E-security - Common flaws - Loud-Fat
advertisement

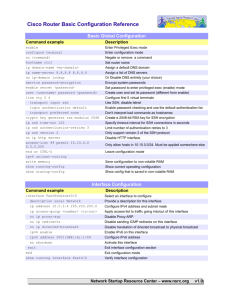
KBOM Aim Develop a series of Success Factors for infrastructure security Demonstrate the Success Factors in a Physical security analogy Extend the analogy to the Digital world Describe typical faults in infrastructure security Good Security Security Success Factors Multiple layers of protection - Defence in-depth - No direct access to customer data Utilises multiple technologies including - Access control - Breach detection - Auditing or recording key events Should integrate Human and Mechanised systems What is not specific required is denied Security systems Testing the key success factors in the real world Good Security: A Physical Analogy Security Camera Motion Detector Guard Security Success Factors Applied Multiple technologies including Access control Breach detection Auditing Ensures one fault does not put the crown jewels at risk Use of manual and digital security Multiple layers of security - “buys” time to repel attacker and prevents bert endangering the jewels Guard E-security systems Relating the digital-world to the real world E-security systems A model that works Countermeasures – Digital & Door + Lock = Physical Firewall Security Camera = Activity Logs Movement Sensors = Intrusion Detection Security Guard = Security Technician Physical Asset = Digital Asset System Logs Security Success Factors Applied Security Interface of manual and digital security Console Alert Multiple technologies including Access control Breach detection Internet Auditing Corporate Network data Ensures one fault does not put the crown jewels at risk Audit Logs Multiple layers of security -“buys” time to repel attacker and prevents bert endangering the jewels -Customer data not inDMZ Common Faults Common Faults Overall configuration & design No proper design documentation – only a collection of clip-art Design rules applied with no understanding so forCorporate Databases example multiple firewalls No ip addresses or server Customer Enterpris provide no extra protection Data e details etc Encrypted Systems No Desk Check done !!!!! information securely Too much newFurther and diverse transferring over the technology – multiple protectionUNIX of Data checking ing Internet Internet Internal Firewall the IntranetOS & Multiple IntranetWindows Perimeter download edWeb scripts Server Firewall versions make it operational Standing data stored in DMZonly protected by 1 Merchant Layer of security securely identified via Certificates ? Central role of the application server that will connect to all data Timesources Authentication flawedNo or centralised Certification User server or logging server SPI Unencrypted Authority securely identified via certificates Application Serverunviable Authentication and permissions ? Internet Databases SET payment No administration access protocol that or terminal servers so sends the user’s Bank details directly when things go wrongtoit is the bank impossible to get access Common Faults: Router Access lists absent, incomplete or applied to the wrong interface SNMP Corporate Network Internet open with Community string of Public & ... (Go on, have a guess) Telnet open - allowing unrestricted terminal access to the internet Audit Logs Small services open And even if the perimeter router isn’t yours WHO PAYS THE PRICE IF IT IS HACKED Bad Config - router 1 of 1 pants#show startup-config hostname pants enable password cisco interface Serial0/0 ip address 194.117.132.10 255.255.255.252 interface FastEthernet1/0 ip address 192.188.144.81 255.255.255.252 ip route 0.0.0.0 0.0.0.0 194.117.132.9 ip route 192.193.97.65 255.255.255.255 195.188.144.82 snmp-server community public RO snmp-server community private RW line con 0 line aux 0 line vty 0 4 password cisco login ! After After router 1 of 2 service password-encryption no service udp-small-servers no service tcp-small-servers hostname pants enable secret 5 $1$s1gN$TDLK8LhaSdgKlDUpR84OY1 enable password notused ! interface Serial0/0 ip address 192.117.132.10 255.255.255.8 ip access-group 102 in ! interface FastEthernet1/0 ip address 195.188.144.81 255.255.255.0 ! ip access-group 103 in After router 1 of 2 ! Management controls access-list 1 permit 193.193.97.65 access-list 1 permit 193.193.116.0 0.0.0.255 ! ! Spoof & rfc 1918 filter access-list 102 deny ip 195.188.144.0 0.0.0.255 any access-list 102 deny ip 10.0.0.0 0. 