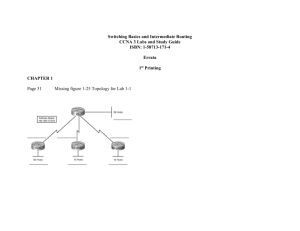
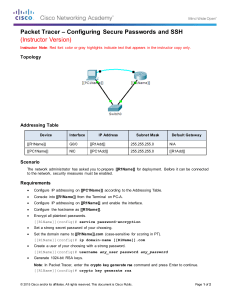
Secured Wired LAN Project Final Report-2011-2012
advertisement

SECURING WIRED LOCAL AREA NETWORK FINAL PROJECT REPORT Mr Sentuya Francis Derrick, ID 08051602 Module: CT3P50N fds0008@londonmet.ac.uk Supervisor: Dr. Shamhram Salekzamankhani s.salekzamankhani@londonmet.ac.uk A Final Project Report as a requirement of London Metropolitan University for a BSc Computer Networking with Honours December-16-2011 Faculty of Computing Page 1-- 1 - of 105 Abstract This report shows how to secure the vulnerabilities of a wired LAN. It examines the technology used to secure the LAN against various dynamic network security threats. A brief history of Network security and its operation is initially outlined. The discussion then is focused on the potential LAN security vulnerabilities using the OSI model. A virtual topology is used to showing the secured LAN achieved by having a good LAN design, incorporating appropriate secured network security devices. A detailed explanation of the security configurations and their verification/results are included. Suggestions and recommendations are given, plus a mentioning of further work to be done. The report concludes that, the set out aims and objective are achieved, and also makes a note that network security is a process that is on-going. New technological mitigation measures should be learned and applied on the LANs. It’s suggested that network professions should be sought, share information, and keep installing software patches on the Local Area Networks systems. Page 1-- 2 - of 105 Contents at Glance 1 – 13 - 105 Chapter 1 Introduction Chapter 2 Literature Review Chapter 3 Approach and Scope 2 – 18 - 105 3 – 24 - 105 Chapter 4 Practical Simulation and Results 4 – 29 - 105 Chapter 5 Critical appraisal, Recommendations and Suggestions for further work 5 – 34 - 105 Chapter 6 Conclusion 6 - 42 - 105 Appendix A: Network Device documentation - show run command. 6 - 46 - 105 Appendix B: Glossary 6 - 65 - 105 Appendix C: Project Proposal 6 - 67 - 105 Page 1-- 3 - of 105 Contents Contents ........................................................................................................................................... 1-- 4 Chapter 1 : Introduction ................................................................................................................. 1-- 13 1.1 Aims and Objectives ............................................................................................................. 1-- 14 Personal and Academic objectives ............................................................................................... 1-- 15 1.2 Methodology ........................................................................................................................ 1-- 15 1.3 Chapter Summary................................................................................................................. 1-- 17 Chapter 2 : Literature Review ........................................................................................................ 2-- 18 2.1 What is a LAN? ............................................................................................................... 2-- 18 - 2.2 What is LAN Security? .................................................................................................... 2-- 19 - 2.2.1 The Evolution of LAN Security ....................................................................................... 2-- 20 2.2.2 LAN’s most vulnerable layer.......................................................................................... 2-- 20 2.3 Common network threats .............................................................................................. 2-- 21 - 2.3.1 Reconnaissance attacks................................................................................................. 2-- 21 2.3.2 Denial-of-service ........................................................................................................... 2-- 21 2.3.3 Access attacks................................................................................................................ 2-- 22 2.4 Chapter Summary........................................................................................................... 2-- 23 - Chapter 3 : Approach and Scope .................................................................................................... 3-- 24 3.1 Approach ........................................................................................................................ 3-- 24 - 3.2 Project Scope.................................................................................................................. 3-- 25 - 3.3 Contingency Plans .......................................................................................................... 3-- 27 - 3.4 Scenario ................................................................................................................................ 3-- 27 3.5 Chapter Summary........................................................................................................... 3-- 28 - Chapter 4 : Practical simulation and results................................................................................... 4-- 29 4.1 Security Configuration on Cisco catalyst Switches ............................................................... 4-- 32 4.1.2 Message of the day / login Banner ............................................................................... 4-- 32 4.1.3 Port level Port Security .................................................................................................. 4-- 32 4.1.4 BPDU Guard................................................................................................................... 4-- 33 4.1.5 Storm Control ................................................................................................................ 4-- 35 4.1.6 Root Guard .................................................................................................................... 4-- 35 4.1.7 Spanning Tree Protocol feature - PortFast .................................................................... 4-- 36 4.1.8 Root Bridge .................................................................................................................... 4-- 36 4.1.9 VLAN Trunk Security ...................................................................................................... 4-- 37 4.110 VLANs ........................................................................................................................... 4-- 38 4.1.11 High Availability with Hot Standby Routing Protocol (HSRP) ...................................... 4-- 39 Page 1-- 4 - of 105 4.2 Security Configuration to manage router security on Cisco Routers............................... 4-- 2 - 4.2.1 Message of the day / login Banner ................................................................................. 4-- 2 4.2.2 Password requirement .................................................................................................... 4-- 2 4.2.3 Secure remote administrative access to routers ............................................................ 4-- 3 4.2.4 Secure router network services ...................................................................................... 4-- 8 4.2.5 Configure Authentication, Accounting, Authorization protocol .................................... 4-- 9 4.2.6 Log router activity ......................................................................................................... 4-- 10 4.2.7 Syslog server.................................................................................................................. 4-- 11 4.2.8 IPS software firewall...................................................................................................... 4-- 13 4.2.9 Secure EIGRP routing protocol authentication ............................................................. 4-- 15 4.2.10 Securing the router IOS image on perimeter, and firewall routers ............................ 4-- 17 4.2.11 Access Lists .................................................................................................................. 4-- 17 4.3 Simulation and verification of user access to different Subnets of the LAN/ Internet .... 4-- 21 4.4 Context-based access control (CBAC) inspection rule ................................................... 4-- 26 - 4.4.1 Inspection rule/Audit-trail enabled screen shot ........................................................... 4-- 27 4.4.2 Simulation of inspection /audit-trail process ................................................................ 4-- 28 4.5 Port Address Translation PAT / NAT Overload ..................................................................... 4-- 28 4.6 DHCP implementation .......................................................................................................... 4-- 31 4.6.1 DHCP Snooping.............................................................................................................. 4-- 32 4.6.2 Dynamic ARP inspection................................................................................................ 4-- 32 4.6.3 IP source guard .............................................................................................................. 4-- 33 4.7 Chapter Summary........................................................................................................... 4-- 33 - Chapter 5 : Critical appraisal, recommendations and suggestions for further work .................... 5-- 34 5.1 Critical appraisal ............................................................................................................. 5-- 34 - 5.2 Suggestions for Further work ......................................................................................... 5-- 37 - 5.2.1 Backup IOS software images ......................................................................................... 5-- 37 5.2.2 Continuous network monitoring ................................................................................... 5-- 38 5.3 Recommendations ......................................................................................................... 5-- 38 - 5.3.1 Virtual private network technology (VPN) .................................................................... 5-- 38 5.3.2 Cisco Adaptive Security Appliance (ASA) firewall ......................................................... 5-- 38 5.4 ASA Intrusion detection and Prevention system ................................................................. 5-- 40 5.5 DNS Implementation on the Cisco ASA ................................................................................ 5-- 40 5.6 Host- Based Intrusion Detection Systems ............................................................................ 5-- 40 5.7 Chapter Summary........................................................................................................... 5-- 41 - Chapter 6 : Conclusion ................................................................................................................... 6-- 42 Page 1-- 5 - of 105 References:..................................................................................................................................... 6-- 44 Appendix A: .................................................................................................................................... 6-- 46 A.1 Device documentation with a show run command ............................................................. 6-- 46 A.1.1 Secured Perimeter Router documentation .................................................................. 6-- 46 A.1.2 Secured Firewall Router documentation ...................................................................... 6-- 48 A.1.3 Secured Layer 3Switch1 documentation ...................................................................... 6-- 52 A.1.4 Secured Layer 3Switch2 documentation ...................................................................... 6-- 55 A.1.5 Secured Layer 2Switch1 documentation ...................................................................... 6-- 58 A.1.6 Secured Layer 2Switch2 documentation ...................................................................... 6-- 60 Appendix B: ................................................................................................................................ 6-- 63 B.1 Glossary ................................................................................................................................ 6-- 63 Appendix C: ................................................................................................................................ 6-- 67 C.1 Project proposal ................................................................................................................... 