Ans2
advertisement
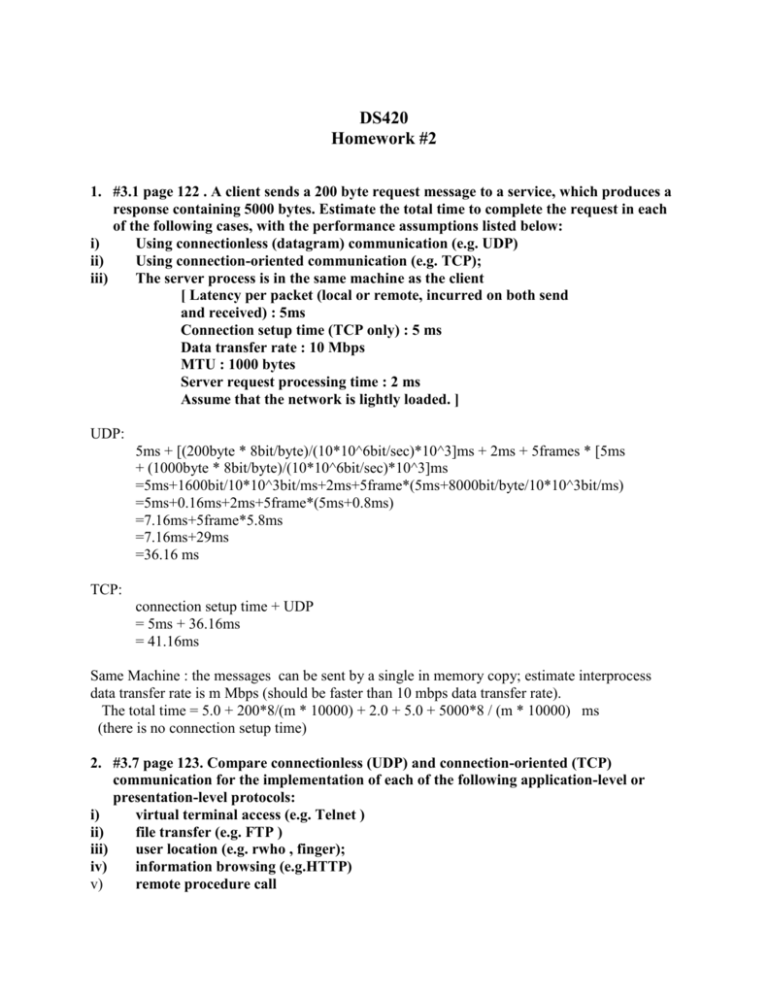
DS420 Homework #2 1. #3.1 page 122 . A client sends a 200 byte request message to a service, which produces a response containing 5000 bytes. Estimate the total time to complete the request in each of the following cases, with the performance assumptions listed below: i) Using connectionless (datagram) communication (e.g. UDP) ii) Using connection-oriented communication (e.g. TCP); iii) The server process is in the same machine as the client [ Latency per packet (local or remote, incurred on both send and received) : 5ms Connection setup time (TCP only) : 5 ms Data transfer rate : 10 Mbps MTU : 1000 bytes Server request processing time : 2 ms Assume that the network is lightly loaded. ] UDP: 5ms + [(200byte * 8bit/byte)/(10*10^6bit/sec)*10^3]ms + 2ms + 5frames * [5ms + (1000byte * 8bit/byte)/(10*10^6bit/sec)*10^3]ms =5ms+1600bit/10*10^3bit/ms+2ms+5frame*(5ms+8000bit/byte/10*10^3bit/ms) =5ms+0.16ms+2ms+5frame*(5ms+0.8ms) =7.16ms+5frame*5.8ms =7.16ms+29ms =36.16 ms TCP: connection setup time + UDP = 5ms + 36.16ms = 41.16ms Same Machine : the messages can be sent by a single in memory copy; estimate interprocess data transfer rate is m Mbps (should be faster than 10 mbps data transfer rate). The total time = 5.0 + 200*8/(m * 10000) + 2.0 + 5.0 + 5000*8 / (m * 10000) ms (there is no connection setup time) 2. #3.7 page 123. Compare connectionless (UDP) and connection-oriented (TCP) communication for the implementation of each of the following application-level or presentation-level protocols: i) virtual terminal access (e.g. Telnet ) ii) file transfer (e.g. FTP ) iii) user location (e.g. rwho , finger); iv) information browsing (e.g.HTTP) v) remote procedure call i) ii) iii) iv) v) The long duration of sessions, the need for reliability and the unstructured sequences of characters transmitted make connection-oriented communication most suitable for this application. Performance is not critical in this application, so the overheads are of little consequence. File calls for the transmission of large volumes of data. Connectionless would be o.k. if error rates are low and the messages can be large, but in the Internet, these requirements aren't met, so TCP is used. Connectionless is preferable, since messages are short, and a single message is sufficient for each transaction. Either mode could be used. The volume of data transferred on each transaction can be quite large, so TCP is used in practice. RPC achieves reliability by means of timeout and re-trys, so connectionless (UDP) communication is often preferred. 3. #3.9 page 123. A specific problem that must be solved in remote terminal access protocols such as Telnet is the need to transmit exceptional events such as 'kill signals' from the 'terminal' to the host in advance of previously-transmitted data. Kill signals should reach their destination ahead of any other ongoing transmissions. Discuss the solution of this problem with connection-oriented and connectionless protocols. This problem is that a kill signal should reach the receiving process quickly even when there is buffer (e.g. caused by an infinite loop in the sender) or other exceptional conditions at the