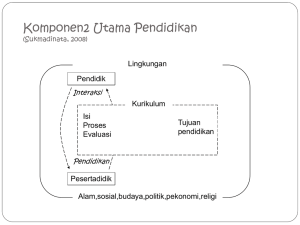
Topic 1.1 Introduction to Information and
Communication Technology
1.1.1.1 Define ICT
ICT IS THE TECHNOLOGY REQUIRED FOR INFORMATION
PROCESSING, IN PARTICULAR, THE USE ELECTRONICS
COMPUTERS, COMMUNICATION DEVICES AND APPLICATION
SOFTWARE TO CONVERT, STORE, PROTECT, PROCESS,
TRANSMIT AND RETRIEVE INFORMATION FROM ANYWHERE,
ANYTIME.
ICT ADALAH TKNOLOGI BERKAITAN PEMPROSESAN
MAKLUMAT , DALAM KATA LAINNYA ADALAH BERKENAAN
PENGGUNAAN KOMPUTER, PERANTI KOMUNIKASI DAN
APLIKASI PERISIAN UNTUK MENUKAR , MENGAWASI,
MEMPEROSES, MENGHUBUNG DAN MENGHASILKAN
MAKLUMAT BILA-BILA DAN DI MANA SAHAJA
1.1.1.2 Describe the brief evolution of
computers
FIRST GENERATION COMPUTERS(1940-1956)
VACUUM TUBES WAS INTRODUCES, IS AN ELECTRONIC TUBE
MADE OF GLASS USED AS COMPUTER COMPONENTS TO STORE
AND PROCESS DATA.
ENIAC IS FIRST GENERATION COMPUTER THAT CONTAINS
WEIGHTS OF 30 TONS, 18000 VACUUM TUBES, 30-50 FOOT
SPACE AND 16000 WATTS OF POWER.
GENERASI PERTAMA (940-1956)
TIUB VAKUM DIPRKENALKAN. MERUPAKAN ALAT ELEKTRONIK
DIPERBUAT DARIPADA KACA DAN DIGUNAKAN SEBAGAI
KOMPONEN KOMPUTER UNTUK MENYIMPAN MEMPOSES DATA
GENERASI KOMPUTER PERTAMA (ENIAC) MEMPUNYAI BERAT
30 TAN, 18000 TIUB VAKUM, LUAS 30 KE 50 KAKI DAN
MENGGUNAKAN KUASA 16000 WATTS.
SECOND GENERATION COMPUTERS(1956-1963)
TRANSISTORS REPLACE VACUUM TUBES IN THIS
GENERATION. TRANSISTORS ARE SMALL DEVICES THAT
TRANSFER ELECTRONIC SIGNAL ACROSS RESISTOR.
TRANSISTOR DO NOT PRODUCED LOTS OF HEATS AND
USE LESS POWER ALSO FASTER, CHEAPER AND SMALLER
THAN VACUUM TUBES.
GENERASI KEDUA KOMPUTER (1956-1963)
◦ TRANSISTOR MENGGANTIKAN TIUB VAKUM DIMANA IA
PERANTI LEBIH KECIL YANG MENUKAR SIGNAL
ELEKTRONIK MERENTASI PERINTANG
◦ TRANSISTOR TIDAK MENGHASILKAN HABA YANG
BANYAK(TIDAK PANAS) DAN KURANG MENGGUNAKAN
KUASA, MURAH DAN KECIL BERBANDING TIUB VAKUM.
THIRD GENERATION COMPUTERS(1964-1971)
INTEGRATED CIRCUITS (IU) REPLACED TRANSISTOR.
AN IU IS A COMPLETE ELECTRONIC CIRCUIT ON A
SMALL CHIP MADE OF SILICONE.
IU WAS RELIABLE, COMPACT AND CHEAPER THAN
TRANSISTORS
GENERASI KETIGA KOMPUTER(1964-1971)
◦ SIRKIT INTEGRASI MENGGANTIKAN TRANSISTOR
◦ IA MERUPAKAN SIRKIT ELEKTRONIK YANG
LENGKAP DIATAS CIP YANG KECIL DIPERBUAT
DARIPAD SILIKON
◦ IA SANGAT SESUAI, KECIL DAN MURAH
BERBANDING TRANSISTOR
FOURTH GENERATION COMPUTERS(1971-PRESENT)
MICROPROCESSOR WAS INTRODUCED, FROM THOUSAND OF
INTEGRATED CIRCUITS CHANGE ONTO SINGLE SILICONE CHIP.
THE INTEL 4004 CHIP DEVELOPED IN 1971, LOCATED ALL THE
COMPONENTS OF THE COMPUTER FROM THE CENTRAL
PROCESSING UNITS AND MEMORY TO INPUT/OUTPUT
CONTROLS ON A SINGLE CHIP.
COMPUTER IS 100 TIMES SMALLER THAN ENIAC COMPUTER IN
FIRST GENERATION.
