Access list - Bill Buchanan
advertisement

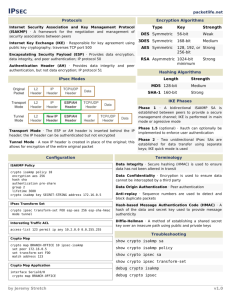
E-Security
CO73046
Network
Security
Contact:
Room:
Telephone:
MSN Messenger:
WWW:
w.buchanan@napier.ac.uk
C.63
X2759
w_j_buchanan@hotmail.com
http://www.dcs.napier.ac.uk/~bill
http://buchananweb.co.uk
Author: Bill Buchanan
Prof. Bill Buchanan
Work Schedule
Week
Date
Academic
Assessment
Lab/Tutorial
1
4 Feb
1: Introduction
2: Security Fundamentals
2
11 Feb
3: IDS
Lab 1: Packet Capture
Lab 2: Packet Capture (Filter)
3
18 Feb
4: Encryption
Lab 3: Packet Capture (IDS)
Lab 4: Packet Capture (ARP)
4
25 Feb
5: Authentication (Part 1)
Lab 5: IDS Snort 1
5
3 Mar
5: Authentication (Part 2)
Lab 6: IDS Snort 2
6
10 Mar
6: Software Security
Lab 7: Private-key encryption
7
17 Mar
7: Network Security
8: Secure Protocols
Lab 8: Public-key encryption
8
7 Apr
9
14 Apr
Security Specialisation (.NET
Security or Network Security)
10
21 Apr
Security Specialisation (.NET
Security or Network Security)
Specialisation Lab
11
28 Apr
Security Specialisation (.NET
Security or Network Security)
Specialisation Lab
12
5 May
Security Specialisation (.NET
Security or Network Security)
C/W hand-in (IDS) [50%]
MCQ Test [10%]
Author: Bill Buchanan
MCQ Test [40%]
Friday, 11 Apr 2008
Week 1-8
Academic
Element
On-line test:
40%
Coursework: Agent-based IDS
Web-CT submission:
50%
Web-CT
submission
.NET Security
On-line test:
10%
Cisco Academy NS 1
On-line test:
10%
On-line
test
Author: Bill Buchanan
Week 8-13
MCQ
Test
Author: Bill Buchanan
Context-based
Access Lists
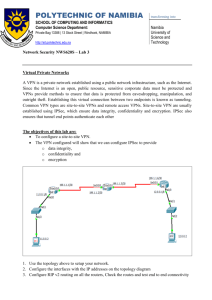
Context-based Access Control (CBAC) are thus stateful, and dynamic,
and can look further into packets than normal ACLs. In client-server
communications the key states in most connections are:
Author: Bill Buchanan
Client sends a SYN flag to the server.
The server responds with a SYN, ACK to the client.
The client responds with an ACK, and the connection is made.
The client and server then communicate.
The client sends a FIN, ACK flag.
The server sends an ACK flag, and the connection is finished.
Author: Bill Buchanan
ip inspect tcp synwait-time. This defines the time to wait before a
connection drops. Default: 30 seconds.
ip inspect tcp finwait-time. This defined the time after a FIN flag for a
connection to be dropped. Default: 5 seconds.
ip inspect tcp idle-time. This defines the length of time that a
connection can be idle. Default: 1 hour.
ip inspect dns-time. This defines the amount of time of a time-out for a
DNS query. Default: 5 seconds.
ip inspect max-incomplete high. This defines the maximum number of
half-open connections, before it starts to delete them one-by-one.
Default: 500.
ip inspect max-incomplete low. This defines the lower limit for the halfopen connections. Default: 400.
ip inspect one-minute high. This defines the maximum number of halfopen connections in a minute, before it starts to delete them one-by-one.
Default: 500 per minute.
ip inspect one-minute low. This defines the lower limit for the half-open
connections over a minute. Default: 400.
