pearl 010 cheatsheet
advertisement
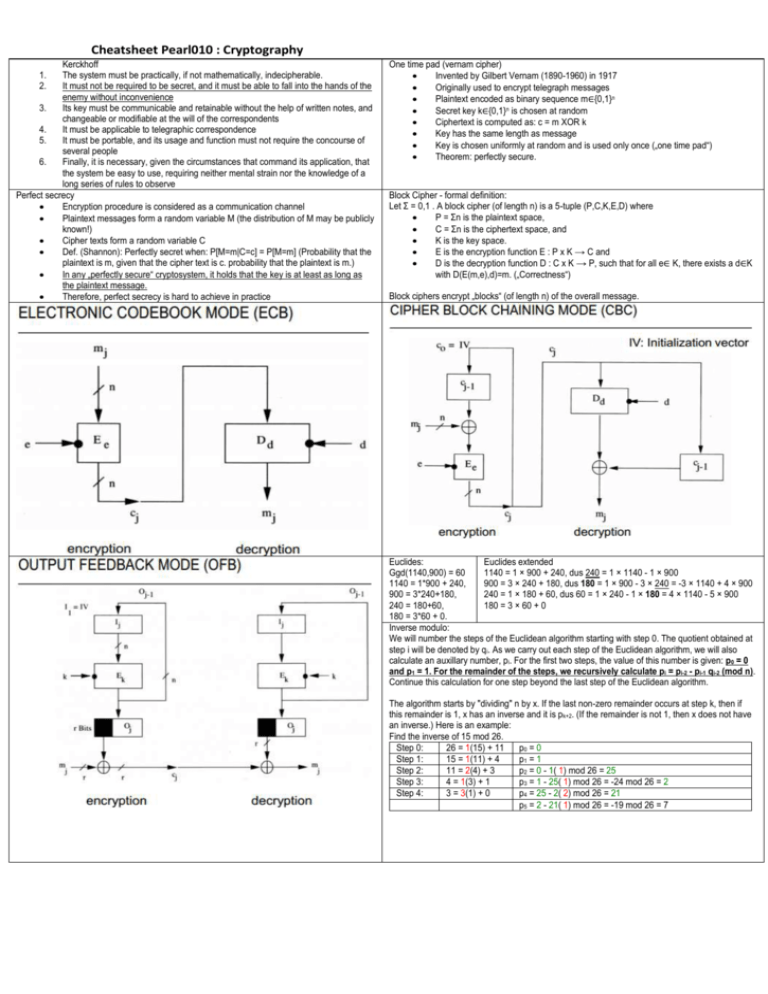
Cheatsheet Pearl010 : Cryptography
Kerckhoff
1.
The system must be practically, if not mathematically, indecipherable.
2.
It must not be required to be secret, and it must be able to fall into the hands of the
enemy without inconvenience
3.
Its key must be communicable and retainable without the help of written notes, and
changeable or modifiable at the will of the correspondents
4.
It must be applicable to telegraphic correspondence
5.
It must be portable, and its usage and function must not require the concourse of
several people
6.
Finally, it is necessary, given the circumstances that command its application, that
the system be easy to use, requiring neither mental strain nor the knowledge of a
long series of rules to observe
Perfect secrecy
Encryption procedure is considered as a communication channel
Plaintext messages form a random variable M (the distribution of M may be publicly
known!)
Cipher texts form a random variable C
Def. (Shannon): Perfectly secret when: P[M=m|C=c] = P[M=m] (Probability that the
plaintext is m, given that the cipher text is c. probability that the plaintext is m.)
In any „perfectly secure“ cryptosystem, it holds that the key is at least as long as
the plaintext message.
Therefore, perfect secrecy is hard to achieve in practice
One time pad (vernam cipher)
Invented by Gilbert Vernam (1890-1960) in 1917
Originally used to encrypt telegraph messages
Plaintext encoded as binary sequence m∈{0,1}n
Secret key k∈{0,1}n is chosen at random
Ciphertext is computed as: c = m XOR k
Key has the same length as message
Key is chosen uniformly at random and is used only once („one time pad“)
Theorem: perfectly secure.