GENERASI KEEMPAT KOMPUTER (1971-AKAN DATANG)
◦ MENGGUNAKAN MIKROPEMPROSESAN, DARIPADA BERIBU
SIRKIT INTEGRASI BERTUKAR KEPADA CIP SILIKON YANG
TUNGGAL
◦ CIP INTEL 4004 DIBANGUNKAN PADA 1971, DIMANA
TERLETAKNYA SEMUA KOMPONEN KOMPUTER DARIPADA
UNIT PEMEPROSESAN PUST DAN MEMORI UNTUK
PENGAWALAN INPUT OUTPUT DIATA CIP TUNGGAL.
FIFTH GENERATION COMPUTER(PRESENT –BEYOND)
FIFTH GENERATION COMPUTING DEVICES BASED ON
ARTIFICIAL INTELLIGENCE ARE STILL IN
DEVELOPMENT THOUGH THERE ARE SOME
APPLICATIONS SUCH AS VOICE RECOGNITION THAT
ARE BEING USED TODAY.
GENERASI KELIMA KOMPUTER (AKAN DATANG –
MASA DEPAN)
◦ BERDASARKAN KEPDA KEPINTARAN BUATAN
DIMANA TELAH DIBINA DAN DIPERTINGKATKAN
PEMBANGUNANNYA SEPERTI FACE VERIFICATION
(PENGENALAN MELALUI WAJAH) YANG MANA
TELAH MULA DIGUNAKAN KINI.
1.1.2.1 LIST THE USAGE OF ICT IN EVERYDAY
LIFE.
EDUCATION
(PELAJARAN)
BANKING
(PERBANKAN)
INDUSTRY
(INDUSTRI)
E-COMMERCE (E-PERDAGANGAN)
1.1.2.2 State the differences between computerized and non-computerized systems.
COMPUTERIZED
ALL BANKING ACTIVITIES ARE DONE BY USING COMPUTER SYSTEM
TRANSACTION CAN BE DONE ANYWHERE AND ANYTIME
IT TAKES SHORTEN TIME FOR ANY BANKING PROCESS
MORE PRODUCTIVE.
MENGGUNAKAN KOMPUTER
SEMUA AKTIVIT PERBANKAN MENGGUNAKAN SISTEM KOMPUTER
TRANSAKSI BOLEH DILAKUKAN BILA-BILA DAN DI MANA SAHAJA
MENGAMBIL MASA YANG SEDIKIT MELAKUKAN PROSES PERBANKAN
LEBIH PRODUKTIF/CEKAP
NON-COMPUTERIZED
ALL BANKING ACTIVITIES WERE DONE MANUALLY
TRANSACTION CAN ONLY BE MADE DURING WORKING HOURS.
IT TAKES LONG TIME FOR ANY BANKING PROCESS
LESS PRODUCTIVE
TIDAK MENGGUNAKAN KOMPUTER
SEMUA AKTIVITI BANK DIJALANKAN SECARA MANUAL
TRANSAKSI DIJALANKAN DALAM WAKTU KERJA SAHAJA
MENGAMBIL PROSES LAMA MENJALANKAN KERJA
KURANG PRODUKTIF/KURANG CEKAP
1.1.2..1 State the impact of ICT on society.
POSITIVE IMPACTS
FASTER COMMUNICATION SPEED
LOWER COMMUNICATION COST
CAN SHARE OPINIONS AND INFORMATION
PAPERLESS ENVIRONMENT
INFORMATION AND COMMUNICATION BORDERLESS THROUGH INTERNET.
KESAN POSITIF
KOMUNIKASI CEPAT
KOS KOMUNIKASI RENDAH
PERKONGSIAN MAKLUMAT
PERSEKITARAN TIADA KERTAS
DUNIA TANPA SEMPADAN (INTERNET)
NEGATIVE IMPACTS
CAN BE NEGATIVE BECAUSE IT COURAGE PEOPLE TO ACCESS PORNOGRAPHY AND
VIOLENCE WEB SITES.
CAN HARM USES FOR LONG HOURS USED
KESAN NEGATIF
PENYALAHGUNAAN KOMPUTER (PORNOGRAFI DAN KEGANASAN)
KESAN BURUK JIKA DIGUINAKAN TERLALU LAMA
Topic 1.2 Computer Ethics and Legal Issues
1.2.1.1 DEFINE COMPUTER ETHICS, CODE OF ETHICS, INTELLECTUAL PROPERTY,
PRIVACY, COMPUTER CRIME AND CYBER LAW.
1. COMPUTER ETHICS IS A SYSTEM OF MORAL STANDARDS OR VALUES USED AS A
GUIDELINE FOR COMPUTER USERS ETHICAL.
