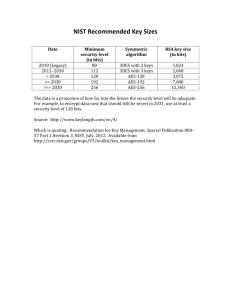
PowerPoint Slides from this Seminar
advertisement

IT Best Practices for Community Colleges Part 3: Configuration Management Donald Hester March 30, 2010 For audio call Toll Free 1-888-886-3951 and use PIN/code 133206 Housekeeping • Maximize your CCC Confer window. • Phone audio will be in presenter-only mode. • Ask questions and make comments using the chat window. Adjusting Audio 1) If you’re listening on your computer, adjust your volume using the speaker slider. 2) If you’re listening over the phone, click on phone headset. Do not listen on both computer and phone. Saving Files & Open/close Captions 1. Save chat window with floppy disc icon 2. Open/close captioning window with CC icon Emoticons and Polling 1) Raise hand and Emoticons 2) Polling options IT Best Practices for Community Colleges Part 3: Configuration Management Donald Hester Configuration Management “The management of security features and assurances through control of changes made to hardware, software, firmware, documentation, test, test fixtures, and test documentation throughout the life cycle of an information system.” • National Information Systems Security Glossary 7 IT Standards Control Objectives for Information and related Technology (COBIT) Information Technology Infrastructure Library (ITIL) International Standards Organization (ISO) National Institute of Standards and Technology (NIST) 8 The facts 80% of IT systems outages are caused by operator and application errors. High-Performance IT organizations Common Characteristics 1 admin for every 100 servers More planned work than unplanned work More staff early in lifecycle Collaboration Posture of compliance (IT standards) Culture of change management Understand causality Manage by facts The missing pieces Configuration Management Change Management Release Management Incident Management Problem Management Benefits of Configuration Management Good CM does not increase workload it decreases it Fewer Incidents Greater Return on Investment (ROI) Faster Recovery (MTTR) Improve IS quality Improve IT service CM Lifecycle Configuration identification • Baseline, gold standard Configuration control • Change management, change control Configuration status accounting • Enforcement Configuration audits • Testing 13 Configuration Identification Configuration Management Database (CMDB) A repository of information related to all the components of an information system • Configuration files • Group Policy settings • Image files for operating systems Details about the important attributes and relationships between them 14 Policy Develop, disseminate, and review/update A documented configuration management policy Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance 15 Baseline Develop, document, and maintain under configuration control, a current baseline configuration • Images • Builds • CMDB • Configuration files • GPO (Group policy objects) 16 Baselines A place to start • Federal Desktop Core Configuration (FDCC) CIS Benchmarks • Modify based upon your needs • You may have different configurations for • • 17 different workstations Compatibility issues Interoperability issues Control Change Determine the types of changes to the information system that are configuration controlled Approve configuration-controlled changes Coordinate and provide oversight for configuration change control activities Document approved configurationcontrolled changes 18 Impact Analysis Analyze changes to the information system to determine potential security impacts prior to change implementation • Confidentiality • Integrity • Availability • Interoperability • Compatibility 19 Restrict changes to the system Define, document, approve, and enforce physical and logical access restrictions associated with changes to the information system • Limit who can make changes • This means no local admins • Automate if possible 20 Least Functionality Configure the information system to provide only essential capabilities and specifically prohibit or restrict the use of functions, ports, protocols, and/or services • If it is not needed why have it? 21 Inventory Develop, document, and maintain an inventory of information system components • Accurately reflect the current system • At a level of granularity deemed necessary 22 NIST There is no compulsory IT standard required for local governments The National Institute of Standards and Technology (NIST)encourages state, local and tribal governments to consider the use of these guidelines, as appropriate In adopting NIST standards the local government demonstrates due diligence Resources Institute of Configuration Management • http://www.icmhq.com/ NIST (FDCC) • http://nvd.nist.gov/fdcc/index.cfm Center for Internet Security (CIS) Benchmarks • http://cisecurity.org/ IT Governance Institute (ITGI) • http://www.itgi.org/ 24 Q&A Donald E. Hester CISSP, CISA, CAP, MCT, MCITP, MCTS, MCSE Security, Security+ Maze & Associates @One / San Diego City College www.LearnSecurity.org http://www.linkedin.com/in/donaldehester http://www.facebook.com/group.php?gid=245570977486 Evaluation Survey Link Help us improve our seminars by filing out a short online evaluation survey at: http://www.surveymonkey.com/s/10SpIT3 Join us in San Diego at the 2010 Online Teaching Conference “Engaging every online student in lean and green times.” June 16, 17, & 18 - San Diego City College Register now at http://otc10.org IT Best Practices for Community Colleges Part 3: Configuration Management Thanks for attending For upcoming events and links to recently archived seminars, check the @ONE Web site at: http://onefortraining.org/