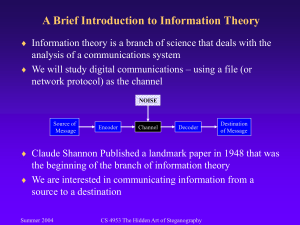
3. Embedding data to transformation fields algorythm
advertisement

Bauman Moscow State University Department of «Science and Management» Department of «Information Security» T.M. Volosatova , N.V. Chichvarin . Steganography in CAD Electronic textbook Tutorial on subjects «Detection and identification signals», «Development of CAD» Moscow (C) 2012 MSTU. 2 UDC 621.391 Reviewers: Prof. E. Gordeev . PhD A. Voronov. TM Volosatova , NV Chichvarin . Steganography in CAD . Tutorial on subjects «Detection and identification signals», «Development of CAD». Electronic textbook . - BMSTU 2012, pp.48 . The manual representation basic materials and questions in the section «Steganography and steganalysis», discipline «detection and identification signals»: computer steganography methods , techniques and digital funds containers and theoretical aspects of steganalysis - data discovery hidden in containers. For teachers of engineering faculty and students . Recommended NMS BMSTU. Electronic textbook Volosatova Tamara Chichvarin Nicolai « Steganography in CAD» © 2012 BMSTU Steganography in CAD/CAM/PLM. Contents. 3 Steganography in CAD Contents Introduction………………………………………………………………………………………..1 Physical steganography.............................................................................................................7 Digital steganography. ..............................................................................................................8 Network ..................................................................................................................................10 Printed .....................................................................................................................................11 Digital Text .............................................................................................................................11 Using Sudoku puzzles. ............................................................................................................12 Additional terminology. ................................................................................................................12 Countermeasures and detection/ ....................................................................................................12 Applications. ..................................................................................................................................13 Use by terrorists. .....................................................................................................................14 Alleged use by intelligence services. ......................................................................................16 Distributed Steganography. ....................................................................................................16 2. Algorithms for digital steganography .....................................................................................20 2.1. Algorithms for embedding data in the spatial domain ...........................................................20 3. Embedding data to transformation fields algorythm .................................................................26 3.1 Embedding data in a discrete cosine transformation coefficients ...........................................28 3.2 Koch algorithm ........................................................................................................................28 3.3. Benham algorithm ..................................................................................................................29 3.4 Podilchuk algorithm ................................................................................................................29 3.5 Hsu algorithm ..........................................................................................................................30 3.6 Cox algorithm ..........................................................................................................................30 3.7 Barni algorithm ........................................................................................................................31 3.8 Additive algorithms .................................................................................................................31 3.8.1 Algorithms based on the linear data embedding ..................................................................31 3.10 The algorithm Chaya (Chae) .................................................................................................33 Steganography in CAD/CAM/PLM. Contents. 4 3.11 The algorithm Kandar (Kundur) ............................................................................................34 4. A choice of a method of embedding of DWM (digital watermark) in the image-container .....36 4.1. The methods using as containers audiofiles ...........................................................................37 4.2 Broadband coding. ...................................................................................................................38 4.3 Phase coding. ...........................................................................................................................38 4.4 The echo-coding ......................................................................................................................39 4.5 Noise replacement. ..................................................................................................................39 5.The market overview of steganography software.......................................................................44 6. Statement of the problem of detection of hidden messages. ...................................................47 Appendix . .....................................................................................................................................53 Abbreviations: DCT - discrete cosine transformation, DWM - digital watermarks, MDCT – modified discrete cosine transformation, IS – information Security, CALS – continuous Acquisition and Life-cycle Support, CEH – digital watermarks, COP – computer steganography, PDU – protocol Data Unit. Introduction. In modern conditions for the creation of competitive products required to provide integrated management of the processes of design, production, delivery and support, including all participants in the product lifecycle. Required for this informational support continuous product lifecycle , as a rule, based on the strategy implemented CALS, which has become widespread in industrialized countries and recommended for use by Russian enterprises Ministry of Economy of the Russian Federation. Centralization of all information about a new product , a large number of both internal and external users of CALS, other risk factors require special attention to the problem of safety management , which is part of the more general problem of information security. In the context of the economic slowdown, it is tempting to reduce the cost of IS within the overall cost reduction. Nevertheless, according to the report KPMG [5], the majority of Steganography in CAD/CAM/PLM. Contents. 5 organizations plan to increase budgets for IB next year , which proves how increased attention over the past few years to information risk management. Important role in solving the problems of information security is given to the international standard ISO17799 (it should be noted the importance of the integration of the standard with the legal framework of the state in the field of information security [2]). Russian companies are also guided by " RD Technical Commission of Russia: Automated systems. Protection against unauthorized access to information». Classification of the requirements for the protection of information and other documents considered in particular in [1]. The result of implementing the standard ISO17799 - Information Security Management System . Its purpose - to reduce losses associated with the violation of information security. In some cases, the scale of the loss can be such that the company faces bankruptcy. An example may serve as an irreplaceable loss CALS- project high-tech products with a long development cycle. Speaking on the practical application of the standard ISO17799, should bear in mind three factors hindering its immediate use. First, the standard recommendations in many cases are quite common. Secondly, in the organization, as a rule, there is a certain system processes, which need to integrate security management process. Theme 1. Steganography: the terminology, the historical review and classification of methods and tools. Questions for self-examination and discussion at the workshop. 1) The historical methods of hiding data. 2) The difference and similarity of steganography cryptography. 3) Theoretical frameworks reflect the terminology used. Literature to explore themes. 1. Gribunin V.G. Binding I.N., Turintsev I.V. Digital Steganography. M.: SOLON-Press, 2002. – 272 pp. 2. Rotation scale and translation invariant spread spectrum digital image watermarking. IEEE Int. Conf. on Image Processing, 1998. P. 4. 3. Pereira S., Joseph J., Deguillaume F. Template Based recovery of Fourier-Based Watermarks Using log-polar and Log-log Maps. IEEE Int. Conf on Multimedia Computing and Systems, 1999. P. 5. Steganography in CAD/CAM/PLM. Contents. 6 Steganography. (From Wikipedia, the free encyclopedia) Steganography is the science of encoding hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message. It is a form of security through obscurity. The word «steganography» is of Greek origin and means «concealed writing». It combines the Greek words «steganos» (στεγανός), meaning «covered or protected», and graphei (γραφή) meaning «writing.» The first recorded use of the term was in 1499 by Johannes Trithemius in his «Steganographia», a treatise on cryptography and steganography, disguised as a book on magic. Generally, the hidden messages will appear to be (or be part of) something else: images, articles, shopping lists, or some other cover text. For example, the hidden message may be in invisible ink between the visible lines of a private letter. The advantage of steganography over cryptography alone is that the intended secret message does not attract attention to itself as an object of scrutiny. Plainly visible encrypted messages — no matter how unbreakable — will arouse interest, and may in themselves be incriminating in countries where encryption is illegal. Thus, whereas cryptography is the practice of protecting the contents of a message alone, steganography is concerned with concealing the fact that a secret message is being sent, as well as concealing the contents of the message. Steganography includes the concealment of information within computer files. In digital steganography, electronic communications may include steganographic coding inside of a transport layer, such as a document file, image file, program or protocol. Media files are ideal for steganographic transmission because of their large size. For example, a sender might start with an innocuous image file and adjust the color of every 100th pixel to correspond to a letter in the alphabet, a change so subtle that someone not specifically looking for it is unlikely to notice it. History of steganography When Herodotus mentions two examples in his Histories. «Demaratus» sent a warning about a forthcoming attack to Greece by writing it directly on the wooden backing of a wax tablet before Steganography in CAD/CAM/PLM. Contents. 7 applying its beeswax surface. Wax tablets were in common use then as reusable writing surfaces, sometimes used for shorthand. In his work Polygraphiae Johannes Trithemius developed his so-called «Ave-Maria-Cipher» with which one can hide information in a Latin praise of God. «Auctor Sapientissimus Conseruans Angelica Deferat Nobis Charitas Potentissimi Creatoris» Physical steganography Steganography has been widely used, including in recent historical times and the present day. Known examples include: Hidden messages within wax tablets — in ancient Greece, people wrote messages on the wood, then covered it with wax upon which an innocent covering message was written. Hidden messages on messenger's body — also used in ancient Greece. Herodotus tells the story of a message tattooed on the shaved head of a slave of Histiaeus, hidden by the hair that afterwards grew over it, and exposed by shaving the head again. The message allegedly carried a warning to Greece about Persian invasion plans. This method has obvious drawbacks, such as delayed transmission while waiting for the slave's hair to grow, and the restrictions on the number and size of messages that can be encoded on one person's scalp. In the early days of the printing press, it was common to mix different typefaces on a printed page due to the printer not having enough copies of some letters otherwise. Because of this, a message could be hidden using 2 (or more) different typefaces, such as normal or italic. During World War II, the French Resistance sent some messages written on the backs of couriers using invisible ink. Hidden messages on paper written in secret inks, under other messages or on the blank parts of other messages. Messages written in Morse code on knitting yarn and then knitted into a piece of clothing worn by a courier. Jeremiah Denton repeatedly blinked his eyes in Morse Code during the 1966 televised press conference that he was forced into as an American prisoner of war by his North Vietnamese captors, spelling out the word: «T-O-R-T-U-R-E». This confirmed for the first time to the U.S. Military (naval intelligence) and Americans that American POWs were being tortured in North Vietnam. Messages written on envelopes in the area covered by postage stamps. Steganography in CAD/CAM/PLM. Contents. 