ETIKA KOMPUTER ADALAH SISTEM BERKAITAN STANDARD MORAL ATAU NILAI
YANG DIGUNAKAN EBAGAI PANDUAN BAGI PENGGUNA KOMPUTER
2. CODE OF ETHICS IS GUIDELINES IN ICT THAT HELP DETERMINE WHETHER A
SPECIFIC COMPUTER ACTION IS ETHICAL OR UNETHICAL.
KOD ETIKA ADALAH PANDUAN BAGI MEMASTIKAN SAMADA PERLAKUAN
MENGGUNAKAN KOMPUTER ITU BERETIKA ATAU TIDAK
3. INTELLECTUAL PROPERTY REFERS TO WORKS CREATED BY INVENTORS, AUTHORS
AND ARTISTS.
HAK MILIK INTELETUAL MERUJUK KEPADA KERJA YANG DIBUAT OLEH PENCIPTA
SEPERTI ARTIS , PEMBUAT PROGRAM DAN SEBAGAINYA.
4. PRIVACY REFERS TO THE RIGHT OF INDIVIDUALS AND COMPANIES TO DENY OR
RESTRICT AND COLLECTION AND USED OF INFORMATION ABOUT THEM.
PRIVASI MRUJUK KEPADA HAK MILIK INDUK ATAU SYARIKAT
5. COMPUTER CRIME IS ANY ILLEGAL ACTS INVOLVING COMPUTERS.
JENAYAH KOMPURER PERLAKUAN TIDAK BAIK MEMBABITKAN KOMPUTER
6. CYBER LAW REFERS TO ANY LAWS RELATING TO PROTECTING THE INTERNET AND
OTHER ONLINE COMMUNICATION TECHNOLOGIES
UNDANG-UNDANG SIBER MERUJUK KEPADA UNDANG-UNDANG BAGI MELINDUNGI
KEPENTINGAN BDERKAITAN INTERNET DAN TEKNOLOGI KOMUNIKASI
1.2.1.2 Differentiate between ethics and law.
Law
Ethics
AS A RULE TO CONTROL COMPUTER USERS.
PERATURAN MENGAWAL PENGGUNA PC
AS A GUIDELINE TO COMPUTER USERS
PANDUAN UNTUK PEN GGNA KOMPUTER
TO PREVENT MISUSE OF COMPUTERS
MENGELAKKAN PENYALAHGUNAAN PC
ETHICAL BEHAVIOR IS JUDGED BY MORAL
STANDARDS. KELAKUAN DIHAKIMI OLEH
STANDARD MORAL
COMPUTER USERS MUST FOLLOW THE
REGULATIONS AND LAW. PENGGUNA PC
MESTI MEMATUHINYA
COMPUTER USERS ARE FREE TO FOLLOW
OR IGNORE THE CODE OF ETHICS. BEBAS
UNTUK MENGIKUT ETIKA ATAU TIDAK
PUNISHMENTS ADA HUKUMAN
NO PUNISHMENT FOR ANYONE WHO
VIOLATES ETHICS. TIADA HUKUMAN UNTUK
MEREKA YANG MELANGGARNYA
DEPEND ON COUNTRY AND STATE WHERE
THE CRIME IS COMMITTED BERGANTUNG
KEPADA NEGARA YANG TERBABIT
UNIVERSAL, CAN BE APPLIED ANYWHERE,
ALL OVER THE WORLD SEMUA TEMPAT DI
DUNIA
NOT OBEYING LAWS ARE CALLED CRIME
TIDAK MEMATUHI AKAN DIGELAR
PENJENAYAH
NOT FOLLOWING ETHICS ARE CALLED
IMMORAL TIDAK MEMATUHINYA DIGELAR
TIDAK BERMORAL
1.2.1.3 State the need for intellectual property laws
AS BUSINESSES CONTINUE TO EXPAND GLOBALLY, BUSINESS OWNERS MUST
REALIZE THE IMPORTANCE OF GETTING PROFESSIONAL ADVICE ON HOW TO
ESTABLISH AND SAFEGUARD THEIR INTELLECTUAL PROPERTY RIGHTS. THESE
INCLUDE :