6-- 67 - Page 1-- 6 - of 105 List of Figures, titles, and their pages I. II. Figure 1: DOS Attack Page 2 -- 22 - 105 Figure 2: Secured LAN Topology Page 4 -- 29 - 105 Page 1-- 7 - of 105 List of Tables, titles, and their pages I. Table 1 Types of Network devices used Page 4 - 30 - of 105 Table 2 Network Configuration Table: Routers Page 4 -- 30- of 105 III. Table 3 End-system configuration table: Switches Page 4 -- 31- of 105 IV. Table 4 End-system configuration table: End devices Page 4 -- 31- of 105 II. Page 1-- 8 - of 105 The following is a reference list of Abbreviations used in this report. AAA: Authentication Authorisation Accounting ASA: Adaptive Security Appliance BPDU: Bridge Protocol Data Unit DHCP: Dynamic Host Configuration Protocol DMZ: Demilitarizes Zone DOS: Denial of Service DTP: Dynamic Trunking Protocol FTP: File Transfer Protocol FDDI: Fibre Distributed Data Interface HTTP: Hypertext Transfer Protocol IPS: Intrusion Prevention System IP: Internet Protocol IEEE: Institute of Electrical and Electronic Engineers LAN: Local Area Network NAT: Network Address Translation MAC: Media Access Control OSI: Open Standard Interconnect POP3: Post office Protocol PAT: Port Address Translation Page 1-- 9 - of 105 SSH: Secure shell VLAN: Virtual Local Area Network VPN: Virtual Private Network Page 1-- 10 - of 105 Acknowledgement I would like to thank Dr. Shamhram Salekzamankhani my project supervisor for his guidance, and continually working with me from the start of my proposal writing up to the implementation phase of this project. Your help has been indispensable when it comes to doing my project and I can’t say enough how much your help and support kept me sane during my project work. Also, thanks to my lecturer Mr Talik Molalingn who taught me a very important module (Fundamentals of Network Security) that has been crucial in doing my project. Also Dr Nicholas Ioannides, who taught me and guided me on how to write a very good structured project report and presentational skills. Big thanks goes to Ebrima Bah for your continued support, discussions till late evenings, advice, and encouragement you have offered me all through my second phase of my project implementation. Lastly but not the least, I thank God for the ability, knowledge, and the gift of life for me to be able to do this project. Page 1-- 11 - of 105 Dedication To my boys who have been so patient with me when I am busy studying and pursuing my academics. You have always given me space and a reading environment that enables me to have the luxury of my intellectual pursuits. You bring a smile to my face every day. I know that as you see me working hard and studying harder till late in the night will inspire you to also work hard in your studies so that your dreams come true. You have encouraged and made me happy seeing you so much interested in your studies and sometimes joining me in my reading study room to read together. Sentuya Francis Derrick Page 1-- 12 - of 105 Chapter 1 : Introduction This is a final project report on a secured wired local area network. As it is required, the report deals with an in depth view backed by my research from different sources such as network security books, the internet, Cisco network related lectures at London metropolitan University on the LAN security threats, and the technological measures that are available and used to secure wired LANs. Equipped with this knowledge, the report shows the implemented measures to achieve a secured wired LAN. The report defines what is meant by Local Area Networks, gives an insight of the background of LANs, and defines network security. It also gives an overview of the evolution of the LAN security, network security threats and the mitigations techniques available. A LAN as a group of computers and devices interconnected together in a limited geographical area such as computer laboratory, home, office buildings, or schools, to enable the sharing of resources like printers, files, applications amongst users on the network. By this definition it’s imperative therefore, to make Local area networks secure to provide network users with confidentiality, data Integrity, and availability. Network security is such an important part of Local area networks which involves securing protocols, technologies, devices, and mitigating any network security threats by use of network security tools and techniques. Network security policies are put in place to provide a framework and guideline for network users/employees to follow when doing their work on LANs. A Virtual topology is used to show how to have a secured LAN solution. Page 1-- 13 - of 105 1.1 Aims and Objectives Aim 1: To investigate which layer of the OSI model is most vulnerable to attacks on the Local Area Network. Objectives (i) To secure the physical devices that operate at the physical layer such as; Routers, Switches, PCs, servers, cables, Network interface cards, Transceivers, Repeaters, Hubs, Multi-station access units. (ii) To secure layer 2 protocols of the OSI model such as the Ethernet/IEEE 802.3, token ring / IEEE 802.5 and devices operating at this layer. (iii)To secure the addressing structure and the routing protocols at the network layer on the LAN. (iv) To have an identifiable secure and reliable transport mechanism between two communicating devices on the Local Area Network. (v) To provide a secure way for applications to translate data formats, encryption, decryption of the data traversing the network by using authentication methods, SSH, passwords, encryption just to mention but a few. (vi) To provide a secure platform where end users interact with application software by securing the application layer protocols such as HTTP, HTTPS, FTP, TELNET, POP3, FTP-DATA and more. Aim 2: To investigate and analyse the available tools and methods to secure a wired Local Area Network. Objectives (i) To prevent un-trusted traffic to access the network resources and secure gateways at the session layers to control the setup and teardown of sessions on the OSI model. Page 1-- 14 - of 105 (ii) To provide a cost effective but efficient and reliable Local Area Network. Personal and Academic objectives (i) To study, learn how to secure Local Area Networks, and the security threats faced by these Networks in a dynamic network technological environment. (ii) To learn how to organise my time meaningfully in order to achieve my intended goals in a given limited time. (iii)To learn the techniques, and approach on how to carry out a meaningful research on specific subject areas. (iv) To achieve skills on how to write a successful, well-structured report. (v) To improve my presentation skills, and my confidence in this area. (vi) To prepare myself for a future career in Computer Network Security, and further studies. 1.2 Methodology 1. By implementing the project in a secure physical environment of London Metropolitan University Cisco laboratory. It is well ventilated, with backup power supply, equipped with all the network devices I will use, and with controlled access to only authorised personnel. 2. The use of the designed logical topology shown in this report using GNS3 and packet tracer software to simulate the security configurations which are later on implemented in the laboratory. 3. To configure layer 2 switch port level security on the Cisco catalyst switches series 2960, and layer 3 switches series 3560. I will also configure storm controls, root and BPDU guard; protect switch ports by setting the maximum MAC address per port, shut down unused ports, and other more security configurations required. Page 1-- 15 - of 105 4. To configure VLANs on the Local Area Network, change the native VLAN , implement inter-VLAN routing on the layer 3 Cisco switches series 3560 provided in the laboratory, and enable routing too. 5. To configure access control lists on the Cisco Router firewall as a measure to filter traffic that is traversing the network fabric both from the external/public network such the internet to the DMZ, and from the private network (LAN) accessing the internet and the demilitarized zone (DMZ). 6. Provide a dynamic IP assignment mechanism by configuring a DHCP server on the LAN VLANs subnet. Configure DHCP snooping and enabling IP source guard on untrusted ports to prevent rogue DHCP on the network. 7. Use/ configure Authentication, Authorization, and Accounting (AAA) protocol on the Cisco routers and implement a locally-based user database to be authenticated in order to access network resources. 8. Use the Cisco Router Firewall with advanced security version IOS image to configure security for the LAN such as IPS, disabling unused router services, ensure minimum password lengthy, encryption of password, limit console and configure SSH on line VTY access. 9. Access control lists will be configured in order to control the in and out of traffic to different subnets of the LAN, and also filter out malicious packets trying to enter the private subnets. 10. Create a demilitarized zone (DMZ) with limited security compared to the private network subnet so as to enable external / internet host based users and company customers to access company web server, at the same time providing security for the systems residing within that zone. Page 1-- 16 - of 105 11. Use Network address translation with port overload (NAT/PAT) on the perimeter router. Host-based intrusion prevention software on end devices like PCs, and servers to provide in-depth checks of packets on layer 4 through to layer 7. 12. Structure the LAN in a hierarchal network design model i.e. core, distribution and access in order to provide redundancy, efficient, security, and reliability on the LAN. 13. Use 2 layer 2, and 2 layer 3 switches and a Cisco Router firewall ,perimeter firewall router, available in the our laboratory that support extra security configurations. 14. To configure context based access control, an inspection rule and an audit trail on the router to inspect the required protocols that pass in and out of the router firewall. This server as an added software firewall to the LAN. 15. Lastly but not the least, configure a syslog server on the network to truck and record the activities on the network for network administrative purposes. 1.3 Chapter Summary In this chapter the report introduces what the project is all about which is to secure a wired LAN. It also outlines the Aims and objectives of the project, outlines the methods that are employed to achieve the aims and objectives. For instance, to secure all the seven layers of the OSI model by using a variety of security configurations, devices, a good network design model and implementing the project to achieve the required results in the end. Page 1-- 17 - of 105 Chapter 2 : Literature Review 2.1 What is a LAN? Local area network comprises of computer devices that have got disks, processors and operating systems as a platform for software and other applications to run on, and they are interconnected in order to communicate with one another within a small geographical area usually a single building or group of buildings. Local Area Networks may also connect to other the network of server computers or mainframes with higher processing power and memory storage that can send information from the Local Area Network over telephone lines to public network. LANs include higher data-transfer rates, no need for a leased telecommunication lines. In the past ARCNET, Token Ring and other technology standards have been used but Ethernet over twisted pair cabling and Wi-Fi are the two most common technologies currently in use. LANs allow users to have isolated or separate offices but still be able to operate off the same system, as if they were all sitting around a single computer. This network can be easily installed simply, upgraded or expanded with little difficulty, even moved or rearranged without disruption. LANs have helped in the increased work place productivity, decreased the amount of paper used and the speeding up of the information flow. It’s important to mention that on the other hand LANs have also created additional work in terms of organization, maintenance, security and trouble-shooting. [5] Brief history In 1970s and 1980s after the development of both desk operating systems bases personal computers and Control Program for Microcomputers based personal computers meant that Page 2-- 18 - of 105 one site could have a big number of computers. A need developed to share disk space and laser printers due to the higher cost of these devices, and as a result the idea of LAN started to be developed. The introduction of the OSI model has enabled multi-vendors’ products that can be compatible and work together on one single machine. As a result, users were able to share resources regardless what operating system, network cards, cabling or protocols being used by different software running on the different machines but interconnected together within a LAN.