Technology In Action
advertisement

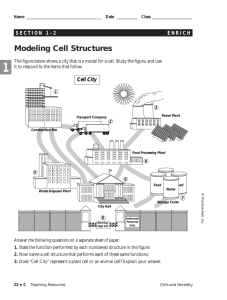
Technology In Action Networking and Security Connecting Computers and Protecting Them from Intruders © 2006 Prentice-Hall, Inc. 1 Technology In Action Networking Advantages and Disadvantages • Advantages – – – – Increased productivity More communication options Enable the sharing of resources Facilitate Internet connectivity • Disadvantages – Complexity – Cost Materials Personnel © 2006 Prentice-Hall, Inc. 2 Technology In Action What is a Network? • Computer network: – Two or more computers connected together – Nodes: Any device connected to a network © 2006 Prentice-Hall, Inc. 3 Technology In Action Network Architecture • Network designs: – Locally controlled: Peer-to-peer (P2P) – Centrally controlled: Client/server Peer-to-peer Client/ server © 2006 Prentice-Hall, Inc. 4 Technology In Action Peer-to-Peer Networks • Nodes communicate with each other: – Peers • Share peripheral devices: – Printers • Home and small office networks © 2006 Prentice-Hall, Inc. 5 Technology In Action Client/Server Networks • Client computers: – Users • Server computers: – Provide resources to clients – Central control unit • Data flows efficiently • Servers respond to requests from clients • Scalable network © 2006 Prentice-Hall, Inc. 6 Technology In Action Servers • Depending on the network size and work load servers can perform a single or multiple roles © 2006 Prentice-Hall, Inc. 7 Technology In Action Dedicated Server Types • • • • • • • © 2006 Prentice-Hall, Inc. Application Authentication File Database Email Web Print 8 Technology In Action Classifications of Client/Server Networks • LAN: local area network – Computers linked together over a small geographic region • WAN: wide area network – Computers linked together over large diverse geographic locations • MAN: metropolitan area network – Computers linked together within a city or county • PAN: personal area network – Wireless devices connected in close proximity to each other © 2006 Prentice-Hall, Inc. 9 Technology In Action Network Topology • Physical layout of networks components – Bus – Ring – Star © 2006 Prentice-Hall, Inc. 10 Technology In Action Bus Topology • All nodes are connected in sequence on a single cable • Used most often on peer-to-peer networks • Networked computers communicate with each other • One computer transmits data at a time: – Access methods avoid data collisions – Data is transmitted in “packets” © 2006 Prentice-Hall, Inc. 11 Technology In Action Ring Topology • Nodes are laid out in a ring • Token (data packet) flows in one direction from device to device © 2006 Prentice-Hall, Inc. 12 Technology In Action Star Topology • Nodes connect to a central communications device (hub/switch) • A node sends a signal to the hub which retransmits it to the other nodes • A node accepts the signal addressed to it © 2006 Prentice-Hall, Inc. 13 Technology In Action Network Operating Systems (NOS) • Provide the protocol that controls the communication between devices on the network • Major network operating systems: – Windows Server 2003 – UNIX – Novell NetWare © 2006 Prentice-Hall, Inc. 14 Technology In Action Network Adapters • Devices connected to or installed in nodes: – Network interface cards (NIC) – External network adapter • Enable communication between nodes NIC © 2006 Prentice-Hall, Inc. External adapter 15 Technology In Action Wireless Adapters • Uses radio waves to connect nodes (2.4GHz) • Each node requires a wireless network adapter © 2006 Prentice-Hall, Inc. 16 Technology In Action Transmission Media • Provides communications channel between nodes • Forms of media: – Telephone wire: Twisted pair – Coaxial cable – Fiber-optic cable – Radio waves: Wireless • Bandwidth: – Data transfer rate – Throughput – Measured in megabits per second (Mbps) © 2006 Prentice-Hall, Inc. 17 Technology In Action Choosing a Cable • • • • • • • Maximum run length Bandwidth Bend radius Cable cost Installation costs Susceptibility to interference Signal transmission methods © 2006 Prentice-Hall, Inc. 18 Technology In Action Twisted Pair Cable • Copper wire twisted around each other to reduce interference • STP- Shielded • UTP- Unshielded – Cat 5 – Cat 6 © 2006 Prentice-Hall, Inc. 19 Technology In Action Coaxial Cable • Four components: – – – – Copper core Nonconductive insulating material Braided metal Plastic cover © 2006 Prentice-Hall, Inc. 20 Technology In Action Fiber-Optic Cable • Components include: – Glass or plastic fibers – Cladding – Outer jacket • Uses light impulses to transmit data • Immune to interference © 2006 Prentice-Hall, Inc. 21 Technology In Action Network Navigation Devices • Devices that help make data flow possible – Repeaters – Hubs – Switches – Routers © 2006 Prentice-Hall, Inc. 22 Technology In Action Ethernet Repeater and Hubs • Repeaters – Amplifies the signal • Hubs – Amplifies the signal – Simultaneous broadcasting – Acts like a cable splitter © 2006 Prentice-Hall, Inc. 23 Technology