255 . 255 .255 any ! ! Traffic filter access-list 102 permit tcp any host 195.188.144.68 eq www access-list 102 permit tcp any host 195.188.144.66 eq smtp access-list 102 permit ip any host 195.188.144.66 ! ! Egress rules access-list 103 permit ip 195.188.144.0 0.0.0.255 any access-list 103 deny ip any any snmp-server community x1xx RO 1 snmp-server community x1xx RW 1 line con 0 password GMxQttt98 login line aux 0 line vty 0 4 access-class 1 in password Tmtttts login Common Faults - Firewalls No anti-spoofing Default passwords, Rules or Config Unused services Rules confused Corporate Network Internet + undocumented No consideration given to error logging or the return connection (which can stop many hacks !!!) Audit Logs Changes to the Configuration not logged No reporting of authorisation failures Before Pix 1 of 3 nameif ethernet0 outside security0 nameif ethernet1 inside security100 hostname firewall fixup protocol ftp 21 fixup protocol http 80 fixup protocol smtp 25 fixup protocol h323 1720 fixup protocol sqlnet 1521 names pager lines 24 no logging console no logging monitor no logging buffered errors no logging trap logging facility 20 Before Pix 2 of 3 interface ethernet0 auto interface ethernet1 auto ip address outside 11.73.2.222 255.255.255.0 ip address inside 11.73.7.251 255.255.255.0 nat (inside) 0 0.0.0.0 0.0.0.0 0 0 static (inside,outside) 11.73.1.2 161.73.1.2 netmask 255.255.255.255 0 0 static (inside,outside) 11.73.1.1 161.73.1.1 netmask 255.255.255.255 0 0 conduit permit tcp host 11.73.1.1 eq smtp any conduit permit tcp host 11.73.1.2 eq www any conduit permit tcp host 11.73.1.2 eq telnet any Before Pix 3 of 3 apply (inside) 11 outgoing_src rip outside passive rip outside default rip inside passive rip inside default route outside 0.0.0.0 0.0.0.0 161.73.2.234 1 no snmp-server location no snmp-server contact snmp-server community public no snmp-server enable traps telnet 11.73.140.99 255.255.255.255 telnet timeout 5 floodguard 1 Cryptochecksum:8c7bc2b51a5bd78305c83a14f13e9c7b After after Pix 1 of 3 nameif ethernet0 outside security0 nameif ethernet1 inside security100 hostname firewall no fixup protocol ftp 21 fixup protocol http 80 fixup protocol smtp 25 no fixup protocol h323 1720 no fixup protocol sqlnet 1521 names pager lines 24 no logging console logging host 192.2.2.1 logging trap 3 logging facility 20 After Pix 2 of 3 interface ethernet0 auto interface ethernet1 auto ip address outside 11.73.2.222 255.255.255.0 ip address inside 11.73.7.251 255.255.255.0 nat (inside) 0 0.0.0.0 0.0.0.0 0 0 static (inside,outside) 11.73.1.2 161.73.1.2 netmask 255.255.255.255 0 0 static (inside,outside) 161.73.1.1 161.73.1.1 netmask 255.255.255.255 0 0 conduit permit tcp host 11.73.1.1 eq smtp any conduit permit tcp host 11.73.1.2 eq www any conduit permit tcp host 11.73.1.2 eq telnet any outbound 11 permit 11.73.0.0 255.255.0.0 smtp tcp outbound 11 deny 11.73.0.0 255.255.0.0 www tcp apply (inside) 11 outgoing_src After Pix 3 of 3 rip outside passive rip outside default rip inside passive rip inside default route outside 0.0.0.0 0.0.0.0 161.73.2.234 1 no snmp-server location no snmp-server contact no snmp-server community public no snmp-server enable traps telnet 11.73.140.99 255.255.255.255 telnet timeout 5 floodguard 1 Cryptochecksum:8c7bc2b51a5bd78305c83a14f13e9c7b Firewall 1 - before Firewall 1 - After Common Faults - Web Server Whoops - SSL is not enabled data in the DMZ – Classical example of pointless Multiple layers Critical Corporate Network Internet Default CGI script or Administration servlets only protected by a simple (Default!!) passwords Developer Audit Logs SDK and doco available Operating systems not properly hardened and configured Common Faults - Applications Confidential screens and information (perhaps passwords) unencrypted – in URL or in cookies Corporate Network Internet Passwords used for highvalue transactions Application authorization that “should work” (as long as you don’t try it) Audit Logs No proper application logging or alerting –making fraud easy Common Faults - IDS Focusing on knownattacks rather than anomalous traffic Not updating it regularly -Attacks emerge every day Encryption Corporate Network Internet -Encryption is our friend – but if you install a network based IDS to monitor encrypted traffic what is it Putting them in a wrong place Audit Logs -You don’t put a motion detector outside your house KBOM