File
advertisement

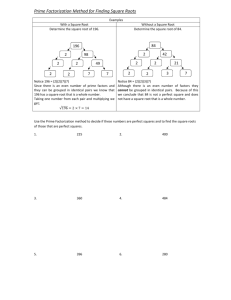
PRIME FACTORIZATION AND ITS APPLICATION TO CRYPTOGRAPHY Ricardo Estrada Justin Griffin Vishaal Sharma WHAT IS PRIME FACTORIZATION? It is the breaking down of a composite number into smaller non trivial divisors, which when multiplied together equals the original integer. A composite number is any positive integer greater than one that is not a prime number. A Prime Number can be divide evenly only by 1 or itself and it must be a whole number greater than 1. List of some of the prime numbers. HOW IS PRIME FACTORIZATION FOUND? Example of Prime Factorization There are different methods which can be utilized to find the prime factorization of a number. One way is to repeatedly divide by prime numbers Prime factorization of 80? Start working from the smallest prime number, which is going to be 2 in this case. 80 / 2 = 40 80 is evenly divided by 2 but 40 is not a prime number so we continue 40 /2 = 20 40 is evenly divided by 2 but 20 is not a prime number so we continue 20 / 2=10 20 is evenly divided by 2 but 10 is not a prime number so we continue 10 / 2 = 5 10 is evenly divided by 2 and 5 is a prime number so we have the answer 2X2X2X2X5=80 ANOTHER METHOD Another way to approach the task is to choose any pair of factors and split these factors until all the factors are prime: Break 80 into 8 X 10 The prime factors of 8 are 2, 2 and 2 The prime factors of 10 are 2 and 5 So the prime factors of 80 are 2, 2, 2, 2, and 5 WHAT IS CRYPTOGRAPHY? The art of protecting information by transforming it (encrypting it) into an unreadable format, called cipher text. Only those who possess a secret key can decipher (or decrypt) the message into plain text. Modern cryptography concerns itself with the following four objectives: 1) Confidentiality (the information cannot be understood by anyone except for whom it was intended for) 2) Integrity (the information cannot be altered in storage or transit between sender and intended receiver without the alteration being detected) 3) Non-repudiation (the creator/sender of the information cannot deny at a later stage his or her intentions in the creation or transmission of the information) 4) Authentication (the sender and receiver can confirm each other's identity and the origin/destination of the information) WHY IS PRIME FACTORIZATION USED IN CRYPTOGRAPHY? Cryptography is all about number theory, and all integer numbers are made up of primes, so you deal with primes a lot in number theory. More specifically, some important cryptographic algorithms such as RSA critically depend on the fact that prime factorization of large numbers takes a long time. Basically you have a "public key" consisting of a product of two large primes used to encrypt a message, and a "secret key" consisting of the primes used to decrypt the message. You can make the public key public, and everyone can use it to encrypt messages to you, but only you know the prime factors and can decrypt the messages. Anyone else who wanted to access your intended crypted messages would have to factor the number, which takes too long to be practical. What are its benefits? Used for encryption of data allowing only the person with the key to access that data, ensuring privacy. Used for signing messages and proving to the recipient that you are who you say you are. Used to solve mathematical problems. What are its cons? Because governments do not wish certain entities in and out of their countries to have access to ways to receive and send hidden information that may be a threat to national interests, cryptography has been subject to various restrictions in many countries, ranging from limitations of the usage and export of software to the public dissemination of mathematical concepts that could be used to develop cryptosystems. However, the Internet has allowed the spread of powerful programs and, more importantly, the underlying techniques of cryptography, so that today many of the most advanced cryptosystems and ideas are now in the public domain. An issue that arises in the usage of prime factorization to cryptography is the potential abuse by people with negative objectives. Often times, cryptography can be used by criminals to conceal the data they are sending back and forth through the internet. These criminals range from sexual predators who are trying to conceal any data that might get them in trouble, drug dealers, terrorists or people that are committing crimes and are trying to conceal it from the prying eyes of law enforcement. This abuse of cryptography brings up the current concern about the government wanting the keys to all encryption software. This means that they would have the ability to intercept anybody's data, decrypt it and observe the message. This is clearly a violation of our privacy. The current work around is to use freely available encryption software or use software that comes from overseas, since those companies don't have to worry about following our government regulations; and its easily available online. WHEN DID IT FIRST GET USED? The origin of cryptography is usually dated from about 2000 BC, with the Egyptian practice of hieroglyphics. These consisted of complex pictograms, the full meaning of which was only known to an elite few. Looking further, the Spartans (around 5B.C.) developed a cryptographic device to send and receive secret messages. The device was a small cylinder called a scytale. This scytale was in the possession of both the sender and the recipient of the message. To prepare the message, a narrow strip of parchment or leather, much like a modern-day paper streamer, was wound around the scytale and the message was written across it. Once unwound, for transport to the receiver, the tape displayed only a sequence of meaningless letters until it was re-wound onto a scytale of exactly the same diameter and the message could then be read. Julius Caesar(100 - 44BC)did not trust his messengers when communicating with his governors and officers; For this reason, he created a system in which each character in his messages was replaced by a character three positions ahead of it in the Roman alphabet. Cryptography changed the way we fought wars and led us to enter WWI. For example, The Zimmermann telegram: On the first day of hostilities, the British cable ship TELCONIA located and cut Germany's transatlantic cables, forcing them to send all their international traffic via Sweden or American-owned cables. Both means ran through the UK and soon all German traffic was routinely routed to ROOM 40, the Royal Navy's cypher organisation. On or about January 16, 1917 two Room 40 cryptanalyst William Montgomery and Nigel De Gray , were given a message encrypted in the German Foreign Office code, a book cypher number 