8 During and after World War II, espionage agents used photographically produced microdots to send information back and forth. Microdots were typically minute, approximately less than the size of theperiod produced by a typewriter. World War II microdots needed to be embedded in the paper and covered with an adhesive, such as collodion. This was reflective and thus detectable by viewing against glancing light. Alternative techniques included inserting microdots into slits cut into the edge of post cards. During WWII, Velvalee Dickinson, a spy for Japan in New York City, sent information to accommodation addresses in neutral South America. She was a dealer in dolls, and her letters discussed the quantity and type of doll to ship. The stegotext was the doll orders, while the concealed «plaintext» was itself encoded and gave information about ship movements, etc. Her case became somewhat famous and she became known as the Doll Woman. Cold War counter-propaganda. In 1968, crew members of the USS Pueblo intelligence ship held as prisoners by North Korea, communicated in sign language during staged photo opportunities, informing the United States they were not defectors, but were captives of the North Koreans. In other photos presented to the US, crew members gave «the finger» to the unsuspecting North Koreans, in an attempt to discredit photos that showed them smiling and comfortable. Digital steganography. Image of a tree with a steganographically hidden image. The hidden image is revealed by removing all but the two least significant bits of each color component and a subsequent normalization. The hidden image is shown below. Steganography in CAD/CAM/PLM. Contents. 9 Image of a cat extracted from the tree image above. Modern steganography entered the world in 1985 with the advent of the personal computers being applied to classical steganography problems. Development following that was very slow, but has since taken off, going by the large number of steganography software available: Concealing messages within the lowest bits of noisy images or sound files. Concealing data within encrypted data or within random data. The data to be concealed are first encrypted before being used to overwrite part of a much larger block of encrypted data or a block of random data (an unbreakable cipher like the one-time pad generates ciphertexts that look perfectly random if one does not have the private key). Chaffing and winnowing. Mimic functions convert one file to have the statistical profile of another. This can thwart statistical methods that help brute-force attacks identify the right solution in a ciphertext-only attack. Concealed messages in tampered executable files, exploiting redundancy in the targeted instruction set. Pictures embedded in video material (optionally played at slower or faster speed). Injecting imperceptible delays to packets sent over the network from the keyboard. Delays in keypresses in some applications (telnet or remote desktop software) can mean a delay in packets, and the delays in the packets can be used to encode data. Changing the order of elements in a set. Content-Aware. Steganography hides information in the semantics a human user assigns to a datagram. These systems offer security against a non-human adversary/warden. Steganography in CAD/CAM/PLM. Contents. 10 Blog-Steganography. Messages are fractionalized and the (encrypted) pieces are added as comments of orphaned web-logs (or pin boards on social network platforms). In this case the selection of blogs is the symmetric key that sender and recipient are using; the carrier of the hidden message is the whole blogosphere. Modifying the echo of a sound file (Echo Steganography). Secure Steganography for Audio Signals. Image bit-plane complexity segmentation steganography Including data in ignored sections of a file, such as after the logical end of the carrier file. Making text the same color as the background in word processor documents, e-mails, and forum posts. Network All information hiding techniques that may be used to exchange steganograms in telecommunication networks can be classified under the general term of network steganography. This nomenclature was originally introduced by Krzysztof Szczypiorski in 2003. Contrary to the typical steganographic methods which utilize digital media (images, audio and video files) as a cover for hidden data, network steganography utilizes communication protocols' control elements and their basic intrinsic functionality. As a result, such methods are harder to detect and eliminate. Typical network steganography methods involve modification of the properties of a single network protocol. Such modification can be applied to the PDU (Protocol Data Unit), to the time relations between the exchanged PDUs, or both (hybrid methods). Moreover, it is feasible to utilize the relation between two or more different network protocols to enable secret communication. These applications fall under the term inter-protocol steganography. Network steganography covers a broad spectrum of techniques, which include, among others: Steganophony - the concealment of messages in Voice-over-IP conversations, e.g. the employment of delayed or corrupted packets that would normally be ignored by the receiver (this method is called LACK - Lost Audio Packets Steganography), or, alternatively, hiding information in unused header fields. WLAN Steganography – the utilization of methods that may be exercised to transmit steganograms in Wireless Local Area Networks. A practical example of WLAN Steganography is the HICCUPS system (Hidden Communication System for Corrupted Networks) Steganography in CAD/CAM/PLM. Contents. 11 Printed Digital steganography output may be in the form of printed documents. A message, the plaintext, may be first encrypted by traditional means, producing a ciphertext. Then, an innocuous covertext is modified in some way so as to contain the ciphertext, resulting in the stegotext. For example, the letter size, spacing, typeface, or other characteristics of a covertext can be manipulated to carry the hidden message. Only a recipient who knows the technique used can recover the message and then decrypt it. Francis Bacon developed. Bacon's cipher as such a technique. The ciphertext produced by most digital steganography methods, however, is not printable. Traditional digital methods rely on perturbing noise in the channel file to hide the message, as such, the channel file must be transmitted to the recipient with no additional noise from the transmission. Printing introduces much noise in the ciphertext, generally rendering the message unrecoverable. There are techniques that address this limitation, one notable example is ASCII Art Steganography [17]. Digital Text Unicode steganography uses lookalike characters of the usual ASCII set to look normal, while really carrying extra bits of information. If the text is displayed correctly, there should be no visual difference from ordinary text. Some systems, however, may display the fonts differently, and the extra information would be easily spotted. Alternately, hidden (e.g., control) characters, and redundant use of markup (e.g., empty bold, underline or italics) can add embedded within a body of text to hide information that wouldn't be visually apparent when displayed, but can be discovered by examining the document source. HTML pages can contain code for extra blank spaces and tabs at the end of lines, as well as different colours, fonts and sizes, which will not be visible when displayed. A more trivial example is white text on a white background, which can be revealed by «selecting». One such method is based on the non-printing Unicode characters Zero-Width Joiner (ZWJ) and Zero-Width Non-Joiner (ZWNJ). These characters are used for joining and disjoining letters in Arabic, but can be used in Roman alphabets for hiding information because they have no meaning in Roman alphabets, and because they are «zero-width» and thus not displayed. The embedding of ZWJ in the cover-text represents «1» and the embedding of ZWNJ represents «0». Groups of characters can be used to represent the letters A (giving it the code “0”, and thus Steganography in CAD/CAM/PLM. Contents. 12 represented by ZWNJ) to Z (giving it the code «1011», and thus represented by ZWJ,ZWNJ,ZWJ,ZWJ). These character groups can be inserted between each character of the cover-text, thereby hiding a message. Using Sudoku puzzles. This is the art of concealing data in an image using Sudoku which is used like a key to hide the data within an image. Steganography using sudoku puzzles has as many keys as there are possible solutions of a Sudoku puzzle, which is 6.71×1021. This is equivalent to around 70 bits, making it much stronger than the DES method which uses a 56 bit key. Additional terminology. In general, terminology analogous to (and consistent with) more conventional radio and communications technology is used; however, a brief description of some terms which show up in software specifically, and are easily confused, is appropriate. These are most relevant to digital steganographic systems. The pay low is the data to be covertly communicated. The carrier is the signal, stream, or data file into which the payload is hidden; which differs from the «channel» (typically used to refer to the type of input, such as «a JPEG image»). The resulting signal, stream, or data file which has the payload encoded into it is sometimes referred to as the package, stego file, or covert message. The percentage of bytes, samples, or other signal elements which are modified to encode the payload is referred to as the encoding density and is typically expressed as a number between 0 and 1. In a set of files, those files considered likely to contain a payload are called suspects. If the suspect was identified through some type of statistical analysis, it might be referred to as a candidate. \ Countermeasures and detection/ Detection of physical steganography requires careful physical examination, including the use of magnification, developer chemicals and ultraviolet light. It is a time-consuming process with obvious resource implications, even in countries where large numbers of people are employed to spy on their fellow nationals. However, it is feasible to screen mail of certain suspected individuals or institutions, such as prisons or prisoner-of-war (POW) camps. During World War II, a technology used to ease monitoring of POW mail was specially treated paper that would Steganography in CAD/CAM/PLM. Contents. 13 reveal invisible ink. An article in the June 24, 1948 issue of Paper Trade Journal by the Technical Director of the United States Government Printing Office, Morris S. Kantrowitz, describes in general terms the development of this paper, three prototypes of which were named Sensicoat, Anilith, and Coatalith paper. These were for the manufacture of post cards and stationery to be given to German prisoners of war in the US and Canada. If POWs tried to write a hidden message the special paper would render it visible. At least two US patents were granted related to this technology, one to Mr. Kantrowitz, U.S. Patent 2,515,232, «Water-Detecting paper and Water-Detecting Coating Composition Therefor», patented July 18, 1950, and an earlier one, «Moisture-Sensitive Paper and the Manufacture Thereof», U.S. Patent 2,445,586, patented July 20, 1948. A similar strategy is to issue prisoners with writing paper ruled with a water-soluble ink that «runs» when in contact with a water-based invisible ink. In computing, detection of steganographically encoded packages is called steganalysis. The simplest method to detect modified files, however, is to compare them to known originals. For example, to detect information being moved through the graphics on a website, an analyst can maintain known-clean copies of these materials and compare them against the current contents of the site. The differences, assuming the carrier is the same, will compose the payload. In general, using extremely high compression rate makes steganography difficult, but not impossible. While compression errors provide a hiding place for data, high compression reduces the amount of data available to hide the payload in, raising the encoding density and facilitating easier detection (in extreme cases, even by casual observation). Applications. Usage in modern printers. Main article: Printer steganography. Steganography is used by some modern printers, including HP and Xerox brand color laser printers. Tiny yellow dots are added to each page. The dots are barely visible and contain encoded printer serial numbers, as well as date and time stamps. Steganography in CAD/CAM/PLM. Contents. 