Author: Bill Buchanan
(config)# ip inspect ?
alert-off
Disable alert
audit-trail
Enable the logging of session information (addresses
and
bytes)
dns-timeout
Specify timeout for DNS
max-incomplete Specify maximum number of incomplete connections
before clamping
name
Specify an inspection rule
one-minute
Specify one-minute-sample watermarks for clamping
tcp
Config timeout values for tcp connections
udp
Config timeout values for udp flows
<cr>
(config)# ip inspect tcp ?
finwait-time
Specify timeout for TCP connections after a FIN
idle-time
Specify idle timeout for tcp connections
max-incomplete Specify max half-open connection per host
synwait-time
Specify timeout for TCP connections after a SYN and
no
further data
(config)# ip inspect max-incomplete low 900
(config)# ip inspect max-incomplete high 1100
and for the maximum open sessions for one-minute:
(config)# ip inspect one-minute low 900
(config)# ip inspect one-minute high 1100
get rid of IP inspect, use:
Author: Bill Buchanan
(config)# no ip inspect one-minute low
Access-list 200 permit tcp any any eq telnet
172.10.10.1
Author: Bill Buchanan
10.1.1.1
Telnet
server
10.1.1.1
Telnet
server
Access-list 200 permit tcp any any eq telnet
172.10.10.1
Access-list 201 deny ip any any
access-list 200 permit tcp any any eq telnet
access-list 201 deny ip any any
Author: Bill Buchanan
int fa0/1
ip access-group 200 out
ip access-group 201 in
10.1.1.1
Telnet
server
Access-list 200 permit tcp any any eq telnet
172.10.10.1
Access-list 201 deny ip any any
ip inspect name Telnet tcp
access-list 200 permit tcp any any eq telnet
access-list 201 deny ip any any
fa0/1
access-group 200 out
access-group 201 in
inspect Telnet out
Author: Bill Buchanan
int
ip
ip
ip
10.1.1.1
Telnet
server
Access-list 200 permit tcp any any eq telnet
172.10.10.1
Access-list 201 deny ip any any
ip inspect name Telnet tcp
access-list 200 permit tcp any any eq telnet
access-list 201 deny ip any any
fa0/1
access-group 200 out
access-group 201 in
inspect Telnet out
Show ip access-list 201
permit tcp host 10.1.1.1 eq telnet host host 172.10.10.1 eq 1234
deny ip any any
Author: Bill Buchanan
int
ip
ip
ip
Port greater than 1023
Listen on port+1
Passive FTP
Active FTP :
command : client >1023 -> server 21
data : client >1023 <- server 20
Passive FTP :
command : client >1023 -> server 21
data : client >1023 -> server >1023
Author: Bill Buchanan
Active FTP
Passive FTP
10.1.1.1
FTP
server
Author: Bill Buchanan
172.10.10.1
Passive FTP
10.1.1.1
FTP
server
Access-list 200 permit tcp any any eq ftp
Access-list 200 deny ip any any
172.10.10.1
access-list 200 permit tcp any any eq telnet
access-list 200 deny ip any any
Author: Bill Buchanan
int fa0/0
ip access-group 200 in
Passive FTP
10.1.1.1
FTP
server
Access-list 200 permit tcp any any eq ftp
Access-list 200 deny ip any any
172.10.10.1
ip inspect name FTPTEST tcp
access-list 200 permit tcp any any eq telnet
access-list 200 deny ip any any
Author: Bill Buchanan
int fa0/0
ip access-group 200 in
ip inspect FTPTEST in
Passive FTP
10.1.1.1
FTP
server
Access-list 200 permit tcp any any eq ftp
Access-list 200 deny ip any any
172.10.10.1
ip inspect name FTPTEST tcp
access-list 200 permit tcp any any eq ftp
access-list 200 deny ip any any
# show ip access-list 200
permit tcp host 172.10.0.1 eq 22140 host 10.1.1.1 eq 32540
permit tcp any any eq ftp
deny ip any any
Author: Bill Buchanan
int fa0/0
ip access-group 200 in
ip inspect FTPTEST in
access-list 101 permit ip 172.10.10.1 0.0.0.255 any
access-list 101 permit ip 192.168.1.0 0.0.0.255 any
int fa0/0
ip inspect myrule in
ip access-group 101 in
www server
172.10.10.2
All incoming traffic is barred
apart from the access to the
web server... but the CBAC
will open up the ACL if
a connection was initiated on
the inspect port (FA0/0).