0075. By the next morning they had deduced enough of the message to be chilled by its content. Sent by the German Foreign Minister Zimmermann to the Mexican President via the German Embassies in Washington and Mexico City, it advised the President of Mexico that Germany proposed to start unrestricted submarine warfare in February and that he should, with German help, attack the US and also convince the Japanese to do the same. In short order the full text was recovered and presented to US President Wilson. On April 2, 1917 the then neutral US declared war on Germany and by 1918 Germany had been defeated. This in turn leads to accelerated sociological and technological change. The first world war showed the importance of cryptography on the battlefield, and the danger of weak encryption. The second world war became a defining moment in the history of cryptography and placed it squarely at the centre of military and political strategy from that time to the present day. HISTORY OF PRIME NUMBERS IN CRYPTOGRAPHY Although not used in cryptography, prime numbers first show up in recorded history in ancient Greece. The Sieve of Eratosthenes is developed by ancient Greek mathematician Eratosthenes. This was around the year 300 BC! Prime numbers then disappear from history for the next two thousand years, reappearing again in the 17th century Pierre de Fermat developed Fermat’s little theorem. 22n + 1 are prime numbers. (Unproved at the time). French monk Marin Mersenne used the formula 2p-1, with p being a prime number. PRIME FACTORIALS IN THE MODERN AGE In modern computing, the first cryptographic standard in the 1970s was NES. Everything changed in 1976 when the Diffie-Hellman key exchange was introduced by Whitfield Diffie and Martin Hellman. This standard did NOT use prime numbers. Instead, it used a block cypher. Block cyphers essentially have plaintext at the root of their encryption. This was a method for two parties with no prior knowledge of each other to share and establish a secret key. This was radically new concept at the time and went a long way into improving cryptography. The original implementation of this involved the formula Ya=G^(Xa)(mod P), where P is a prime number and G is primative root mod P. This was the beginning of public key cryptography. Later, in 1978 cryptography using primes comes into its own with the RSA algorithm. RSA is used in many different things, from credit cards to browsers to email encryption. THE DIFFIE-HELLMAN KEY EXCHANGE Definition: If every element in group G can be expressed as the product of finitely many powers of g, then element g is a generator. Definition: Now assume g is a primitive root mod p. If g^x ≡ y (mod p) then the discrete logarithm of y to the base g is indg(y)=x mod(ø(p)) Two people, A & B, do not want C to hear their message. They create two public numbers g and p, where p is a prime and g is a primitive root mod p. A now computes u ≡g^a(mod p) and sends u to B, where a is another random number A has chosen. B does the same thing, choosing random number b and sending v from v ≡g^b(mod p) to A. Now both have the same key, computed with k=g^(ab)(mod p) THE RSA ALGORITHM Created by Rivest, Shamir, and Adleman at MIT in 1977. Users A and B have the same problem as in the previous slide, not wanting C to have their information. Both select two large prime numbers at random, p and q of near equal size so that n = pq is 1024 bits. Now compute n=pq and φ= (p-1)(q-1). Integer e is then chosen, such that 1 < e < φ, & gcd(e, φ) = 1. Now compute the secret exponent d such that 1 < d < ≡ & ed ≡ 1 (mod φ). Note that the most common choices for e are 3, 17 and 65537. All of these numbers are Fermat primes (Fx=2^(2^x)+1). The Extended Euclidean Algorithm is used to do this, and the process is known as modular inversion. The public key is (n, e) and the private key is (n, d). d, p, q, and φ are kept secret. From the above, it is easy to see why the RSA algorithm is fairly secure. This is just the key generation! A BETTER PICTURE OF RSA Key Generation Encryption Decryption FUTURE OF PRIME FACTORIZATION AND CRYPTOGRAPHY In theory, a newer technology could render current cryptographic schemes (such as RSA) useless. Current cryptographics use the process of prime factorization to select a number so large that it would be impossible for any one to break the cypher text. With todays computing power, it would take millions of years before a computer could decipher the text. The next big threat to current cryptography schemes is the quantum computer, which is currently being researched by various universities throughtout the world. A large quantum computer, if one is ever built, could theoretically factor numbers quickly enough to defeat the code, which would make this cryptographic and its prime factorizatioin useles. If a quantum computer is eventually built, the prime factorization algorithms being used for encryption would be rendered useless. However, there will be alternate cryptographic schemes that employ different algorithms that do not use prime factorization. It seems that the future of prime factorization and its application to cryptography may be coming to an end due to the processing capabilities of quantum computing. If a normal computer would take billions of years to decipher a text, a quatum computer could theoretically decipher this text in minutes! Below are the current methods being used to encrypt our data and the possible future replacements. Hint, they do not include prime factorization. POSSIBLE REPLACEMENTS: Hash based signature scheme A hash function is an algorithm that transforms text into a relatively short string of bits, called the signature. Its security is based on being able to produce a unique signature for any given input. Even inputs that are only slightly different from one another should produce different hashes. Error correcting codes Such a scheme would introduce errors into a message to make it unreadable. Only the intended receiver of the message would have the right code to correct the error and make the document readable. Multivariable public-key cryptosystem (MPKC) To crack it, a machine must solve multivariable nonlinear equations. This type of cryptography is extremely efficient and much faster to produce than other schemes, such as RSA, which must use numbers hundreds of digits long to be secure. Lattice based system The lattice is a set of points in a many-dimensioned space. Possibly useful for both digital signatures and public-key cryptography, a lattice system would be cracked by finding the shortest distance between a given point in space and the lattice. It has potential, but it still needs more research. REFERENCES http://www.mathsisfun.com/prime-factorization.html http://en.wikipedia.org/wiki/Prime_factor