[1] 2.2 What is LAN Security? LAN security involves the protecting of information, systems and the hardware that used to store, and transmit that information. It involves the steps taken to make sure that confidentiality, integrity, and availability of data / resources is achieved and maintained on the private or local area network from both form the internal and external networks threats. Network security solutions started coming up as the early 1960 but didn’t have a big impact due to the complexity of network security and the dynamic/ever changing nature of networks and most importantly companies, governments and other organisations had not realised the importance of network security on the company networks not until the 2000s. Since then network security become an integral part of the business networks and dedicated network security devices have emerged and there is a surge in the demand for network security professions. [5] Page 2-- 19 - of 105 2.2.1 The Evolution of LAN Security LAN security threats mostly target protocols and other technologies used on the local area network infrastructure. They fall into two types: Denial of service and spoofing attacks. The following shows the measures or Security technologies that have been developed over the last 13 year to mitigate LAN types of threats. In 1998 measures to Mitigate MAC Address Spoofing, MAC Address Table Overflow Attacks, and LAN Storm were released. In 2000 measures to Mitigate Root Bridge Spoofing and VLAN Attacks were released. In 2003 measures to Mitigate ARP Spoofing Attacks were released. Network Security is also achieved by the use of encryption and hashing mechanisms on the data as it traverses the network fabric. The following gives an outline of the cryptography security technology and their timeline: In 1993 Cisco GRE Tunnels was released. In 1996 Site-to-Site IPsec VPNs was released In 1999 Secure Socket Layer (SSH) was released In 2000 Multi-Protocol Label Switching (MPLS VPNs) was released In 2001 Remote-Access IPsec VPN was released In 2002 Dynamic Multipoint VPN was released In 2005 Secure Socket Layer (SSL) VPN was released. 2.2.2 LAN’s most vulnerable layer Basing on the OSI model research approach to find out which layer of the seven (7) layers is most vulnerable; I concluded that Layer 2 of the OSI model – (Data link layer) poses the most network security vulnerabilities on the LAN. The data link layer is divided into two sub-layer; Page 2-- 20 - of 105 logical link control and Media Access Control layer. Examples of the protocols that run on this layer are; FDDI, Ethernet, Token ring, MAC addresses, and the devices used on this layer are layer 2 and 3 LAN switch that perform switching and filtering of frames and packets basing on the MAC address and IP address if IP routing is enabled on the layer 3 switches. This makes layer 2 switches completely transparent to the network protocols and user applications. Unauthorised access to the layer 2 devices puts the whole network resources and performance at high security risk. In implementing this project I have seriously considered layer 3 switches. In addition, all protocols on other layers of the OSI model are secured to provide a holistic secure LAN environment for security threats. [3] 2.3 Common network threats 2.3.1 Reconnaissance attacks These types of attacks gather information on the network or targeted device’s security vulnerabilities that maybe exploited later by using tools like: [3] Packet sniffers, Ping sweeps, Port Scans, Internet information queries, 2.3.2 Denial-of-service This type of attack sends large numbers of requests over the network in order to cause the target devices to be overwhelmed causing them to run suboptimal and eventually becoming unavailable to serve its legitimate access and use. Examples of DOS attacks are:[3] Page 2-- 21 - of 105 Ping of Death, Smurf Attack, TCP SYN Flood attack Worm, DOS Attack Figure 3: DOS Attack 2.3.3 Access attacks These attacks are geared towards gaining access to the computer network and retrieve data, and escalate rights to resources. The following are the types of this form of attack: [3] Man-in-the-middle, Buffer overflow, Port Redirection, Password attacks, Trust exploitation Virus, Trojan horse, Page 2-- 22 - of 105 The following shows other categories of network security threats that can exploit network vulnerabilities on the LAN especially the LAN switches. MAC address spoofing, Spanning Tree Protocol manipulation attack, MAC address table overflows, LAN storms, VLAN attacks, 2.4 Chapter Summary This chapter is about what a LAN is, the meaning of LAN security, the evolution of LAN technology, the computer network threats, and the technology used to mitigate these threats in order to have a secured LAN. The chapter also out lines and defines the most common LAN security threats, points out and explains why layer 2 of the OSI model is the most Vulnerable layer. This means that on the LAN its imperatives to have this layer more adequately. Page 2-- 23 - of 105 Chapter 3 : Approach and Scope 3.1 Approach In the implementation of this project the network hierarchical design model is used to point out, identify, and subdivide the areas required on the LAN to be secured, how to secure them, and against what. The network hierarchical design model includes the Access, Distribution, and Core layers. On the Access Layer The strategy is to starts by securing the LAN’s Access layer devices which are interconnected with straight through, and cross over cables to endpoints such as: hosts, servers, and other devices that act as network clients, including non-endpoint devices like layer 2 switches. The following security configurations are made on these devices to mitigating attacks: [3] Switch port security, LAN storm controls, Limit one MAC address per port, Root guard, VLANs, BPDU’s Shutdown unused port and services, Enforce password encryption and minimum length, Mitigate STP manipulation, On the Distribution layer Page 3-- 24 - of 105 The using of Cisco layer 3 switches on this layer will support IP routing, switching, and the implementation of inter-VLAN routing on this level. A Cisco router firewall with an advances security version is configured with the following security configurations: [3] Access control lists, Cisco IOS IPS configurations, DMZ connection link to the DMZ Inspection rule, and context based access control list On the Core layer A Cisco router supporting advance security version is also used here to provide a connection to the ISP/internet (Public network). It is the network perimeter router onto which to configure NAT/PAT and is the network backbone fibre.[3] A Virtual LAN topology is used on Cisco packet tracer, and GNS3 software to simulate to secured LAN. Devices used on this software application are Cisco network devices such as router, and switches, running Cisco IOS images. 3.2 Project Scope The focus of this project is on securing Wired Local Area Network, the technology used to secure LANs, and the security threats that are faced on this type of networks. This report is not going to discuss the security of wireless LANs or even voice. It should be noted that Wide Area Networks are not dealt with here as well but only dealt with as a source of public traffic which should be controlled when accessing the LAN. During the project implementation phase, the report refers to the traffic from the WAN in this case the internet as untrusted traffic which should be controlled in and out going due to the network security threats that it poses to the wired LAN. Page 3-- 25 - of 105 The following are the assumptions held during the implementation of this project. I. II. It’s assumed that physical devices are in a secure university laboratory. It’s assumed that companies should not sit back after all the security measures /configurations are done on the network, but continually monitor, patch vulnerabilities by installing software patches and test the vulnerabilities of the LAN security. III. It is the assumption that the devices used and the configurations done are Cisco based configurations on Cisco devices. However, it should be noted that there is interoperability of this technology with other vendor’s devices. IV. It’s also assumed that the implemented security measures done in this project is acting as a microcosm setup that can be applied to a production network. The following are the risks that may jeopardise my project or the constraints, and the contingency plan in place. I. The limited access to the laboratories which is put in place by the university management has hampered a quick implementation and less time and experience on the real devices. II. Also the time allocated to the supervisors to be spending with us is really not enough, for instance they are only allowed 15 minutes to spend with us as far as the project is concerned. III. The unreliable software packages used like packet tracer and the lack of GNS3 Cisco IOS images act as constraints to doing my project. IV. The lack of network devices that I would have liked to implement on the security configurations is a big setback. Page 3-- 26 - of 105 3.3 I. Contingency Plans To use network software simulation packages like GNS3 and packet tracer 5.3.1 in case no access to laboratories granted. II. To negotiate more time to be allowed spend in the laboratory and also work very closely with my supervisor. III. To use of alternative devices available that performs more or less the same functions as the ones intended to use when designing the topology. 3.4 Scenario As my final year project am required to secure a wired LAN. A research by reading about the LAN security history, evolution of LAN security threats, types of threats, ways of mitigating these threats and practical implementation of a secured wired area network. With this background information and with a virtual topology is to be used to have a secure LAN. The topology includes the network devices that are used such as: the Cisco layer 2 catalysts switches series 2960, Cisco layer 3 catalyst switches series 3560, and as an alternative to the Cisco Adaptive security appliance (ASA) a Cisco Router firewall series 2811 version 12.2 is used. Cisco IOS IPS software is configured on the Router as a firewall. The project is implemented in the London Metropolitan University laboratory that has got Cisco networking devices mentioned above. In order to meet the specific requirements of the project, I have put an emphasis on securing protocols to be used on the LAN, layer 2 of the OSI model (Data link layer), and secure the internal/private network from un-trusted external traffic. Page 3-- 27 - of 105 3.5 Chapter Summary This chapter of the report is about the approach or style used to implement the project which is designed basing on the network hierarchal design model comprising of the three layers i.e. access, distribution, and core. The limits of the project are also outlined and shown to be covering only the securing of the Wired LAN, with contingency plans put in places such as use of different network simulation software like GNS3 in case there is no access to real/ physical network devices. Lastly but not the least, the scenario is given which is a requirement by London Metropolitan University as a client to secure a wired LAN. Page 3-- 28 - of 105 Chapter 4 : Practical simulation and results The following is the Figure showing a secured LAN topology. Secured Wired LAN Topology Figure 4: Secured LAN Topology Page 4-- 29 - of 105 The following table shows the Network devices and the cables that are used in the implementation phase of the project. Table 5: Types of Network devices used Table 6 Network Configuration Table: Routers Page 4-- 30 - of 105 Table 7 Network configuration table: Switches Table 8 End-system configuration table: End devices Page 4-- 31 - of 105 The following is the detailed discussion, illustration, explanation of the configurations and results achieved by the measures implemented to secure a wired LAN Cisco catalyst Switches. At this level the following are the security configurations that are configured on catalyst switches are as follows: 4.1 Security Configuration on Cisco catalyst Switches 4.1.2 Message of the day / login Banner A legal warning to anyone who gains unauthorised access to this switch that he/she will be prosecuted if unlawful access is attempted has been configured using the command line “Banner login $ ...$” in global configuration mode shown below.[2] ! --- Displays a login message L3switche1(config)#banner login $ This switch is the property of FDS Tech. Disconnect now if you are unauthorised to access. Any violations will be prosecuted. $ 4.1.3 Port level Port Security To prevent MAC table overflows and MAC Spoofing all access switch ports are allowed a maximum of one MAC address learned dynamically per each port from the list as determined by the Network Administrator. This is achieved by using command line “switchport portsecurity maximum 1”, and “switchport port-security mac-address sticky”. Any violation of this setting will trigger a shutdown of the port achieved by this command “switchport port-security violation shutdown”. For all the non-used access port are disabled by “shutdown” command. This port security measures will control unauthorised expansion of the network and prevent the port from forwarding frames with a source MAC address that is not assigned to it or is outside the group of the defined addresses on that port. The following below is the combination of the Port security configuration enabled only on access mode ports as mentioned above: [9] ,[4] Page 4-- 32 - of 105 ! ---- enable switch port security on access port L3swtich1(config)# interface fa0/1 L3swtich1(config-if)#switchport mode access L3swtich1(config-if)#switchport port-security L3swtich1(config-if)#switchport port-security maximum 1 L3swtich1(config-if)#switchport port-security violation shutdown L3swtich1(config-if)#switchport port-security mac-address security sticky ! --- Shutdown switch unused ports L3swtich1(config)#interface range fa0/1 - 24 L3swtich1(config-range-if)#shutdown L3swtich1(config-range-if)#end 4.1.4 BPDU Guard In order to prevent any rogue switch on the network by an attacker, BPDU guard is configured on user-facing ports with Port-Fast enabled. Using the command line “spanningtree bpduguard enable” in interface configuration mode. An unauthorized BPDUs received on ports with this feature enabled will be disabled thus eliminating invalid configurations from attackers. The following illustrates the configuration that enables BPDU guard configuration.