o TRADEMARKS FOR BRAND IDENTITY
o COPYRIGHTS FOR MATERIALS
o PATENTS FOR INVENTIONS
o DESIGN FOR PRODUCT APPEARANCE
PERNIAGAAN BERKEMBANG SECARA GLOBAL DIMANA PEMILIK MESTI SEDAR
KEPENTINGAN MENDAPATKAN KHIDMAT NASIHAT BAGAIMANA MENJAGA
HAK MILIK MEREKA. INI MERANGKUMI
o IDENTITI PRODUK
o HAKCIPTA
o PATEN
o REKABENTUK
1.2.2.1 List ways to protect privacy.
PRIVACY CAN BE PROTECTED BY:
(A) PRIVACY LAW
THE PRIVACY LAWS IN MALAYSIA EMPHASISES ON THE FOLLOWING:
- SECURITY SERVICES TO REVIEW THE SECURITY POLICY
- SECURITY MANAGEMENT TO PROTECT THE RESOURCES
- SECURITY MECHANISM TO IMPLEMENT THE REQUIRED SECURITY
SERVICES
- SECURITY OBJECTS, THE IMPORTANT ENTITIES WITHIN THE
SYSTEM ENVIRONMENT
(A) UNDANG-UNDANG PRIVASI
UNDANG-UNDANG PRIVASI DI MALAYSIA BERKAITAN DENGAN
- SERVIS KESELAMATAN UNTUK MEMAPARKAN POLISI KESELAMATAN
- PENGURUSAN KESELAMATAN UNTUK MENGAWAL SUMBER
- MEKANISMA KESELAMATAN BAGI MENGIMPLEMENTSI KEPERLUAN
PERKHIDMATAN KESELAMATAN
- OBJEK KESELAMATAN, ENTITI PENTING BERKAITAN PERSEKITARAN
KESELAMATAN
1.2.2.1 List ways to protect privacy.
PRIVACY CAN BE PROTECTED BY:
(B) UTILITIES SOFTWARE
- INSTALL ANTI-SPAM PROGRAM, FIREWALL, ANTI-SPYWARE AND
ANTIVIRUS
- PURCHASE GOODS WITH CASH RATHER THAN CREDIT CARD
- CLEAR YOUR HISTORY FILE WHEN YOU ARE FINISHED BROWSING
- FILL IN ONLY NECESSARY INFORMATION ON WARRANTY AND
REGISTRATION FORM.
(B) PERISIAN UTILITI
- MENGINSTALL PROGRAM ANTI SPAM, DINDING API, ANTI PERISIK DAN
ANTIVIRUS
- MEMBELI BARANGAN SECARA TUNAI
- MENGHILANGKAN SEJARAH CARIAN INTERNET APABILA SELESAI
MELAYARI INTERNET
- HANYA MENGISI PERKARA YANG PERLU DALAM BORANG INTERNET
1.2.2.2 State authentication and verification methods/ technologies.
AUTHENTICATION IS A PROCESS WHERE USERS VERIFY THEIR IDENTITY. AUTHENTICATION
DEALS WITH THE PROBLEM OF DETERMINING WHETHER A USER SHOULD BE ALLOWED
ACCESS TO A PARTICULAR SYSTEM.
PEMBUKTIAN MERUPAKAN PROSES DI MANA PENGGUNA MENGESAHKAN BUKTI IDENTITI
SAMADA PENGGUNA ITU DIBENARKAN ATAU TIDAK MENGAKSES SESUATU SISTEM
METHODS OF AUTHENTICATION
THERE ARE TWO COMMONLY USED AUTHENTICATION METHODS, WHICH ARE BIOMETRIC
DEVICE AND CALLBACK SYSTEM.
LANGKAH DALAM PEMBUKTIAN
ADA 2 CARA YANG BIASA IAITU PERANTI BIOMETRIK DAN SISTEM PANGGIL SEMULA
A. BIOMETRIC DEVICE/ PERANTI BIOMETRIK IS A DEVICE THAT TRANSLATES PERSONAL
CHARACTERISTICS INTO A DIGITAL CODE THAT IS COMPARED WITH A DIGITAL CODE
STORED IN THE DATABASE.
ADALAH PERANTI YANG MENUKAR KARAKTOR PERIBADI KEPADA KOD DIGITAL YANG BOLEH
MEMBANDINGKAN DENGAN KOD DIGITAL YANG DISIMPAN DALAM PANGKALAN DATA
B. CALLBACK SYSTEM/SISTEM PANGGIL SEMULA REFERS TO THE CHECKING SYSTEM THAT
AUTHENTICATES THE USER
MERUJUK KEPADA SISTEM YANG MENYEMAK PEMBKTIAN OLEH PENGGUNA
1.2.2.2 State authentication and verification methods/ technologies.
METHODS OF VERIFICATION
THERE ARE TWO METHODS COMMONLY USED IN VERIFICATION, WHICH
ARE USER IDENTIFICATION AND PROCESSED OBJECT.
LANGKAH DALAM PENGESAHAN
2 KAEDAH BIASA DALAM PENGESAHAN ADALAH MENGENALPASTI
IDENTITI DAN OBJEK PEMPROSESAN
A. USER IDENTIFICATION/PENGENALPASTI IDENTITI REFERS TO THE
PROCESS OF VALIDATING THE USER.
MERUJUK KEPADA PROSES YANG DIJALANKAN PRNGGUNA BAGI
PENGESAHAN
B. PROCESSED OBJECT/ OBJEK PEMPROSESAN REFERS TO SOMETHING
THE USER HAS SUCH AS IDENTIFICATION CARD, SECURITY TOKEN
AND CELL PHONE.
