NOTE: Attempt ANY TWO QUESTIONS
advertisement

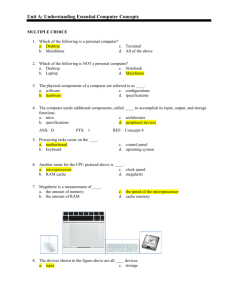
JRE SCHOOL OF Engineering CLASS TEST-1 EXAMINATIONS FEB14 Subject Name CAO Roll No. of Student Subject Code Max Marks Max Duration Time Date 21 Feb 2014 For EC and AEI branches only SECTION – A EC 403 20 60 min 09:20 to 10:20 AM (2 marks * 2 Questions = 4 Marks) NOTE: ATTEMPT ANY TWO QUESTIONS 1. Define an abstract computer and list limitation of a computer. Ans. An abstract machine, also called an abstract computer, is a theoretical model of a computer hardware or software system used in automata theory. Abstraction of computing processes is used in both the computer science and computer engineering disciplines and usually assumes discrete time paradigm. 2. What are the components at processor design level in a computer. CPU design focuses on six main areas: 1. datapaths (such as ALUs and pipelines) 2. control unit: logic which controls the datapaths 3. Memory components such as register files, caches 4. Clock circuitry such as clock drivers, PLLs, clock distribution networks 5. Logic gate cell library which is used to implement the logic 3. Describe cache memory. Ans. A CPU cache is a cache used by the central processing unit (CPU) of a computer to reduce the average time to access memory. The cache is a smaller, faster memory which stores copies of the data from frequently used main memory locations. Most CPUs have different independent caches, including instruction and data caches, where the data cache is usually organized as a hierarchy of more cache levels (L1, L2 etc.) SECTION – B (3 marks * 2 Questions = 6 Marks) NOTE: ATTEMPT ANY TWO QUESTIONS 1. Discuss memory hierarchy with help of a diagram. Ans. 2. Explain error detection and error correction techniques. And. The general definitions of the terms are as follows: Error detection is the detection of errors caused by noise or other impairments during transmission from the transmitter to the receiver. Summer is another name for error detection Error correction is the detection of errors and reconstruction of the original, error-free data. Error detection is most commonly realized using a suitable hash function (or checksum algorithm). A hash function adds a fixed-length tag to a message, which enables receivers to verify the delivered message by recomputing the tag and comparing it with the one provided. There exists a vast variety of different hash function designs. However, some are of particularly widespread use because of either their simplicity or their suitability for detecting certain kinds of errors (e.g., the cyclic redundancy check's performance in detecting burst errors). Random-error-correcting codes based on minimum distance coding can provide a suitable alternative to hash functions when a strict guarantee on the minimum number of errors to be detected is desired. Repetition codes, described below, are special cases of error-correcting codes: although rather inefficient, they find applications for both error correction and detection due to their simplicity. 3. Explain Architecture and Organization of a computer. Ans. The components from which computers are built, i.e., computer organization. In contrast, computer architecture is the science of integrating those components to achieve a level of functionality and performance. It is as if computer organization examines the lumber, bricks, nails, and other building material While computer architecture looks at the design of the house. SECTION – C (5 marks * 2 Questions = 10 marks) NOTE: ATTEMPT ANY TWO QUESTIONS 1. Explain interrupts with diagram. • Ans. Mechanism by which other modules (e.g. I/O) may interrupt normal sequence of processing • Program — e.g. overflow, division by zero • Timer — Generated by internal processor timer — Used in pre-emptive multi-tasking • I/O — from I/O controller • Hardware failure — e.g. memory parity error 2. Discuss characteristics of memory. • Ans. Location • Capacity • Unit of transfer • Access method • Performance • Physical type • Physical characteristics • Organisation 3. • Discuss memory access methods. Ans. Sequential — Start at the beginning and read through in order — Access time depends on location of data and previous location — e.g. tape • Direct — Individual blocks have unique address — Access is by jumping to vicinity plus sequential search — Access time depends on location and previous location — e.g. disk • Random — Individual addresses identify locations exactly — Access time is independent of location or previous access — e.g. RAM • Associative — Data is located by a comparison with contents of a portion of the store — Access time is independent of location or previous access — e.g. cache 4. • Draw and explain Instruction cycle with help of a diagram. Ans. Two steps: — Fetch — Execute Fetch: • Program Counter (PC) holds address of next instruction to fetch • Processor fetches instruction from memory location pointed to by PC • Increment PC — Unless told otherwise • Instruction loaded into Instruction Register (IR) • Processor interprets instruction and performs required actions Execute: • Processor-memory — data transfer between CPU and main memory • Processor I/O — Data transfer between CPU and I/O module • Data processing — Some arithmetic or logical operation on data • Control — Alteration of sequence of operations — e.g. jump • Combination of above ************