[4] ! --- Enables bpdu guard on user-ports L3swtich1(config)#interface fa0/2 L3swtich1(config-if)#spanning-tree bpduguard enable And to verify that this configuration is done on the interface in question the following output displays this application combined with port security, and shutdown configurations output: !---- Output of switch port security configured on the port interface FastEthernet0/4 Page 4-- 33 - of 105 switchport access vlan 2 switchport mode access switchport port-security switchport port-security mac-address sticky switchport port-security mac-address sticky 0001.C9DA.0939 switchport port-security violation shutdown ! ---- Unused interfaced are shutdown interface FastEthernet0/5 switchport access vlan 99 shutdown ! To further enhance security on the switch to watch out for login attacks login access is configured to be disabled for 30 seconds if there is 3 failed logins within 10 seconds or less. This is shown by the configuration below, followed by its verification output. !---- Enables login to be disabled for 30 sec after three failed attempts within 10 sec L3swtich1 (config)#login block-for 30 attempts 3 with 10 L3swtich1(config)#login quiet-mode access-class 101 L3swtich1 (config)#login delay 3 L3swtich1 (config)#login on-failure L3swtich1 (config)#login on-failure log L3swtich1 (config)#login on-success log L3swtich1 (config)#end L3switch1# ! --- Verifies enhanced login security by use of the show login command L3switch1#sh login A default login delay of 1 second is applied. No Quiet-Mode access list has been configured. All failed login is logged. All successful login is logged. Page 4-- 34 - of 105 Router enabled to watch for login Attacks. If more than 3 login failures occur in 10 seconds or less, Logins will be disabled for 30 seconds. Router presently in Normal-Mode. Current Watch Window Time remaining: 7 seconds. Login failures for current window: 0. Total login failures: 0. L3switch1# 4.1.5 Storm Control To control broadcast, multicasts, or uncast of hostile packets flooding the LAN segments that degrades the network performance, a 50% suppression level is set on all ports connecting switches to switches (trunk ports) by using the following command line; “Storm- control broadcast level 50” in interface configuration mode.[4] The following configuration enables storm control on ports connecting switches to other switches (trunk ports). For example on L3switch1 switch it’s configured on fa0/2 ! ---- enables Storm control on the interface L3swtich1(config)#interface fa0/2 L3swtich1(config-if)#storm-control broadcast level 50 4.1.6 Root Guard This configuration helps to limit the switch ports on which the root bridge can be negotiated in switched networks. It is deployed on ports that connect to switches that should not be the root bridge. When the attacker sends out spoofed BPDUs in order to become a root bridge the switch receiving the BPDUs will ignore them and put the port in a root-inconsistent state, and the port will recover until the attacker stops sending BPDUs. Root guard is the best practice Page 4-- 35 - of 105 even though there may be a switch with a zero priority and a lower MAC address, and therefore a lower a lower bridge ID. The following configuration enables root guard:[4] ! --- Enable guard root feature on the interface fa0/1 L3swtich2(config)#interface fa0/4 L3swtich2(config-if)#spanning-tree guard root 4.1.7 Spanning Tree Protocol feature - PortFast To eliminate the vulnerability of a longer waiting time a port has to transition from blocking to forwarding state, the ports that are configured with portfast feature are access ports interfaces in order to shorten the waiting time the port has to transition from blocking to forwarding immediately bypassing listening and learning phases by using the following command on all switch access ports “spanning-tree portfast” The following configuration enables portfast on switch port in the access mode. This helps in mitigating STP attacks. ! --- Enable portfast feature on the interface L3swtich1(config)#interface fa0/2 L3swtich1(config-if)#spanning-tree portfast 4.1.8 Root Bridge Layer 3switch1 is configured as the primary root bridge to serve as a known reference point for all spanning-tree calculations to determine which redundant paths to block. Layer 3 switch2 set as secondary root. This is to eliminate any root bridge manipulation on the network. This is shown in the following configuration below that is configure on L3switch1 root bridge primary, and L3switch2 as a secondary root bridge:[4] ! --- Enables the switch to be Root Bridge (primary and secondary) Page 4-- 36 - of 105 L3swtich1(config)#spanning-tree vlan 1 root primary L3swtich2(config)#spanning-tree vlan 1 root secondary The following output verifies that L3switch1 is the root bridge. L3switch1#sh spanning-tree VLAN0001 Spanning tree enabled protocol ieee Root ID Priority 24577 Address 0001.4390.419A This bridge is the root Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec Bridge ID Priority 24577 (priority 24576 sys-id-ext 1) Address 0001.4390.419A Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec Aging Time 20 Interface Role Sts Cost Prio.Nbr Type ---------------- ---- --- --------- -------- -------------------------------Fa0/2 Desg FWD 19 128.2 P2p Fa0/4 Desg FWD 19 128.4 P2p 4.1.9 VLAN Trunk Security In order to mitigate VLAN hopping attacks, trunking is enabled on trunk ports, and the native VLAN 1 is changed to VLAN 99 on all trunk ports with “switchport trunk native vlan 99” to mitigate double tagging. To mitigate switch spoofing, auto trunking negotiations and DTP is disabled with “switchport trunk encapsulation dot1q”and enabled trunking manually with “switchport mode trunk”. The combined configuration on trunk ports of L3switch1, L3switch2, L2switch1, and L2switch2 devices is shown below.[4] ! – enable trunking on the link and sets native vlan 99 on it L3switch1(config)# interface fa0/1 Page 4-- 37 - of 105 L3switch1(config-if)#no shutdown L3switch1(config-if)#switchport mode trunk L3switch1(config-if)#switchport trunk encapsulation dot1q L3switch1(config-if)#switchport trunk native vlan 99 L3switch1(config-if)#switchport nonnegotiable ! --- Associate all other ports with the new native vlan 99 L3switch1(config-if)#interface range fa0/5 – 24 L3switch1(config-if)#interface range g0/1 - 2 L3switch1(config-if)#switchport access vlan 99 The following output verify of trunk link security as performed on L3switch2: 4.110 VLANs VLAN segmentations coupled with inter-VLAN routing implemented on L3switch1, and L3switch2 separate sensitive data departments such as the management, enhance LAN security, and mitigate broadcast storms propagating the entire network which can used as a tool by attackers to broadcast attacks to the entire network . The following configuration shows this implementation. ! --- creates VLAN 2, assign IP address, and subnet mask an interface L3switch1(config)# vlan 2 Page 4-- 38 - of 105 L3switch1(config-vlan)#exit L3switch1(config)#interface vlan 2 L3switch1(config-if)#ip address 192.168.20.1 255.255.255.0 ! --- Assigns an interface to a vlan and enables it too. L2switch1(config)# interface fa0/2 L2switch1(config-if)#switchport access vlan 2 L2switch1(config)#no shutdown 4.1.11 High Availability with Hot Standby Routing Protocol (HSRP) As it is one of objectives, Hot Standby Router Protocol (HSRP) is configured on the switches on the LAN to provide network with redundancy, and make sure that the traffic on the LAN is immediately and transparently recover from first hop failures in network edge devices. The configuration to achieve this is done on the L3switches (1 and 2) as shown in this configuration below: [11] On L3switch1 On L3switch2 interface Vlan3 ip address 192.168.30.3 255.255.255.0 standby 2 192.168.30.1 Standby 2 priority 160 Standby 2 preempt Standby 2 track fa0/3 65 Standby 2 authentication VLAN3 interface Vlan3 ip address 192.168.30.3 255.255.255.0 standby 2 192.168.30.1 Standby 2 preempt Standby 2 track fa0/3 65 Standby 2 authentication VLAN3 In this case the standby IP address is 192.168.30.1, and the HSRP will prefer the Layer 3 switch with a higher priority. Both switches have preempt to become the active switch when its priority is higher than all other HSRP configured switches in the hot standby group. Page 4-- 39 - of 105 4.2 Security Configuration to manage router security on Cisco Routers In order to Implementing Router security basing on the project design starts with securing the access to the router by following the planned steps below: 4.2.1 Message of the day / login Banner A legal warning to anyone who gains unauthorised access to this router that he/she will be prosecuted has been configured using the command line “Banner login $ ...$” in global configuration mode shown below: ! --- Displays a login message firewallRouter(config)#banner login $This router is the property of FDS Tech. Disconnect now if you are unauthorised to access it. Any violations will be prosecuted. $ 4.2.2 Password requirement A strong password is a fundamental element of controlling secure access to the router. For this reason password security is enhanced as follows: There is a minimum length of 10 characters required for all passwords used. This is configured from the global configuration mode. Also a configuration that encrypts all passwords that are configured on the router is done by use of “service password encryption” command line which prevents all plaintext passwords to be displayed in plain text or readable form. Also configured is an encrypted password requirement to access the global configuration mode by use of the “enable secret password”. Any authentication failures are configured to be logged on the syslog server. The combined configuration below illustrates the above: ! --- enables global encrypted password, sets minimum length password, encrypts all password configured and logs failed authentication Page 4-- 2 - of 105 firewallRouter(config)#enable secret cisco12345 firewallRouter(config)#security passwords min-length 10 firewallRouter(config)#service password-encryption firewallRouter(config)#security authentication failure rate 5 log 4.2.3 Secure remote administrative access to routers In addition, line console 0,VTY, and aux security is enhanced by setting passwords, exectimeout setting to close down the live connection on these ports if they are left idle, set authentication, authentication retries in case of any failures. To secure line VTY, the secure shell (SSH) transport mechanism is configured with the command line transport input ssh which enables the sending of data in an encrypted form instead of plain text as it is with telnet. To guard against both malicious attacks, and orphaned sessions caused by remote system crashes TCP keepalives is enabled on incoming connections using the service tcpkeepalives-in in global configuration command. For Aux line, a no password and login is configured in combination to secure this access port. The configuration on the line VTY, and console port is illustrated below respectively: [4] ! --- Enables password, and time out on console line firewallRouter(config)#line console 0 firewallRouter(config-line)#password cisco12345 firewallRouter(config-line)#exec-timeout 2 30 firewallRouter(config-line)#login firewallRouter(config-line)#logging synchronous Page 4-- 3 - of 105 The following output verifies that valid username and password should be used within a specific allowed time to have access. The output shows a failed login, login warning, timed out login and a display login log with the date and time when it happened. In this second part, valid username and password are verified, access granted to global and privileged configuration modes. Page 4-- 4 - of 105 The VTY line on the router is often used for remote access, and to enhance security for the data pass on this connection SSH input transport mechanism, exec-timeout, and authentication is configured as illustrated below: ! --- Creates domain name: FDS.com firewallRouter(config)# ip domain-name FDS.com firewallRouter(config)#crypto key generate rsa (generated 1024 bit RSA keys) firewallRouter(config)#username Admin1 secret Admin1pass ! --- Enables ssh, time out, and authentication retries on vty firewallRouter(config)#line vty 0 4 firewallRouter(config-line)#password cisco12345 firewallRouter(config)#no transport input firewallRouter(config)#transport input ssh firewallRouter(config)#ip ssh exec-timeout 2 30 firewallRouter(config)#ip ssh authentication-retries 3 firewallRouter(config)#login local firewallRouter(config)#exit ! ---- secure orphaned remote connections to the router firewallRouter(config)#service tcp-keepalives-in In order to verify the configuration of secure socket shell (SSH) on line VTY, a ping command using the DOS prompt on the management host which is on VLAN 2 to the router interfaces of the perimeter, and firewall router. A valid username and password are required to open the connection on the foreign host (router). An invalid login is also shown that causes the connection to be shut down. Page 4-- 5 - of 105 SSH connection to the firewall Router ! ---- Secure unused Aux ports firewallRouter(config)#line aux 0 firewallRouter(config-line)#no password firewallRouter(config-line)#login firewallRouter(config-line)#exit Page 4-- 6 - of 105 To further enhanced the router security to watch out for login attacks the logins are configured to be disabled for 30 seconds if there is 3 failed logins within 10 seconds or less. This is shown by the configuration below followed by its verification. !