WMS07 - Hyper-V Security and
Best Practices
Dan Stolts
Microsoft
http://blogs.technet.com/danstolts
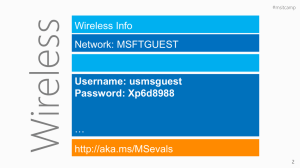
Announcing…
http://www.microsoft.com/MAP
https://connect.microsoft.com/InvitationUse.aspx?ProgramID=2307&InvitationID=MP31GT76-X98X&SiteID=297
MAP: User Interface & Reports
Server Migration & Virtualization Candidates
Windows Server
2008
New User
Interface
Virtualization
Windows Vista
•Speed up Planning with Actionable Proposals and Assessments
•Collect Inventory of Servers, Desktops and Applications
Agentlessly
•Offers Recommendations for Server/Application Virtualization
•Works with the Virtualization ROI Tool to generate ROI calculations
GET BETA
CLICK HERE
Agenda
•
•
•
•
•
•
Virtualization Requirements
Hyper-V Security
Microsoft Secure Development Lifecycle
Server Core
Enabling Hyper-V with Server Core
Designing a Windows Server 2008 Hyper V &
System Center Infrastructure
• Hyper-V Storage & Pass Through Disks
• Deployment Considerations
• Best Practices & Tips and Tricks
Virtualization Requirements
•
•
•
•
•
•
•
•
•
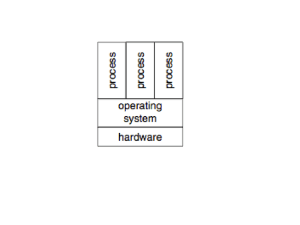
Scheduler
Memory Management
VM State Machine
Virtualized Devices
Storage Stack
Network Stack
Ring Compression (optional)
Drivers
Management API
Old: Virtual Server Architecture
Host
Virtual Server
WebApp
IIS
Guests
Windows
Ring 3: User Mode
Virtual Server
Service
Virtual Server
Guest Applications
ISV
Ring 1: Guest Kernel Mode
VM Additions
Windows (NT4, 2000, 2003)
Windows Server 2003/Windows XP
Kernel
Provided by:
Device
Drivers
Ring 0: Kernel Mode
VMM Kernel
Server Hardware
New: Hyper-V Architecture
Parent Partition
Child Partition
Rest of
Windows
Virtualization Stack
WMI Provider
VM
Service
Server Core
Windows
Kernel
Provided by:
Guest Applications
VM Worker
Processes
ISV
Ring 3: User Mode
Virtualization
Service
Device Providers
(VSPs)
Drivers
Hyper-V
Virtualization
Service
Clients
(VSCs)
VMBus
Ring 0: Kernel Mode
Windows hypervisor
Server Hardware
OS
Kernel
Enlightenments
Virtualization Attacks
Parent Partition
Child Partition
Rest of
Windows
Virtualization Stack
WMI Provider
VM
Service
Server Core
Windows
Kernel
Provided by:
Guest Applications
VM Worker
Processes
ISV
Ring 3: User Mode
Virtualization
Service
Device Providers
(VSPs)
Drivers
Hyper-V
Virtualization
Service
Clients
(VSCs)
VMBus
VMBus
Ring 0: Kernel Mode
Windows hypervisor
Server Hardware
Hackers
OS
Kernel
Enlightenments
Why not get rid of the parent?
• No defense in depth
• Entire hypervisor running in the most privileged mode of the system
Virtual
Machine
Virtual
Machine
Virtual
Machine
User
Mode
User
Mode
User
Mode
Kernel
Mode
Kernel
Mode
Kernel
Mode
•Scheduler
•Memory Management
•Storage Stack
•Network Stack
•VM State Machine
•Virtualized Devices
•Drivers
•Management API
Hardware
Ring 3
Ring 0
Ring -1
Micro-kernelized Hypervisor
• Defense in depth
• Using hardware to protect
• Hyper-V doesn’t use ring compression translation
●
Further reduces the attack surface
Parent Partition
Virtual
Machine
Virtual
Machine
VM State Machine
Virtualized Devices
Management API
User
Mode
User
Mode
Storage Stack
Network Stack
Drivers
Kernel
Mode
Kernel
Mode
Scheduler
Memory Management
Hardware
Ring 3
Ring 0
Ring -1
Hyper-V Security
Security Assumptions
•
•
Guests are untrusted
Trust relationships
●
●
•
•
•
•
Code in guests can run in all
available processor modes,
rings, and segments
Hypercall interface will be well
documented and widely available
to attackers
All hypercalls can be attempted
by guests
Can detect you are running on a
hypervisor
●
•
Parent must be trusted by
hypervisor
Parent must be trusted by children
We’ll even give you the version
The internal design of the
hypervisor will be well
understood
Security Goals
• Strong isolation between
partitions
• Protect confidentiality and
integrity of guest data
• Separation
• Unique hypervisor resource pools
per guest
• Separate worker processes per
guest
• Guest-to-parent communications
over unique channels
• Non-interference
• Guests cannot affect the contents
of other guests, parent, hypervisor
• Guest computations protected from
other guests
• Guest-to-guest communications not
allowed through VM interfaces
Isolation
• We’re serious folks
●
●
●
No sharing of virtualized
devices
Separate VMBus per vm to
the parent
No sharing of memory
• Each has its own address
space
●
●
●
●
VMs cannot communicate
with each other, except
through traditional networking