receiving host. With a connection-oriented , reliable protocol such as TCP, all packets must be received and acknowledged in the order in which they are transmitted. Thus a kill signal cannot overtake other data already in the stream. To overcome this, an out-of-band signalling mechanism must be provided. In TCP, this is called the URGENT mechanism. Packets containing data that is flagged as URGENT bypass the flow-control mechanisms at the receiver and are processed immediately. With connectionless protocols, the process at the sender simply recognized the event and sends a message containing a kill signal in the next outgoing packet. The message must be resent until the receiving process acknowledges it. 3. #4.7 page 162 Sun XDR marshals data by converting it into a standard big-endian form before transmission. Discuss the advantages and disadvantages of this method when compared with CORBA's CDR. The XDR method which uses a standard form is inefficient when communication takes place between pairs of similar computers whose byte orderings differ from the standard. It is efficient in networks in which the byte-ordering used by the majority of the computers is the same as the standard form. The conversion by senders and recipients that use the standard form is in effect a null operation. In CORBA CDR senders include an identifier in each message and recipients convert the bytes to their own ordering if necessary. This method eliminates all unnecessary data conversions, but adds complexity in that all computers need to deal with both variants. 4. #4.8 page 163 Sun XDR aligns each primitive value on a four byte boundary, whereas CORBA CDR aligns a primitive value of size n on an n-byte boundary. Discuss the trade-offs in choosing the sizes occupied by primitive values. Marshalling is simpler when the data matches the alignment boundaries of the computers involved. Four bytes is large enough to support most architectures efficiently, but some space is wasted by smaller primitive values. The hybrid method of CDR is more complex to implement, but saves some space in the marshalled form. 6. a) Describe and illustrate the process of decrypting base64 encoded text, using as an example the encoded text QSBzaG9ydCBzYW1wbGU= The RFC 2045 "MIME message formats" will also be helpful. Step 1: Convert the letters into base64 codes 16,18,1,51,26,6,61,50,29,2,1,51,24,22,53,48,27,6,20 Step 2: Convert base64 codes into binary numbers 01000001,00100000,01110011,01101000,01101111,01110010, 01110100,00100000,01110011,01100001,01101101,01110000, 01101100,01100101,00 Step 3: Convert binary numbers into decimal numbers 65,32,115,104,111,114,116,32,115,97,109,112,108,101 Step 4: Convert decimal numbers to ASCII characters Ans: A short sample b) A given file is 3072 bytes long. How many bytes long will it be if it is encoded into base64 encoding, where a CR-LF pair is inserted after every 80 output bytes and at the end? Step 1: 3072 bytes long file becomes 3072 *(4/3) = 4096 bytes in bsae64 format. No. of 80-character line =ceiling 4096/80 = 52 lines 52 pairs of CR-LF are needed. Step 2: Total size of the file = 4096 + 52* 2 = 4200 Ans: 4200 bytes long will it be if it is encoded into base64 encoding.