14 Example from modern practice. The larger the cover message is (in data content terms—number of bits) relative to the hidden message, the easier it is to hide the latter. For this reason, digital pictures (which contain large amounts of data) are used to hide messages on the Internet and on other communication media. It is not clear how commonly this is actually done. For example: a 24-bit bitmap will have 8 bits representing each of the three color values (red, green, and blue) at each pixel. If we consider just the blue there will be 28 different values of blue. The difference between 11111111 and 11111110 in the value for blue intensity is likely to be undetectable by the human eye. Therefore, the least significant bit can be used (more or less undetectably) for something else other than color information. If we do it with the green and the red as well we can get one letter of ASCII text for every three pixels. Stated somewhat more formally, the objective for making steganographic encoding difficult to detect is to ensure that the changes to the carrier (the original signal) due to the injection of the payload (the signal to covertly embed) are visually (and ideally, statistically) negligible; that is to say, the changes are indistinguishable from the noise floor of the carrier. Any medium can be a carrier, but media with a large amount of redundant or compressible information are better suited. From an information theoretical point of view, this means that the channel must have more capacity than the «surface» signal requires; that is, there must be redundancy. For a digital image, this may benoise from the imaging element; for digital audio, it may be noise from recording techniques or amplification equipment. In general, electronics that digitize an analog signal suffer from several noise sources such as thermal noise, flicker noise, and shot noise. This noise provides enough variation in the captured digital information that it can be exploited as a noise cover for hidden data. In addition,lossy compression schemes (such as JPEG) always introduce some error into the decompressed data; it is possible to exploit this for steganographic use as well. Steganography can be used for digital watermarking, where a message (being simply an identifier) is hidden in an image so that its source can be tracked or verified (for example, Coded Anti-Piracy), or even just to identify an image. Use by terrorists. When one considers that messages could be encrypted steganographically in e-mail messages, particularly e-mail spam, the notion of junk e-mail takes on a whole new light. Coupled with the «chaffing and winnowing» technique, a sender could get messages out and cover their tracks all at once. Steganography in CAD/CAM/PLM. Contents. 15 An example showing how terrorists may use forum avatars to send hidden messages. This avatar contains the message «Boss said that we should blow up the bridge at midnight» encrypted with mozaiq using «växjö» as password. Rumors about terrorists using steganography started first in the daily newspaper USA Today on February 5, 2001 in two articles titled «Terrorist instructions hidden online» and «Terror groups hide behind Web encryption». In July the same year, an article was titled even more precisely: «Militants wire Web with links to jihad». A citation from the article: «Lately, al-Qaeda operatives have been sending hundreds of encrypted messages that have been hidden in files on digital photographs on the auction site «eBay.com". Other media worldwide cited these rumors many times, especially after the terrorist attack of 9/11, without ever showing proof. The Italian newspaper Corriere della Sera reported that an Al Qaeda cell which had been captured at the Via Quaranta mosque in Milan had pornographic images on their computers, and that these images had been used to hide secret messages (although no other Italian paper ever covered the story). The USA Today articles were written by veteran foreign correspondent Jack Kelley, who in 2004 was fired after allegations emerged that he had fabricated stories and sources. In October 2001, the New York Times published an article claiming that al-Qaeda had used steganography to encode messages into images, and then transported these via e-mail and possibly via USENET to prepare and execute the September 11, 2001 terrorist attack. The Federal Plan for Cyber Security and Information Assurance Research and Development, published in April 2006 makes the following statements: «...immediate concerns also include the use of cyberspace for covert communications, particularly by terrorists but also by foreign intelligence services; espionage against sensitive but poorly defended data in government and industry systems; subversion by insiders, including vendors and contractors; criminal activity, primarily involving fraud and theft of financial or identity information, by hackers and organized crime groups...». «International interest in R&D for steganography technologies and their commercialization and application has exploded in recent years. These technologies pose a potential threat to national Steganography in CAD/CAM/PLM. Contents. 16 security. Because steganography secretly embeds additional, and nearly undetectable, information content in digital products, the potential for covert dissemination of malicious software, mobile code, or information is great». «The threat posed by steganography has been documented in numerous intelligence reports». Moreover, an online «terrorist training manual», the «Technical Mujahid, a Training Manual for Jihadis» contained a section entitled «Covert Communications and Hiding Secrets Inside Images». By early 2002, a Cranfield University MSc thesis developed the first practical implementation of an online real-time Counter Terrorist Steganography Search Engine. This was designed to detect the most likely image steganography in transit and thereby provide UK Ministry of Defence Intelligence Staff a realistic approach to «narrowing the field», suggesting that interception capacity was never the difficulty but rather prioritising the target media. Alleged use by intelligence services. In 2010, the Federal Bureau of Investigation revealed that the Russian foreign intelligence service uses customized steganography software for embedding encrypted text messages inside image files for certain communications with «illegal agents» (agents under non-diplomatic cover) stationed abroad. Distributed Steganography. There are distributed steganography methods, including methodologies that distribute the payload through multiple carrier files in diverse locations to make detection more difficult. For example the U.S. Patent 8,527,779 by cryptographer William Easttom (Chuck Easttom) Methods of computer steganography The results of a comparative analysis of methods for COP are shown in Table 1. Steganographic Brief description of methods the methods Limitations 1.Methods of using the special properties of computer data formats Steganography in CAD/CAM/PLM. Contents. Benefits 17 Margins are 1.1. Methods of expanding in many The low degree of using earmarked for multimedia formats, they secrecy, the transfer of the expansion of are filled with zero small amounts of fields of computer information and are not information limited data formats considered program Ease of use 1.2. Methods of special formatting of text files: 1.3.1. Methods of using the known displacement of words, sentences, paragraphs These methods are based on the change of lines and placement of words in a sentence that is provided by inserting extra spaces between words Acrostic - a special 1.2.2. Methods case of this method (for for selecting certain example, the initial positions of letters letters of each line form (zero code) a Message) 1.2.3. Methods of using the special properties of the field formats are not displayed on the screen 1. The weak performance of the method, the transfer of small amounts of information 2. The low degree of secrecy Ease of use. There is a published software implementation of this method 1.The weak performance of the Easy of use. Has published the Methods based on the use of special "invisible", hidden fields for the organization of footnotes and references (eg, use a black font on a black background) 1.3. Methods The information of hiding places in is usually stored in the Steganography in CAD/CAM/PLM. Contents. 18 the unused floppy disks unused places GMD (e.g., zero-track) method, the transfer of small amounts of information 2. The low degree of secrecy 1.4.Methods of simulating the functions (mimicfunction) The method is based on the generation of text and is a generalization of the acrostic. For the secret message is generated meaningful text, hiding the message 1.5. Methods for removing an identifying header file Concealed message is encrypted and the result identifies the header is removed, there is a need to leaving only the advance pass the encrypted data. The information to the receiver knows in recipient advance of the transfer of messages and is missing a title 1. The weak performance of the method, the transfer of small amounts of information 2. The low degree of secrecy software implementation of this method The resulting text is not suspicious for monitoring network Easy of implementation (White Noise Storm, S-Tools), ensure the implementation of this method with the given algorithm 2. Methods of using redundant audio and visual information 3.1. Methods of using the redundancy of digital photography, digital audio and digital video Digital samples contain very little useful information. They filled more information does not affect the quality of experience that allows you to hide confidential information Due to the introduction of additional information distorted the statistical characteristics of digital streams. To reduce the signs of compromise requires correction of the statistical characteristics Steganography in CAD/CAM/PLM. Contents. Ability to transfer a large amount of hidden information. The possibility of copyright protection, the latent image of the brand, registration numbers, etc. 19 As can be seen from Table 1, the first direction based on the use of special properties of computer data formats, rather than redundancy itself the data. Special properties of selected formats, taking into account protection of concealed message from the immediate listening, viewing or reading. Based on the analysis of materials, we can conclude that the main direction Steganography is the use of computer and audio visual redundancy Information. As the preliminary analysis, the use of steganography methods for solving is possible in principle. However, all The methods have the following disadvantages: The set of possible implementations is countable, and of course, that allows for a simple brute-force attack methods, although it requires considerable computational cost. Not all implementations are consistent with the possibility of hardware implementation. Theme 2. Computer steganography: classification, benchmarking methods and tools. Questions for self-examination and discussion at the workshop. 1) Structure of steganography. 2) Comparative analysis of the basic methods and tools of computer steganography. 3) The study of open-source products. Literature to explore themes. 1. Gribunin V.G. Binding I.N., Turintsev I.V. Digital Steganography. M.: SOLON-Press, 2002. – 272 pp. 2. Lin Ch-Y., Chang Sh.-F. Distortion Modeling and Invariant Extraction for Digital Image Print-and Scan Process. International Symposium on Multimedia Information Processing, 1999. P. 10. 3. Lin Ch-Y., Chang Sh.-F. Public Watermarking Surviving General Scaling and Cropping: An Application for Print-and-Scan Process. Multimedia and Security Workshop at ACM Multimedia, 1999. Steganography in CAD/CAM/PLM. Contents. 20 2. Algorithms for digital steganography 2.1. Algorithms for embedding data in the spatial domain The advantage of these algorithms embedded in the spatial domain is the fact that data is introduced in the original image, and there is no need to perform computationally cumbersome linear transformations of images. Data implemented by manipulating the brightness and color components. Most of the algorithms embedded in the spatial domain lata images based on the use of broadband signals. The basic idea behind the use of steganography is that the data is embedded in the noise signal of low power. Since the signal of low power, the data used to protect noiseresistant codes. 2.1.1 The algorithm Kutter Kutter algorithm assumes that the image has RGB encoding. Embedding is performed in the blue channel, since the blue color of the system least sensitive of human vision. - embedded bits, - container, - pseudo-random position in the which the attachment. The secret bits embedded in the blue channel by modifying the brightness Where - constant, which determines the energy of the embedded signal. Its value depends on the of the scheme. The more , the higher the robustness of investing, but the greater his visibility. Removing the bit carried by the recipient without his original image, that is blind. To do so runs the prediction value the original, unmodified pixel based on the values of its neighbors. Also, there is a modification of this algorithm, which for assessment using pixel values of several Steganography in CAD/CAM/PLM. Contents. 21 pixels located in the same column and the same line. In this case, the assessment has the form: Where ( - the number of pixels from the top (bottom, left, right) of the estimated pixel ). So in the process of embedding each bit of CEH was repeated times, we get cr estimates one bit. The secret is a bit after averaging the difference between estimates pixel and its real value The sign of this difference determines the value of embedded bits. This algorithm does not guarantee the faithful always determine the value of the secret bits both as a function of extracting bits is not the inverse function embedded. Algorithm is robust to many of the known attacks: low-pass filtering image, its compression, in accordance with the algorithm of JPEG, cutting edges. 