Capabilities - Key CyberSecurity, Inc.

2Q 2014 Presentation
Key Cybersecurity, Inc.
17959 Dumfries Shopping Center Suite B
Dumfries, VA 22026-2490
703.402.2542
Shawn Key
CEO, President skey@keycybersecurity.com
Privileged and Confidential
Accolades
Most Disruptive Solution – Security Category
Best of Breed – All Security Categories
Inaugural Cohort Member (Graduate)
Cyber Tipline
Provider
™
CyberMerlin
Provisional Patent No. 61/986,553
Enables agencies and organizations to identify unknown and known file activity typically undetected on the enterprise network and connected devices.
Provides capability to locate desired files algorithmically instead of by keyword, allowing for a paradigm shift in file location independent of file type or language.
“Understanding the file activity on your network is just a few clicks away…”
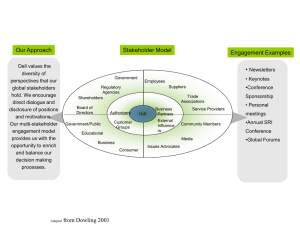
Value Proposition
Undetected child pornography files are being stored on the network.
Privacy Information is being stored in the clear
Corporate reputation is at stake
Embarrassing headlines
Remediation costs
Locate files proactively, reduce liability, handle the issue internally
Identify PI, mitigate concern, ensure compliance with standards/regulations
Intellectual Property is being sent to or accessed by competitors
Corporate espionage
Competitor advantage
Financial loss
Monitor file activity and “bad actors”, locate source of leak, remediate issue
“The Specialized Threat and Protection (STAP) market will reach $1.17 billion in annual revenue by 2017” - IDC
Legalities
"We are pretty sure we have child pornography on our network but if we find it, we have to do something about it and that becomes onerous and potentially costly."
Sarbanes Oxley Public Law 107-204:
A section of the Sarbanes-Oxley Act that says a person is guilty of a felony, punishable by up to
20 years in prison, if he [sic] “alters, destroys, mutilates, conceals, covers up, falsifies, or makes a false entry in any record, document, or tangible object with the intent to impede, obstruct, or influence the investigation or proper administration of any matter within the jurisdiction of any department or agency of the United States.
”
Ignorance is NOT Bliss
The American Bar Association Criminal Justice Section
Center for Continuing Legal Education http://www.strozfriedberg.com/files/Publication/2ff70060-e3c5-43f8-bf98-
024a2b4b3509/Presentation/PublicationAttachment/412a1aa4-562b-402d-800d-
0097b96248b6/DigitalContrabandFindingChildPornintheWorkplaceWhiteCollarCrimeProg ram.pdf
ABA/CCLE – Audio track
“The company must take steps to minimize its own liability risks from an employee’s illegal access to child porn, and those risks can loom large if the illicit images are mishandled.
”
Simply ignoring the problem is not an option, not only from a moral perspective, but also as a legal matter: “doing nothing: could provide a basis for “hostile work environment ” claims or may subject the company to civil suit by “any person aggrieved ” by the possession of the images. Significantly, sticking one’s head in the sand also could expose managers to child porn
“possession” charges or damage the companies reputation if unannounced searches and arrests of employees occur at the workplace.
”
Circulating the child porn images internally or to outside experts to elicit multiple views about how to handle the situation may implicate
“distribution” issues. Relying on inhouse IT staff to investigate the problem also poses potential problems, including the possibility that they might inadvertently taint or destroy evidence, “leak” facts about the internal investigation, or “check out” web sites visited by the offending employee, thereby caching more illegal child porn onto the company network.
”
How Big is the CP Problem?
November 21, 2013
If you've got a big company system, I can almost guarantee that you have child pornography on it…It's there somewhere.’’
Kenneth Citarella, Deputy Chief of Investigations, Westchester
County District Attorney's Office.
“Child pornography is hidden on virtually every large corporate network, according to security experts.
” - Internetnews.com
™
Detection Mode
Find unknown problematic and illicit files
Search Mode
Find all instances of a known file
Forensics Mode
Utilize file reports to augment forensic activities
Automatically Detects/Monitors/Alerts
Compiles Forensic Reports
Customization and “Webcrawling”
Capability
Proprietary “Certainty Hash Value”
Differentiator
Integrated Vision Technology (3Q 2014)
™
CyberMerlin Functionality
CyberMerlin Server
• Server stores file signatures, performs fast matching, provides communications to
CyberMerlin user agents, stores and displays results of scans and much more.
CyberMerlin Web Console
• Provides administrative access to a server, database management, user agent management and much more. Friendly browser user interface powered by
Google Web Toolkit.
CyberMerlin User Agent
• Downloadable agent performs multiple functions – it scans local filesystem and looks for illicit files, In secondary mode, it functions as a crawler to scan/load hashes from the web/cloud. Platform independent and works on Windows, Mac
OSX, Linux and other O/Ss.
Current Activities
Dell Solutions Center (DSC)
Create scalable, cloud based solution which runs ALL major platforms
Dell Appliance Group (NCS)
Create revenue via the distribution of a new capability appliance based solution
Dell Entrepreneur in Residence (EIR)
Applicant for the prestigious Dell Founders Club
Dell OEM Division
Exploring the marketing possibility of CyberMerlin as a desktop OEM solution and/or a network appliance for K-12 organizations (CIPA/FERPA compliance)
DC Innovates
Applicant for DC based grant funding in the Tech Corridor (up to $200k)
Beta Customer and Strategic Partner
Opportunities
CyberMerlin – National Exposure
Insert Pending Press Release
(June 14
th
EST)
Executive Management and Advisory Team
Shawn R. Key
Founder
15 years of Cybersecurity and
Information Assurance product and services experience
Zal Azmi
Chief Strategy Officer
Former CIO of the FBI
CEO, Nexus Solutions LLC
Dan Woolley
Mach 37 General Partner
Dell, Computer Associates
CEO, Global Integrity
Charles Gold
C. Gold Strategic Marketing
20 years software marketing experience
Skip Lawver
Former Cybercrime SME
Professor Emeritus, Eastern Michigan
University
Informal Advisors
(in contractual discussions)
On behalf of Key Cybersecurity, Inc., we thank you for your time and consideration.
Privileged and Confidential