here
advertisement

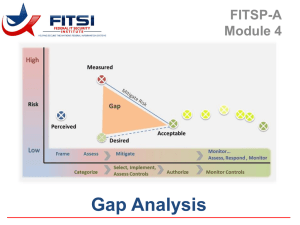
System Security Categorization Review (NOTE: See Excel Spreadsheets for GSS & MA Systems Categorization) System Security Categorization Review for the [SystemName (Acronym) and System Version Number] Date Month, Year 1 System Security Categorization Review Overview XYZ COMPANY conducted a System Security Categorization assessment of the [SystemName] (SystemAcronym). The purpose of this assessment is to identify and document the system’s security categorization per the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-60, Guide for Mapping Types of Information and Information Systems to Security Categories, and the Federal Information Processing Standard (FIPS) 199, Standards for Security Categorization of Federal Information and Information Systems. This document provides the security categorization for the (SystemAcronym). System Security Categorization Process Background. The System Security Categorization is an invaluable asset in the Certification and Accreditation (C&A) process and FIPS 199 requires it. The System Security Categorization determination and document process follows NIST SP 800-60, Guide for Mapping Types of Information and Information Systems to Security Categories, which implements FIPS 199. The basis for the categorization is the identification of the types of information stored or created within the system, and determining the expected impact to the SSA or the entity from a loss in Confidentiality, Integrity, and Availability to the system or data. Impact Levels. Descriptions of the security impact levels are below. Security Impact Levels Security Attribute CONFIDENTIALITY INTEGRITY AVAILABILITY Low The unauthorized disclosure of information could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. Security Impact Level Moderate The unauthorized disclosure of information could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. The unauthorized modification or destruction of information could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. The unauthorized modification or destruction of information could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. The disruption of access to or use of information or an information system could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. The disruption of access to or use of information or an information system could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. 2 High The unauthorized disclosure of information could be expected to have a severe, catastrophic adverse effect on organizational operations, organizational assets, or individuals. The unauthorized modification or destruction of information could be expected to have a severe, catastrophic adverse effect on organizational operations, organizational assets, or individuals. The disruption of access to or use of information or an information system could be expected to have a severe, catastrophic adverse effect on organizational operations, organizational assets, or individuals. System Security Categorization Review Process Steps. The steps to determine the System Security Categorization are as follows: Obtain review and analyze existing documentation and interview system personnel to characterize the system and identify the data elements and information contained within the system. Use NIST SP 800-60, to conduct an analysis to map each of the data elements to an applicable Information Type. Determine and document the provisional impact levels, High, Medium, or Low, for Confidentiality, Integrity, and Availability for each of the Information Types. The highest impact level for Confidentiality, Integrity, and Availability is the overall impact level for the System Security Categorization impact level. See Appendix A for the characterization of the system and the data types selected. For further information, refer to NIST SP 800-60 and FIPS 199. NIST 800-60 Volume I, the overview of Security Categorization, is at http://csrc.nist.gov/publications/nistpubs/800-60-rev1/SP800-60_Vol1-Rev1.pdf NIST 800-60 Volume II contains the details of the individual information types is at http://csrc.nist.gov/publications/nistpubs/800-60-rev1/SP800-60_Vol2-Rev1.pdf. FIPS 199 is at http://csrc.nist.gov/publications/fips/fips199/FIPS-PUB-199-final.pdf. 3 System Security Categorization Review Recommended Security Categorization for (SystemName) (System Acronym) System Name: System Acronym: GSS/MA: Description of System: 4 System Security Categorization Review The following information types have been derived utilizing NIST SP 800-60. Information Type Impact Level for Confidentiality Impact Level for Integrity Impact Level for Availability Given the information types and impact levels, the following are the system’s impact levels: Final Impact Level for Confidentiality Final Impact Level for Integrity Final Impact Level for Availability The System Security Categorization recommendation: LOW MODERATE HIGH 5 Overall Impact Level System Security Categorization Review Appendix A: NIST 800-60 Security Categorization Worksheet (Place copy of Security Categorization Worksheet here) System Information: MA Identifier: MA Name: MA Acronym: System Information: MA Identifier: Description: MA Name: MA Acronym: MA Description: Resident GSS Infrastructures: FISMA ID Owner Sharing Partner Resident GSS Infrastructures: FISMA ID Owner Sharing Partner 800-60 Provisional Impact Levels Δ Applicable NIST 800-60 MA Information Type Legend: Confidentiality Integrity Availability 800-60 Provisional C I Impact LevelsA Applicable NIST 800-60 MA Information Type C Δ Δ Legend: Confidentiality C Integrity I Availability A C Δ Adjusted Impact Levels = Deviation HWM = High Water-Mark = No Change = Reduce = Increase Adjusted Impact Levels I Δ A Δ HWM = Deviation HWM = High Water-Mark = No Change = Reduce = Increase I Overall Security Category Overall Security Applicable NIST Category 800-60 MA Information Type Information Type Association Rationale Impact Level Adjustment Factors Applicable NIST 800-60 MA Information Type Information Type Association Rationale Impact Level Adjustment Factors 6 Δ A Δ HWM