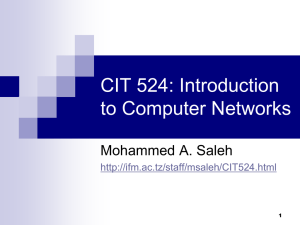
rollover cable
advertisement

DCN286 INTRODUCTION TO DATA COMMUNICATION TECHNOLOGY Network Physical Layer Connection Purpose of Physical Layer The role of the OSI physical layer is to encode the binary digits that represent data link layer frames into signals and to transmit and receive these signals across the physical media---- cooper wires, optical fiber, and wireless that connect network devices. Network Access Layer The network access layer is concerned with all of the issues that an IP packet requires to actually make a physical link to the network media. It includes the LAN and WAN technology details, and all the details contained in the OSI physical and data link layers. Popular Copper Media Standards TIA (Telecommunications Industry Association) and EIA (Electronic Industries Alliance) work together to publish commercial building telecommunications cabling standards TIA/EIA-568-B which defines how to use the pins on the connectors on the ends of the cables. IEEE (Institute of Electrical and Electronic Engineers) publishes LAN standards such as IEEE802.3 which will define cable requirement. Coaxial cable Gradually outdated from LAN Can run for longer distances than either STP or UTP Less expensive than fiber-optic cable though it is expensive than STP or UTP Still popular for TV and home internet service STP (Shielded Twisted Pair) cable Shielding provides better electrical signals by reducing noise and attenuation. Shielding makes the cable more expensive, heavier and hard to bend. UTP (Unshielded Twisted Pair) Flexible and easy install Offer the same data speeds Inexpensive RJ45 connector (RJ11 is for phone cable). UTP Implementation UTP Implementation Straight-through Cable Switch to Router Switch to PC or Server Hub to PC or Server Cross-over Cable Switch to Switch; Switch to Hub; Hub to Hub Router to Router; PC to PC; Router to PC Roll-over Cable (Configuration Purposes) PC to Router; PC to Switch UTP Implementation Straight-Through cable A cable that maintains the pin connection all the way through the cable. Cat 5 and Cat5e: Only wires 1, 2, 3, and 6 are used Gigabit Ethernet uses all the wires To connect devices such as PC or routers to other devices as hub or switches. UTP Implementation Cross-over cable A cable that crosses the critical pair to properly align, transmit, and receive signals on the device with line connections Pin 1 at one end and Pin 3 at the other end Pin 2 at one end and Pin 6 at the other end Used to connect similar devices: Switch to switch Hub to hub TIA/EIA568-A and B pin outs Pin # 1 2 3 4 5 6 7 8 Function TD+ TDRD+ Unused Unused RDUnused Unused 568A wire color White/Green Green White/Orange Blue White/Blue Orange White/Brown Brown 568 B wire color White/Orange Orange White/Green Blue White/Blue Green White/Brown Brown Straight through cable Can be used to connect PC and other network equipments to LAN hub/switch Wire 1 and 2 are used to transmit data Wire 3 and 6 are used to receive data Cross-over cable It is used to connect two same equipments such as PC-to-PC. Both ends need to send data on pin 1 and 2; receive data on pin 3 and 6. In 568B, one end has white/orange and orange on pin 1 and 2; another has white/orange and orange on pin 3 and 6. In 568B, one end has white/green and green on pin 3 and 6; another end has them on pin 1 and 2. Rollover cable Usually used as console cable. Change the sequence on another end. Rollover or Console Cable The cable used between a terminal and a console port is a rollover cable with RJ-45 connectors. Rollover cable (or Console cable) has a different pinout than the straight-through or crossover cable. The pinout for a rollover cable is: 1 to 8, 2 to 7, 3 to 6, 4 to 5, 5 to 4, 6 to 3, 7 to 2, and 8 to 1. Connector and Adapter The 8 Position 8 Contact (8P8C) (often called RJ45) connector Cross over adapter Optic media Fiber-optic cable has the strongest ability to resist EMI (electromagnetic interference), RFI (Radio Frequency Interference) Fiber’s bandwidth is much higher than any other media. Fiber is highly secure and it is easy to detect intrusion. Fiber uses light signal transmission and its attenuation is much less than electrical signals. Its length could be very long Optical fiber cable components Core: usually made by silicon dioxide (from sand) Cladding: coated on the core to reflect light and seal it inside Buffer: physical protect cladding and core Jacket: prevent damage from abrasion, solvents and other contaminants Optical Fiber Connector (Optional) LC/PC connector and SC/PC connectors have caps covering the ferrules Other connectors are ST, SC, MT, MT-RJ, MU, etc, etc Multimode fiber Fiber with large (greater than 10 μm) core diameter may allow light coming in with different angles. (It must be in limit of acceptance cone) Single mode fiber Fiber with a core diameter less than about ten times the wavelength of the propagating light and it can only allow light coming in from one direction. LAN Connectivity Devices Repeaters Hubs Switches Bridges Routers Repeaters A repeater can be used to increase the length of your network by eliminating the effect of attenuation on the signal. It connects two segments of the same network, overcoming the distance limitations of the transmission media. Some repeaters also serve as transmission media adapters, connecting two different types of media. Repeaters Repeaters can connect segments that have the same access method. (CSMA/CD, Token Passing, Polling, etc.) Disadvantages Repeaters do not filter data Its use is inappropriate when there is a heavy network traffic. Repeater 10base5 – 500meter cable length limit; 10base2 - 200meter cable length limit; 10BaseT - 100meter cable length limit; Repeater is to amplify signal and extend the cabling distance. Working in layer 1 (Physical) of TCP/IP model Repeaters Figure11-6 Hub Central connection of Ethernet LAN. Physically Star topology and could be logically RING, Bus and/or Star May have built-in repeater Working in layer 1 (Physical) of TCP/IP model Hubs A hub is used as a central point of connection among media segments. Cables from network devices plug in to the ports on the hub. Hubs are referred as Concentrators or multiport repeater Hubs receive signals from connected devices and transmit them to the other connected devices Hubs Regenerate and repeat signals Propagate signals through the network Can not filter network traffic Can not determine the best path Are used as network concentration points. Hubs Types of Hubs Passive Hubs Active Hubs Intelligent Hubs (Switches) Passive Hub It functions only as a connection point for the signals The signal pass through a passive hub without regeneration or amplification. Active Hub It regenerates or amplifies the signal before they are retransmitted. Drawback: The noise is also regenerated Switch Think switch as a hub with bridge functioning on each port (interface): 1. Switch will offer central connection to all hosts. 