Chapter 12
advertisement

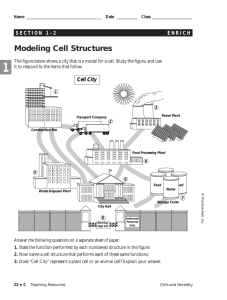
Technology in Action © 2008 Prentice-Hall, Inc. 1 Technology in Action Chapter 12 Behind the Scenes: Networking and Security © 2008 Prentice-Hall, Inc. 2 Chapter Topics • • • • • • • • • • • Advantages of business networks Client/server vs. peer-to-peer networks Classifications of client/server networks Client/server network components Types of servers Network topologies Types of transmission media Network software Network adapters Moving data in a client/server network Securing networks © 2008 Prentice-Hall, Inc. 3 Networking Advantages • Networks – Increase productivity – Enable the sharing of hardware resources – Enable the sharing of software – Facilitate Internet connectivity © 2008 Prentice-Hall, Inc. 4 Client/Server Networks • Server-based network – Clients and servers • Data flows efficiently • Servers respond to requests from clients • Servers perform specific tasks • Scalable network • Centralized © 2008 Prentice-Hall, Inc. 5 Classifications of Client/Server Networks • LAN – Local area network – Computers linked together over a small geographic region © 2008 Prentice-Hall, Inc. 6 Classifications of Client/Server Networks • WAN – Wide area network – Computers linked over large geographic locations • MAN – Metropolitan area network – Computers linked together within a city or county © 2008 Prentice-Hall, Inc. 7 Classifications of Client/Server Networks • PAN – Personal area network – Wireless devices connected in close proximity to each other • Intranet – Private corporate network – Protected by a firewall © 2008 Prentice-Hall, Inc. 8 Constructing Client/Server Networks • • • • Servers Network topologies Transmission media Network operating system (NOS) • Network adapters • Network navigation devices © 2008 Prentice-Hall, Inc. 9 Servers • Number and type of servers depend on network size and workload • Dedicated server – Performs one specific function • Authentication server – Keeps track of network logins and services available • File server – Stores and manages files © 2008 Prentice-Hall, Inc. 10 Dedicated Servers • Print server – Manages client-requested printing jobs – Creates print queue (prioritizes print jobs) • Applications server – Acts as a storage area for application software • Database server – Provides clients with access to database information • E-mail server – Processes and delivers incoming and outgoing e-mail © 2008 Prentice-Hall, Inc. 11 Dedicated Servers • Communications server – Handles communications between networks including the Internet – Often the only device on the network directly connected to the Internet • Web server – Hosts a Web site available through the Internet © 2008 Prentice-Hall, Inc. 12 Network Topologies • The physical layout of computers, transmission media, and other components • Types of network topologies – Bus topology – Ring topology – Star topology – Hybrid topology © 2008 Prentice-Hall, Inc. 13 Bus Topology • All nodes are connected in sequence on a single cable • Used most often on peer-to-peer networks • Networked computers communicate with each other • One computer transmits data at a time – Access methods avoid data collisions – Data is transmitted in “packets” © 2008 Prentice-Hall, Inc. 14 Ring Topology • Nodes are laid out in a ring • Token (data packet) flows in one direction from device to device • Recent versions have data transfer rates up to 100 Mbps © 2008 Prentice-Hall, Inc. 15 Star Topology • Nodes connect to a central communications device (switch) • A node sends a signal to the switch, which retransmits it to the other nodes • A node accepts only signal addressed to it © 2008 Prentice-Hall, Inc. 16 Avoiding Data Collisions on an Ethernet Network © 2008 Prentice-Hall, Inc. 17 Transmission Media • The routes data takes to flow between devices on a network • Wired • Wireless – Wireless Fidelity (Wi-Fi) – Uses radio waves – 802.11 standard © 2008 Prentice-Hall, Inc. 18 Choosing a Cable • • • • • Installation costs • Susceptibility to interference • Signal transmission methods Maximum run length Bandwidth Bend radius Cable cost Comparison of Characteristics of Major Cable Types Cable Characteristics Twisted Pair (Cat 6) Coaxial (ThinNet) Coaxial (ThickNet) Fiber-Optic Maximum Run Length 328 feet (100 m) 607 feet (185 m) 1,640 feet (500m) Up to 62 miles (100 km) Bandwidth 1,000 Mbps 10 Mbps 10 Mbps 100 Mbps to 2 Gbps Bend Radius (Flexibility) No limit 360 degrees/foot 30 degrees/foot 