incident-mgmt
advertisement

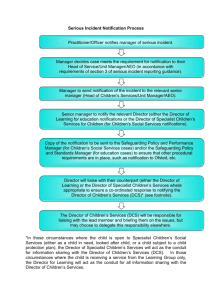
Information Security Incident Management Process A. Kostina, N. Miloslavskaya, and A. Tolstoy, Proceedings of the 2nd International Conference on Security of Information and Networks, 93-97, 2009 Presented by Anh Nguyen February 15, 2010 Organization • Introduction • International Documents Regulating IS Incidents and Management • IS Event and IS Incident • Approach to ISIMP Development • VEI Detection and Notification Joint Process • Conclusions 2 Organization • Introduction • International Documents Regulating IS Incidents and Management • IS Event and IS Incident • Approach to ISIMP Development • VEI Detection and Notification Joint Process • Conclusions 3 Introduction Why ISIMP? • Detect, report and assess IS incidents • Respond to IS incidents • Learn from IS incidents Introduction Why ISIMP? • One of the basic parts of ISMS • Data obtained from ISIMP can be used in other ISMS’ processes • Helps assess the overall level of organization’s IS Organization • Introduction • International Documents Regulating IS Incidents and Management • IS Event and IS Incident • Approach to ISIMP Development • VEI Detection and Notification Joint Process • Conclusions 6 International Documents Regulating IS Incidents and Management • The Standard ISO/IEC 27001 “Information technology – Security techniques – Information security management systems – Requirements” • NIST SP 800-61 <<Computer security incident handling guide>> • CMU/SEI-2004-TR-015 <<Defining incident management processes for CSIRT>> Organization • Introduction • International Documents Regulating IS Incidents and Management • IS Event and IS Incident • Approach to ISIMP Development • VEI Detection and Notification Joint Process • Conclusions 8 IS Event and IS Incident IS Event • IS Event – An identified occurrence of a system, service or network state indicating a possible breach of IS policy or failure of safeguards IS Event and IS Incident IS Event (Cont.) IS Event and IS Incident IS Incident • IS Incident – Is indicated by a single or a series of unwanted or unexpected IS events that have a significant probability of compromising business operations and threatening IS IS Event and IS Incident IS Incident (Cont.) Organization • Introduction • International Documents Regulating IS Incidents and Management • IS Event and IS Incident • Approach to ISIMP Development • VEI Detection and Notification Joint Process • Conclusions 13 Approach to ISIMP Development IS Incident Management Policy • The importance of IS incident management • IS events detection, alerts and notification about IS incidents procedures • Summary of activities following the confirmation that an IS event is an IS incident • Structure of IS incidents management • List of legal acts being used Approach to ISIMP Development IS Incidents Management Process • Vulnerabilities, IS events and incidents (VEI) detection • VEI notification • VEI messages processing • Reaction to IS incidents • IS incidents analysis • IS incidents investigation • ISIMP efficiency analysis Approach to ISIMP Development IS Incidents Management Process (Cont.) Organization • Introduction • International Documents Regulating IS Incidents and Management • IS Event and IS Incident • Approach to ISIMP Development • VEI Detection and Notification Joint Process • Conclusions 17 VEI Detection and Notification Joint Process VEI Detection and Notification Joint Process (Cont.) VEI Detection and Notification Joint Process (Cont.) VEI Detection and Notification Joint Process (Cont) VEI Detection and Notification Joint Process (Cont) VEI Detection and Notification Joint Process (Cont) VEI Detection and Notification Joint Process (Cont) VEI Detection and Notification Joint Process (Cont) VEI Detection and Notification Joint Process (Cont) Organization • Introduction • International Documents Regulating IS Incidents and Management • IS Event and IS Incident • Approach to ISIMP Development • VEI Detection and Notification Joint Process • Conclusions 27 Conclusions • Thank you for your time • Questions and feedback are welcome 28