2. Switch will only forward frame according to destination MAC address on per-port base. 3. Will regenerate signals (repeater function) 4. Most switches are working in layer 2 (Data Link) of TCP/IP model. Switches LAN Switch broadcast traffic LAN switch Broadcasts to all ports on LAN sw itch. Single Switch Virtual LANs broadcast source Forwarding Frame based on Destination MAC Address The switch maintain table, called a MAC table, that maps destination MAC addresses with ports used to connect to each node. For each incoming frame, the destination MAC address in the frame header is compared to the list of addresses in the MAC table. If a match is found, the port number in the table that is paired with MAC address is used as exit port for the frame. The MAC table can be referred to by many different name. It also called Switch table or Bridge table. Switch Operation To accomplish Frame Forwarding, Ethernet LAN switches use five basic operations: Learning: The Mac table must be populated with MAC addresses and their corresponding ports. The learning process allows these mappings to be dynamically acquired during normal operation. Aging: The entries in the MAC table acquired by the learning process are time stamped. This time stamp is used as a means for removing old Continues Slide-37 entries in the MAC table. After it is made in the MAC table, a procedure begins count down, once it reaches count 0, the entry is aged out and remove from the table. Flooding: If a switch does not have a MAC address entry in its MAC table that matches the destination MAC address of received frame, the switch will flood the frame. Flooding involves sending a frame to all ports except the port on which the frame arrived. Switch Continues Selective Forwarding: Selective forwarding is the process of examining the destination MAC address of a frame and forwarding it out to the appropriate port. Filtering: In some cases, a frame is not forwarded. This process is called frame filtering e.g. a switch does not forward a frame to the same port on which it arrived. A switch will also drop a corrupt frame. If a frame fails a CRC check, the frame is dropped. Ethernet Bridge Intelligent device to forward frame according to destination Media Access Control (MAC) address Forwarding: If the destination MAC address has a port different to the originate port, the frame will be sent. Filtering: If the destination MAC address is reachable with the same interface when it arrived, the frame will be discarded. Working in layer 2 (Data Link) of TCP/IP model Layer 2 Bridging Bridges Segmentation 80% of LAN traffic stays on local LAN 20% of LAN traffic travels between LANs LAN A bridge LAN B Router Redirect packets according to destination logical address (IP address). Can build routing path between different network segments (subnets) Can act as firewall Can work as VPN (server) connection Working in layer 3 (Network) of TCP/IP model Routers Figure 11-7 Wireless tech introduction Infrared Bluetooth Microwave Radio Wi-Fi In general, wireless network is secondary because of two concerns: speed and security. But, it does offer mobility and convenience. Wireless Networking Media Radio frequency (RF) Laser Infrared (IR) Satellite/Microwaves Wireless transmission techniques to carry wireless signals Wireless signals are electromagnetic waves that travel through the air. Wireless Networking Media Infrared Line of sight Short distances No obstacles between transmitter and receiver Radiofrequency Allows devices to be in different room or even buildings Limited radio Can be single or multiple (Spread spectrum) frequencies Single Frequency Is subject to outside interference and geographic obstructions Insecure (Easily monitored by others) Spread Spectrum Multiple frequencies More secure Security in the Wireless Environment The first level of security in a wireless LAN consists of protecting the radio frequency waveform itself. Security in the Wireless Environment Wireless Access Points Wireless Bridges Encryption WEP – Wireless Equivalence Privacy EAP – Extensible Authentication Protocol (IEEE 802.1X) Wireless LAN Topology Wireless Bridges Wireless Security If you think someone might eavesdrop on your LAN radio links….. Encryption is the key Wireless Security Approaches WEP – Wired Equivalency Privacy IEEE 802.1X or Extensible Authentication Protocol (EAP) Wireless Equivalent Privacy WEP It is a security mechanism defined with the IEEE 802.11 standard. Designed to protect over the over-the-air transmissions between wireless LAN access points and NICs. IEEE 802.11b requires 40-bit encryption keys Cisco supports the optional 128-bit standard. WEP Goals Deny access to the network by unauthorized users who do not possess the appropriate WEP key. Prevent the decoding of captured WLAN traffic hat is WEP-encrypted without the possession of the WEP key. Should be supplemented with additional higher-level security mechanisms such as VPNs or Firewalls. 802.1X/EAP Extensible Authentication Protocol It is an alternative WLAN security approach to WEP 802.1X/EAP focuses on providing: Centralized authentication Dynamic key distribution It is a standard for port-based network access control Cabling the WAN Wide Area Network (WAN) Services To connect one network to a remote network Provide different connection methods Different cabling standards from those of LANs