2.1.2. Algorithm Bruyndonckx To improve the immunity applies Code Bose-Chaudhuri-Hokvingema (BCH). Implementation is carried out by modifying 8x8 block of luminance pixels. The process of embedding is carried out in three stages: Classification of pixels within the block into two groups with approximately uniform brightness. Split each group into categories defined by this grid. Modification of medium brightness values of each category in each group. In the classification there are two types of blocks: blocks with contrast and noise units with distinct differences of brightness. In blocks of the second type of zone different brightness do not have to lie close to each other, not must contain an equal number of pixels. Moreover, some pixels in general can not belong to any one zone. In the first type of blocks classification is particularly difficult. Steganography in CAD/CAM/PLM. Contents. 22 To perform the classification of the brightness values are sorted in ascending order. Further is the point at which the slope of the tangent to the resulting curve is maximal. This point is the boundary separating the two zones in the event that the slope of greater than a certain threshold. Otherwise, the pixels are divided equally between the zones. To sort by category to the pixel blocks are superimposed masks are different for each zone and each block. Purpose is to provide a mask of secrecy implementation. The set of pixels was divided into five subsets: two bands, two category, and the pixels not belonging to any zone (for the blocks of the first type). - the average brightness for the pixels of the two zones and categories. Embedding a bit CEH (option) and the equality of brightness values in the each zone is provided by: and CEH extraction algorithm is the inverse algorithm implementation. At the same time calculated the average values of brightness, and there are differences 2.1.3. Algorithm Langelaar This algorithm also works with blocks of 8x8. First, it creates pseudorandom mask of zeros and ones of the same size subunit value, and and In addition, each block is divided into two , depending on the mask. For each subunit calculates the average brightness . Next, choose a threshold , and a bit of CEH is built as follows: If this condition is not fulfilled, it is necessary to change the brightness values of pixels subunit . To remove the bits of CVD calculated average luminance subblocks - , Steganography in CAD/CAM/PLM. Contents. . The 23 difference between them to determine the required bits: 2.1.4. Algorithm Pitas In this algorithm, the CEH is a two dimensional array of bits the size of image, and the number of units it is equal to the number of zeros. There are several versions of the algorithm proposed Pitasom. Initially proposed to incorporate bits of CVD in each pixel of the image, but then wisely decided to use for this target blocks of 2x2 or 3x3 pixels, which makes the algorithm more robust to compression or filtering. CEH is added to the image: . In the case of a detector block for the introduction of CEH calculates the average brightness value of the block. Hence it is possible to uneven implementation of CEH in pixels, that is, the value of . Thus it is possible to obtain CEH is optimized by the criterion of robustness to the procedure of the compression algorithm JPEG. To do this 8x8 block elements are calculated in advance, "capacity" of each pixel (taking into account DCT quantization matrix, and JPEG). Then CEH implement in accordance with the calculated capacity. This optimization is done once and for all, and found the mask is applied for each image. 2.1.5. Algorithm Rongen In this algorithm, as well as in the algorithm Pitas, CVD is a two-dimensional matrix of ones and zeros to be approximately equal to their number. The pixels in the that you can implement one (ie robust to distortion), are defined in the the basis of a characteristic function (the characteristic pixels). This function can be computed locally, based on analysis of adjacent pixels. Characteristic pixel is approximately one hundredth of the total, so not all CVD unit is incorporated into these positions. To increase the number of characteristic of pixels, if necessary, is proposed to small predistortion image. The detector finds the values of the characteristic pixel, and compares with the best of him CEH. If the image does not contain CEH, then the characteristic pixels of ones and zeros will be roughly equal. 2.1.6. The algorithm PatchWork Steganography in CAD/CAM/PLM. Contents. 24 The algorithm Patchwork is a statistical approach. Initially pseudo-random manner on the basis of two key selected pixel. Then the brightness of one of them is increased by a value (from 1 to 5), the value of brightness of the other - is reduced to the same value. Further, this process is repeated large number of times (~ 10000) and is the sum of all differences. By value this amount is judged on the presence or absence of CVD in the image. The values of selected pixels in each step - и , the increment - . The sum of the differences of pixel values. Expected value (the sum of the difference of pixel values in an empty container) is close to zero for sufficiently large n. Expected value will be more . is a Gaussian distribution. In detektor accordance with the key value is checked and if it is significantly different from zero, the decision on the presence of data. To improve the robustness algorithm instead of individual pixels, you can use blocks, or patches (hence the name of the algorithm). Patchwork algorithm is sufficiently resistant to compression operations image, its truncation, change the contrast. The main drawback of the algorithm is its instability to affine transformations, i.e., rotate, translate, scale. Another disadvantage is the low bandwidth. Thus, the The basic version of the algorithm for the transmission of a bit of a hidden message requires 20,000 pixels. 2.1.7. Algorithm Bender Bender's algorithm is based on copying blocks of randomly selected texture area to another, which has similar statistical characteristics. It leads to the appearance of the image is completely identical blocks. These blocks can be be found as follows: Analysis of the autocorrelation function stego and finding the peaks. Shift the image in accordance with these peaks and subtracting the image from its shifted copy. Steganography in CAD/CAM/PLM. Contents. 25 The difference in locations of pirated units should be close to zero. Selects a threshold value and smaller than this threshold in absolute value are considered to be the desired blocks. Since copies of the blocks are identical, they vary in the same transformation the entire image. If we make the block size is sufficiently large, then the algorithm will resistant to most of distortion. Algorithm is robust to filtering, compression, image rotation. The main drawback of the algorithm is the complexity of finding an exceptional area, the blocks of which may be substituted without any noticeable degradation in image quality. But addition, this algorithm as the container can be used just enough texture images. 2.1.8. Method of LSB LSB (Least Significant Bit, LSB) - the essence of this method is to replace the least significant bits in the container (images, audio or video) to the obscure bits. The difference between empty and filled containers should not be perceptible to human senses. The method is as follows: Suppose there are 8-bit grayscale image. 00h (00000000b) denotes the color black, FFh (11111111b) - white. In total there are 256 levels . Also assume that the message consists of a byte - for example, 01101011b. By using two low-order bits in the descriptions of pixels, we need 4 pixels. For example, they are black. Then the pixels that contain a hidden message will appear as follows: 00000001 00000010 00000010 00000011. Then change the color of pixels: the first - 1/255 second and third - to 2/255 and the fourth - 3/255. Such gradations, besides that invisible to humans, might not appear when using low-quality output devices. LSB methods are unstable for all kinds of attacks and may be used only in the absence of noise in the data channel. Detection of LSB-encoded stego carried out by the anomalous characteristics of the distribution range of values of bits of digital signal samples. All methods of LSB are usually additive. Theme 3. Digital steganography: the terminology, classification and comparative analysis methods and tools. Questions for self-examination and discussion in seminars. 1) The historical methods of hiding data. Adopted terminology. 2) Theoretical principles of digital steganography based on the terminology used. 3) Comparative analysis of the means of digital steganography. Literature to explore themes. Steganography in CAD/CAM/PLM. Contents. 26 1. Gribunin V.G. Binding I.N., Turintsev I.V. Digital Steganography. M.: SOLON-Press, 2002. – 272 pp. 2. Kutter M. Watermarking Resisting to Translation, Rotation, and Scaling. Signal Processing Laboratory, 1998. P. 10. 3. Kutter M. Digital Signature of Color Images using Amplitude Modulation. Signal Processing Laboratory, 1997. P. 9. 4. Herrigel A., Pereira S., Petersen H. Secure Copyright Protection Techniques for Digital Images. International Workshop on Information Hiding, 1998. P. 22. 5. Ramkumar M. Data Hiding in Multimedia – Theory and Applications. New Jersey Institute of Technolog, 1999. P. 70. 6. Bender W. Applications for Data Hiding. IBM Systems Journal, 2000. P. 22. 7. Chae J., Manjunath B. A Robust Data Hiding Technique using Multidimensional Lattices. Proc. IEEE Conference on Advances in Digital Libraries, 1998. P. 8. 8. Chae J., Manjunath B. A Technique for Image Data Hiding and Reconstruction without Host Image. Proceedings of the SPIE - The International Society for Optical Engineering. 1999, P. 9. Cuche E., Marquet P., Spatial filtering for zero-order and twin-image elimination in digital offaxis holography. Applied Optics V.39, 2000. P. 4070–4075 3. Embedding data to transformation fields algorythm Real images are not realey random processes with even magnitude distribution. It is well known fact which is being used in compression algorythms, that most of the energy of the image is concentrated in the bottom of the spectrum. That's why one need to decompose the image to subbands. Stegomessage is mixed to the subbands of the image. Low frequency subbands contain most of the energy, thus having a noisy nature. High frequency are more exposed to different processing algorythms, whether it is compressing or Low Pass Filtration. Thus the best candidate for message embedding is middle frequency subbands of the image spectrum. Typical image noise distribution and image frequency spectrum processing is shown on Fig.3 Steganography in CAD/CAM/PLM. Contents. 27 Fig.3. Image noise and processing noise versus frequency Processing noise appears as a result of transformant coefficients quantization. It can be treated as reduction of correlation between the original image transformant coefficients and quantizated coefficients. For example at high levels of compression a situation can occur, when full subbands are discarded. I.e. in general noise dispersion in this subbands is infinite. There is a reduction of correlation between subband coefficients before and after quantization. To achieve acceptable results one need to average the processing noise level over many images. Transformations may be sorted by achieved gainings from encoding [13], single, Adamar's, Haar's, DCT, Wavelet. Gaining from encoding is refered to as a level of transformation coefficients dispersions redistribution. The greatest advantage gives Karhunen-Loeve transformation (KLT), the smallest - the expansion in the basis of a single pulse (ie, no conversion). The transformations that have high values of the gains from coding such as DCT, wavelet-transformation, characterized by dramatically uneven distribution of the variances of the coefficients of subbands. High-frequency subbands not suitable for investment because of the large noise processing, and bass - because of the high-noise images. So you have to be limited midranges bands in which the image noise is approximately equal to the noise processing. Since these bands a bit, then the bandwidth stegokanala small. In the case of conversion of lower gains from coding, such as Hadamard or Fourier series, there are more blocks in which the image noise is approximately equal to the noise processing. Consequently, the capacity of the above. Therefore, to increase the capacity of steganographic channel is better to use a lower conversion gain from coding, poorly suited for compression of signals. The effectiveness of the wavelet-transformation and DCT for image compression due to the fact that they are well modeled in the image processing mid-frequency request, separated by «significant» part of «insignificant». Hence, they are more appropriate to apply in the case of the active offender, as a modification of significant factors could lead to an unacceptable distortion of Steganography in CAD/CAM/PLM. Contents. 28 the image. In applying the transformation to the low values of the gains from coding violations there is a risk investments, because the conversion factors are less sensitive to modifications. Fig.4. Block of pixels (8x8) with the location of the DCT coefficients. 