Chaffing-and
advertisement

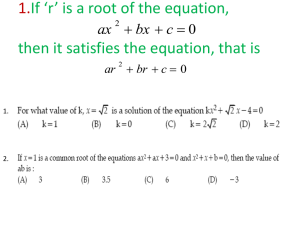
Chaffing-and-Winnowing (Conceptualization and Simulation) Ng Hian, James (HT035267U, nghianja@comp.nus.edu.sg) 8th November 2003 Abstract This is a project report for the module CS5231: Cryptographic Techniques and Data Security. In this report, I am discussing on Ronald L. Rivest’s ‘Chaffing-andWinnowing’ idea of confidential message transmission. With the help of a prototype of a simulator, this project tries to give a demonstration and evaluation of the concept behind the idea. Keywords: cryptology, security technique, steganography, message transmission. 1. Introduction In 1998, Ronald L. Rivest [1] introduced a new scheme for transmitting messages in confidentiality. It is called ‘chaffing and winnowing’. He claimed that the technique could provide a high level of privacy without the use of any encryption or key, thus bypassing the law to release the encryption key to the government when required. It was closer to steganography than encryption. He further explained ‘chaffing and winnowing’ examples under different scenarios to demonstrate the workings of the technique as well as the strengths. Based on Rivest’s descriptions on the algorithm used in the idea of ‘chaffing and winnowing’, I have designed and developed a simulator to try to demonstrate that it is indeed easy to adopt such a scheme in transmitting messages. Though the simulator is at best just a prototype and not a fullblown simulator, it is still useful to the understanding of the concept. Through it, one can see that the algorithm provides a certain level of confusion in the packets of message data sent and an eavesdropper needs to spend a considerable amount of time guessing the correct data packets if it is possible at all. With this security and that it is relatively easy to deploy, usage should be of a wide scope. As for how secure the scheme is, it has been subsequently evaluated by Bellare and Boldyreva [2]. Bellare et al. conceptualized the idea of ‘chaffing and winnowing’ given in [1] and gave a more concrete scenario of its workings. They argued that abstractly, ‘chaffing and winnowing’ is a form of encryption itself and posed the question: Can chaffing-and-winnowing based schemes provide the same level of privacy, and, if so, can this be proven, and under what assumptions? They evaluated the three examples given by Rivest and found them to give a low-level of privacy. They went on to give alternatives that were simpler, proven secure and equally cost-effective. This paper is organized as follows: section 2 is the description of the algorithm outlined, section 3 is on my simulator, section 4 is on the implementation of the types of message transmission, section 5 is on the examples of ‘chaffing and winnowing’, section 6 touches briefly on usage scenarios, and section 7 is on the evaluation study by Bellare et al. 2. Algorithm The basic concept of the algorithm is relatively simple. Given two parties wanting to transmit data to each other, ‘chaffing-andwinnowing’ provides a scheme in which information can be transmitted safely. There is no need for encryption or holding multiple keys. It is simple, secure, and cost-effective. Sometimes, a complex problem does not necessary requires a complex solution. ‘Chaffing-and-winnowing’ works in the following way: 1. 2. 3. 4. 5. 6. Two parties arranged to transmit information/data across an unsecured communication line. The sender breaks the message to be sent into packets appends to each packet a message authentication code (MAC)*. A serial number is also appended to each packet for the identification of missing packets and removing of duplicated ones. ‘Chaff’ packets with bogus MAC are added to the stream of good packets, randomly intermingled. At least one bad packet is added for every good packet preferably. The receiver just discards all the bad packets and retains the good packets to retrieve the correct message. * The MAC is computed from a function of the packet contents and a secret authentication key. This key is decided beforehand with any standard technique. The way the receiver sieve through the packets to get the good ones is similar to the way a network computer receives TCP/IP data-grams. In a typical packet-based communication system, the receiver will automatically discard all packets with bad MAC. So the ‘winnowing’ process is a normal part of such a system. 3. Simulator By studying the paper by Rivest in detail, I managed to grasp the ‘chaffing-andwinnowing’ idea and come up with a design for the structure of my implementation of the simulator. The design is shown in Figure 1. Controller Initialize the system environment; instantiate the sender, receiver and eavesdropper; act as transmission link. Alice The sender of message packets and chaff them. Eve The eavesdropper listens to all the packets. Figure 1: Design of the simulator Bob The receiver of message packets and filters them. With the design in place, development is done with the programming language of choice being Java™. The version of Java™ used is JDK1.4.1 which provides good application packages for developing graphical user interfaces. The final product has a control window and three message transmission windows as shown in the set of figures, Figure 2a, 2b, 2c and 2d. They correspond to the components stated in the design. 