MERUJUK KEPADA PENGGUNA YANG MEMPUNYAI OBJEK SEPERTI KAD
PENGENALAN, TOKEN KESELAMATAN DAN TELEFON.
1.2.3.1 a)List effects of controversial contents of pornography on society
PORNOGRAPHY
CAN LEAD TO CRIMINAL ACTS SUCH AS EXPLOITATION OF WOMEN AND CHILDREN
CAN LEAD TO SEXUAL ADDICTION OR PERVERSION
CAN DEVELOP LOW MORAL VALUE TOWARDS OTHER MEN, WOMEN OR CHILDREN
CAN ERODE GOOD RELIGIOUS, CULTURAL AND SOCIAL BELIEFS AND BEHAVIOR
PORNOGRAFI
◦ BOLEH MENGGALAKKAN PERLAKUAN JENAYAH SEPERTI EKSPLOITASI WANITA DAN KANAKKANAK
◦ BOLEH MENJURUS KEPADA PERLAKUAN SEKS
◦ BOLEH MEMBANGUNAKAN NILAI MORAL YANG RENDAH TERHADAP LELAKI DAN WANITA
NAHUPUN KANAK-KANAK
SLANDER
CAN DEVELOP INTO A SOCIETY THAT DISREGARDS HONESTY AND TRUTH
CAN DEVELOP BAD HABIT OF SPREADING UNTRUTHS AND RUMORS
CAN LEAD TO UNNECESSARY ARGUMENT
CAN CAUSE PEOPLE TO HAVE NEGATIVE ATTITUDES TOWARDS ANOTHER PERSON
FITNAH
BOLEH MEMBANGUNKAN MASYARAKAT YANG TIDAK JUJUR
BOLEH MEMBANGUNKAN TABIAT BURUK SEPRTI MENYEBARKAN KHABAR ANGIN
MEMBAWA KEPADA PERTELINGKAHAN YANG TIDAK PERLU
BOLEH MENYEBABKAN PERLAKUAN NEGATIF ANTARA SAU SAMA LAIN ATAU MASYARAKAT
KESELURUHANNYA
1.2.3.2 Describe the process of filtering to control access to controversial contents
THE METHOD OF CHOICE TO LIMIT ACCESS ON THE INTERNET IS TO FILTER EITHER BY
A. KEYWORD BLOCKING. THE METHOD USES A LIST OF BANNED WORD OR OBJECTS TERMS
SUCH AS XXX, SEX, AND NUDE. AS THE PAGE IS DOWNLOADING, THE FILTER
SEARCHES FOR ANY OF THESE WORDS. IF FOUND, IT WILL BLOCKED THE PAGE
COMPLETELY. STOP DOWNLOADING THE PAGE, BLOCK THE BANNED WORDS AND
EVEN SHUT DOWN THE BROWSER.
B. SITE BLOCKING. THE METHOD USE SOFTWARE TO LIST THE WEBSITES THAT WILL BE
BLOCKED BY USING SOFTWARE. THE SOFTWARE PREVENTS USERS FROM BEING
ACCESS THE WEB SITES ON LIST.
C. WEB RATING SYSTEM. WEB SITES ARE RATING IN TERMS OF NUDITY, SEX, VIOLENCE AND
LANGUAGE. THE WEB SITES RATE CAN BE DONE BY SETTING THE BROWSER TO ONLY
ACCEPT PAGE WITH CERTAIN LEVEL OF RATINGS.
LANGKAH PENAPISAN DALAM MELAYARI INTERNET ADALAH
A. PENGHALANG KATAKUNCI
KATAKUNCI YANG BERKAITAN DENGAN PERKARA-PERKARA BURUK DISIMPAN DALAM
PANGKALAN DATA.PENGGUNA YANG MENAIP ATAU MENEKAN PERKATAAN TERSEBUT
AKAN DIHALANG DARI MENGAKSES LAMAN BERKAITAN PERKARA TERSEBUT
B. PENGHALANG TAPAK
SATU PERISIAN BERFUNGSI UNTUK MENGENALPASTI LAMAN-LAMAN YANG TIDAK
PATUT ATAU BOLEH DILAYARI.
C. SISTEM RATING WEB
MERUPAKAN SISTEM YANG MENGENALPASTI LAMAN-LAMAN YANG TIDAK BAIK YANG
SELAU DILAYARI. SISTEM AKAN MENGHALANG PENGGUNA DARIPADA MELAYARI
LAMAN-LAMAN WEB TERSEBUT.