---- Enables login to be disabled for 30 sec after three failed attempts within 10 sec firewallRouter(config)#login block-for 30 attempts 3 with 10 firewallRouter(config)#login quiet-mode access-class 101 firewallRouter(config)#login delay 3 firewallRouter(config)#login on-failure firewallRouter(config)#login on-failure log firewallRouter(config)#login on-success log firewallRouter(config)#end The output below verifies the enhanced login security configuration that is applied on logins. It should be noted that this configuration is done on all the network devices used in the implementation phase. Enhanced login security Page 4-- 7 - of 105 4.2.4 Secure router network services In order to further secure the perimeter and firewall routers, some IP and network services that are not needed to support traffic and protocols on this network are disabled with a “no” command. Some of these services can present vulnerability in the router security that can be manipulated by an attacker to gain access to the LAN. The following configuration shows the sample configuration:[2],[4] This configuration disables IP services ! --- Disables router ip and network services PerimeterRouter(config)#no service udp-small-servers PerimeterRouter(config)#no service tcp-small-servers PerimeterRouter(config)#no ip bootp server PerimeterRouter(config)#no service finger PerimeterRouter(config)#no ip finger PerimeterRouter(config)#no ip http servers PerimeterRouter(config)#no snmp-servers The following disables network services that allow certain packets to pass through the router used by remoter users. ! --- Disables router services PerimeterRouter (config)#no cdp run PerimeterRouter(config)#no service config PerimeterRouter(config)#no ip source-route PerimeterRouter(config)#no ip classless ! --- Secures interfaces Page 4-- 8 - of 105 PerimeterRouter(config)#interface fa0/1 PerimeterRouter(config-if)#no ip directed-broadcast PerimeterRouter(config-if)#no ip proxy-arp PerimeterRouter(config-if)#shutdown 4.2.5 Configure Authentication, Accounting, Authorization protocol For more secured Administration management, a local authentication data base is configured on both perimeter and firewall routers, comprising of user account with a username, secret (encrypted) password, privilege level 15. As note, in a production environment the database can be widened as may be required. AAA protocol services are enabled with “aaa new-model” command line on both the perimeter and firewall routers to offer authentication, authorisation, and accounting of users accessing the network resources. AAA service is configured to use the local database by configuring default login authentication method list with the command line “aaa authentication login default local”. Configure local user database and enabling AAA on both routers. The following combined configuration illustrates the above: [4] ! --- Configures a local user and password firewallRouter(config)#username Admin1 privilege 15 secret Admin1pass !--- Enables aaa on the router firewallRouter(config)#aaa new-model firewallRouter(config)#aaa authentication login default local firewallRouter(config)#aaa authentication login TELNET-LOGIN local ! --- Applying the authentication method list to line console, and vty firewallRouter(config)#line console 0 firewallRouter(config-if)#login authentication default firewallRouter(config-if)#end Page 4-- 9 - of 105 firewallRouter(config)#line vty 0 4 firewallRouter(config)#login authentication TELNET-LOGIN firewallRouter(config)#end For the purposes of authentic time synchronisation on all the devices on the LAN, NTP authentication is configured on the Routers and switches, set a password, and a trusted key is as NTP client for the NTP server as mention above in the log router section. The following illustrates the above configuration: ! --- Enables ntp authentication, sets key, password for the router as ntp client firewallRouter(config)#ntp authenticate firewallRouter(config)#ntp authentication-key 1 md5 cisco12345 firewallRouter(config)#ntp trusted-key 1 firewallRouter(config)#ntp server "192.168.20.3" keyt 1 And the following output verifies firewall router as an NTP client for the NTP server IP address 192.168.20.3 having the synchronised time as well. 4.2.6 Log router activity The network activity logs are sent to syslog server acting as a central management station where a regularly review of all the logged activities is done. The activities configured to send messages to the syslog are for instance: the IPS inspections on every packet that enters or Page 4-- 10 - of 105 goes out of the private network on the router firewall, the login failures and successes extra. A time stamps setting is configured with Service timestamps command line. The routers, switches are configured as syslog/NTP clients, enabling them to synchronise their hardware clock as learned from the NTP server, and log massages with correct time stamps to the syslog server. These logs with the time stamps are used to determine whether the router has been compromised, allow the tracing of network attacks more credibly, and verify if the router is working properly. The above is achieved by the following configuration:[4] ! --- enables perimeter and firewall to log messages to the syslog server PerimeterRouter(config)#logging 192.168.20.3 firewallRouter(config)#logging 192.168.20.3 !--- enables routers to synchronise date and time with the NTP server firewallRouter(config)#ntp update-calendar firewallRouter(config)#service timestamps log datetime msec 4.2.7 Syslog server The syslog solution consists of the syslog server and client. A syslog server receives and store log messages, for instance the firewall logs; all the IPS process on the packets that pass in and out of the firewall, the audit session trails, login failures and successes, SSH sessions and many more activities on the network. The following screen shots shows the logged messages generated on the syslog server with the time of the activity happening, host name, and the message (what happened).[4] Page 4-- 11 - of 105 Syslog server Screen shot Page 4-- 12 - of 105 4.2.8 IPS software firewall The Cisco IOS intrusion prevention system is configured on the firewall router operating in the inline mode as a network based IPS implementation system. This is to inspect, analyse the content and payload of packets at layer 2 through layer 7, monitor ingress, and egress traffic in order to stop all malicious traffic. The IPS is configured to send log messages to the syslog server with “IP IPS notify log” and “logging syslog ip address” The following configuration illustrates IPS software configuration.[4] ! ---- Creates an IOS ips directory, storage location, ips rule, and enables logging firewallRouter#mkdir ipsdir firewallRouter(config)#ip ips config location flash:ipsdir Page 4-- 13 - of 105 firewallRouter(config)#ip ips name iosip firewallRouter(config)#ip ips notify log firewallRouter(config)#logging host 192.168.20.3 ! ---- Enable ips to use signature categories, first retire signature and un-retire all ios-ips basic firewallRouter(config)#ip ips signature-category firewallRouter(config-ips-category-action)#category all firewallRouter(config-ips-category-action)#retired true firewallRouter(config-ips-category-action)#exit firewallRouter(config-ips-category)#category ios_ips basic firewallRouter(config-ips-category-action)#retired false firewallRouter(config-ips-category-action)#exit firewallRouter(config-ips-category-action)#exit ! --- Apply the ips rule to the interface fa0/0, fa1/0, and fa1/1 firewallRouter(config)#interface fa0/0 firewallRouter(config-if)#ip ips iosips out firewallRouter(config-if)#ip iosips in !--- modify the event action of the signature to alert, and drop firewallRouter(config)#ip is signature-definition firewallRouter(config-sigdef)#signature 2004 0 firewallRouter(config-sigdef-sig)#status firewallRouter(config-sigdef-sig-status)#retired false firewallRouter(config-sigdef-sig-status)#enable true firewallRouter(config-sigdef-sig-status)#exit firewallRouter(config-sigdef-sig)#engine firewallRouter(config-sigdef-sig-engine)#event-action produced-alert firewallRouter(config-sigdef-sig-engine)#event-action deny-packet-inline firewallRouter(config-sigdef-sig-engine)#exit firewallRouter(config-sigdef-sig-engine)#exit Page 4-- 14 - of 105 The following screenshot shows ISP processing/ inspecting in-line all the packets from subnet 192.168.20.2 outbound through the firewall and the replies inbound through the firewall router back to the VLAN 2 (source). ISP processing/ inspecting in-line 4.2.9 Secure EIGRP routing protocol authentication In order to safe guard the information carried in the routing protocol, EIGRP routing protocol is configured authentication using message digest algorithm 5 (MD5). This algorithm will allow routers to compare signatures that should all be the same within the EIGRP area. The following command is used to configure routing protocol authentication for EIGRP on the perimeter router, and the same configuration is done on the firewall routers.[2] Page 4-- 15 - of 105 EIGRP authentication on the perimeter router ! --- Creating a key chain for the EIGRP routing protocol on the subnet on perimeter Router PermiterRouter(config)#router eigrp 1 PermiterRouter(config)#network 192.168.60.0 255.255.255.252 PermiterRouter(config)#exit PermiterRouter(config)#key chain EIGRP-KEY PermiterRouter(config-keychain)#key 1 PermiterRouter(config-keychain)#key-string cisco PermiterRouter(config-keychain)#exit PermiterRouter(config-keychain)#exit ! --- Enables and applying the authentication key chain on the interface PermiterRouter(config)#interface fa0/1 PermiterRouter(config-if)#ip authentication mode eigrp 1 md5 PermiterRouter(config-if)#ip authentication key-chain eigrp 1 EIGRP-KEY Configuring EIGRP authentication on the firewall router ! --- Creating a key chain for the EIGRP routing protocol on the subnet on firewall Router firewallRouter(config)#router eigrp 1 firewallRouter(config)#network 192.168.60.0 255.255.255.252 firewallRouter(config)#network 192.168.40.0 255.255.255.0 firewallRouter(config)#network 10.10.10.0 255.255.255.0 firewallRouter(config)#network 10.20.20.0 255.255.255.0 firewallRouter(config)#exit firewallRouter(config)#key chain EIGRP-KEY firewallRouter(config-keychain)#key 1 firewallRouter(config-keychain)#key-string cisco firewallRouter(config-keychain)#exit firewallRouter(config-keychain)#exit ! --- Enables and applying the authentication key chain on the interface firewallRouter(config)#interface fa0/1 Page 4-- 16 - of 105 firewallRouter(config-if)#ip authentication mode eigrp 1 md5 firewallRouter(config-if)#ip authentication key-chain eigrp 1 EIGRP-KEY 4.2.10 Securing the router IOS image on perimeter, and firewall routers In order to have the router IOS images secured a secure boot-image command is used to enable IOS image resilience on the router. Also to secure the boot configurations the secure boot-config command is used to secure the boot configuration. The following configuration illustrates the above configuration.[4] ! --firewallRouter(config)#secure boot-image firewallRouter(config)#secure boot-config IOS image resilience verification. 