access-list 102 permit tcp any host 172.10.10.2 eq www
access-list 102 deny ip any any
int s0
ip access-group 102 in
Author: Bill Buchanan
192.168.1.2
Author: Bill Buchanan
Author: Bill Buchanan
IPSec
Author: Bill Buchanan
VPN types
Access VPN
Internet
Intranet VPN
Internet
Extranet VPN
Company 1
Company 2
Author: Bill Buchanan
Internet
Internet
Internet
Author: Bill Buchanan
Internet
VPN types
PPTP (Point-to-point Tunneling Protocol). Created by
Microsoft and is routable. It uses MPPE (Microsoft
Point-to-point Encryption) and user authentication.
L2TP (Layer 2 Tunneling Protocol). Works at Layer 2 to
Forward IP, IPX and AppleTalk (RFC2661). Cisco, Microsoft,
Ascent and 3Com developed it. User and machine authentication,
but no encryption (but can be used with L2TP over IPSec).
Author: Bill Buchanan
IPSec. An open standard. Includes both encryption and
Authentication.
Author: Bill Buchanan
Encryption. IPSec can support symmetric or asymmetric
encryption, but typically uses the method illustrated in Figure
6.11, where a shared key is used to encrypt the data, and the
public key is used to provide authentication. To generate the
secret keys it uses IKE (Internet Key Exchange - using DiffieHellman) which have a certain life time (such as 10 hours), after
which new keys are automatically created. Once the secret key
is created, the routers can then use an encryption method such
as DES, 3DES or AES to encryption the data packets.
Kpb1 Public key passed (Kpb1)
Kpv1
Kpb2
Public key passed (Kpb2)
Kpv2
Shared-key passed
(used to encrypt
all data and
authentication)
Hashed
value
Authentication
Encryption
Hashed
value
Author: Bill Buchanan
Encryption
IPSEC
Author: Bill Buchanan
Authentication. Once the secret key has been created
the public and private keys are used to authenticate
devices, where the hashed value is generated using either
MD5 or SHA, and is then encrypted using the private key
of the device. Only the device’s public key can be used to
decrypt it. The remote device will check it with its expected
hashed value, and if they are the same, the device which
sent the authentication has been authenticated.
IPSEC
IPSec protocol. The IPSec protocol is either ESP
(Encapsulated Security Protocol), or AH (Authentication
Header).
AH (Authentication Header). This adds an authentication
header, which defines data authentication and anti-reply.
This doesn’t actually encrypt the data.
Author: Bill Buchanan
ESP (Encapsulation Secure Payload). ESP takes the
original data packet, and breaks off the IP header. The
rest of the packet is encrypted, with the original header
added at the start, along with a new ESP field at the start,
and one at the end (Figure 8.1). It is important that the IP
header is not encrypted as the data packet must still be
read by routers as it travels over the Internet. Only the
host at the other end of the IPSec tunnel can decrypt the
contents of the IPSec data packet.
Internet
IP header
AH
header
Data
Data
IP header
ESP
header
Enc. Data
AH (Authentication Header).
This adds an authentication
header, which defines data
authentication and antireply. This doesn’t actually
encrypt the data.
ESP (Encapsulation Secure
Payload). ESP takes the
original data packet, and
breaks off the IP header.