4. Message Transmission Figure 2a: Control Panel There is basically three ways of transmitting messages from one point to another point through a transmission medium. The medium can be wired as in electrical wires and optical cables or wireless as in radio waves and frequencies. The three basic ways are plain transmission, jumbled transmission, and transmission with ‘chaffing-andwinnowing’. Plain transmission is simply the sending of a message in packets one-by-one and in sequence. Each packet can contain anything from a data bit to a character or even to a word from a message sentence. For illustration purposes, the simulator uses a word as the content in a packet transmitted. To see how the simulator performs a plain message transmission, select the first choice from the control panel and start the simulation. After a message is entered into the top text area and the ‘Send’ button clicked, it can be seen that the message has been broken down into word components and packaged into packets for transmission. The packets are in the form of tuples with 3 elements each. The first element is the sequence number indicating the order that the receiver should process the packet. The second element is the payload, i.e. the word. The third is a number that is not in use here. The packets are displayed on the bottom text area of the sender window and the receiver and eavesdropper get to see the same packets. Figure 2b: Message Sender Figure 2c: Message Receiver deduce the MAC difference. There are two other options for ‘chaffingand-winnowing’ but they are discussed in the next section. 5. Forms of C-and-W Figure 2d: Eavesdropper For jumbled transmission, the packets are not sending out in the order they are packaged. Packets are created from the message entered in the same way as in plain transmission but instead of sending a packet once it is packaged in sequence, the packets are stored in an array and the order rearranged before they are sent out. The randomly jumbled sequence of packets can be observed in the windows for Alice, Bob and Eve. Bob the receiver gets the randomly ordered packets from Alice the sender and constructs the original sequence based on the sequence numbers. Then the message is extracted from the packets. However, jumbled transmission does not stop the eavesdropper from knowing the message as she is also supposed to know the method of ordering the packets by the sequence numbers. The ‘chaffing-and-winnowing’ way of message transmission is simulated when the third option is selected in the control panel. This option demonstrates the core workings of the algorithm but not yet the full example described. It shows the situation whereby the sender inserts chaff packets along with the actual packets and sends them all out. In this extremely simplified case, the difference between an actual packet’s MAC and a chaff packet’s MAC is that the former is an odd number while the latter is an even number. The receiver knows this fact too so he is able to winnow out the correct packets. The eavesdropper on the other hand does not know this but in this case, it is not hard to There are various forms described and examples explained on ‘chaffing-andwinnowing’. Rivest has given three examples of the different forms (or schemes) in which ‘chaffing-and-winnowing’ can be performed and the simulator has implemented two variant versions of them. I will explain the simulator’s implementations along with Rivest’s examples here. The fourth option on the simulator’s control panel will set the system to perform message transmission of packets containing words from the message entered using ‘chaffingand-winnowing’ with a computed MAC. A typical MAC algorithm can be any function that appears to act randomly to the eavesdropper. Rivest’s example involves a HMAC-SHA1 MAC algorithm that have an output from concatenating the output of the HMAC-SHA1 MAC algorithm together with the low-order bit of the message being MAC’ed. The version in the simulator is a modified one that uses a key string distributed by the control panel to the sender and receiver, and with a concatenation of the key and a message word, a SHA1-digested MAC is obtained. To retrieve the original message after transmission, the receiver simply checks each packet by extracting the content of the packet (which is the word) and concatenate with the key string before digesting. If the newly SHA1-digested string matches with the MAC in the packet, then the packet can be unpackaged to retrieve the word for the original message. Figure 3 below shows the original message and the packets received. See that chaffs packets with similar MAC are added. know the secret authentication key used to compute the MACs. Figure 3: Word-by-word c-and-w The last option in the simulator tries to model the above idea. However, using one bit from a data stream is not easy to do for demonstration so I made use of one English character from the message to be sent instead. Everything done here is the same as what has been done in the previous option. The sole difference is that each packet carries only one English character as payload. Figure 4 shows the original message and the packets received. One can see that it is very inefficient. In order to make the ‘chaffing-andwinnowing’ technique more efficient and to reduce the bandwidth, Rivest suggests an alternative paradigm. First apply an all-ornothing transform to the message. One can think of this transform somewhat similar