCES: Anderson, R (2001), Security Engineering : a guide to building dependable distributed systems, John Wiley. Brassard, G. (1988), Modern cryptology a tutorial, Lecture notes in computer science number 325, SpringerVerlang. Caelli, W.; Longley, D.; Shain, M. (1989), Information Security for Managers, Stockton Press. Davis, D. W.; Price, W. L. (1989), Security for computer networks (second edition), John Wiley & Sons, Chichester. Dening, D. E. R. (1983), Cryptography and data security, Addison Wesley, Reading, MA. Kahn, D. (1967), The codebreakers, New York,: MacMillan; (abridged edition, (1974) Signet, New York) Knuth, D. (1981), The art of computer programming 2nd ed. volume 2 seminumerical algorithms, Reading MA.: Addison-Wesley. Salomaa, Arto (1990), Public-Key Cryptography, Springer-Verlag, (EATCS Monographs on Theoretical Computer Science Volume 23). Schneier, B (1995), Applied cryptography : Protocols, algorithms, and source code in C (2nd. Ed.), John Wiley & Sons Inc. Seberry, J.;Pieprzyk, J. (1989), Cryptography: an introduction to computer security, Prentice Hall. \\yagi\usr\cse5210\COURSE.DOC February 12, 2016 16:36.