The rest of the packet is
encrypted, with the original
header added at the start
Author: Bill Buchanan
Data
Internet
ESP encapsulated within
an AH.
Data
AH
header
ESP
header
Enc. Data
Author: Bill Buchanan
IP header
IPSEC
Author: Bill Buchanan
• Symmetric encryption. With this the two devices
get their shared key using IKE, and then use a
private key encryption method such as DES,
3DES or AES.
• Asymmetric encryption. With this the two
devices generate their own public and private
keys, and pass their public keys to each other,
which are then used to encrypt the data. Only the
private keys for the devices can decrypt the data.
The RSA encryption algorithm is a typical
asymmetric algorithm.
Author: Bill Buchanan
• IKE: Asymmetric public key to secure the
connection.
• Authentication: Asymmetric public key.
• Encryption: Single exchanged key. Symmetric
encryption algorithm.
Protocol numbers
PPTP uses GRE (Protocol number 47)
IPSec - ESP (Protocol number 50)
IPSec - AH (Protocol number 51).
Version
Version
TCP
TCP
Higher-level
Higher-levelprotocol/data
protocol/data
Header
Headerlength
length
Type
Typeof
ofservice
service
Total
Totallength
length
Identification
Identification
00 DD M
M
Time-to-Live
Time-to-Live
Fragment
FragmentOffset
Offset
Protocol
Protocol
Header
HeaderChecksum
Checksum
Source
SourceIP
IPAddress
Address
Destination
DestinationIP
IPAddress
Address
1 ICMP Internet Control Message [RFC792]
6 TCP Transmission Control [RFC793]
8 EGP Exterior Gateway Protocol [RFC888]
9 IGP any private interior gateway [IANA]
47 GRE General Routing Encapsulation
50 ESP Encap Security Payload [RFC2406]
51 AH Authentication Header [RFC2402]
55 MOBILE IP Mobility
88 EIGRP EIGRP [CISCO]
89 OSPFIGP OSPFIGP [RFC1583]
115 L2TP Layer Two Tunneling Protocol
Author: Bill Buchanan
IP
IP
Author: Bill Buchanan
IKE (Internet Key
Exchange)
Kpb1 Public key passed (Kpb1)
Kpv1
Kpb2
Public key passed (Kpb2)
Kpv2
Shared-key passed
(used to encrypt
all data and
authentication)
Hashed
value
Diffie-Hellman:
Group 1: 768-bit
Group 2: 1024-bit
- Suffers from MITM
Authentication
UDP port 500 is used for IKE
Encryption
Hashed
value
Author: Bill Buchanan
Encryption
Usage: isakmp policy <priority> authen <pre-share|rsa-sig>
Author: Bill Buchanan
Pre-shared keys. This uses pre-defined values for the
authentication.
RSA encrypted nonces. Peers encrypt with their private key and then
the other side decrypts with the public key of the sending peer.
RSA signatures. This uses asymetric public and private key pairs with
certificate authority (CA). Peers exchange their certificates,
and contact the a respected CA to validate them.
IKE phases
Author: Bill Buchanan
IKE Phase 1. Define the policies between the peers.
IKE Phase 2. Defines the policies for transform sets, peer IP
Addresses/hostnames and lifetime settings.