3.1 Embedding data in a discrete cosine transformation coefficients When we use this method, the container is divided into blocks of 8x8 pixels. DCT is applied to each block, resulting in a matrix of dimension 8x8 DCT coefficients. The coefficients are denoted by , where the - block number, 3 - the position of the coefficient within the block. If the block is scanned in a zigzag manner (as it is in JPEG), the coefficients are denoted by . The coefficient in the upper left corner is usually called the DC-coefficient. It contains information about the brightness of the entire block. The other coefficients are called ACcoefficients. Sometimes it runs monetary policy of the entire image, rather than individual units. Next, we consider some of the algorithms for implementing DCT in the field of DWM. 3.2 Koch algorithm In this algorithm in a block of 8x8 by embedding 1 bit of DWM. We describe two implementations of this algorithm can be selected pseudorandomly two or three DCT coefficients. We consider the variation of the algorithm with two selectable coefficients. Embedding information in the following manner: for the transferring of 0-bit is necessary to ensure that the difference between the absolute values of the coefficients would be greater than Steganography in CAD/CAM/PLM. Contents. 29 some positive value, and for the transferring of the 1-bit of this difference is less than some negative value: 3.3. Benham algorithm This algorithm is an improved version of the previous one. Improvements carried out in two directions: to embed all the blocks are not used, but only «suitable» for this, within a block are selected for embedding not two, but three coefficients, which reduces distortion. Suitable for building information blocks are images that are not too smooth, nor does it contain a small number of circuits. For the first type of blocks is characterized by the vanishing of the high-frequency coefficients, for the second type - very large values of several low-frequency coefficients. These features are the cut-off criterion of unsuitable units. When embedding a bit DWM pseudorandomly selected three coefficients DCT block. If you want to invest 1, the coefficients vary so much (if required) that the third factor was less than each of the first two, if you want to embed a 0, it is more than the others. In the event that such a modification would lead to degradation of the image is too large, the coefficients do not change, and this block is simply not used. Changing the three factors instead of two, and even more so the rejection of the changes in the case of unacceptable distortion reduces the error introduced by the DWM. The decoder will always be able to determine the block in which DWM is not built by repeating the analysis performed in the coder. 3.4 Podilchuk algorithm This algorithm requires the presence of the source image from a detector in the detection of a DWM. Embedded data simulated real random process with normal distribution, unit variance and zero mean. For each DCT coefficient is determined by the threshold value, above which the change could lead to degradation of the image. This threshold depends on the position of the coefficient in the matrix (i.e., the frequency range over which it is responsible). In addition, the threshold is due and the properties of the image: contrast and brightness of the block. Embedding is as follows: if the absolute value of the coefficient is less than the threshold, it does not change. Otherwise, it is added to the product of the threshold values and the values of DWM. When it detects a DWM, first the coefficients of the original image are subtracted from the corresponding coefficients of the modified image. Then calculated the correlation coefficient, and established the fact of a DWM. Steganography in CAD/CAM/PLM. Contents. 30 3.5 Hsu algorithm In this algorithm, the decoder DWM also requires the original image. However, the decoder determines not the fact of DWM, and distinguishes built-in data. As the DWM appears black and white image is half the size of the container. Before embedding the image subjected to random permutations. DWM is embedded in the mid-DCT coefficients (the fourth part of the total). These coefficients are located along the second diagonal DCT. For embedding DWM bit coefficient in the it is necessary to find the sign of the difference of the coefficient of the current block and the corresponding coefficient from the previous block: If you need to build 1, the coefficient change so that the sign of the difference was positive, if 0 - so that the sign of the difference was negative. There are a number of improvements to the basic algorithm. First, instead of the values of the coefficients, you can use their absolute values. Second, instead of the coefficient of the previous block, you can use DC-coefficient of the current block. It also takes into account the process of quantization of the coefficients: Another improvement of this algorithm is the sorting order in which blocks of the DWM are arranged in descending order in which the number of units. The blocks of the original image and the container are arranged in descending order of variances. After that holds the corresponding embedding data. This algorithm is not robust with respect to the JPEG-compression. 3.6 Cox algorithm This algorithm is robust to many signal processing operations. Detection of integrated DWM it is done using the original image. Insertion data represent a sequence of real numbers with zero mean and unit variance. For investment information using multiple AC-DCT coefficients of images with the greatest vigor. The author suggests three ways to embed DWM according to the following expressions: The first version can be used when energy is comparable to the energy DWM modifiable factor. Otherwise, either DWM will not robust or distortion is too large. Therefore, it is to embed the information is possible only with a slight change in the range of energy values of the Steganography in CAD/CAM/PLM. Contents. 31 coefficients. When it detects a DWM performs the reverse operation: compute DCT original and modified images, found the difference between the coefficients of the highest magnitude. 3.7 Barni algorithm This algorithm is an improvement of the Cox algorithm, and it also holds monetary policy of the entire image. It is no longer required detection of the source image, that is, the scheme blind. To embed a DWM are not used most AC-coefficients, and average in size. As the DWM performs an arbitrary bit string. The selected coefficients are modified as follows: Then the inverse DCT is performed and produced an additional processing step: the original and modified images are combined with weighting coefficients: Here, for the textured areas (in which the human eye is very sensitive to the added noise) and in the homogeneous regions. The value of is not for every pixel individually, and for non- overlapping blocks of fixed size. For example, as expedient to use the normalized variance of the blocks. In the DWM detector computed the correlation between the modified image and DWM, 3.8 Additive algorithms Algorithms for additive introduction of information are in a linear modification of the original image, and its recovery in the decoder is the correlation methods. In this DWM is usually added to the image container, or «fusion» in it. 3.8.1 Algorithms based on the linear data embedding In the additive methods of implementing the DWM is a sequence being implemented in the selected subset of samples of the original image commonly used expression for the embedding of information in this case: where- weighting factor, - a modified pixel. Another way to embed the watermark was proposed by Cox: Steganography in CAD/CAM/PLM. Contents. of length , which is . The main and most 32 or, with the using logarithms of the coefficients For installation in accordance with the first formula, DWM in the decoder can be found as: Here, extracting the mean a counts of the resulting image, whether or not containing CEH . After compared with the original CEH. With that as a measure of identity watermark value is the correlation coefficient sequences: This value varies in the range [-1, 1]. Values close to unity, indicate that the extracted sequence are most likely to match the built-in data. Therefore, in this case, it is concluded that the analyzed image contains a watermark. In the decoder can be installed a certain threshold, (here - default standard deviation), which determines the probability of errors of the first and second kind, when detecting DWM. The coefficient can not be permanent, and adaptively change according to the local properties of the original image. This makes the watermark more robust (resistant to removal). To increase the robustness of the implementation of the algorithms used in many broadband signals. At the same information bits can be repeated many times, are encoded using the correction code, or these may be applied to any other conversion, after which they are modulated with a Gaussian pseudo-random sequence. This sequence is a good model of the noise present in real images. At the same time synthetic images (created on the computer) do not contain noise and are difficult to seamlessly integrate a sequence. To extract the embedded information in the additive embedding scheme is usually necessary to have a CEH source image that is strong enough limits the scope of such methods. There are also blind extraction methods CEH [15], compute the correlation sequence of the coefficients of the resulting image : Steganography in CAD/CAM/PLM. Contents. with all 33 Then, the resulting value of the correlation coefficient is compared with some threshold of detection The main disadvantage of this method is that the image itself, in this case is regarded as a noise signal. There is a hybrid approach (half-blind scheme), when the information about the original image is available in the retrieval of information, but do not know the actual original image. The correlation method can only detect the presence or absence of DWM. For all the same bits of information needed to test all possible sequences, which is extremely computationally complex task. 3.9 Algorithms based on the merger of the CEH and the container If instead of a sequence of pseudorandom numbers is embedded in the image another image (eg company logo), the corresponding algorithms are called algorithms implementing the merger. The size of messages being introduced much smaller than the original image. Before embedding, it can be encrypted or transformed in some other way. Such algorithms have two advantages. First, you can prevent a distortion of the hidden message, because people will still be able to recognize it. Secondly, the presence of an embedded logo is a more convincing proof of ownership than the presence of a pseudo-random numbers. 3.10 The algorithm Chaya (Chae) The algorithm is implemented in black and white image (logo), up to 25% of the size of the original image. Before embedding the one-level decomposition is performed as an original image and logo with the Haar filter. The wavelet coefficients of the original image are denoted as wavelet coefficients of the logo - , and . The modifications are all conversion factors. First, the coefficients of each sub-band as the original image and the logo is represented by 24 bits (of which one bit is assigned to the sign). Since the size of the logo is 4 times smaller than the original image, it is necessary to increase the number of its coefficients. For this purpose, the following steps. Denote by A, B, and C, respectively, senior, middle and low bytes of the 24 - bit representation of the logo. High byte of each of these numbers represents, respectively, A, B, or C, Steganography in CAD/CAM/PLM. Contents. 34 the other two bytes are filled with zeros. Then, the advanced four unit factors logo. He then added to the element-wise 24-bit version of the original image The resulting value is displayed back to the original scale based on the minimum and maximum values of the coefficient of subband. After that is the inverse discrete VI. To remove the CEH used inverse formula This algorithm makes it possible to hide a fairly large amount of data in the original image up to a quarter of the size of the original image. 3.11 The algorithm Kandar (Kundur) Also, as in the algorithm, Chaya, and implemented the original images are of the wavelet transform. Used to embed all the coefficients of detailed subbands. Many of these factors is divided into non overlapping blocks of size are denoted , where and . The blocks and , respectively, the location factor and the level of resolution. The watermark is added to the elements of the original image as follows: – where where scale factor, calculated by the formula: – weighting matrix, which determines the frequency sensitivity of the system view of the person, - operator of the DFT. Thus, the algorithm uses a fairly complex model of human of view. For detection in the detector can be used as the calculation correlation function, and visual comparison. 3.12 Algorithms based on the quantization By quantization we mean the process of mapping a large (possibly infinite) set of values with a finite set of numbers. It is clear that this is accompanied by a decrease of information due to its distortion. The quantization is used in compression algorithms. There are scalar and vector quantization. In vector quantization, as opposed to a scalar, the map is not of a single frame, and their combination (vector). From information theory it is known that vector quantization on the Steganography in CAD/CAM/PLM. Contents. 