COMP 343-443: Computer Networks
advertisement

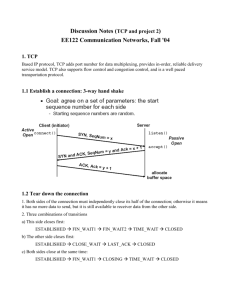
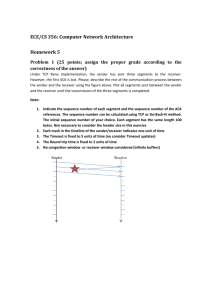
1. (a) (b) (c) COMP 343-443: Computer Networks Key to Midterm Write the common and distinguishing features of Go-Back-N protocol Selective Repeat, and TCP (20 points) Solution: Common Features: All of them use pipelining, provide congestion control and flow control because they all are Transport Layer, reliable protocols. In addition, they use time-out to detect lost packets and use sequence numbers and checksum to detect duplicate packets and errors respectively. Thirdly, the sender always buffers outgoing segments. Go-Back-N: (1) Sender uses one timer (2) Receiver sends cumulative acknowledgment, (3) After timeout, sender resends all segments starting from the last segment that was correctly acknowledged. (3) Receiver discards out-of-order segments, (4) Receiver does not buffer. Selective Repeat: (1) Sender uses multiple timers, (2) Receiver acknowledges each segment individually, (3) Sender resends segment for which timeout occurs, (4) Receiver buffers out-of-order segments. TCP: (1) A hybrid between GBN and SR. (2) Implementations can have buffering at the receiver side or not, (3) Has several special features not present in either GBN or SR such as Fast Transmit, and Delayed Acknowledgment, (4) Cumulative acknowledgement. A key difference between TCP and GBN is that TCP sender will resend only segment n if the timer for it expires, whereas GBN will resend segments n, n+1, etc. 2. It is common for an institutional network to be based on a high-speed LAN. Suppose that a router in this network is connected to a router in the public Internet by means of a 3 Mbps access link. Suppose further that the LAN runs at 12 Mbps. Users at the institutional network are accessing the web servers in the Internet at the rate of 30 requests per second and the average request size is 100 Kbits. (a) Compute the traffic intensities at LAN and the access link and comment on the values. (b) Suppose you add an institutional web cache whose hit rate is 0.5, how are the traffic intensities affected? (c) Assuming an Internet delay of 2 seconds (round-trip time between access link router and an outside webserver on an average), and 20 millisecond-delay for requests that can be satisfied by the web cache, compute the average delay for a cache hit rate of h, where 0<h<1. (a) Solution: Traffic intensity at LAN is: (30 requests/sec) * (100 Kbits/request)/(12 Mbps) = 0.25 Traffic intensity at access link is: (30 requests/sec) * (100 Kbps/request)/(3Mbps)=1.0 Traffic intensity at LAN is acceptable. However, at the access link it is too high and will cause a serious degradation in performance. (b) Cache hit rate of 0.5 means, that on an average, 50% of the requests will be served by the LAN and the remaining 50% will go out on the access link. The LAN continues to generate 30 requests/second and hence will incur a traffic intensity of 0.25 as before. However, only 50% of 30 requests/second, namely 15 requests/second, will go out on the access link. Hence traffic intensity at access link will be equal to 0.5 (c) h*(0.020seconds)+((1-h)*(2.02seconds)=2.02-(2*h)seconds. (15 points) 3. Consider sending a large file of F bits from Host A to Host B. There are m links (and m-1 switches) between A and B. Neglect propagation delays and queueing delays. Host A segments the file into segments of S bits each. Assume that F/S is an integer. Host A adds h bits of header to each segment forming packets of size h+S each. Each link has a transmission rate of R bps. Find the end-to-end delay in sending the file. (10 points) Solution: Size of Packet + header = h+S. Time of transmission for Packet 1 on Link 1 = (h+S)/R seconds. Time of transmission for Packet 1 for m links = m(h+S)/R seconds. (a) After Packet 1 arrives at the destination, every subsequent (h+S)/R seconds, each other packet will arrive. There are (F/S)-1 such packets. The transmission time for these packets = ((h+S)/R)*((F/S)-1) seconds. (b) Hence the total end-to-end delay is the sum of (a) and (b) values. It is equal to ((h+S)/R)(m – 1 +F/S) seconds. 4. We know from my lecture in class, that streaming audio and video can and is usually done using UDP sockets. Consider webpages that have embedded streaming audio/video displays. In this case, you know that webpages use HTTP whose underlying protocol is TCP; but the inlaid streaming multimedia uses UDP? Could you discuss the situation, analyze and offer your thoughts on what may really be going on? (10 points) Solution: Will be discussed in class. 5. Can you think of a useful application in any domain that could use the internet, use TCP or UDP sockets and not already known publicly? Try your best to be creative. (10 points) Solution: How about this? A universal appointment system: All of us schedule appointments for various things such as dental visits, annual checkups, hair salons, spa, Carpet Cleaning, for meeting with friends, etc. etc. Now here is how things should be: You go to one website, your information/profile is there. You pick the place for appointment (say Mathangi R. Sekharan, MD on Davis St. Evanston) and peruse their system as to when appointments are available and pick the one that is most suitable to you among the ones available. At the end of the session, two things should happen: your calendar wherever the heck it is, (your PDA or Yahoo!Calendar) and the appointment or calendar system at the Service Location should get updated. Cool, huh?