1.2.4.1 Explain the need for cyber law
THE NEED FOR CYBER LAW IS TO PROTECT THE INTERNET AND OTHER
ONLINE
COMMUNICATION TECHNOLOGIES.THE NEEDS OF CYBER LAW ARE
INTEGRITY AND SECURITY INFORMATION
LEGAL STATUS OF ONLINE TRANSACTIONS
PRIVACY AND CONFIDENTIALLY OF INFORMATION
INTELLECTUAL PROPERTY RIGHTS
SECURITY OF GOVERNMENT DATA
KEPERLUAN UNDANG-UNDANG SIBER ADALAH UNTUK MENGAWAL INTERNET
DAN LAIN-LAIN TEKNOLOGI ATAS TALIAN. IA BERKAITAN
MAKLUMAT KESELAMATAN DAN INTEGRITI
TRANSAKSI ATAS TALIAN YANG SAH
MAKLUMAT PRIVASI DAN SULIT
HAK CIPTA TERPELIHARA
KESELAMATAN DATA KERAJAAN
1.2.4.2 Explain briefly the computer crimes below:
COMPUTER FRAUD IS DEFINED AS HAVING AN INTENTION TO TAKE
ADVANTAGE OVER OR CAUSING LOSS TO OTHER PEOPLE, MAINLY ON
MONETARY BASIS THROUGH THE USE OF COMPUTERS.
THERE ARE MANY FORMS OF COMPUTER FRAUD WHICH INCLUDE EMAIL HOAXES, PROGRAM FRAUD, INVESTMENT SCHEMES, SALES
PROMOTIONS AND CLAIMS OF EXPERTISE ON CERTAIN FIELDS.
PENIPUAN KOMPUTER MERUJUK KEPADA MENGAMBIL PERHATIAN
ATAU KESEMPATAN YANG BOLEH MENGAKIBATKAN KERUGIAN
KEPADA ORANG LAIN MENERUSI PENGGUNAAN KOMPUTER.
CONTOHNYA PENIPUAN EMAIL, SKIM PELABURAN, PROMOSI JUALAN
DSBNYA.
COPYRIGHT INFRINGEMENT IS DEFINED AS A VIOLATION OF THE
RIGHTS SECURED BY A COPYRIGHT. COPYRIGHT INFRINGEMENT
INVOLVES ILLEGAL COPY OR REPRODUCTION OF COPYRIGHTS
MATERIAL BY THE BLACK MARKET GROUP. THE OPEN COMMERCIAL
SALE OF PIRATED ITEM IS ALSO ILLEGAL.
PELANGGARAN HAKCIPTA MERUJUK KEPADA PELANGGARAN KEPADA
HAKCIPTA, MENYALIN SEMULA TANPA KEBENARAN DAN
SEBAGAINYA.
1.2.4.2 Explain briefly the computer crimes below:
COMPUTER THEFT IS DEFINED AS THE UNAUTHORIZED USE OF ANOTHER
PERSON’S PROPERTY WITH THE INTENTION TO DENY THE OWNER THE
RIGHTFUL POSSESSION OF THAT PROPERTY OR ITS USE.EXAMPLES OF
COMPUTER THEFT INCLUDE:
TRANSFER OF PAYMENTS TO THE WRONG ACCOUNTS
GET ONLINE MATERIALS WITH NO COST
TAP INTO DATA TRANSMISSION LINES ON DATABASE AT NO COST
DIVERT GOODS TO THE WRONG DESTINATION
PENCURIAN KOMPUTER BERMAKSUD PENGGUNAAN TANPA KEBENARAN
KEATAS HAK MILIK ORANG LAIN DENGAN NILAI MEROSAK, MENGUBAH,
MENUKAR DAN SEBAGAINYA
◦ PENGALIHAN WANG DARI AKAUN ORANG LAIN
◦ MENDAPAT BARANAN ATAS TALIAN TANPA BAYAR
◦ MENDAPAT MAKLUMAT TAMNPA BAYARAN\
◦ MENGALIHKAN PENGHANTARAN BARANGAN KE TEMPAT LAIN
1.2.4.2 Explain briefly the computer crimes below:
COMPUTER ATTACK MAY BE DEFINED AS ANY ACTIVITIES TAKEN TO DISRUPT
THE EQUIPMENT OF COMPUTER SYSTEMS, CHANGE PROCESSING CONTROL OR
CORRUPT STORED DATA.
COMPUTER ATTACK CAN BE IN THE FORMS OF:
PHYSICAL ATTACK THAT DISRUPT THE COMPUTER FACILITY OR ITS
TRANSMISSION LINES.
AN ELECTRONIC ATTACK THAT USES THE POWER OF ELECTROMAGNETIC
ENERGY TO OVERLOAD COMPUTER CIRCUITRY.
A COMPUTER NETWORK ATTACK THAT USES A MALICIOUS CODE TO
EXPLOIT A WEAKNESS IN SOFTWARE, OR IN THE COMPUTER SECURITY
PRACTICES OF A COMPUTER USER
SERANGAN KOMPUTER DIDEFINISIKAN SEBAGAI AKTIVITI MENGGANGU
PERALATAN KOMPUTER , MENGUBAH KAWALAN DAN MEROSAKKAN DATA
YANG DISIMPAN. SERANGAN KOMPUTER BOLEH DALAM BENTUK
◦ SRANGAN FIZIKAL YANG MEROSAKKAN PERALATAN DAN TALIAN PENGHANTARAN
◦ SERANGAN ELEKTRONOK DI MANA BOLEH MENYEBABKAN KEROSAKAN ATAS
PERALATAN AKIBAT LEBIHAN KUASA.