35 effective scalar degree of compression, having a greater complexity. In steganography are used both types of quantization. In the encoder quantizer entire range of the original set is divided into intervals and each interval representing the number of his chosen. This number is a code word and the quantizer is usually the centroid of the interval of quantization. The set of code words is called a workbook quantizer. All values that fall in this interval are replaced by the encoder to the corresponding code word. In the decoder, the number of accepted matches a certain value. Quantization interval is usually referred to as quantizer step. Embedding data using the quantization refers to non-linear methods. Transmitted message has limited power to perform its stealth requirements. Interference is the original signal and another Gaussian noise - noise processing (quantization). Encoder source signal is known, the decoder has to retrieve CVD without the knowledge of both components of the noise. There are numerous methods to improve Costas (to combat the noise), consisting in the use of structured quantizers (eg, lattice or a tree). Most preferably, the introduction of information in the spectral region of the image. If this linear methods are used, then the embedding CEH produced in the middle of the band. This is because the energy of the image is concentrated mainly in the low-frequency (LF) region. Consequently, the detector CEH in this area there is a loud noise of the signal. In the highfrequency (RF) fields of the noise has a large amount of processing, such as compression. In contrast to the linear and nonlinear circuits embedded information can be used bass region, since the power being introduced CEH does not depend on the amplitude ratios. This is explained by the fact that the non-linear algorithms to hide the correlation detector is not used, the coefficients of small and large amplitude are treated equally. Section 4. Classification and comparative analysis of methods and means of embedding data into various containers. Questions for self-examination and discussion in seminars. 1) adopted terminology. 2) Theoretical principles of steganography based on the terminology used. 3) Comparative analysis of the means of embedding data in a variety of containers. Literature to explore themes. 10. Gribunin V.G. Binding I.N., Turintsev I.V. Digital Steganography. M.: SOLON-Press, 2002. 272 pp. 11. Kutter M. Watermarking Resisting to Translation, Rotation, and Scaling. Signal Processing Laboratory, 1998. P. 10. Steganography in CAD/CAM/PLM. Contents. 36 12. Kutter M. Digital Signature of Color Images using Amplitude Modulation. Signal Processing Laboratory, 1997. P. 9. 13. Herrigel A., Pereira S., Petersen H. Secure Copyright Protection Techniques for Digital Images. International Workshop on Information Hiding, 1998. P. 22. 14. Ramkumar M. Data Hiding in Multimedia – Theory and Applications. New Jersey Institute of Technolog, 1999. P. 70. 15. Bender W. Applications for Data Hiding. IBM Systems Journal, 2000. P. 22. 16. Chae J., Manjunath B. A Robust Data Hiding Technique using Multidimensional Lattices. Proc. IEEE Conference on Advances in Digital Libraries, 1998. P. 8. 17. Chae J., Manjunath B. A Technique for Image Data Hiding and Reconstruction without Host Image. Proceedings of the SPIE - The International Society for Optical Engineering. 1999, P. 18. Cuche E., Marquet P., Spatial filtering for zero-order and twin-image elimination in digital offaxis holography. Applied Optics V.39, 2000. P. 4070–4075 4. A choice of a method of embedding of DWM (digital watermark) in the image-container Embedding of DWM is possible thanks to peculiarity of system of perception of the person. It is well known that images possess big psychovisual redundancy. The eye of the person is similar to the low-frequency filter therefore especially imperceptible there are distortions in high-frequency area of a range of spectrum. For negotiation of influences of a printing-down and scan-out the most successful there were the methods which have received the name of the modulations methods of the image-container, and modulation can be carried out both in frequency [2-5], and in spatial areas of the image [7,8]. For compensation of geometrical distortions such as shift, turn and change of scale of the image is used the polar logarithmic system of coordinates with a corner and logarithmic radius on axes of coordinates [3] or is applied transformation of Mellinga [2] invariant to turn and scale. In case introduction of DWM in frequency area of modulation are exposed peak components of a complex range of the image container [3] . For this purpose previously is made calculation peak and phase partials components of transformation of Fourier. For a characterization of consequences of the geometrical distortions connected with casual turn, shift or scale change, in the image-container, except DWM, the imagetemplate [9] is built in. In case introduction of DWM in spatial area the signal of DWM is built in by modulation of the initial image-container, and extraction DWM (demodulation) is carried out by means of a linear filtration of the image [7]. If the image is color, a signal of DWM takes root by updating of values of pixels into Blue channel the RGB of the image [8]. Updating is carried Steganography in CAD/CAM/PLM. Contents. 37 out either addition, or subtraction depending on value of the introduced bit of DWN of brightness of the image-container. 4.1. The methods using as containers audiofiles For reliable concealment of data in the acoustic channel the system of concealment must reply the following requirements: to be resistant to everywhere used algorithms of compression with losses not to bring in a signal distortions perceived by human hearing not to bring appreciable changes in container statistics De facto a standard format of sound files at the moment is the MP3 format. Therefore, work not defiant suspicions of stegosystem in the acoustic channel should be based on this format. MP3 - the full name MPEG 1 Layer 3 - a format of coding of the sound files, entering into a standard of coding of a image information of MPEG 1. Basic feature of a format is compression with losses: after packing and unpacking of the sound file by means of MP3 result isn't a bit-by-bit copy of the original. Over again, when coding insignificant components are purposefully excluded from a packed signal. At preservation of acceptable quality, a MP3 allows to compress sound data in ten and more times. It is reached by the accounting of features of human hearing, including effect of masking of a weak signal of one range of frequencies more powerful signal of the next range when it takes place, or a powerful signal of the previous frame causing temporary falling of sensitivity of an ear to a signal of the current frame (minor sounds are removed which aren't heard by a human ear because of existence during this or previous moment of another, louder ). It is considered as inability of the majority of people to distinguish signals, on capacity lying below a certain level, a miscellaneous for different frequency ranges. This process is called as adaptive coding and allows to save on the least significant from the point of view of perception the person sounding details. Extent of compression (therefore and quality), is defined by width of a data flow set at coding - bitrate. As well as in the considered case of introduction of information in images, algorithms of introduction in audiofiles place hidden data or in an uncompressed signal before its compression, or it is direct in the compressed signal - as a rule, in entropic compressed coefficient of transformation. Some methods as use for concealment not an audiosignal as that, and various features and office information of files-containers. Steganography in CAD/CAM/PLM. Contents. 38 Let's consider at first algorithms of concealment of data in an uncompressed sound stream. 4.2 Broadband coding. In a signal is added modulated by the message the noise with amplitude slightly above a masking limit . Advantage of this scheme is effectiveness performance and high capacity, a shortcoming - heard distortions brought in a signal. At concealment of one bit in sequence of coefficient the target sequence is calculated as follows: where - casual binary sequence, - threshold of audibility of i subband , - the hidden bit. For calculation of a threshold of audibility the can be used psychoacoustic model containing in a format of coding of a MP3, or any other . Thus, the method allows to operate psychoacoustic nature of distortions brought in a signal. For extraction of the hidden bit from sequence of coefficient is used function of correlation of the accepted coefficient and initial casual sequence. It should be noted that because of unreliability of extraction this method demands use of codes of correction of mistakes. It leads to reduction as speed, and capacity of a method. 4.3 Phase coding. In this method that fact is used that the human ear perceives not values of a phase, but only their difference. The signal breaks into segment, values of a phase on the first segment are used for coding of the hidden message, value of phases of other segment so that the difference of phases between segment remained invariable. For coding of values of phases, on a crowd of phases is allocated the set of evenly distributed values corresponding to bits 0 and 1. Value of a phase is replaced with the next value corresponding to the demanded bit. The difference of values in a set depends on frequency of a strip, and varies from sensitive strips to on on high-frequency strips. For coding of one bit of the hidden message is used a certain sequence of changes of phases, various for coding 0 and for coding 1. For extraction of the hidden message the following Steganography in CAD/CAM/PLM. Contents. function of detection is used: 39 where - amplitude and the phase i-go of the received signal. - expected sequence of phases in the process of coding bit 1. - expected sequence of phases in the process of coding bit 0. and - the next to the values of phases corresponding 1 and 0. If , the bit of the hidden message is accepted equal 1, differently 0. Method provides high efficiency of coding by criterion of the signal/noise, however its capacity of the relation is insignificant, and makes from 8 to 32 bits a second. 4.4 The echo-coding. Uses non-uniform intervals between an echo-signals for coding of sequence of values. When overlapping a number of restrictions be observed condition of obscurity for human perception. The echo is characterized by three parameters: initial amplitude, extent of attenuation, delay. At achievement of a certain threshold between a signal and an echo they mix up. In this point of people can't distinguish these two signals. It is difficult to define existence of this point, as it depends on quality of initial record and the listener. As a rule, the delay about one thousand second that is quite acceptable for the majority of records and listeners is used. Two various delays are used at zero and unit coding. These both delays should be less, than a threshold of sensitivity of an ear of the listener to a received echo. 4.5 Noise replacement. In this method that fact is used that the human ear perceives not so much a form, how many energy of noise. As in the MP3 format is completely coded the form noisy frequency subband , data subband can be used for concealment of data. The entrance signal is transformed to frequency area by means of the modified discrete cosine transformation (MDKP) used in a MP3. At concealment of one bit in sequence of coefficient, the target sequence is calculated as follows: где - Random binary sequence, Steganography in CAD/CAM/PLM. Contents. 40 When extracting the hidden bits, as in the case of wideband coding using the correlation function of the coefficients and adopted the original random sequence. As proposed to use the noisy bands with frequencies above 5 kHz. It should be noted that the method is stable with respect to the MP3 compression, since the algorithm MP3 encoding does not change the signs of the coefficients MDKP. Capacity method ranges from 20 to 60 bits per second. The method also quite simple to implement, because it is based on widely implemented on different platforms MDKP algorithm, which is a part MP3 encoder. In general, methods of hiding data in an uncompressed audio stream are a number of serious disadvantages: Possible visibility when listening; Limited bandwidth; Implementation complexity. Introduced into the signal unnatural distortion in the signal, such as white noise a certain amplitude, discrete phase of the signal, etc., can be high probability of finding the specific methods of detection. Thus, the algorithms are more promising to reveal more details 'Directly into the compressed MP3 stream'. At the current time is invited to a series of algorithms that use the data to hide proprietary information MP3, the most famous of these is the ability to 'mp3stego'. This algorithm modifies MP3 encoding process, so that the LSB official fields frame MP3, for example, the volume of information within the main frame coincide with the current bit obscure. The features of the method are almost unnoticeable when listening; high complexity of implementation and slow work, as it is necessary to complete the entire MP3 encoding process, the capacity of 50 bits per second. It should be noted that the information entered in the Service lead to changes discrepancies in the results of these methods with the results of the standard Encoder MP3. Such changes can be detected with high probability the enemy. As a faster alternative, we proposed a method of concealment data using a particular format MP3 - interframe gaps. Steganography in CAD/CAM/PLM. Contents. 