Policy priority
pixfirewall(config)# isakmp
Usage: isakmp policy <priority>
isakmp policy <priority>
isakmp policy <priority>
isakmp policy <priority>
isakmp policy <priority>
authen <pre-share|rsa-sig>
encrypt <aes|aes-192|aes-256|des|3des>
hash <md5|sha>
group <1|2|5>
lifetime <seconds>
Author: Bill Buchanan
When two peers connect, the lowest priority
is tried first, so the lowest is the most desired
IKE Phase 1
ISAKMP policy 5
Authentication:
Encryption:
Hashing:
Diffie-Hellman:
Lifetime:
Pre-shared key
Identity:
Key:
Peer:
172.16.0.1
172.16.0.2
192.168.0.1
Pre-share
DES
SHA
Group 1
86400 secs (1 day)
ISAKMP policy 5
Authentication:
Encryption:
Hashing:
Diffie-Hellman:
Lifetime:
Pre-share
DES
SHA
Group 1
86400 secs (1 day)
address
ABC&FDD
172.16.0.2
Pre-shared key
Identity:
Key:
Peer:
address
ABC&FDD
172.16.0.1
Author: Bill Buchanan
10.0.0.1
IKE Phase 1
10.0.0.1
ISAKMP policy 5
Authentication:
Encryption:
Hashing:
Diffie-Hellman:
Lifetime:
172.16.0.1
Pre-share
DES
SHA
Group 1
86400 secs (1 day)
192.168.0.1
172.16.0.2
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
sysopt
enable outside
key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
identity address
policy 5 authen pre-share
policy 5 encrypt des
policy 5 hash sha
policy 5 group 1
policy 5 lifetime 86400
connection permit-ipsec
ISAKMP policy 5
Authentication:
Pre-share
Encryption:
DES esp-des esp-sha-hmac
crypto
ipsec transform-set MYIPSECFORMAT
crypto map MYIPSEC 10 ipsec-isakmp
Hashing:111 permit ip 10.0.0.0
MD5
access-list
255.255.255.0 176.16.0.0
255.255.255.0
Diffie-Hellman:
Group
crypto
map MYIPSEC 10 match address
111 1
crypto map MYIPSEC 10 set peer 176.16.0.2
Lifetime:
86400MYIPSECFORMAT
secs (1 day)
crypto
map MYIPSEC 10 set transform-set
crypto map MYIPSEC interface outside
address
ABC&FDD
172.16.0.2
Pre-shared key
Identity:
Key:
Peer:
address
ABC&FDD
172.16.0.1
Author: Bill Buchanan
Pre-shared key
Identity:
Key:
Peer:
IKE Phase 2
10.0.0.1
Access list 111
Source:
Destination:
172.16.0.1
10.0.0.0/16
192.168.1.0/24
172.16.0.2
Access list 112
Source:
Destination:
192.168.0.1
192.168.1.0/24
10.0.0.0/16
Crypto IPSec assoc. security lifetime
900 seconds
Crypto map MYIPSEC:
Match:
ACL named 111
Peer:
172.16.0.2
SA lifetime:
900 sec
Transform set:
MYIPSECFORMAT
Author: Bill Buchanan
Crypto IPSec assoc. Transform set MYIPSECFORMAT
Transform 1: esp-des
Transform 2: esp-sha-hmac
Transform 3:
IKE Phase 2
10.0.0.1
Access list 111
Source:
Destination:
172.16.0.1
10.0.0.0/16
192.168.1.0/24
Crypto IPSec assoc. security lifetime
900 seconds
172.16.0.2
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
sysopt
192.168.0.1
enable outside
key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
identity address
policy 5 authen pre-share
policy 5 encrypt des
policy 5 hash sha
policy 5 group 1
policy 5 lifetime 86400
connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
Crypto map MYIPSEC:
Match:
ACL named 111
Peer:
172.16.0.2
SA lifetime:
900 sec
Transform set:
MYIPSECFORMAT
Author: Bill Buchanan
Crypto IPSec assoc. Transform set MYIPSECFORMAT
Transform 1: esp-des
Transform 2: esp-sha-hmac
Transform 3:
Configuring IKE
172.16.0.1
Enable IKE
Configure a preshared-key
Define ISAKMP
map
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
Author: Bill Buchanan
10.0.0.1
Author: Bill Buchanan
Security Association (SA)
Security Associations (SA)
• An SA is similar to a TCP session.
• When a connection is made for IPSec, an SA is created.