to a zip compression where a lost bit during transmission will render the whole message unrecoverable. It is a keyless, invertible transform with the property that inversion is hard if any block of the output is missing. The reason for doing the transform is that the sender wants to ensure that the receiver sees the entire message or none of it. Figure 4: Char-by-char c-and-w The above method has a problem. The eavesdropper may also distinguish wheat from chaff by the contents of each packet. So if the wheat packets each contain an English sentence or word, while the chaff packets contain random bits, then the eavesdropper will have no difficulty in winnowing the wheat from the chaff herself. On the other hand, if each wheat packet contains a single bit, and there is a chaff packet with the same serial number containing the complementary bit, then the eavesdropper will have a very difficult (essentially impossible) task. Being able to distinguish wheat from chaff would require her to break the MAC algorithm and/or In this method, Alice (the sender) will preprocess the message using the transform before breaking the output into blocks. Each block is MAC’ed, resulting in a stream of valid packets. Then chaff packets are inserted into random positions in this stream. Intuitively, an eavesdropper must guess the positions of all the chaff packets in order to decipher. 6. Scenarios of usage Usage of the ‘chaffing-and-winnowing’ technique is vast, according to Rivest. The scenarios he gives as well as other possible scenarios are described in the following paragraphs. The first scenario involves Alice communicating with Bob using a standard packet-based communication scheme. Each packet is authenticated with a MAC created using a secret authentication key known only to Alice and Bob. If Alice and Bob wish to communicate privately without an eavesdropper able to understand the message, they can program the application transmitting the message to add chaff packets automatically. The second scenario is one that Alice and Bob having no intention of achieving confidentiality of their message from an eavesdropper. It actually involves a third party, Charlie that wittingly or unwittingly, inserts chaff packets to the transmission of Alice and Bob. Charlie may wittingly do this by being an administrator of the network. A third scenario is that the transmission stream between Alice and Bob is being multiplexed with another transmission stream. The new stream is simply message packets belonging to another communication link between two other people. This achieves ‘chaffing-and-winnowing’ without incurring high overheads and hence saves on bandwidth. 7. Evaluation Study Rivest has noted that his examples will not provide a high level of privacy so the main evaluation is to find out how secure in providing confidentiality the ‘chaffing-andwinnowing’ technique really is. Bellare et al. has provided the answers to such an evaluation. The first of Rivest’s schemes evaluated is the bit-by-bit scheme. This is the scheme where every bit of data sent has an opposite bit value as chaff. It has been proven that this scheme provides privacy in the findthen-guess sense assuming the MAC is a pseudo-random function. The second scheme is the scattering scheme where an all-or-nothing transform is applied on the message transmitted. Close examination has shown that the security provided is unclear. This has to do with the definition of security for an all-or-nothing transform. Analysis of the definition is inconclusive so this type of ‘chaffing-andwinnowing’ scheme cannot be proven. Another debate on the whole ‘chaffing-andwinnowing’ technique is the question: Is ‘chaffing-and-winnowing’ a form of encryption? Rivest states that winnowing does not employ encryption and so does not have a ‘decryption key’. Everything is done without an encryption algorithm. The only key exchange taking place is the key for computing the MAC, which is not use for decrypting any code. The packets transmitted are ‘hidden’ among a sea of unwanted packets. Hence the technique is more closely related to steganography and is not a form of encryption. On the other hand, under the convention in modern cryptography, the use of terminology is different. Rivest uses the terminology of cryptographic policy discussion while Bellare et al. use the technical terminology of cryptographers which is more suited to security analysis. Thus by definition, the key for the MAC is a decryption key as it enables recovery of the original message. 8. Conclusions The ‘chaffing-and-winnowing’ technique is an interesting idea. It is easy to implement and the simulation has shown that building an application the uses the technique for confidential message transmission is viable. Though the technique can be costly in terms of transmission bandwidth, specific design of the usage can still make it efficient. The main concern of it is that its level of privacy cannot be properly determined through analysis but a newer scheme has been proposed to address this concern. Resources Lecture Notes in Computer Science, Java™ J2SE 1.4.1 SDK (http://www.java.sun.com) References [1] Ronald L. Rivest Chaffing and Winnowing: Confidentiality without Encryption http://theory.lcs.mit.edu/~rivest/chaffing .txt (1998) [2] Mihir Bellare and Alexandra Boldyreva The Security of Chaffing and Winnowing ASIACRYPT 2000, LNCS 1976, pp. 517-530, 2000 []