41 The data stream consists of MP3 frames - plots the data encoding 26ms audio signal. Each frame contains a 4-byte header containing a synchronizing word and service information. Service information includes, in particular, the version format, stereo mode and bitrate. These values uniquely determine the frame size. The number of bytes needed to compress the sound with a given quality depends on the characteristics of a particular sound. Thus, the difficult to compress signal sections with more detail requires more bytes than the simple ones. On this basis, MP3 allows for storage of compressed data frame in the remaining unoccupied bytes the previous frame. In order to properly positioned in the frame header specifies the offset to the beginning of the data. Tag end of the data itself is not, decoding stops at the end extracting the required number of cosine transform coefficients. Any information between the end of one frame and the beginning of the next data the frame is ignored decoder, respectively, that is where you can place hidden data. To do this, the frame size increases by increasing its bit rate by one level, for example, 128kbits / c up to 160kbit / c. This method does not introduce any distortion in the sound-box, easy, fast has a large bandwidth (about 20% of the container). However, knowing concealment algorithm is easy to detect the presence of hidden information, based on from the fact that the standard MP3 stream is no «extra» bytes. Thus, the method can be used only when needed rapid transfer of large amount of information and is not expected serious opposition the enemy. The most resistant to the discovery of a method for concealing errors in the quantization MP3 of the coefficients. MP3 encoding is built in a classic case of compression with losses, which consists of three steps: Convert the signal to a lot of information about the signal was concentrated in a small number of coefficients. In the MP3 used a modified discrete cosine transform. Quantization, that is, dividing the coefficients obtained for certain values and then rounding the result to the nearest whole number. At this stage there is a loss of information. The values of the quantization of dividers to MP3 evaluated on the basis of a given bit rate and the psychoacoustic model that determines the maximum allowable noise level. The entropy of lossless compression. In MP3 compression is used with static Huffman codes. Obtained during the quantization integer coefficients can be directly used for hiding data, eg by embedding in the least significant bit. This, however, introduces considerable noise in the Steganography in CAD/CAM/PLM. Contents. 42 output signal and with high probability can be detected. Can be used to conceal only part of the coefficients, choosing them as to minimize the distortion introduced. Since the modified rate differs from the original by not more than 1, minimizing the total deviation from the original signal is reduced to the selection coefficients with the fractional part is close to 0.5. In addition, to maintain the structure stream of compressed data, the coefficients are selected, the modification which does not change size of the encoding of speech, in particular, are discarded with zero coefficients value. There is a problem decoding at the receiver - decoder has no information about what factors are used to hide, that is, message should be presented as a function of the decoder to a known vector of bits all the coefficients, as used, or not. Using this as a multiplication by a function common to the sender and receiver given by secret key matrix, a system of linear algebraic equations, which the sender solves for the vector-bit coefficients. Do not be modifying factors determine the values of some variables. Maximally possible size of the message, in which the system has a solution tends to the number of modifiable factors in the increase of the number thus, the method allows no loss of capacity used to hide arbitrary elements of the container. Structure of entropy coding in MP3 imposes additional restrictions on permissible to modify the coefficients. The coefficients in the one block divided into three groups, each of which is packaged with a separate Huffman table. The first two groups are packed in pairs as follows: in the flow written code from the table corresponding to the pair, after which the sign bits are written each sample. Numbers greater than the maximum for the table are coded as the maximum possible count, plus the number of bits determined by the table, written after the code that contains the number added to the value. The last block of coefficients is encoded fours with the possible values coefficients -1, 0, 1. The length of blocks contained in the overhead frame that allows us to calculate the number of zero values of samples at the end of the frame. Changes in the coefficients of the last block, ie, replacement of -1 and 0, 0 and 1, will change the size of the compressed coefficient (because of the appearance or disappearance sign bit), which in turn can lead to structural damage of MP3 files - information will be more or less than the allocated space for it in the frame. From the coefficients of the first two blocks of modifications to be no more than one factor in the pair, and the need to retrofit a pair of code size coincided with the size of the source code. Steganography in CAD/CAM/PLM. Contents. 43 Typically, this condition is satisfied for codes large numbers. Percentage of available coefficients decreases rapidly with decreasing bit rate, as more coefficients are coded zero or close to zero values. These limitations lead to a screening of about 85% of the appropriate coefficients. Maximum permissible deviation of the fractional part of the coefficient of 0.5 is defined based on size of the message, which should hide in the container so that the number of available coefficients were close to the maximum message size. In order to achieve acceptable levels of performance of the method, MP3 stream is divided on the staff of the same size. The number of frames in the groups selected in order that the number of modifiable factors they had about the same. In each group, hiding SLAE is solved independently. Thus, the despite the fact that while the Gauss method in each group is proportional to the cube the number of equations, the total time increases linearly with the number of factors used. However, each group must contain a certain the number of bits of the service, which recorded the length of the message in this group. Hence the smaller the group, (and faster method), the more bits spent on the service information. This method of protection from high throughput detection provides the ability to order a half per cent of the container. It is well suited for situations where the expected counter-informed enemy. Theme 5. Steganalysis: the terminology, the basic theoretical aspects. Questions for self-examination and discussion in seminars. 1) adopted terminology. 2) Theoretical propositions steganalysis based on accepted terminology. 3) Example histogram steganalysis. Literature to explore themes. 1. Mitchell T. Machine Learning. "— McGraw-Hill, 1997. 2. Farid H., Lyu S. Detecting Hidden Messages Using Higher-Order Statistics and Support Vector Machines // Information Hiding. "— 2002. "— pp. 340–354. 3. Farid H., Lyu S. Steganalysis using color wavelet statistics and one-class support vector machines // Security, Steganography, and Watermarking of Multimedia Contents. "— 2004. — pp. 35–45. Steganography in CAD/CAM/PLM. Contents. 44 4. Cristianini N., Shawe-Taylor J. An introduction to support vector machines and other kernel-based learning methods. "— Cambridge University Press, 2000. "— March. 5. Schoelkopf B., Sung K., Burges C. et al. Comparing Support Vector Machines with Gaussian Kernels to Radial Basis Function Classifiers: Tech. rep.: Massachusetts Institute of Technology, 1996. 6. Bedi C., Goyal H. Qualitative and Quantitative Evaluation of Image Denoising Techniques// International Journal of Computer Applications. — 2010. — October. — Vol. 8, no.14. — pp.31–34. 7. Pevný T., Fridrich J. Merging Markov and DCT Features for Multi-Class JPEG Steganalysis // Proceedings SPIE, Electronic Imaging, Security, Steganography, and Watermarking of Multimedia Contents IX. "— Vol. 6505. "— 2007. 8. Pevný T., Bas P., Fridrich J. Steganalysis by subtractive pixel adjacency matrix // Trans. Info. For. Sec. "— 2010. "— June. "— Vol. 5. "— pp. 215–224. 5.The market overview of steganography software Blindside is an application of steganography that allows one to conceal a file, or set of files within a standard computer image. The new image looks identical to the human eye, but can contain up to 50k or so of secret data. The hidden files can also be password encrypted, to prevent unauthorised access to their data. DataMark Technologies currently market four digital steganography products StegComm for confidential multimedia communication, StegMark for digital watermarking of digital storage media, StegSafe for digital storage and linkage and StegSign for e-commerce transactions. Each software product is packaged into a Standard version and a Professional version. While the Standard versions cater to the general needs of our customers, additional security and accessibility features are found in Professional versions. Digital Picture Envelope is a program you can make your secret data imperceptible to any human eyes. So, you can store/send it very safely in/through your computer. Actually, it can embed your secret data in a vessel image (we call it a "dummy" image, or a "picture envelope") without changing the visual quality of the dummy image.It does not change even the file size. If you want to see the secret data, you can easily restore it from the secret- embedded dummy image. Steganography in CAD/CAM/PLM. Contents. 45 The program gifshuffle is used to conceal messages in GIF images by shuffling the colourmap, which leaves the image visibly unchanged. gifshuffle works with all GIF images, including those with transparency and animation, and in addition provides compression and encryption of the concealed message. Hide4PGP is a freeware program distributed as source code in ANSI C and precompiled executables for DOS (any version but 1.x - is there one outside the museum?), OS/2 (Warp and up), and the Win32 console (9x and NT). It's purpose is to hide any data in a way that the viewer or listener does not recognize any difference. InThePicture Encrypt Files & Messages into redundant space in Windows Bitmap (BMP) image files. Invisible Secrets hides your private data into innocent looking files, like pictures, or web pages. It also features: strong encryption algorithms; a locker that allows you to password protect certain applications; a password management solution and a realrandom password generator; a shredder that helps you destroy beyond recovery files, folders and internet traces; the ability to create self-decrypting packages; secured password transfer. JPHIDE and JPSEEK are programs which allow you to hide a file in a jpeg visual image. There are lots of versions of similar programs available on the internet but JPHIDE and JPSEEK are rather special. The design objective was not simply to hide a file but rather to do this in such a way that it is impossible to prove that the host file contains a hidden file. Given a typical visual image, a low insertion rate (under 5%) and the absence of the original file, it is not possible to conclude with any worthwhile certainty that the host file contains inserted data. As the insertion percentage increases the statistical nature of the jpeg coefficients differs from "normal" to the extent that it raises suspicion. Above 15% the effects begin to become visible to the naked eye. Of course some images are much better than others when used a host file - plenty of fine detail is good. A cloudless blue sky over a snow covered ski paradise is bad. A waterfall in a forest is probably ideal. P3Stego will hide information in MP3 files during the compression process. The data is first compressed, encrypted and then hidden in the MP3 bit stream. Although MP3Stego has been written with steganographic applications in mind it might be used as a copyright marking system for MP3 files (weak but still much better than the MPEG copyright flag defined by the standard). Any opponent can uncompress the bit stream and recompress it; this will delete the hidden information -- actually this is the only attack we know yet -- but at the expense of severe quality loss. Steganography in CAD/CAM/PLM. Contents. 