• The SA identifies each peer (with their IP address), the
security protocols used, and a security parameter index
(SPI).
show isakmp sa – show IKE security associations
show crypto sa – detailed information on crypto maps.
clear crypto isakmp – clear all the IKE security associations
clear crypto ipsec sa – clears all the IPSec security associations
Author: Bill Buchanan
An SA is created either by IKE (automatically) or can be
manual. The SA is not created until it is required (many
devices have a green light for an SA).
Stages
IKE Phase 1
IKE Policies
-Hashing algorithm (SHA/MD5)
-Encryption (DES/3DES)
-Diffie-Hellman agreements
-Authentication (pre-share, RSA nonces, RSA sig)
IKE Phase 2
Fairly fast mode
as a secure connection
has been made
Crypto ACL matches
Protect data
Author: Bill Buchanan
Crypto maps are exchanged
-AH, ESP (or both)
-Encryption (DES, 3DES)
-ESP (tunnel or transport)
-Authentication (SHA/MD5)
SA lifetimes defined
Author: Bill Buchanan
Configuring IKE
IKE Phase 1
Author: Bill Buchanan
IKE Policies
-Hashing algorithm (SHA/MD5)
-Encryption (DES/3DES)
-Diffie-Hellman agreements
-Authentication (pre-share, RSA nonces, RSA sig)
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
Author: Bill Buchanan
pixfirewall(config)# isakmp
Usage: isakmp policy <priority> authen <pre-share|rsa-sig>
isakmp policy <priority> encrypt <aes|aes-192|aes-256|des|3des>
isakmp policy <priority> hash <md5|sha>
isakmp policy <priority> group <1|2|5>
isakmp policy <priority> lifetime <seconds>
isakmp key <key-string> address <ip> [netmask <mask>] [no-xauth]
config-mode]
isakmp enable <if_name>
isakmp identity <address|hostname|key-id> [<key-id-string>]
isakmp keepalive <seconds> [<retry seconds>]
isakmp nat-traversal [<natkeepalive>]
isakmp client configuration address-pool local <poolname> [<pif_n
isakmp peer fqdn|ip <fqdn|ip> [no-xauth] [no-config-mode]
1. Enable IPSec
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
Apply to IKE to an Interface. Initially IKE is enabled on an interface (such
as on the outside interface):
isakmp enable outside
Author: Bill Buchanan
usage: isakmp enable <if_name>
2. Define pre-shared key
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
isakmp key <key-string> address <ip> [netmask <mask>] [no-xauth]
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
Author: Bill Buchanan
Define Shared Key for Diffie-Hellman. Next the Diffie-Hellman process
requires a key-string, such as ABC&FDD, which will be used with a peer at
the address of 176.16.0.2 (which has a subnet mask of 255.255.255.255 so
that it is only one host):
3. Define identity
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
Define Host/Address. If RSA encryption is being used for the public-key
encryption, the hostname, or its IP address can be used to generate the key
for RSA encryption. Otherwise with pre-share the identity is used to identify
the peer. This is achieved using an address with:
isakmp identity address
Address is normally used, but Hostname is used where the IP address changes
often.