In Action Ethernet Switches and Routers • Switches – Send data to specific nodes on the network • Routers – Communicates data between different networks © 2006 Prentice-Hall, Inc. 24 Technology In Action Data Transmission and Protocols • Computer protocols are rules for electronic information exchange • Open system protocols: – Any computer can communicate with other computers using the same protocols • Circuit switching • Packet switching © 2006 Prentice-Hall, Inc. 25 Technology In Action Circuit Switching • Dedicated connection between two points • Remains active until the transmission is terminated • Telephone communications © 2006 Prentice-Hall, Inc. 26 Technology In Action Packet Switching • Data is broken into small units called packets • Packets are sent over various routes to their destination • Packets are reassembled by the receiving computer • Packets contain: – Destination/source addresses – Reassembling instructions – Data © 2006 Prentice-Hall, Inc. 27 Technology In Action Ports • Source Ports - is assigned to the client and is used to keep track of user sessions. • Destination Ports - are used to route packets to the appropriate application. • Listening Ports - software that responds to a port number is said to be "listening" for its packets. • 65,535 ports • Well known ports are 0-1023. – Port 80 HTTP © 2006 Prentice-Hall, Inc. 28 Technology In Action Headers • Encapsulation- layering of instructions onto the data • Headers are like mailing addresses and handling instructions • Contains information for the handling of the data block © 2006 Prentice-Hall, Inc. 29 Technology In Action TCP, IP, UDP • TCP- Transmission Control Protocol – Reliable Will resend lost packets Error checking – Send in an orderly fashion • UDP - User Datagram Protocol – Faster – Less reliable – Streaming • Internet Protocol - specifies the format of packets © 2006 Prentice-Hall, Inc. 30 Technology In Action MAC Address • Media Access Control address: hardware address that uniquely identifies each node of a network. • Example: 07-a1-34-ff-b5-df © 2006 Prentice-Hall, Inc. 31 Technology In Action IP Addresses • Unique number that identifies NOS/devices connected to the Internet • Example: 134.68.76.100 • Static address: – Address never changes: Enter it manually • Dynamic address: – Temporary address: Automatically assigned © 2006 Prentice-Hall, Inc. 32 Technology In Action Anatomy of a Data Packet © 2006 Prentice-Hall, Inc. 33 Technology In Action OSI (Open Systems Interconnection) Model © 2006 Prentice-Hall, Inc. 34 Technology In Action © 2006 Prentice-Hall, Inc. 35 Technology In Action Questions? © 2006 Prentice-Hall, Inc. 36 Technology In Action Network Security • Why attack a network rather than the computers on the network? – Lower risk of getting caught – Less work – Availability of tools – Numerous methods © 2006 Prentice-Hall, Inc. 37 Technology In Action Networking Attack Methods • • • • Sniffing Spoofing DoS – Denial of Service Port Scanning © 2006 Prentice-Hall, Inc. 38 Technology In Action Ethereal- Packet Sniffer © 2006 Prentice-Hall, Inc. 39 Technology In Action Netstumbler - Wireless Network Scanner © 2006 Prentice-Hall, Inc. 40 Technology In Action NetScan- Port Scanner © 2006 Prentice-Hall, Inc. 41 Technology In Action Wireless Security or Lack Thereof • Lack of user awareness • No authentication • Pervasiveness • Tools are easily available • Poor security design – Weak encryption – Enabled defaults Admin PW Broncast on SSID © 2006 Prentice-Hall, Inc. 42 Technology In Action 150ft = 6 Houses, 1 street © 2006 Prentice-Hall, Inc. 43 Technology In Action 450ft = 40 houses, 4 streets © 2006 Prentice-Hall, Inc. 44 Technology In Action WWWD 2004 Stats • 228537 APs found • 140890 No WEP (60+%) – Wired Equivalent Privacy • 71850 Default SSID (30+%) – Service Set IDentifier • 62859 Default SSID and No WEP (27+%) © 2006 Prentice-Hall, Inc. 45 Technology In Action Wireless Math Open wireless + Netstumbler = War Driving + GPS + Internet = http://www.wifimaps.com/ © 2006 Prentice-Hall, Inc. 46 Technology In Action Wireless Security Best Practices • Change default settings – Admin password – SSID – Service Set identifier Rename Choose wisely • Turn on WEP encryption • Disable SSID Broadcast • Create a VPN and use encryption © 2006 Prentice-Hall, Inc. 47 Technology In Action Wireless Security Paradoxs and Myths • • • • • MAC filtering Disable SSID Broadcast Disable DHCP Antenna placement WEP Enabled © 2006 Prentice-Hall, Inc. 48 Technology In Action Network Security • Firewalls: Block unused ports – Protects against port scanning • Authentication: – User ID and password used to access the network • Access privileges: – Close access to unused network systems – Use encryption and VPNs • Monitor your network – Fake APs – Watch traffic – Scan detectors © 2006 Prentice-Hall, Inc. 49 Technology In Action Links http://netstats.indiana.edu/wanmap/index.h tml http://reviews.cnet.com/Bandwidth_meter/ 7004-7254_7-0.html © 2006 Prentice-Hall, Inc. 50