Guests can’t perform DMA
attacks because they’re
never mapped to physical
devices
Guests cannot write to the
hypervisor
Parent partition cannot write
to the hypervisor
Microsoft Secure Development
Lifecycle
Hyper-V & SDL
• Hypervisor built with
●
●
●
Stack guard cookies (/GS)
Address Space Layout
Randomization (ASLR)
Hardware Data Execution
Prevention
• No Execute (NX) AMD
• Execute Disable (XD) Intel
●
●
●
Code pages marked read
only
Memory guard pages
Hypervisor binary is signed
• Hypervisor and Parent going
through SDL
●
●
●
Threat modeling
Static Analysis
Fuzz testing & Penetration
testing
Hyper-V Security Model
• Uses Authorization Manager
(AzMan)
●
●
●
Fine grained authorization and
access control
Department and role based
Segregate who can manage
groups of VMs
• Define specific functions for
individuals or roles
●
Start, stop, create, add
hardware, change drive image
• VM administrators don’t have to
be Server 2008 administrators
• Guest resources are controlled
by per VM configuration files
• Shared resources are protected
●
●
Read-only (CD ISO file)
Copy on write (differencing disks)
Server Core
Windows Server Core
• Windows Server frequently deployed for a single
role
●
Must deploy and service the entire OS in earlier
Windows Server releases
• Server Core a new minimal installation option
●
●
Provides essential server functionality
Command Line Interface only, no GUI Shell
• Benefits
●
●
●
●
Fundamentally improves availability
Less code results in fewer patches and reduced
servicing burden
Low surface area server for targeted roles
More secure and reliable with less management
Windows Server Core
Enabling Hyper-V with Server Core
Step-by-step instructions…
Installing Hyper-V Role on Core
Install Windows Server 2008 and select a Server Core
installation option
Set Admin Password
●
●
net user administrator <new_password>
shutdown /r /t 0
Rename Computer
●
●
netdom renamecomputer %computername%
/newname:<new_computername>
shutdown /r /t 0
Join Domain
●
●
●
netdom join %computername% /domain:<domain>
/userd:<username> /passwordd:*
enter password when prompted
shutdown /r /t 0
Add domain account to local
admin group
●
●
net localgroup administrators /add <domain_account>
logoff
Add Hyper-V Role
●
●
ocsetup Microsoft-Hyper-V
Restart when prompted
Connect remotely via MMC
Enabling Remote Desktop
• OPTIONAL
● cscript \windows\system32\scregedit.wsf /ar 0
● cscript \windows\system32\scregedit.wsf /cs 0
Hyper-V Networking
Hyper-V Networking
• Don’t forget the parent
is a VM
• Two physical network
adapters at minimum
●
●
●
●
One for management
One (or more) for VM
networking
Dedicated NIC(s) for
iSCSI
Connect parent to
back-end management
network
• Only expose guests to
internet traffic
Hyper-V Network Configurations
• Example 1:
●
●
●
●
Physical Server has 4 network adapters
NIC 1: Assigned to parent partition for
management
NICs 2/3/4: Assigned to virtual switches for
virtual machine networking
Storage is non-iSCSI such as:
• Direct attach
• SAS or Fibre Channel
Hyper-V Setup & Networking 1
Hyper-V Setup & Networking 2
Hyper-V Setup & Networking 3
Parent
Partition
Child Partitions
VM Worker
Processes
Applications
Applications
Applications
VM 1
VM 2
VM 3
WMI Provider
VM Service
Windows
Server 2008
Windows
Kernel
VSP
VS
VSC
Windows
Kernel
VSC
Linux
Kernel
VSC
VS
P
P
VMBus
VMBus
VMBus
Windows hypervisor
Mgmt
NIC 1
VSwitch 1
NIC 2
VSwitch 2
NIC 3
VSwitch 3
NIC 4
“Designed for Windows” Server Hardware
User
Mode
VMBus
Kernel
Mode
Ring -1
Hyper-V Network Configurations
• Example 2:
●
●
●
●
Server has 4 physical network adapters
NIC 1: Assigned to parent partition for
management
NIC 2: Assigned to parent partition for iSCSI
NICs 3/4: Assigned to virtual switches for
virtual machine networking
Hyper-V Setup, Networking &
iSCSI
Parent
Partition
Child Partitions
VM Worker
Processes
Applications
Applications
Applications
VM 1
VM 2
VM 3
WMI Provider
VM Service
Windows
Server 2008
Windows
Kernel
VSC
Windows
Kernel
VSC
Linux
Kernel
User
Mode
VSC
VSP
VS
P
VMBus
VMBus
VMBus
Windows hypervisor
Mgmt
NIC 1
iSCSI NIC
2
VSwitch 1
NIC 3
VSwitch 2
NIC 4
“Designed for Windows” Server Hardware
VMBus
Kernel
Mode
Ring -1
Networking: Parent Partition
Networking: Virtual Switches
Legacy vs. Synthetic NIC
• Legacy Network Adapter
●
●
●
Up to 4 per virtual machine
Pros: Needed for PXE/RIS/WDS installation
Cons: Slow
• Synthetic Network Adapter
●
●
Up to 8 per virtual machine!