30 degrees/foot Cable Cost Very low Low Moderate High Installation Cost Very low Low Slightly higher than ThinNet Most expensive because of Installation training required Susceptibility to Interference High Low Very low None (not susceptible to EMI and RFI) © 2008 Prentice-Hall, Inc. 19 Twisted Pair Cable • Pairs of copper wire twisted around each other • Twists make the wires less susceptible to interference • Shielded twisted pair (STP) UTP – Layer of foil shielding • Unshielded twisted pair (UTP) – Cat 5E: Bandwidth 200 Mbps – Cat 6: Bandwidth 1 Gbps – No foil layer © 2008 Prentice-Hall, Inc. STP 20 Coaxial Cable • Four components – Copper core – Nonconductive insulating material – Braided metal – Plastic cover © 2008 Prentice-Hall, Inc. 21 Fiber-Optic Cable • Components include – Glass or plastic fibers – Cladding – Outer jacket • Uses light impulses to transmit data • Immune to interference © 2008 Prentice-Hall, Inc. 22 Wireless Media 802.11 Standard • Wi-Fi, short for Wireless Fidelity – 802.11b – first cost-effective wireless devices. – 802.11a, 802.11g – bandwidth increased to 54 Mbps – Super G – bandwidth to 108 Mbps – 802.11n – will support higher throughput and greatly increased range © 2008 Prentice-Hall, Inc. 23 Network Operating Systems (NOS) • Provide the protocol that controls the communication between devices on the network • Major network operating systems – Windows Server 2003 – UNIX – Novell NetWare © 2008 Prentice-Hall, Inc. 24 Network Adapters • Devices that enable computers to communicate on a network • Network interface cards (NICs) • Three functions – Generate network transmission signals – Create data packets – Act as information gatekeepers • Ethernet compliant • Wireless NICs © 2008 Prentice-Hall, Inc. 25 Network Navigation Devices • Media Access Control (MAC) address – Six two-digit numbers (01:40:87:44:79:A5) – Physical address of network adapter – Internal network identification • Repeaters and Hubs – Amplify signals and retransmit them © 2008 Prentice-Hall, Inc. 26 Network Navigation Devices • Switches and Bridges – Send data on a specific route through the network – Bridges send data between collision domains • Routers – Send information between two networks © 2008 Prentice-Hall, Inc. 27 Network Security Threats • Human Errors and Mistakes – Accidents and mistakes • Malicious Human Activity – Current and former employees hacking or planting viruses • Natural Events and Disasters – Hurricanes, floods, fire © 2008 Prentice-Hall, Inc. 28 Network Security • Authentication – User ID and password used to access the network – Use of a possessed object for access • Access privileges – Enable access to certain network systems • Physical protection measures – Restrict physical access to sensitive network equipment – Magnetic card readers – Biometric access devices © 2008 Prentice-Hall, Inc. 29 Network Security • Firewalls – Prevent access to the network by unauthorized users – Composed of software and/or hardware – Screen and validate data packets – Bastion host/proxy server © 2008 Prentice-Hall, Inc. 30 Network Firewall Layout © 2008 Prentice-Hall, Inc. 31 Chapter 12 Summary Questions • What are the advantages of a business network? © 2008 Prentice-Hall, Inc. 32 Chapter 12 Summary Questions • How does a client/server network differ from a peer-to-peer network? © 2008 Prentice-Hall, Inc. 33 Chapter 12 Summary Questions • What are the different classifications of client/server networks? © 2008 Prentice-Hall, Inc. 34 Chapter 12 Summary Questions • What components are needed to construct a client/server network? © 2008 Prentice-Hall, Inc. 35 Chapter 12 Summary Questions • What do the various types of servers do? © 2008 Prentice-Hall, Inc. 36 Chapter 12 Summary Questions • What are the various network topologies? © 2008 Prentice-Hall, Inc. 37 Chapter 12 Summary Questions • What types of transmission media are used in client/server networks? © 2008 Prentice-Hall, Inc. 38 Chapter 12 Summary Questions • What software needs to be running on computers attached to a client/server network? © 2008 Prentice-Hall, Inc. 39 Chapter 12 Summary Questions • How do network adapters enable computers to participate in a client/server network? © 2008 Prentice-Hall, Inc. 40 Chapter 12 Summary Questions • What devices assist in moving data around a client/server network? © 2008 Prentice-Hall, Inc. 41 Chapter 12 Summary Questions • What measures are employed to keep large networks secure? © 2008 Prentice-Hall, Inc. 42