SERANGAN RANGKAIAN KOMPUTER DENGAN MENGGUNAKAN KOD
SERANGAN BAGI MENGEKSPLOIT KELEMAHAN PERISIAN DSBNYA
1.3.1 Definition
1.3.1.1 Define Computer security.
COMPUTERS SECURITY MEANS PROTECTING
OUR COMPUTER SYSTEMS AND THE
INFORMATION THEY CONTAINS AGAINST
UNWANTED ACCESS, DAMAGE,
DESTRUCTION OR MODIFICATION.
KESELAMATAN KOMPUTER BERMAKSUD
MELINDUNGI SISTEM KOMPUTER DAN
MAKLUMAT DI DALAMNYA DARIPADA AKSES
YANG TIDAK DIBENARKAN, KEROSAKAN
DAN PENGUBAHAN
1.3.2.1 Explain briefly the different threats to computer
security:
MALICIOUS CODE IS ALSO KNOWN AS A ROUGE PROGRAM. IT
IS A TREAT TO COMPUTING ASSETS BY CAUSING UNDESIRED
EFFECTS IN THE PROGRAMMER’S PART. THE EFFECT CAUSE BY
AGENT, WITH THE INTENTION TO CAUSE DAMAGE. THE
AGENT FOR MALICIOUS CODE IS THE WRITER OF THE CODE,
OR ANY PERSON WHO CAUSES ITS DISTRIBUTION. THERE ARE
VARIOUS KINDS OF MALICIOUS CODE. THEY INCLUDE VIRUS,
TROJAN HORSE, LOGIC DOOR, TRAPDOOR AND BACKDOOR,
WORM AND MANY OTHERS.
KOD MALICIOUS JUGA DIKENALI SEBAGAI PROGRAM PEMECAH.
IA MENGGANGU ASET KOMPUTER DENGAN MENYEBABKAN
KEROSAKAN. AGEN KOD INI AKAN MENGUBAH KOD YANG
TERDAPAT DALAM PROGRAM DAN MEROSAKKAN KOMPUTER
DENGAN KESANNYA SEPERTI GANGGUAN KEPADA
PERJALANAN PROGRAM. CONTOHNYA TROJAN HORSE, LOGIC
DOOR, TRAPDOOR DAN BACKDOOR, WORM(CECACING) DAN
BANYAK LAGI
1.3.2.1 Explain briefly the different threats to computer security:
HACKING IS A SOURCE OF THREAT TO SECURITY IN COMPUTER. IT IS DEFINED
AS UNAUTHORIZED ACCESS TO THE COMPUTER SYSTEM BY A HACKER.
HACKERS ARE PERSONS WHO LEARN ABOUT THE COMPUTER SYSTEM IN
DETAIL. THEY WRITE PROGRAM REFERRED TO AS HACKS. HACKERS MAY USE
A MODEM OR CABLE TO HACK THE TARGETED COMPUTERS.
HACKING ADALAH SUMBER GANGGUAN KEPADA KESELAMATAN DALAM
KOMPUTER. IA BOLEH DIISTILAHKAN SEBAGAI AKSES TANPA KEBENARAN
KEPADA SISTEM KOMPUTER OLEH ORANG YANG DIKENALI SEBAGAI HACKER.
HACKER ADALAH ORANG YANG ADA KEPANDAIAN TENTANG SISTEM
KOMPUTER. MEREKA MENULIS PROGRAM KOMPUTER BERDASARKAN
PENGGUNAAN MODEM DAN KABEL UNTUK MEROSAKKAN KOMPUTER.
ENVIRONMENTAL DISASTER. BE IT AT HOME, STORES, OFFICES AND ALSO
AUTOMOBILES. EXAMPLES OF NATURAL AND ENVIRONMENTAL DISASTERS:
FLOOD
FIRE
EARTHQUAKES, STORMS AND TORNADOS
EXCESSIVE HEAT
INADEQUATE POWER SUPPLY
BENCANA ALAM ADALAH JUGA SATU CARA YANG MEROSAKKAN KOMPUTER.
CONTOHNYA BANJIR, TANAH RUNTUH, GEMPA BUMI DAN SEBAGAINYA.
1.3.3.1 Select the appropriate security measures to overcome the
identified computer threats.