Block Cipher - formal definition:
Let Σ = 0,1 . A block cipher (of length n) is a 5-tuple (P,C,K,E,D) where
P = Σn is the plaintext space,
C = Σn is the ciphertext space, and
K is the key space.
E is the encryption function E : P x K → C and
D is the decryption function D : C x K → P, such that for all e∈ K, there exists a d∈K
with D(E(m,e),d)=m. („Correctness“)
Block ciphers encrypt „blocks“ (of length n) of the overall message.
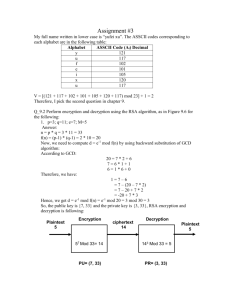
Euclides:
Euclides extended
Ggd(1140,900) = 60
1140 = 1 × 900 + 240, dus 240 = 1 × 1140 - 1 × 900
1140 = 1*900 + 240,
900 = 3 × 240 + 180, dus 180 = 1 × 900 - 3 × 240 = -3 × 1140 + 4 × 900
900 = 3*240+180,
240 = 1 × 180 + 60, dus 60 = 1 × 240 - 1 × 180 = 4 × 1140 - 5 × 900
240 = 180+60,
180 = 3 × 60 + 0
180 = 3*60 + 0.
Inverse modulo:
We will number the steps of the Euclidean algorithm starting with step 0. The quotient obtained at
step i will be denoted by qi. As we carry out each step of the Euclidean algorithm, we will also
calculate an auxillary number, pi. For the first two steps, the value of this number is given: p0 = 0
and p1 = 1. For the remainder of the steps, we recursively calculate pi = pi-2 - pi-1 qi-2 (mod n).
Continue this calculation for one step beyond the last step of the Euclidean algorithm.
The algorithm starts by "dividing" n by x. If the last non-zero remainder occurs at step k, then if
this remainder is 1, x has an inverse and it is pk+2. (If the remainder is not 1, then x does not have
an inverse.) Here is an example:
Find the inverse of 15 mod 26.
Step 0:
26 = 1(15) + 11 p0 = 0
Step 1:
15 = 1(11) + 4
p1 = 1
Step 2:
11 = 2(4) + 3
p2 = 0 - 1( 1) mod 26 = 25
Step 3:
4 = 1(3) + 1
p3 = 1 - 25( 1) mod 26 = -24 mod 26 = 2
Step 4:
3 = 3(1) + 0
p4 = 25 - 2( 2) mod 26 = 21
p5 = 2 - 21( 1) mod 26 = -19 mod 26 = 7
Cheatsheet Pearl010 : Cryptography
Modular arithmetic:
Two integers a,b are said to be congruent modulo n, if n | (a-b). In this
case, we write a ≡ b (mod n).
a ≡ b (mod n) iff there exists an integer k with a-b = kn.
24 ≡ 9 (mod 5)
11 ≡ 17 (mod 7)
Euler:
Definition: We denote the number of elements in ℤn* by ᵠ(n) and call it
Euler’s totient function.
For all primes p: ᵠ(p) = p-1
For N=pq with distinct primes p,q: ᵠ(N) = (p-1)(q-1)
Key Generation:
Choose two large and distinct primes p,q and set N = pq
Note that ϕ(N)=(p-1)(q-1)
Plaintext space and ciphertext space: ℤN*
Choose an exponent e with gcd(e,ϕ(N)) = 1 (coprime: exponent e must be a number
that doesn’t share any prime factors with ϕ(N).)
Compute the unique exponent d with ed ≡ 1 (mod ϕ(N))
(d = ((ϕ(N) * k) + 1) / e. with k as an integer. D must be unique!)
Public key: (N,e) Secret key: d
Encryption with public key (N,e):
c = E(m,e) = me mod N
Decryption with secret key d:
m = D(c,d) = cd mod N