Question 1: Fill blank or choose the correct answer
advertisement

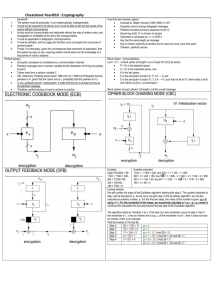
ITIS 3200 Knowledge Points Chap 1: (1) What properties do “C, I, A” stand for in computer security? (2) The concepts of a security threat and an attack. What is the major difference between them? (3) The concepts of a security policy and a security mechanism. What is the major difference between them? (4) Under what conditions do we call a security mechanism secure, precise, and broad? You must be able to use a figure to illustrate their relationship. If we describe a scenario, you should be able to figure out what category the mechanism falls into. Chap 2: (1) When we provide a description of a group of subjects, objects and the operations that each subject can perform on an object, you must be able to draw the access control matrix. (2) In real systems we do not directly use access control matrix but some alternatives. Please explain the reasons. Chap 4: (1) Understand Figure 4-1. If we present a similar figure, you must be able to tell whether or not the system is secure. (2) Understand the concepts of discretionary access control, mandatory access control, and originator controlled access control. If we describe a scenario, you should be able to identify which kind of access control is adopted. You should be able to describe an example to explain every kind of access control. Chap 5: (1) Why do we call Bell-LaPadula “no read up, no write down”? (2) Understand the simple security property and Star property. Why simple security policy alone is not enough to enforce information confidentiality? Please describe an example to show the violation. (3) Understand the “categories” that we introduce to expand each security classification. Understand the relationships “⊆” and “⊇” between two sets of categories, and “∈” between an element and a set. You must understand these concepts. See page 63 to 64 in the book for this part. Understand Figure 5-2. (4) Understand the relationship “dominate” between two security levels. This will allow you to determine whether a person can read and/or write a file based on the Bell-LaPadula model. (5) If we provide the security clearance of a person, and the security classification of a file, you must be able to determine what operation (read, write, both, or neither) the person can perform on the file based on the Bell-LaPadula model. (6) In real life, how can a person with high security clearance communicate to a person with low security clearance? We allow high clearance guy to temporarily degrade her/his level. (7) In the B2 Unix system, why do we put the system calls in the lowest confidentiality level? 1 Chap 6: (1) In Biba model, we enforce “no read down, no write up” for data integrity. If we provide the integrity level of a person and a file, you must be able to determine whether or not the read or write operation can be performed. (2) Understand the rules in the Clark-Wilson model. In Clark-Wilson integrity model, why do we need a rule to transform an UDI to a CDI? What is the append-only CDI described in CR4 for reconstruction of operations? (3) What is the advantage of the concept “transaction” that is introduced into the Clark-Wilson model? Chap 7: (1) Understand the Chinese wall model. Understand the Simple security condition and the Star property. Why do we need the Star property to enforce the Chinese wall model? If we provide a COI and CD data set, you must be able to determine whether or not the assignment of access rights to subjects will violate the model. You should also be able to remove corresponding access rights of the users to the datasets to remove the violations. (2) You must be able to draw the Role Hierarchy if we provide the description of the roles and their relationship. You must be able to properly introduce new roles when we describe the expected properties. Make sure that you do not draw those extra links between the roles. (3) Understand the concept of “originator controlled access”. (4) You must understand the principle of “separation of duty” and can use it to explain some regulations. Chap 8: (1) Understand the meaning of transposition ciphers and substitution ciphers. You should be able to give an example of each kind of ciphers. If we describe a system, you should be able to identify whether it is a transposition cipher or a substitution cipher. (2) What are the “cipher-text only”, “known plaintext” and “chosen plaintext” attacks? (3) What is a “one time pad”? (4) You should be able to conduct the exclusive-or calculation. (5) In DES, which component contributes the most to the safety? How large is the block size? How long is the key? (6) Different modes of DES. Specifically, you should understand the structure of ECB mode and CBC mode. What security problem may be caused by the ECB mode? In the CBC mode, if we provide one of the encryption/decryption chain structures, you should be able to draw the other one. You should be able to identify how the errors in transmission will impact the decryption results. For example, if the value of one bit in the cipher text is changed, how will the final decryption result be impacted? (7) You should be able to conduct modular calculation using the equations (a * b) mod p = ((a mod p) * (b mod p)) mod p and (a + b) mod p = ((a mod p) + (b mod p)) mod p You should be able to calculate the Totient function φ(n) of a number. (8) Why do we say a secure asymmetric encryption algorithm must be robust against chosen plaintext attack? 2 (9) You should understand the encryption/decryption procedures of RSA and understand why for some special numbers (such as 0 or 1), the cipher text will be the same as plaintext? Understand why in practice, we should use a very long block instead of a single-character block in RSA (See the example on page 116)? (10) Understand the expected features of a cryptographic checksum function. If we provide a description of a function, you should be able to identify whether or not it satisfies the requirements of a good hash function. You should be able to design a generic algorithm to identify or construct examples that violate the expected properties of a good hash function. Chap 9: (1) Understand the notions to represent a security protocol. You should understand the contents in the messages of a protocol among multiple parties. (2) Understand the concepts of session keys and interchange keys. What are the advantages of this distinction? (section 9.1) (3) Understand “forward search attack”. If we describe a scenario, you must be able to figure out how a malicious node can conduct a forward search attack. At the same time, you should be able to correctly calculate the total number of possible messages that the attacker needs to search. (Examples are given in Section 9.1 and our class contents.) (4) Understand “man-in-the-middle attack”. If we describe a scenario, you must be able to figure out how a malicious node can conduct a man-in-the-middle attack. Be very careful since man-in-the-middle attack is more than sending a fake public key. (Examples are given in pages 129—130.) (5) Understand the two methods to guarantee the freshness of the message: timestamp and challenge-response. Understand the advantages and disadvantages of each method. (6) What are the essential parts of a certificate? Why does a CA need to sign the identity and its public key in a single message? Understand two ways to form certificate chains: certificate hierarchy (X.509) and certificate signature chains (PGP). You do not need to remember the details of the components of X.509 certificates or PGP certificates. (7) Understand the certificate revocation mechanisms. What is a CRL and what is Online Certificate Status Protocol (OCSP)? How does the expiration date in a certificate help reduce the size of the “Certificate Revocation List”? (8) Understand the concept of a digital signature. Why do we say that a classical key encrypted message cannot be used as a digital signature? (Section 9.5) (9) When a message needs to be both enciphered and signed, why should we always sign first? Chapter 11: (1) Why is it not safe to store the user password in clear text or in an encrypted format on the machine? (2) If we describe a scenario, you should be able to figure out: (a) what is the total number of possible passwords? (b) if we also provide the speed that a malicious node can test passwords, you must be able to figure out for how long the attacker can try a certain percentage of the passwords? Or how long 3 the password has to be if we want the passwords to be safe for at least a certain amount of time? (3) Understand the concept of password aging. (4) What is salting in password protection? How does the salting help to protect the passwords in a computer system under dictionary attacks? (5) What mechanisms have people adopted to mitigate on-line password trial-anderror attacks? Chapter 12: (1) Understand the design principles of security mechanisms that we describe in class. If we provide the description of the principles and their names, you should be able to link them together. Chapter 13: (1) Why is it essential for us to maintain the correctness of the information in a DNS server? (2) Understand two kinds of anonymous email services: the Cypherpunk type and the anon.penet.fi type. What are the security problems of the approaches? (3) In Cyperpunk mechanism, why do we need to pad the messages? 4