Data Backup :
Cryptography
Anti virus
Anti spyware
Firewall
Human Aspects
1.3.3.2 Apply the correct security procedures.
DATA BACKUP :
SALINAN FAIL ATAU PROGRAM DALAM BENTUK CD ATAU DVD, DISKET ATAU CAKERA
KERAS
CRYPTOGRAPHY
PROSES MENYEMBUNYIKAN MAKLUMAT DENGAN MENGUBAH MAKLUMAT DALAM
BENTUK YANG LAIN TETAPI DIFAHAMI OLEH EMPUNYANYA.
ANTI VIRUS
MENGGUNAKAN PERISIAN ANTI VIRUS. CONTOH KASPERSKY, AVD, PANDA DAN
SEBAGAINYA
ANTI SPYWARE
PERISIAN YANG MELINDUNGI KOMPUTER DARIPADA PERISIKAN LUAR MELAUI ATAS
TALIAN DIMANA SPYWARE AKAN MENCURI MAKLUMAT PENTING PENGGUNA SEPERTI NO
PIN BANK DAN SEBAGAINYA.
FIREWALL
MELINDUNGI KOMPUTER BERDASARKAN POLISI KESELAMATAN. BOLEH BERBENTUK
PERKAKASAN ATAU PERISIAN. 3 JENISIAITU
SCREENING ROUTERS- RINGKAS, HANYA MELIHAT ALAMAT DAN JENIS PROTOCOL.
PROXY GATEWAY- RUMIT, MLIHAT KESELURUHAN TEKS
GUARD-LEBIH RUMIT, JUGA MELIHAT KESELURUHAN TEKS
HUMAN ASPECTS
MERUJUK KEPADA PENGGUNA DAN JUGA PENGGANGU DALAM SISTEM KOMPUTER.
1.4.1 Impact of ICT on Society
1.4..1.1 Impact of ICT on Society
POSITIVE IMPACT
FASTER COMMUNICATION SPEED. WITH THE INTERNET, NEWS OR MESSAGE ARE
SEND VIA E-MAIL TO ANYONE EFFICIENTLY. WITH THE CAPABILITY OF BROADBAND
AND SPEED OF CONNECTION ON THE INTERNET, ANY INFORMATION CAN BE
TRAVEL FASTER.
LOWER COMMUNICATION COST. WITH THE INTERNET, WE DO NOT HAVE TO PAY
ANY BASIC SERVICES PROVIDED BY IN THE INTERNET. FURTHERMORE, THE COST OF
THE CONNECTION TO THE INTERNET IS RELATIVELY CHEAP.
IPEOPLE CAN SHARE OPINION FROM INFORMATION THROUGH DISCUSSION GROUP
AND FORUMS THROUGH INTERNET.
INFORMATION CAN BE STORED AND RETRIEVED THROUGH THE DIGITAL MEDIUM
INSTEAD OF PAPER. (PAPERLESS ENVIRONMENT)
INFORMATION AND COMMUNICATION CAN BE BORDERLESS THROUGH INTERNET.
BY USING INTERNET, PEOPLE ALL AROUND THE WORLD CAN BE CONNECTED
THROUGH EACH OTHER.
IMPAK POSITIF
KELAJUAN KOMUNIKASI YANG CEPAT – MELALUI INERNET, BERITA ATAU MESEJ
MENERUSI EMAIL AKAN LEBIH CEPAT DAN PANTAS.
KOS KOMUNIKSI YANG RENDAH – DENGAN INTERNET, KITA TIDAK PERLU MEMBUAT
PEMBAYARAN ASAS PERKHIDMATAN.
MANUSIA BOLEH BERKONGSI MAKLUMAT – MELALUI FORUM INTERNET
PENYIMPAN MAKLUMAT BOLEH DIBUAT DAN TANPA KERTAS
DUNIA TANPA SEMPADAN – DENGAN INTERNET , MANUSIA BOLEH BERHUBUNG
DENGAN SEMUA ORANG DI DUNIA DENGAN MUDAH
NEGATIVE IMPACT
Borderless information at time can be negative because it
courage people to access pornography and violence website. It
can cause low moral values. It also can created problems such as
gambling, information theft and fraud.
Computers can harms users if they use for long hours frequently
KESAN NEGATIF
MAKLUMAT TANPA SEMPADAN KADANGKALA ADALAH NEGATIF
– CONTOHNYA MENGGALAKKAN PORNOGRAFI DAN KEGANASAN
KOMPUTER MENGGANGGU KESIHATAN JIKA DIGUNAKAN
TERLALU LAMA.
Choose ONE of the following topics:
Copyright and Piracy from Moral and Legal
Standpoints.
Lack of Security and its Effects on
Industry/Economy/ Government.
Malaysian Cyber Law, Electronic
Government Law.
Phishing
Virus (Trojan Horse, Salami Attack)
Hacking
Security Measures (Biometrics,
Authentication
DIGITAL SIGNATURE ACT 1997
TELEMEDICINE ACT 1997
COMPUTER CRIME ACT 1997
COMMUNICATION AND MULTIMEDIA ACT
19989