Word Format - WACE 2015 2016
advertisement
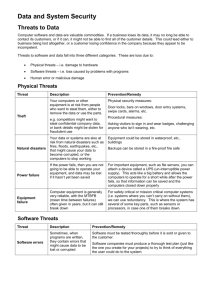
APPLIED INFORMATION TECHNOLOGY FOUNDATION COURSE Marking key for the Externally set task Sample 2016 Copyright © School Curriculum and Standards Authority, 2014 This document – apart from any third party copyright material contained in it – may be freely copied, or communicated on an intranet, for non-commercial purposes in educational institutions, provided that the School Curriculum and Standards Authority is acknowledged as the copyright owner, and that the Authority’s moral rights are not infringed. Copying or communication for any other purpose can be done only within the terms of the Copyright Act 1968 or with prior written permission of the School Curriculum and Standards Authority. Copying or communication of any third party copyright material can be done only within the terms of the Copyright Act 1968 or with permission of the copyright owners. Any content in this document that has been derived from the Australian Curriculum may be used under the terms of the Creative Commons Attribution-NonCommercial 3.0 Australia licence Disclaimer Any resources such as texts, websites and so on that may be referred to in this document are provided as examples of resources that teachers can use to support their learning programs. Their inclusion does not imply that they are mandatory or that they are the only resources relevant to the course. 2014/10310 1 Applied Information Technology Externally set task – marking key 1. Classify each of the hardware components of the advertised computer system as a type of hardware device. (12 marks) Note: Some of the hardware components may be used in more than one classification. Description Lists valid hardware components Hardware components Input dual-layer DVD burner drive * multimedia keyboard optical scroll mouse 5 x USB2 ports * Processing Intel Pentium G2020 Dual –Core processor Output 18.5” LCD widescreen monitor dual-layer DVD burner drive * stereo sound and speakers 5 x USB2 ports * Storage 6GB DDR3 RAM 500GB SATA hard disk drive Communication 10/100 ethernet LAN Note: components shown with an asterisk (*) are shown as an output and input device Total Marks 4 1 4 2 1 12 Applied Information Technology | Foundation | Externally set task| Marking key | Sample 2016 2 2. When using a computer system, it is recommended that you regularly backup important data. Describe two (2) backup strategies that can be used and, for each, a device that can be used. Description Provides a detailed description of two different backup strategies to do a backup and the device that could be used for the backup. Provides a limited description of two different hardware strategies to do a backup and the device that could be used for the backup. Lists two hardware different hardware devices to do a backup Total Answer could include, but is not limited to: Types of backup strategies local remote Hardware devices local external hard disk drive (large volume of data) flash drive (small volume of data) remote online storage (for example, Google drive - small volume of data). 3. Marks 5–6 3–4 1–2 6 Describe two (2) methods of physically caring for a computer system. Description Provides two methods and a detailed description of each method for physically caring for the computer system Provides a two methods and limited description of each method for physically caring for the computer system Lists 1 or 2 different methods of physically caring for the computer system Total Answer could include, but is not limited to: Methods of physically caring for the computer system provide adequate ventilation don’t place near or use liquids near the computer system reduce dust levels by using air-conditioning reduce the level of static by using anti-static mats. Applied Information Technology | Foundation | Externally set task | Marking key | Sample 2016 Marks 3–4 1–2 1–2 4 3 4. A computer system should be protected from a range of external threats. List two (2) external threats to a computer system and, for each, describe one (1) strategy that could reduce the external threat to a computer system. Description Marks Lists two external threats and describes in detail one strategy to reduce each 5–6 threat Lists two external threats and briefly describes one strategy to reduce each 3–4 threat Lists one or two external threats, with a limited or incorrect description of the 1–2 strategy to reduce each threat (or provides no description) Total 6 Answer could include, but is not limited to: External threats to a computer system Threat 1: viruses strategy: use anti-virus software to prevent, detect and remove computer viruses. Anti-virus software is installed on a computer system. Virus protection can be provided as an external service, usually linked to an email service. The software is used to conduct real-time checks of incoming email and internet usage, or used on a time interval. threat 2: remote access and control strategy: use of a firewall to prevents programs and processes from gaining access via a network or internet link to a computer system. A firewall will only prevent access to a computer system. 5. List four (4) types of application software that you could install on this computer system for personal use. For each type of software: provide an example describe one (1) personal use for this software. Description Lists four types of application software Marks 1–4 (1 per application) 1–4 (1 per example) Provides an appropriate example of each type of application software listed Describes an appropriate personal use for each type of software listed clear description (2 marks) limited description (1 mark) 1–8 (2 per use) Total 16 Answer could include, but is not limited to: Types of application software and examples: word processing: Microsoft Word spreadsheet: Microsoft Excel presentation: Microsoft PowerPoint desktop publishing: Microsoft Publisher database: Microsoft Access graphics capture/edit: Adobe Photoshop video capture/edit: Adobe Premiere communications (including email and browsers): Internet Explorer games: examples will vary. Applied Information Technology | Foundation | Externally set task| Marking key | Sample 2016