4.2.11 Access Lists I have configured extended access control list on the firewall router to filtering traffic from the internet/ISP web-server accessing the internal/private web server on the 192.168.40.0 subnet which is the DMZ zone on the private network, and to limit public initiated connection Page 4-- 17 - of 105 access the internal/private 192.168.20.0 and 192.168.30.0 subnets (VLANs 2 and 3). I have also used ACL to allow internal/private users to access selected internet services like web browsing, FTP, FTP-data, pop3, SMTP, SNMP, https, and only to allow replies for only those established connections from the private network by use of the “established” command. an inspection rule is created by use of context-based access control (CBAC) to inspect the traffic allowed in and out of the outside interface of the firewall as shown in the configuration, and verified by the ping command. [2] Access control list configurations The following access-list 111 deny all packets containing IP address from any local address 127.0.0.0/8, IP multicast range, private 172.16.0.0 in order to Mitigate IP address spoofing with ACL and its applied on the fa0/1 192.168.60.1 inbound the firewall router. ! ----deny all packets containing IP address 127.0.0.0/8, private 172.16.0.0, IP multicast range firewallRouter(config)#access-list 111 deny ip 127.0.0.0 0.255.255.255 any log firewallRouter(config)#access-list 111 deny ip 224.0.0.0 15.255.255.255 any log firewallRouter(config)#access-list 111 deny ip host 255.255.255.255 any log firewallRouter(config)#access-list 111 deny ip 172.16.0.0 0.15.255.255 any log firewallRouter(config)#access-list 111 permit ip any 192.168.0.0 0.0.255.255 ! --- applied on the fa0/1 192.168.60.1 inbound firewallRouter(config)#interface fa0/1 firewallRouter(config-if)#ip access-group 111 in ! ---The following access-list 107 permits all the required ICMP messages for proper network operations outbound to the fa0/ 1 ip 192.168.60.1 on the firewall router while denying all others. firewallRouter(config)#access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 echo-reply firewallRouter(config)#access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 parameter-problem Page 4-- 18 - of 105 firewallRouter(config)#access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 packet -too-big firewallRouter(config)#access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 source-quench firewallRouter(config)#access-list 107 deny icmp any any log firewallRouter(config)#interface fa0/1 firewallRouter(config-if)#ip access-group 107 out The following access-list 103 and 104 is configured on interface fa0/0 ip10.10.10.2 of the firewall router for VLAN 2 traffic and it permits TCP, IP, ICMP and allow replies for only the connections that are established form the private subnet of VLAN 2 (192.168.20.0). firewallRouter(config)#access-list 103 permit icmp 209.165.200.0 0.0.0.255 192.168.20.0 0.0.0.255 firewallRouter(config)#access-list 103 permit ip 192.168.60.0 0.0.0.255 192.168.20.0 0.0.0.255 firewallRouter(config)#access-list 103 permit ip 192.168.40.0 0.0.0.255 192.168.20.0 0.0.0.255 firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq www firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq ftp firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq 20 firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq 443 firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq smtp firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq pop3 firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 192.168.60.2 eq 22 Page 4-- 19 - of 105 firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 192.168.60.2 eq 23 firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 192.168.60.2 eq 161 firewallRouter(config)#access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 192.168.60.2 eq 53 firewallRouter(config)#access-list 104 permit icmp 209.165.200.0 0.0.0.255 192.168.20.0 0.0.0.255 established firewallRouter(config)#int fa0/0 firewallRouter(config-if)#ip access-group 103 out firewallRouter(config-if)#ip access-group 104 in ! ---The following access-list 105 and 106 is configured on interface fa1/1 ip10.20.20.2 of the firewall router for vlan 3 traffic and it permits tcp, ip, icmp and allow replies for only the connections that are established form the private subnet of vlan 3 (192.168.30.0). firewallRouter(config)#access-list 105 permit icmp 209.165.200.0 0.0.0.255 192.168.30.0 0.0.0.255 firewallRouter(config)#access-list 105 permit ip 192.168.60.0 0.0.0.255 192.168.30.0 0.0.0.255 firewallRouter(config)#access-list 105 permit ip 192.168.40.0 0.0.0.255 192.168.30.0 0.0.0.255 firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq www firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq ftp firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq 20 firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq 443 firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq smtp firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq pop3 firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 192.168.60.2 eq 22 firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 192.168.60.2 eq 23 Page 4-- 20 - of 105 firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 192.168.60.2 eq 161 firewallRouter(config)#access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 192.168.60.2 eq 53 firewallRouter(config)#access-list 106 permit icmp 209.165.200.0 0.0.0.255 192.168.30.0 0.0.0.255 established firewallRouter(config)#int fa1/1 firewallRouter(config-if)#ip access-group 105 out firewallRouter(config-if)#ip access-group 106 in 4.3 Simulation and verification of user access to different Subnets of the LAN/ Internet The following screen shot shows using a ping command to verify that the private/internal VLANs users (on network 192.168.20.0, and 192.168.30.0) are being able to access the internet but only allowing required or established reply(only initiated internally). This is enforced by the access control list as shown in the access control list section above. The ping command is executed from VLAN 2 and VLAN 3 as shown in the two screen shots below: Successfully ping to the ISP/Internet ping form PCO host on VLAN 3 Page 4-- 21 - of 105 Successfully ping to the ISP/Internet form PCO host on VLAN 2 Page 4-- 22 - of 105 Public users access DMZ web server but not private VLAN subnets The following screen shot shows using a ping command to verify that the public users (on the 209.165.200.0 network) are only allowed to access the DMZ web server subnet (on the internal network 192.168.40.0) but not the private network. This is enforced by the access control list as shown in the access control list section above.[7] ISP/WEB server pings successfully the Company DMZ Web server Page 4-- 23 - of 105 ISP/WEB server pings unsuccessfully the private VLAN 2, and 3 subnets Private subnets (VLAN 2 & 3) have inter- VLAN routing and can access to DMZ Also the following ping command output verifies that the internal private subnets (192.168.20.0 and 192.168.30.0) on different VLANs 2, 3 have connectivity with the DMZ subnet (192.168.40.0) for the purposed of file and data access on the server firm. This is enforced by the access control list as shown in the access control list section above. Page 4-- 24 - of 105 Ping Form PCO host on VLAN 2 to the DMZ web server and Host on VLAN 3 successfully Page 4-- 25 - of 105 Ping Form PC1 host on VLAN 3 to the DMZ web server and Host on VLAN 2 successfully 4.4 Context-based access control (CBAC) inspection rule The following configuration is done for the inspection rule on the firewall router. firewallRouter(config)#ip access-list extended out-in firewallRouter(config)#permit ip any any firewallRouter(config)#exit ! --firewallRouter(config)#interface fa0/1 firewallRouter(config-if)#ip access-group out-in in ! --firewallRouter(config)#ip inspect name in-out-in icmp Page 4-- 26 - of 105 firewallRouter(config)#ip inspect name in-out-in http firewallRouter(config)#ip inspect name in-out-in telnet firewallRouter(config)#ip inspect name in-out-in udp firewallRouter(config)#ip inspect name in-out-in tcp ! --firewallRouter(config)#ip inspect audit-trail firewallRouter(config)#service timestamps debug datetime msec firewallRouter(config)#logging host 192.168.20.3 ! --firewallRouter(config)#interface fa0/1 firewallRouter(config-if)#ip inspect in-out-in out The screen shot below shows that the inspection rule is enabled to inspection telnet, TCP, HTTP, UDP protocols in and out through the firewall router. 4.4.1 Inspection rule/Audit-trail enabled screen shot Page 4-- 27 - of 105 4.4.2 Simulation of inspection /audit-trail process 4.5 Port Address Translation PAT / NAT Overload I have configured NAT/PAT overload on the perimeter router using this command line “ip nat inside source list 1 interface overload”. NAT overload has only one publically exposed IP address. Incoming packets from the public network are routed to their private destination on the private network by referring to the NAT overload perimeter router that trucks public to private port pairs. In addition to the above I have used a static route “ip nat inside source static local-ip global ip”, and the access control list discussed in the next subheading, allow the public users/internet users to access only the company/private web server in the DMZ zone. At the same time allowing private network users to access the internet without exposing their private host IP addresses. By this configuration I also achieve the following:[2] Page 4-- 28 - of 105 Protect the private network address being advertised to the public thus securing the internal network. Provide consistency for internal network addressing scheme by use of private addresses and NAT enabling support of new public addressing scheme without a need to change the inside/internal client address. The configuration illustrates the complete command line configuration done on the perimeter router, followed by the Nat translations performed by these configurations on the perimeter router, and lastly the debug output of the Nat process on this same router. NAT/PAT configuration ! --- Establishes a static route to the DMZ web server perimiterRouter(config)#ip nat inside source static 192.168.40.2 255.255.255.0 ! --- Identify which addresses are eligible to be translated perimiterRouter(config)# access-list 1 permit 192.168.0.0 0.0.255.255 ! --- Identify the outside interface fa0/1 as the inside global address to be overloaded perimiterRouter(config)#ip nat inside source list 1 interface fa0/1 overload !--- Identify the inside NAT interface perimiterRouter(config)#interface fa0/0 perimiterRouter(config-if)#ip nat inside ! --- Identify the outside NAT interface perimiterRouter(config)#interface fa0/1 perimiterRouter(config)#ip nat outside Verification of Nat translations, debug, statistics, ! --- This output generated before any translations done perimeterRouter#sh ip nat translations Pro Inside global Inside local --- 209.165.200.226 192.168.40.2 Outside local --- Outside global --Page 4-- 29 - of 105 ! --- After the translation initiated by the ping command perimeterRouter#sh ip nat translations Pro Inside global Inside local Outside local Outside global icmp 209.165.200.225:37192.168.20.2:37 209.165.200.226:37 209.165.200.226:37 icmp 209.165.200.225:38192.168.20.2:38 209.165.200.226:38 209.165.200.226:38 icmp 209.165.200.225:39192.168.20.2:39 209.165.200.226:39 209.165.200.226:39 icmp 209.165.200.225:40192.168.20.2:40 209.165.200.226:40 209.165.200.226:40 --- 209.165.200.226 192.168.40.2 --- --- ! ---- Display live NAT translations as the happen on the PAT/NAT router IP NAT debugging is on perimeterRouter# *Dec 07, 12:35:23.3535: NAT: s=192.168.20.2->209.165.200.225, d=209.165.200.226 [79] *Dec 07, 12:35:23.3535: NAT*: s=209.165.200.226, d=209.165.200.225->192.168.20.2 [195] perimeterRouter# *Dec 07, 12:35:25.3535: NAT: s=192.168.20.2->209.165.200.225, d=209.165.200.226 [80] *Dec 07, 12:35:25.3535: NAT*: s=209.165.200.226, d=209.165.200.225->192.168.20.2 [196] perimeterRouter# *Dec 07, 12:35:26.3535: NAT: s=192.168.20.2->209.165.200.225, d=209.165.200.226 [81] *Dec 07, 12:35:26.3535: NAT*: s=209.165.200.226, d=209.165.200.225->192.168.20.2 [197] perimeterRouter# *Dec 07, 12:35:26.3535: NAT: expiring 209.165.200.225 (192.168.20.2) icmp 37 (37) perimeterRouter# *Dec 07, 12:35:27.3535: NAT: s=192.168.20.2->209.165.200.225, d=209.165.200.226 [82] *Dec 07, 12:35:27.3535: NAT*: s=209.165.200.226, d=209.165.200.225->192.168.20.2 [198] perimeterRouter# *Dec 07, 12:35:27.3535: NAT: expiring 209.165.200.225 (192.168.20.2) icmp 38 (38) Page 4-- 30 - of 105 perimeterRouter# *Dec 07, 12:35:28.3535: NAT: expiring 209.165.200.225 (192.168.20.2) icmp 39 (39) perimeterRouter# *Dec 07, 12:35:29.3535: NAT: expiring 209.165.200.225 (192.168.20.2) icmp 40 (40) perimeterRouter#un all All possible debugging has been turned off perimeterRouter# ! ---- Displays the NAT statistics after any translations perimeterRouter#sh ip nat statistics Total translations: 5 (1 static, 4 dynamic, 4 extended) Outside Interfaces: FastEthernet0/1 Inside Interfaces: FastEthernet0/0 Hits: 61 Misses: 154 Expired translations: 85 Dynamic mappings: perimeterRouter# 4.6 DHCP implementation The implementation of DHCP is configured on the layer 3 switches, 2 DHCP pools are configured one for VLAN 2 on L3switch1 and the other VLAN 3 on L3switch2 dynamically offers to the network devices IP address from a pool of allowed configured IP address and excluding those that are required for security purposes as maybe required. This configuration below achieved the above: [2], [6] ! --- Two IP addresses for the default gateway and the syslog server/ management are excluded from the pool of addresses. L3switch1(config)#ip dhcp excluded-address 192.168.20.1 L3switch1(config)#ip dhcp excluded-address 192.168.20.3 Page 4-- 31 - of 105 ! --- Creates the IP pool name on the DHCP server L3switch1(config)#ip dhcp pool LAN-POOL-1 L3switch1(dhcp-config)#network 192.168.20.0 255.255.255.0 L3switch1(dhcp-config)#default-router 192.168.20.1 L3switch1(dhcp-config)#end 4.6.1 DHCP Snooping To protect the Network against rogue DHCP servers, DHCP snooping is implemented to create a logical firewall between un-trusted hosts and DHCP servers. The following is the illustration of the configuration that achieves the above that is configured on both DHCP servers on the secured wired LAN:[6] !