Author: Bill Buchanan
isakmp identity <address|hostname|key-id> [<key-id-string>]
4. Define Authentication type
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
isakmp policy <priority> authen <pre-share|rsa-sig>
isakmp policy 5 authen pre-share
Author: Bill Buchanan
Define Policy Number. Each IKE has a policy number, where a 1 is the
highest priority. Thus a higher value is typically used so that higher priorities
can inserted at a future time. The following defines a policy number of 5 and
that a pre-shared key is used (otherwise rsa-sig can be defined):
5. Define encryption type
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
isakmp policy <priority> encrypt <aes|aes-192|aes-256|des|3des>
isakmp policy 5 encrypt des
Author: Bill Buchanan
Define Encryption Type. Then the encryption type can be defined, such as
for the DES encryption algorithm (others include aes, aes-192, aes-256,
and 3des):
6. Define hashing function
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
Define Hashing Function. Next the hashing technique needs to be
defined, as this will be used in the authentication process. The method
methods are MD5 and SHA. As SHA has a larger hash code, and thus has
less chance of creating the same signature for different unhashed values, it
is typically used for enhanced security. Thus to define SHA:
isakmp policy <priority> hash <md5|sha>
isakmp policy 5 hash sha
Author: Bill Buchanan
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
7. Define Diffie-Hellman type
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
Define Diffie-Hellman Type. Next the Diffie-Hellman method type is
defined. For 768-bit Diffie-Hellman a Group 1 is used, while 1024-bit DiffieHellman uses Group 2, and 1582-bit Diffie-Hellman uses Group 5. Thus to
setup Group 1 settings:
isakmp policy <priority> group <1|2|5>
isakmp policy 5 group 1
Author: Bill Buchanan
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
8. Define lease time
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
isakmp policy <priority> lifetime <seconds>
isakmp policy 5 lifetime 86400
Author: Bill Buchanan
Define Lease Time. Finally the default lifetime is defined in terms of
seconds. Thus to setup a period of 1 day (86,400 seconds) the following
can be defined:
Allow IPSec to flow
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 176.16.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
sysopt connection { permit-ipsec | permit-l2tp | permit-pptp | timewait |
{tcpmss [minimum] <bytes>} }
sysopt connection permit-ipsec
Author: Bill Buchanan
Once the IKE is setup, the IPSec parameters can be defined. First we must
allow the IPsec packets to pass through the PIX. Normally these would be
interrupted by ACLs, which must be bypassed. This includes protocols: 50
(ESP), 51 (AH) and 500 (IKE). To do this the following is used:
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
Usage: [ show ] crypto { ca | dynamic-map | ipsec | isakmp |
map | sa } ...
show crypto engine [verify]
[ show | clear ] crypto interface [counters]
Author: Bill Buchanan
The crypto command is then used to define the encryption used, and define
a mapping. Its usage is:
IKE Phase 2
Author: Bill Buchanan
Crypto maps are exchanged
-AH, ESP (or both)
-Encryption (DES, 3DES)
-ESP (tunnel or transport)
-Authentication (SHA/MD5)
SA lifetimes defined
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
usage: crypto ipsec transform-set <trans-name> [ ah-md5-hmac|ah-sha-hmac ]
[ esp-aes|esp-aes-192|esp-aes-256|esp-des|esp-3des|esp-null ]
[ esp-md5-hmac|esp-sha-hmac ]
crypto ipsec transform-set <trans-name> mode transport
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
Author: Bill Buchanan
Is it AH, ESP or both?
The first configuration defines the security protocol defined between the
peers. The following defines a transform set named MYIPSECFORMAT
which uses DES for encapsulating security payload (ESP) and SHA for the
authentication:
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
usage: crypto map <map-name> { (interface <if-name>)) |
(client configuration address initiate|respond) |
(<seqno> ipsec-manual|ipsec-isakmp|match|set ...)}
crypto map MYIPSEC 10 ipsec-isakmp
Author: Bill Buchanan
Define Crypto Map. Next a crypto map can be defined, where MYIPSEC
defines the name associated with the map and 10 is a sequence number.
These sequence numbers allow different crypto combinations to be set for
different peers which make connections on the interface that has the crypto
map applied. There can only be crypto map on each interface, thus
sequence number blocks can apply different policies to a specific crypto
map:
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
access-list 111 permit ip 10.0.0.0
255.255.255.0
255.255.255.0
All other traffic is allow to pass, but not through the tunnel.
176.16.0.0
Author: Bill Buchanan
Define Access Control List. Next the access control list (number 111) can
be defined to specify the traffic which will be encrypted. In the following
traffic from 10.0.0.0/24 to 176.16.0.0/24 will be encrypted.
