Networking Admin
1 to 4 lectures a week for 11 weeks for a
total of 23 lectures
Interleaves with Functional Programming
First prac this week (THU 17): then every
second teaching week (5 pracs in total)
Introduction
1-1
Practicals with a difference
Two weeks to ‘execute them’
Self assessment
They will be as last year, so you will be able
to have the solutions ahead of handing in,
if you like responsibility
Well, PERSONAL RESPONSIBILITY
should be the keyword of your relation
with this course
It worked reasonably well last year and the
year before
Introduction
1-2
The course is entirely based on
a book (a very good one!)
First 5 chapters (about 500 pages)
Of course, some material will be left out:
altogether about 260 pages
Still, 10 to 20 pages to read per lecture
(depending on difficulty)
Book must be read BEFORE practicals,
though might be understood for real just
after ending prac
Introduction
1-3
The book again…
Important: references in the book. Get
used to that and use them (within reason)
Another important resource, of course: the
internet
(for example wikipedia and from there to ‘core’ documents,
up to RFCs; www.networksorcery.com is a very useful
resource for protocols)
Introduction
1-4
So why having lectures?
Actually not too sure: tradition? Lack of
inventiveness? Because life has to be hard,
as parents / teachers kept telling you? ;-)
Lectures to get your interest going, or to
clarify general / difficult concepts
To ease the difficulty of self learning
(which remains the best way to learn,
however)
As interactive as possible, please (like,
don’t fall asleep…)
Introduction
1-5
The book (and a lot of
material!)
A note on the use of these ppt slides:
We’re making these slides freely available to all (faculty, students, readers).
They’re in PowerPoint form so you can add, modify, and delete slides
(including this one) and slide content to suit your needs. They obviously
represent a lot of work on our part. In return for use, we only ask the
following:
If you use these slides (e.g., in a class) in substantially unaltered form,
that you mention their source (after all, we’d like people to use our book!)
If you post any slides in substantially unaltered form on a www site, that
you note that they are adapted from (or perhaps identical to) our slides, and
note our copyright of this material.
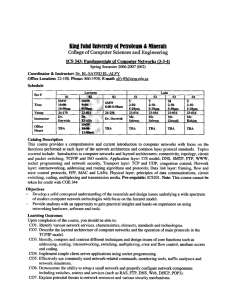
Computer Networking:
A Top Down Approach ,
4th edition.
Jim Kurose, Keith Ross
Addison-Wesley, July
2007.
Thanks and enjoy! JFK/KWR
All material copyright 1996-2007
J.F Kurose and K.W. Ross, All Rights Reserved
Introduction
1-6
Chapter 1: Introduction
Our goal:
get “feel” and
terminology
more depth, detail
later in course
approach:
use Internet as
example
Overview:
what’s the Internet?
what’s a protocol?
network edge; hosts, access
net, physical media
network core: packet/circuit
switching, Internet structure
performance: loss, delay,
throughput
security
protocol layers, service models
history
Introduction
1-7
Chapter 1: roadmap
1.1 What is the Internet?
1.2 Network edge
end systems, access networks, links
1.3 Network core
circuit switching, packet switching, network structure
1.4 Delay, loss and throughput in packet-switched
networks
1.5 Protocol layers, service models
1.6 Networks under attack: security
1.7 History
Introduction
1-8
What’s the Internet: “nuts and bolts” view
PC
millions of connected
computing devices:
hosts = end systems
wireless
laptop
running network
cellular
handheld
apps
communication links
fiber, copper,
access
points
radio, satellite
wired
links
transmission
rate = bandwidth
routers: forward
router
packets (chunks of
data)
Mobile network
server
Global ISP
Home network
Regional ISP
Institutional network
Introduction
1-9
“Cool” internet appliances
Web-enabled toaster +
weather forecaster
IP picture frame
http://www.ceiva.com/
World’s smallest web server
http://www-ccs.cs.umass.edu/~shri/iPic.html
Internet phones
Introduction
1-10
What’s the Internet: “nuts and bolts” view
protocols control sending,
Mobile network
receiving of msgs
e.g., TCP, IP, HTTP, Skype,
Ethernet
Internet: “network of
networks”
loosely hierarchical
public Internet versus
private intranet
Global ISP
Home network
Regional ISP
Institutional network
Internet standards
RFC: Request for comments
IETF: Internet Engineering
Task Force
Introduction
1-11
What’s the Internet: a service view
communication
infrastructure enables
distributed applications:
Web, VoIP, email, games,
e-commerce, file sharing
communication services
provided to apps:
reliable data delivery
from source to
destination
“best effort” (unreliable)
data delivery
Introduction
1-12
What’s a protocol?
human protocols:
“what’s the time?”
“I have a question”
introductions
… specific msgs sent
… specific actions taken
when msgs received,
or other events
network protocols:
machines rather than
humans
all communication
activity in Internet
governed by protocols
protocols define format,
order of msgs sent and
received among network
entities, and actions
taken on msg
transmission, receipt
Introduction
1-13
What’s a protocol?
a human protocol and a computer network protocol:
Hi
TCP connection
request
Hi
TCP connection
response
Got the
time?
Get http://www.awl.com/kurose-ross
2:00
<file>
time
Q: Other human protocols?
Introduction
1-14
Chapter 1: roadmap
1.1 What is the Internet?
1.2 Network edge
end systems, access networks, links
1.3 Network core
circuit switching, packet switching, network structure
1.4 Delay, loss and throughput in packet-switched
networks
1.5 Protocol layers, service models
1.6 Networks under attack: security
1.7 History
Introduction
1-15
A closer look at network structure:
network edge:
applications and
hosts
access networks,
physical media:
wired, wireless
communication links
network core:
interconnected
routers
network of
networks
Introduction
1-16
The network edge:
end systems (hosts):
run application programs
e.g. Web, email
at “edge of network”
peer-peer
client/server model
client host requests, receives
service from always-on server
client/server
e.g. Web browser/server;
email client/server
peer-peer model:
minimal (or no) use of
dedicated servers
e.g. Skype, BitTorrent
Introduction
1-17