---Enables DHCP snooping on the switch L3swtich1(config)#ip dhcp snooping !--- DHCP snooping is not active until DHCP snooping is enabled on a VLAN. L3swtich1 (config)#ip dhcp snooping vlan 2 !--- Configures the interface connected to the DHCP server as trusted. L3swtich1(config)#interface fastEthernet 0/2 L3swtich1(config-if)#ip dhcp snooping trust 4.6.2 Dynamic ARP inspection To make sure that valid and only Valid ARP packet requests and responses are forwarded by performing an IP-to-MAC mapping, the dynamic ARP inspection feature is configured to achieve this. The following configuration is configured on both L3switches (1 and 2) DCHP servers VLANS and applied on the interface as shown below:[6] !--- Enables dynamic ARP inspection on the VLAN L3swtich1(config)#ip arp inspection vlan 2 Page 4-- 32 - of 105 !--- Configures the interface connected to the DHCP server as trusted. L3swtich1(config)#interface fastEthernet 0/2 L3swtich1(config-if)#ip arp inspection trust 4.6.3 IP source guard This feature is configured to restrict IP traffic on un-trusted layer 2 ports by filtering traffic based on DHCP snooping binding database or manually configuring IP source binding as result it will prevent IP spoofing attacks when hosts tries to spoof or use IP address of another host. The following configuration is configured on both L3switches (1 and 2) DCHP servers VLANS and applied on the interface as shown below:[6] !--- Enables IP source guard with source IP filtering L3swtich1(config)#interface fastEthernet 0/2 L3swtich1(config-if)#ip verify source 4.7 Chapter Summary This chapter has discussed and show the heart and soul of the project by showing the steps taken and how they are done in order to have a secured wired LAN. Among the security measures taken are to secure the layer 2 devices like the switches, layer 3 switches and routers , all the way through layer 7 of the OSI model. The examples of some of the configures security measures include securing Device access line and ports, configures passwords, Access control lists, firewalls, VLANs, NAT, Provide a reliable addressing scheme, configuring of the DMZ, creating logs, and many more. Page 4-- 33 - of 105 Chapter 5 : Critical appraisal, recommendations and suggestions for further work 5.1 Critical appraisal The following is the critical appraisal for the meaning of the results from the implementation of the project. 1. The VLAN implementation on the LAN is used to achieve the following objectives as shown below: Security: VLANs have been configured to separate sensitive data departments, for example the management department VLAN 2 , and VLAN 3 human resource form the rest of the network subnets. Broadcast storm mitigation: By segmenting the network into VLANs such as 2, and 3, it is made it possible to manage and confine the broadcast storms to devices within specific VLANs other than propagating throughout the entire network. Cost reduction: VLANs don’t need very expensive network upgrades and its more efficient use of the existing bandwidth and uplink. Higher performance: The VLANs implementation here has helped to divide a flat layer 2 network into multiple logical workgroups (broadcast domain) thus reducing unwanted traffic on the network and boost performance. 2. By using port address translation (PAT/NAT) it is been possible to separate the private network by using the class C IP address of 192.168.0.0- 192.168.255.255 and class A 10.0.0.0 -10.255.255.255 from the public/ internet address. PAT prevents the private Page 5-- 34 - of 105 IP addresses to be advertised on the public network. As a result secure the private network and improve the LANs addressing scheme. 3. Configuring username, password with a minimum length of 10 characters both alphabetic and numerical, encryption and a legal warning for any unauthorised access on the network devices such as the switches and routers enhances their security. Valid login credentials will have to be entered to have access. Any plain text passwords will be ciphered. 4. The configuration of the context based access control inspection rule helps to inspect and provide an audit trail for the protocols which are allowed in the private network through the firewall router. This rule is a Cisco software firewall that is configured in this case to enhanced inspection of packets through the firewall router. For instance, it is configured to inspect http, telnet, UDP to mention but a few. 5. The use of the hierarchal network design model approach to secure the LAN, it is made it possible to have a step by step approach starting from: The access layer with tool like port security, root guard, storm controls, BPDU guard, SSH transport input, VLAN trunking and disabling of the DTP, shut down shut down of all unused ports and services, primary root bridge, encryption of all passwords used, timeout on console, VTY are configured. On the distribution layer, in order to manage and control traffic in and out of different subnets to provide security, minimise the effects of any security breach across the network, Cisco IOS firewall, access control lists, and the secured EIGRP routing protocol are configured. Page 5-- 35 - of 105 The core layer is dedicated to transport traffic with PAT translations performed on in and out traffic on the network. In addition, all other required basic security configuration is done on the routers used at this level: for example, minimum length password requirement on all access lines, disable unused ports and services, to mention but a few. 6. Access control lists have enabled the control of traffic that is: allowed to in and out of the private network subnet to the public network, and the DMZ, For instance, the public network users are not allowed access to the private network but allowed access to the DMZ zone, private network users are allowed access to the internet but for only limited services such as www, ftp, ftp-data, amongst others and only allow replies to those connections initiated from the private VLAN subnets. 7. The router firewall is configured with the Cisco IOS IPS that assessing, tracks, and analyses any risk of the packets in-line going in and out on all interface connected to this firewall router. If the IPS detects unwanted security risk packets it drops the packet. 8. Authentication, authorisation and accounting protocol (AAA) is enabled to secure the access to network resources by limiting access to only those who have the right to access, and are what they say to be. This is achieved with configuring of a user’s database locally that contains the usernames, passwords, and the privileges’ granted, against which every login is checked / authenticated, authorised to access the resources in question and also provide the accountability for that login and logging any access to resources. Page 5-- 36 - of 105 9. The information that is logged on the syslog server from the managed devices helps to achieve the following: To have an insight into the nature of the attacks towards the LAN, To use the logged information for the purposes of troubleshooting, To have a clear picture of events correlation information of the multiple network devices (that is to say, the relationship between events occurring on different systems). 10. Lastly but not the least, the DMZ segment is offering the public users, (our customers) the access to the resources such the company web server within a lower level security zone and at the same time protecting our private subnets. It’s one way of providing a window into the company dealings. 5.2 Suggestions for Further work 5.2.1 Backup IOS software images In order to manage Cisco IOS images running on the Cisco devices on the LAN, and safeguard them against attacks that can put the router configurations or the operating systems at risk. Administrators should save, backup, restore configuration, and IOS images. For this reason, therefore, the report recommends IOS software images, configuration files, and revision level of Cisco IOS images files that be maintained, and should be copied on the central TFTP server as a backup.[4] Page 5-- 37 - of 105 5.2.2 Continuous network monitoring It is critical to verify that the counter measures are in place are working properly. To assist with the compliance of the company security policy, the Network Security Wheel that defines a continuous process of secure, monitor, test, and improve should be followed in order to achieve continuous security on the LAN.[2] 5.3 Recommendations 5.3.1 Virtual private network technology (VPN) As the company grows and it start having remote worker/ branches/ or teleworkers, or even within the LAN, VPN technology can be of great advantage to increase and maintain greater security on sensitive company data/ transactions.[2] 5.3.2 Cisco Adaptive Security Appliance (ASA) firewall As proposed in the interim report, the report recommends the use of the Cisco security appliance (ASA) as a modern up-to-date firewall router. It is modelled on a self-defending Network (SDN) principle having several protective and integrated layers such as firewalls, intrusion prevention, and anomaly mitigation. Cisco Adaptive Security Appliance provides state-full application inspection of all application and services traffic based on explicitly preconfigured polices and rules. This inspection keeps tracks of every connection passing through the interface making sure that they are valid connections, and monitors established, closed, resets or negotiates state of connections, and maintains a database with this information in a stable table. ASA provides intelligent threat defence and secure communications services that stop attacks before they affect business Page 5-- 38 - of 105 continuity. Packet headers and contents of the packets are examined through up to the application layer. [3] Cisco Adaptive Security Appliance can be configured to inspect the following protocols: Extended Simple Mail Transfer Protocol (ESMTP) This restricts the type of SMTP commands that can pass through Cisco ASA. Skinny Protocol (Simple Client Control Protocol -SCCP) To support a unified wired LAN (Audio and data), the Cisco ASA offers the ability to inspect skinny transactions using this protocol that making the wired LAN a secure unified network. Simple Network Management Protocol (SNMP) The Cisco ASA can be configured to deny traffic based on the SNMP packet versions. Early versions are less secure. This practice can be incorporated as a security policy thus making the LAN more secure. Trivial File Transfer Protocol (TFTP) Cisco ASA TFTP application inspection is used to: (i) Prevent hosts from opening invalid connections, and (ii) Enforces the creation of a secondary channel initiated from the server thus restricting TFTP clients creating them. Real Time Streaming Protocol (RSTP) Cisco ASA supports the inspection of this protocol which is a multimedia streaming protocol as stipulated in RFC 2326 which could have disastrous embedded codes. This protocol mostly use TCP port 554 application, and the applications that use RSTP are Real Audio, Apple Quick Time, Real Player, Cisco IPTV. [3] Page 5-- 39 - of 105 5.4 ASA Intrusion detection and Prevention system Even though I have configures the Cisco IOS IPS in my project. I strongly recommend the implement Inline Intrusion prevention system on the Cisco ASA which is more secure than promiscuous mode but affects overall throughput. In this case the Cisco ASA will direct all traffic to the Adaptive Inspection Prevention Security Service Module for process and analyse, dropping any malicious packets, generate an alarm, or reset connection, before it is forwarded by the ASA. This will mitigate network attacks such as Denial of Service (i.e. TCP sync flood attacks, land attacks, Smurf attacks), Distributed Denial of Service, Session Hijacking (i.e. Man- in-the- Middle).[3] 5.5 DNS Implementation on the Cisco ASA Traditionally, DNS queries will require not only relying on generic UDP handling based on activity timeouts. With the Cisco Adaptive Security Appliance, UDP connections associated with DNS queries and responses are torn down as soon as a reply to a DNS query has been received (like the DNS guard feature in Cisco PIX firewall). Cisco ASA DNS will further provide more security measures such as:[3] Guarantees that the ID’s of the DNS reply matches ID’s of DNS query, Allows translation of DNS packets using NAT, Reassembles DNS packets to verify its length which has a maximum of 65,553 bytes making any packets larger than that to be dropped. 