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
usage: crypto map <map-name> { (interface <if-name>)) |
(client configuration address initiate|respond) |
(<seqno> ipsec-manual|ipsec-isakmp|match|set ...)}
crypto map MYIPSEC 10 match address 111
Author: Bill Buchanan
Associate Access Control List. After this, an access list number can be
defined (in this case it is 111), where anything matching this list will either
be encrypted (for outgoing data) or decrypted (for incoming data) as defined
by the crypto map block (which is sequence number 10). Thus we can have
different security settings depending on the sequence number:
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 192.168.0.0
255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
usage: crypto map <map-name> { (interface <if-name>)) |
(client configuration address initiate|respond) |
(<seqno> ipsec-manual|ipsec-isakmp|match|set ...)}
crypto map MYIPSEC 10 set peer 176.16.0.2
Author: Bill Buchanan
Define Peer for Crypto List. Next the peer which is associated with the
crypto map security policy defined:
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
usage: crypto map <map-name> { (interface <if-name>)) |
(client configuration address initiate|respond) |
(<seqno> ipsec-manual|ipsec-isakmp|match|set ...)}
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
Author: Bill Buchanan
Define Peer for Crypto List. Next the type of hashing and/or encoding is
defined using the transform mapping:
10.0.0.1
172.16.0.1
172.16.0.2
192.168.0.1
isakmp enable outside
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 5 authen pre-share
isakmp policy 5 encrypt des
isakmp policy 5 hash sha
isakmp policy 5 group 1
isakmp policy 5 lifetime 86400
sysopt connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
usage: crypto map <map-name> { (interface <if-name>)) |
(client configuration address initiate|respond) |
(<seqno> ipsec-manual|ipsec-isakmp|match|set ...)}
crypto map MYIPSEC interface outside
Author: Bill Buchanan
Apply on an Interface. Next the crypto map can be applied onto an
interface (only one is allowed on each interface):
Tunnel
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
sysopt
172.16.0.1
enable outside
key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
identity address
policy 5 authen pre-share
policy 5 encrypt des
policy 5 hash sha
policy 5 group 1
policy 5 lifetime 86400
connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0 192.168.0.0
255.255.255.0 crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
172.16.0.2
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
sysopt
192.168.0.1
enable outside
key ABC&FDD address 176.16.0.1 netmask 255.255.255.255
identity address
policy 5 authen pre-share
policy 5 encrypt des
policy 5 hash sha
policy 5 group 1
policy 5 lifetime 86400
connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 192.168.0.0 255.255.255.0
10.0.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.1
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
Author: Bill Buchanan
10.0.0.1
Tunnel
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
isakmp
sysopt
172.16.0.1
enable outside
key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
identity address
policy 5 authen pre-share
policy 5 encrypt des
policy 5 hash sha
policy 5 group 1
policy 5 lifetime 86400
connection permit-ipsec
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
crypto map MYIPSEC 10 ipsec-isakmp
access-list 111 permit ip 10.0.0.0 255.255.255.0
192.168.0.0 255.255.255.0
crypto map MYIPSEC 10 match address 111
crypto map MYIPSEC 10 set peer 176.16.0.2
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
crypto map MYIPSEC interface outside
172.16.0.2
192.168.0.1
crypto isakmp policy 1
hash sha
authentication pre-share
group 1
lifetime 86400
encryption des
crypto isakmp key ABC&FDD address 172.16.0.1
crypto ipsec transform-set rtpset esp-des esp-md5-hmac
Crypto identity address
crypto map mymap 1 ipsec-isakmp
set peer 172.16.0.1
set transform-set rtpset
match address 115
interface FastEthernet0/0
ip address 172.16.0.2 255.255.255.0
crypto map mymap
access-list 115 permit ip 192.168.0.0 0.0.0.255 10.0.0.0
0.0.0.255
Author: Bill Buchanan
10.0.0.1