Pros: Blazing fast
• Both:
●
●
Support VLANs
Dynamic or Static MAC addresses
VM with Legacy & Synthetic NIC
Hyper-V Storage & Pass
Through…
Step by Step Instructions
Hyper-V Storage...
• Performance wise from fastest to slowest…
●
Fixed Disk VHDs/Pass Through Disks
• About the same in terms of performance
●
Dynamically Expanding VHDs
• Grow as needed
• Pass Through Disks
●
●
Pro: VM writes directly to a disk/LUN without
encapsulation in a VHD
Cons:
• You can’t use VM snapshots
• Dedicating a disk to a vm
VM Setting No Pass Through
Computer Management: Disk
Taking a disk offline
Disk is offline…
Pass Through Configured
Best Practices & Tips and Tricks
Deployment Considerations
• Minimize risk to the Parent Partition
●
●
Use Server Core
Don’t run arbitrary apps, no web surfing
• Run your apps and services in guests
• Moving VMs from Virtual Server to Hyper-V
●
FIRST: Uninstall the VM Additions
• Two physical network adapters at minimum
●
●
●
●
One for management (use a VLAN too)
One (or more) for vm networking
Dedicated NIC(s) for iSCSI
Connect parent to back-end management network
• Only expose guests to internet traffic
Windows Server 2003 (today)
Cluster Creation
Cluster Hyper-V Servers
Don't forget the ICs!
Emulated vs. VSC
Anti-Virus & BitLocker…
• Parent partition
●
Run AV software and exclude .vhd
• Child partitions
●
Run AV software within each VM
• BitLocker
●
●
Great for branch office
Protects data while a system is offline
Bitlocker – Persistent Protection
Mitigating Against External Threats…
Very Real Threat of Data Theft When a System is Stolen, Lost,
or Otherwise Compromised (Hacker Tools Exist!)
Decommissioned Systems are not Guaranteed Clean
Increasing Regulatory Compliance on Storage Devices Drives Safeguards
(HIPPA, SBA, PIPEDA, GLBA, etc…)
BitLocker Drive Encryption Support in Windows Server 2008
Addresses Leading External Threats by Combining Drive Level Encryption
with Boot Process Integrity Validation
Leverages Trusted Platform Model (TPM) Technology (Hardware Module)
Integrates with Enterprise Ecosystem Maintaining Keys in Active Directory
Protects Data While a System is Offline
Entire Windows Volume is Encrypted (Hibernation and Page Files)
Delivers Umbrella Protection to Applications (On Encrypted Volume)
Ensures Boot Process Integrity
Protects Against Root Kits – Boot Sector Viruses
Automatically Locks System when Tampering Occurs
Simplifies Equipment Recycling
One Step Data Wipe – Deleting Access Keys Renders Disk Drive Useless
More…
• Mitigate Bottlenecks
●
●
●
Processors
Memory
Storage
• Don't run everything off a single spindle…
●
Networking
• VHD Compaction/Expansion
●
Run it on a non-production system
• Use .isos
●
●
●
●
Great performance
Can be mounted and unmounted remotely
Physical DVD can’t be shared across multiple vms
Having them in SCVMM Library fast & convenient
Creating Virtual Machines
• Use SCVMM Library
• Steps:
1.
2.
3.
4.
5.
6.
7.
Create virtual machine
Install guest operating system & latest SP
Install integration components
Install anti-virus
Install management agents
SYSPREP
Add it to the VMM Library
• Windows Server 2003
●
Create vms using 2-way to ensure an MP HAL
Online Resources
•
Microsoft Virtualization Home:
http://www.microsoft.com/virtualization
•
Windows Server Virtualization Blog Site:
http://blogs.technet.com/virtualization/default.aspx
•
Windows Server Virtualization TechNet Site:
http://technet2.microsoft.com/windowsserver2008/en/servermanager/virtualization.ms
px
•
Windows Server 2008 with Hyper-V RC1:
●
http://www.microsoft.com/downloads/details.aspx?FamilyId=7EDAA89F-9F64488D-93C0-858D2D8799DF&displaylang=en
•
Windows Hyper-V Installation Guide:
●
http://www.microsoft.com/windowsserver2008/virtualization/install.mspx
© 2008 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries.
The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market
conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation.
MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
Your Feedback is Important
Please fill out a session evaluation form and either put them in the basket
near the exit or drop them off at the conference registration desk.
Thank you!
WMS07 - Hyper-V Security and Best
Practices
Dan Stolts
Microsoft
http://blogs.technet.com/DanStolts