46 NICETEXT is a package that converts any file into pseudo-natural-language text OutGuess is a universal steganographic tool that allows the insertion of hidden information into the redundant bits of data sources. The nature of the data source is irrelevant to the core of OutGuess. The program relies on data specific handlers that will extract redundant bits and write them back after modification. In this version the PNM and JPEG image formats are supported. In the next paragraphs, images will be used as concrete example of data objects, though OutGuess can use any kind of data, as long as a handler is provided. Scramdisk is a program that allows the creation and use of virtual encrypted drives. Basically, you create a container file on an existing hard drive which is created with a specific password. This container can then be mounted by the Scramdisk software which creates a new drive letter to represent the drive. The virtual drive can then only be accessed with the correct passphrase. Without the correct passphrase the files on the virtual drive are totally inaccessible. The program snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected. SteganoGifPaletteOrder Hiding data into the palette of a GIF file. Steganos hides secret information in sound, image, and text files. This sensitive data is being encrypted beforehand. That way files can be sent over the Internet without being discovered by a third party. Stego Hide and recover encrypted data in your GIF files StegParty is a system for hiding information inside of plain-text files. Unlike similar tools currently available it does not use random gibberish to encode data -- it relies on small alterations to the message, like changes to spelling and punctuation. Because of this you can use any plain-text file as your carrier , and it will be more-or-less understandable after the secret message is embedded. wbStego is a tool that hides any type of file in bitmap images, text files, HTML files or Adobe PDF files. The file in which you hide the data is not optically changed. It can be used to exchange sensitive data securely or to add hidden copyright information to the file. TextHide Software to hide any data in unsuspicious text in order to store or communicate secrets (textual steganography). Steganography in CAD/CAM/PLM. Contents. 47 6. Statement of the problem of detection of hidden messages. The vast majority of methods for detection of hidden data is based on an analysis of the characteristics of the probability distribution of the container elements. This allows you to predict the enemy's actions in solving the problem of detection of hidden data. The following is a mathematical model of the basic most probable enemy action, based on the provisions of detection theory. Adoption of a solution enemy hidden in the target data carrier is not performed on a single value of a quantity characterizing the contents of the media, and throughout the carrier, i.e. based on a sample consisting of N values of the implementation that makes better use of a priori information and to receive the greater good than the more significant sample size N. Thus, the task of the enemy on the development of detection methods can be interpreted as an optimization problem: P обн - probability of detection, Pлт – false alarm where a collection of empty containers, the function of hiding data - detection, F(I) = 1 if the decision is "YES" F(I) = 0 if the decision is "NO" We write the function of detection by assessing: - The threshold score. Since the containers are used as sources of excess real signal, the contents of the container can be divided into signal and "noise", where the noise is understood sampling noise, quantum noise, etc. the distortions introduced in the "ideal" signal. In the case of non-volatile media as containers for the noise we mean the unused blocks of the file system. Imagine the container as Steganography in CAD/CAM/PLM. Contents. 48 I = L +G Where - the container without the noise, - noise is present in the container. Then Where - the weight of the corresponding estimates. It is clear that with increasing resources enemy, particularly the number of empty containers available, estimation is improved: Besides the introduction of hidden data in the signal-to-container could result in «visible» outside observer distortions. Accordingly, based on the results of the analysis and of a hidden data channel practicable algorithms for data hiding place hidden in the noise of the data container: Thus, the optimal method for detection of hidden data is constructed based on the following algorithm of detection: Select the noise parameters from the provided container for analysis using the selected method of isolating the noise N, The decision is "YES" or "NO" depending on the evaluation of hidden data in the selected noise Consequently, the task of developing a detection method can be represented as a function of searching for an optimal evaluation and optimal allocation function Noise The task of constructing a noise estimation is the task of classification. According to its interpretation in the present case is required to construct an algorithm which assigns to the noise obtained from the presented analysis for the container to one of two classes - the class of noise containing hidden data or class of noises that do not contain hidden data. The object in this case, Steganography in CAD/CAM/PLM. Contents. 49 noise can be represented as a vector consisting of separate noise characteristics. The algorithm uses the sample selection, which consists of a set of empty and full containers. Application 1 PROGRAM for the discipline «Steganography in CAD/CAM/PLM». 1. Goals and objectives of the discipline: Familiarize students with various methods of steganography, used for hiding the project documentation in CAD/CAM/PLM during the data exchange within secure channels of communication and on peripheral storage devices. Main group of methods to be studied consists of the following group methods: • Classical steganography has been widely used, including in recent historical times and the present day. • Computer steganography - the branch of the classical steganography based on the characteristics of computing platform.( hiding data in unused fields of file formats, the substitution of characters in file names etc). • Digital steganography - the branch of the computer steganography, based on the data hiding within digital objects of the analog origin, i.e. multimedia objects (image, video stream, etc) Hiding data on various storage devices and in different channels of communication. 2. The study of this discipline is based on the following knowledge: - Mathematical analysis. (Fourier series and integrals, discrete spectral transforms, the theory of functions of complex variable theory of differential equations,special functions, - Linear Algebra. (The algebra of logic, algebra, fuzzy logic) - Probability theory (the theory of stochastic processes) 1. - Requirements for the results of the development of disciplines: 3. As a result, the discipline the student must: to know: • Elements of the theoretical foundations of classical steganography. • Elements of the theoretical foundations of computer steganography - hiding data in unused fields of file formats, the substitution of characters in file names, text steganography, the transmission of data within secure channels, etc. • Elements of the theoretical foundations of digital steganography - hiding data in digital objects with the analog nature, that is, the multimedia objects (images, videos, sounds). Steganography in CAD/CAM/PLM. Contents. 50 To be able to: • study new methods of embedding of the stego message into different containers on their own. • Assess the reliability of different implementations of steganography techniques possess. • Skills of the assessment of the subsystem’s ability to protect a data from an unauthorized access in various communication channels. • Skills of development of the software and the hardware complexes to protect the external storage devices from the unauthorized access and copying. 4. The volume of disciplines and types of training activities Type of school work Class work (total) Hours (Total) 52 Including: lectures 34 Workshops (as part of the complex) 18 Home work (total) Summary*) Type of certification (test, exam) 92 The total labor output ratio hours 92 test Note: Seminars are held in the conjunction with lectures. Lectures and seminars form complexes. *) The student must defend his summary during the colloquium. 5. Contents of discipline. The content of the complexes of discipline The name of the complex The theoretical foundations of computer steganography. Steg’s preparation Theoretical Foundations of digital steganography Сontent of the complex The methods of the data and signals concealing at the physical level. Special types of signal modulation. Special encoders and decoders. Scrambling in the channels of communication. Methods of optical, acoustic and radio holography. Formulation and solution of inverse problems in optics, acoustics, and radio. Theoretical Foundations of digital steganography methods based on the data hiding within digital objects of the analog nature. Steganography in CAD/CAM/PLM. Contents. Volume 10 20 12 51 Theoretical Foundations Mathematical methods for detection and of Steganalysis identification of stego into different containers 6. The content of the workshop (held in parallel with the lectures) 10 The discipline complex Software implementation of the spatial signal processing techniques. Software implementation of methods for solving the inverse problem. Software implementation of simulation methods of the messages embedding into different containers in computer steganography Software implementation of simulation methods of the messages embedding into different containers in digital steganography Software implementation of methods for steganalysis 7. Dining assignments for seminars means MathCAD 1. Workshop number 1. Determination of functions and definition of derivatives I). Find function values at x = 1. II). Find the derivatives of the function. 1. f ( x) 2 f ( x) 3 5 1 2 x 4 7; 4 3 5 2x x 4 5 1 7 x 6 2; 7 3 5 6x x 3. f ( x) 3x 2 1 3 1; 7 3 2 7x x III) Steganography methods. 1. Method LSB. 2. Hiding data in an image by Cutters. 3. Research on the influence of noise on the concealment method Cutters. 4. Steganography images using Patchwork. 5. Steganography sound method Patchwork. 6. Research on the influence of noise on the concealment method LSB. Educational-methodical and informational support disciplines: a) The basic literature http://www.cl.cam.ac.uk/~fapp2/steganography/ http://www.demcom.com/english/steganos/ Steganography in CAD/CAM/PLM. Contents. 52 http://eprint.iacr.org/2005/305 http://www.topreferats.ru/comp/6636.html http://www.signumtech.com b)Further Reading 1.Pereira S., Joseph J., Deguillaume F. Template Based recovery of Fourier-Based Watermarks Using log-polar and Log-log Maps. IEEE Int. Conf on Multimedia Computing and Systems, 1999. P. 5. 1. Lin Ch-Y., Chang Sh.-F. Distortion Modeling and Invariant Extraction for Digital Image Print-and Scan Process. International Symposium on Multimedia Information Processing, 1999. P. 10. 2. Lin Ch-Y., Chang Sh.-F. Public Watermarking Surviving General Scaling and Cropping: An Application for Print-and-Scan Process. Multimedia and Security Workshop at ACM Multimedia, 1999. 3. Pereira S., Thierry P. Fine Robust Template Matching for Affine Resistant Image Watermarks. IEEE Trans. on Image Processing, 1999. - P. 12. 4. Kutter M. Watermarking Resisting to Translation, Rotation, and Scaling. Signal Processing Laboratory, 1998. P. 10. 5. Kutter M. Digital Signature of Color Images using Amplitude Modulation. Signal Processing Laboratory, 1997. P. 9. 6. Herrigel A., Pereira S., Petersen H. Secure Copyright Protection Techniques for Digital Images. International Workshop on Information Hiding, 1998. P. 22. 7. Anderson R., Needham R., Shamir A. The Steganographic File System// Proceedings of the Second International Workshop on Information Hiding. — «Springer-Verlag, 1998.» — Pp. 73–82. 8. McDonald A., Kuhn M. StegFS: A Steganographic File System for Linux // In Information Hiding. "— 1999. "— Pp. 462–477. 9. Varun S., Shibin K. Magikfs – The Steganographic Filesystem On Linux // http://magikfs.sourceforge.net. 10. Chetan G. Dissecting NTFS Hidden Streams// http://www.forensicfocus.com/dissecting-ntfs-hidden-streams. Steganography in CAD/CAM/PLM. Contents. 53 11. Guillaume T. A few thoughts about steganography// http://www.guillermito2.net/stegano/ideas.html. 12. FIPS publication 197 Advanced Encryption Standard. — Federal Information Processing Standards Publ., 2001. 13. Fruhwirth C. New Methods in Hard Disk Encryption// http://clemens.endorphin.org/nmihde/nmihde-A4-os.pdf. Appendix Check lists. 1. A comparison of cryptographic capabilities and methods of steganography to hide data transmission channels transmit messages. 2 . What are the differences and similarities of methods of computer and digital steganography. 3 . Analyze vulnerabilities steganographic system based on its structural scheme. 4 . Analyse the "possibilities" of Eve in an attempt to identify the correspondence of Alice and Bob . 5 . Identify capacity constraints successfully hide data in images. 6. Contrast can be successfully hide data files containing images and audio files in digital steganography algorithms discussed . 7. Are there fundamental ( teoretichiskie ) constraints on development , the development of new methods of digital steganography. 8. Are there fundamental limitations in the development and the development of new methods of computer steganography. 9. Assess vulnerabilities in applications directories FAK stegosystem Steg FS. 10 . Determine fundamentally original method of digital steganography from those described in the manual . The comparative analysis of these methods by " originality ." 11. Determine the fundamental differences in the formulation of cryptanalysis and steganalysis . Steganography in CAD/CAM/PLM. Contents.