5.6 Host- Based Intrusion Detection Systems Since I did implement my project in controlled environment I didn’t have the opportunity to implement Cisco Security Agent software firewall. However, I recommend this host based Page 5-- 40 - of 105 firewall should be installed on individual servers or client machines to safeguard critical computer systems and will intercept any attacks.[3] 5.7 Chapter Summary In this chapter of the report an in-depth critical appraisal is discussed showing how the methods have been used to achieve the required results and the meaning of this result. Also the recommendations are given for future considerations such as the use of the Cisco Adaptive Security Appliance, and suggestions of further work like bucking up IOS configurations and continuous monitoring of the LAN’s security Page 5-- 41 - of 105 Chapter 6 : Conclusion Over the course of implementing the project the main goal is to ultimately secure a wired Local Area Network. The implementation phase project carried out in a secured London Metropolitan University laboratory enabled the achievement of the objective to secure the physical layer (layer 1) of the OSI mode. Through the research, simulations, and analysis, it’s been possible to have a secure layer 2 to through layer 7 of the OSI model layers with the necessary security configuration such as switch port security, shut down unused ports and services, change native VLAN from 1 to any other number, IP source guard, DHCP Snooping, dynamic ARP inspections, VLAN segmentation, password requirements. Just to mention but a few. In addition, by using Network address translation / port address translation (NAT/PAT) technology, access list control, and configuration of a demilitarized zone (DMZ) I have managed to secure the private network from receiving untrusted traffic from the public network/internet. I have achieved redundancy, reliability on the network by having extra backup trunk links and using the 3 layered network design that includes access, distribution, and core. The implementation of VLANs and inter-VLAN routing improves for security, reliability, and it’s cost effective. It is required for companies, governments and non-governments organisations, schools, and homes put in place Network Security Policies which acts as a framework and guideline to be followed by the network users in order to achieved continuously secure network. Network Security Professionals should be employed and continually install software patches, monitor, and test the LAN security. They should also keep learning and sharing information about the new security threats. Having said that it should be noted that over the last 20 years companies have come to realise a great need to secure their LANs due to the increasing dynamic network security threats that has resulted in loss of data, leakage of confidential information, political Page 6-- 42 - of 105 collisions between countries, identity loss which resulted in big financial losses, damaged company brands, and individuals. As a result they are committing a lot of money to maintain a secure LAN environment so as to achieve confidentiality, Integrity, and availability on their networks. I have learnt a lot about the network security threats and the technology to mitigate these threats in order to have a secured wired LAN. Also learnt; how to organise meaningfully my time in order to achieve my intended goals in a given limited time, the techniques and approach on how to carry out a meaningful research on specific topics. And also gained skills in poster presentation, writing a well-structured report, presentation skills, increased my confidence, and prepared myself for a future carrier as a computer network security professional. Page 6-- 43 - of 105 References: 1. Local Area Networks (LANS). (2011, 12 14). Retrieved 10 20, 2011, from www.referenceforbusiness.com: http://www.referenceforbusiness.com/small/IncMail/Local-Area-Networks-LANS.html 2. Bob Vachon, Rick Graziani. (2008). Accessing the WAN. Indianapolis: Cisco Press. 3. Hucaby. (2005). Cisco ASA and PIX Firewall Handbook. Indianapolis: Cisco Press. 4. Micheal Watkins, Kevin Wallace,. (2010). CCNA Security . Indianapolis: Cisco Press. 5. orbit-computer-solutions. (2011, 12 14). Free Computer Training and Home Networking Tutorials. Retrieved 11 25, 2011, from www.orbit-computer-solutions.com: http://www.orbit-computer-solutions.com/ 6. press, c. (2011, 12 14). Catalyst 6500 Release 12.2SXF and Rebuilds Software Configuration Guide - DHCP Snooping. Retrieved 10 29, 2011, from cisco.com: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SXF/native/confi guration/guide/snoodhcp.html 7. Press, C. (2011, 12 14). Demilitarized Zone (DMZ) Port - Cisco Systems:. Retrieved 10 22, 2011, from cisco.com: http://www.cisco.com/en/US/docs/ios/12_3/12_3x/12_3xr/dmz_port.html#wp1046651 8. Press, C. (2011, 12 14). Ethernet-to-the-Factory 1.2 Design and Implementation Guide Implementation of Security [Design Zone for Manufacturing] - Cisco Systems:. Retrieved 12 01, 2011, from cisco.com: http://www.cisco.com/en/US/docs/solutions/Verticals/EttF/ch5_EttF.html#wp103160 Page 6-- 44 - of 105 9. Press, C. (2011, 12 14). Layer 2 Security Features on Cisco Catalyst Layer 3 Fixed Configuration Switches Configuration Example - Cisco Systems:. Retrieved 11 13, 2011, from cisco.com: http://www.cisco.com/en/US/products/hw/switches/ps5023/products_configuration_ex ample09186a00807c4101.shtml#ipsourceguard 10. Rick Graziani, Allan Johnson. (2009). Routing Protocols and Concepts. Indianapolis: Cisco Press. 11.http://www.cisco.com/en/US/tech/tk648/tk362/technologies_tech_note09186a0080094afd.sht ml Page 6-- 45 - of 105 Appendix A: A.1 Device documentation with a show run command A.1.1 Secured Perimeter Router documentation perimeterRouter#sh run Building configuration... Current configuration : 2397 bytes ! version 12.4 service tcp-keepalives-in service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname perimeter ! boot-start-marker boot-end-marker ! security authentication failure rate 5 log security passwords min-length 10 enable secret 5 $1$CuvP$QG5GryTJC0z6DJsTYuF3E0 ! aaa new-model ! aaa authentication login default local enable aaa authentication login TELNET_LOGIN local ! aaa session-id common memory-size iomem 15 no ip source-route ip cef ! no ip bootp server no ip domain lookup ip domain name FDS.com ip auth-proxy max-nodata-conns 3 ip admission max-nodata-conns 3 login block-for 30 attempts 3 within 10 login delay 3 login quiet-mode access-class 101 login on-failure log login on-success log ! Page 6-- 46 - of 105 voice-card 0 ! key chain EIGRP-KEY key 1 key-string 7 1511021F0725 ! username Admin1 privilege 15 secret 5 $1$mERr$ZR1fkPDr3Z4icChNe.bBZ. secure boot-image secure boot-config ! ip ssh time-out 15 ip ssh authentication-retries 4 ! interface FastEthernet0/0 description connecting an inside interface ip address 192.168.60.2 255.255.255.252 ip authentication mode eigrp 1 md5 ip authentication key-chain eigrp 1 EIGRP-KEY ip nat inside ip virtual-reassembly shutdown duplex auto speed auto ! interface FastEthernet0/1 ip address 209.165.200.225 255.255.255.224 ip nat outside ip virtual-reassembly shutdown duplex auto speed auto ! interface Serial0/2/0 no ip address shutdown ! interface Serial0/2/1 no ip address shutdown clock rate 125000 ! router eigrp 1 network 192.168.0.0 no auto-summary ! no ip classless ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 209.165.200.255 ! ip http server no ip http secure-server Page 6-- 47 - of 105 ip nat inside source list 1 interface FastEthernet0/1 overload ip nat inside source static 192.168.40.2 209.165.200.225 ! access-list 1 permit 192.168.0.0 0.0.255.255 no cdp run ! control-plane ! banner motd ^C This switch is the property of FDS Tech. Disconnect now if you are unauthorised access. Any violations will be prosecuted. ^C ! line con 0 exec-timeout 2 30 logging synchronous line aux 0 line vty 0 4 exec-timeout 2 30 logging synchronous login authentication TELNET_LOGIN transport input ssh line vty 5 15 login authentication TELNET_LOGIN ! scheduler allocate 20000 1000 ntp authentication-key 1 md5 0822455D0A165445415F59 7 ntp authenticate ntp trusted-key 1 ntp update-calendar ntp server 192.168.20.3 key 1 end A.1.2 Secured Firewall Router documentation firewallRouter#sh run Building configuration... Current configuration : 4081 bytes ! version 12.4 service tcp-keepalives-in service timestamps debug datetime msec localtime year service timestamps log datetime msec service password-encryption ! hostname firewallRouter ! boot-start-marker boot-end-marker ! Page 6-- 48 - of 105 security authentication failure rate 5 log security passwords min-length 10 enable secret 5 $1$vtP7$ngKYPBqqhuhqGIWRbiFc4. ! aaa new-model ! aaa authentication login default local enable aaa authentication login TELNET-LOGIN local ! aaa session-id common memory-size iomem 15 no ip source-route ip cef ! no ip bootp server no ip domain lookup ip domain name FDS.com ip auth-proxy max-nodata-conns 3 ip admission max-nodata-conns 3 ip ips name iosips login block-for 30 attempts 3 within 10 login delay 3 login quiet-mode access-class 101 login on-failure log login on-success log ! voice-card 0 ! key chain EIGRP_KEY key 1 key-string 7 00071A150754 ! ip inspect audit-trail ip inspect name in-out-in icmp ip inspect name in-out-in telnet ip inspect name in-out-in http ip inspect name in-out-in tcp ip inspect name in-out-in udp ! ip ips config location flash:ipsdir/ retries 1 ip ips name iosips ip ips signature-category category all retired true category ios_ips basic retired false ! username Admin1 privilege 15 secret 5 $1$mERr$ZR1fkPDr3Z4icChNe.bBZ. secure boot-image secure boot-config ! ip ssh time-out 15 Page 6-- 49 - of 105 ip ssh authentication-retries 4 ! interface FastEthernet0/0 description connecting to L3switch1 ip address 10.20.20.2 255.255.255.0 ip authentication mode eigrp 1 md5 ip authentication key-chain eigrp 1 EIGRP-KEY ip access-group 106 in ip access-group 105 out ip ips iosips in ip ips iosips out duplex auto speed auto ! interface FastEthernet1/1 description connecting to L3switch2 ip address 10.10.10.2 255.255.255.0 ip authentication mode eigrp 1 md5 ip authentication key-chain eigrp 1 EIGRP-KEY ip access-group 106 in ip access-group 105 out ip ips iosips in ip ips iosips out duplex auto speed auto ! interface FastEthernet0/1 description connecting to perimeter router ip address 192.168.60.1 255.255.255.252 ip authentication mode eigrp 1 md5 ip authentication key-chain eigrp 1 EIGRP-KEY ip access-group 107 out ip inspect in-out-in in ip inspect in-out-in out duplex auto speed auto ! interface FastEthernet1/0 description connecting to DMZserver ip address 192.168.40.1 255.255.255.0 ip ips iosips in ip ips iosips out duplex auto speed auto ! router eigrp 1 network 10.0.0.0 network 192.168.0.0 no auto-summary ! ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 192.168.60.2 Page 6-- 50 - of 105 ip route 192.168.20.0 255.255.255.0 FastEthernet0/0 ip route 192.168.30.0 255.255.255.0 FastEthernet0/1 ! ip http server no ip http secure-server ! logging 192.168.20.3ip access-list extended out-in permit ip any any access-list 103 and 104 remark permits tcp,ip ,icmp and allow replys for only the connections that are established form the private subnet of vlan 2,and applied outbound int fa0/0 on the firewall router. access-list 103 permit icmp 209.165.200.0 0.0.0.255 192.168.20.0 0.0.0.255 access-list 103 permit ip 192.168.60.0 0.0.0.255 192.168.20.0 0.0.0.255 access-list 103 permit ip 192.168.40.0 0.0.0.255 192.168.20.0 0.0.0.255 access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq www access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq ftp access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq 20 access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq 443 access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq smtp access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 209.165.200.226 eq pop3 access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 192.168.60.2 eq 22 access-list 103 permit tcp 192.168.20.0 0.0.0.255 host 192.168.60.2 eq telnet access-list 105 and 106 remark permits tcp,ip ,icmp and allow replys for only the connections that are established form the private subnet of vlan 3,and applied outbound int fa1/1 on the firewall router. access-list 105 permit icmp 209.165.200.0 0.0.0.255 192.168.30.0 0.0.0.255 access-list 105 permit ip 192.168.60.0 0.0.0.255 192.168.30.0 0.0.0.255 access-list 105 permit ip 192.168.40.0 0.0.0.255 192.168.30.0 0.0.0.255 access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq www access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq ftp access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq 20 access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq 443 access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq smtp access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 209.165.200.226 eq pop3 access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 192.168.60.2 eq 22 access-list 105 permit tcp 192.168.30.0 0.0.0.255 host 192.168.60.2 eq telnet access-list 107 remark permits all the required ICMP messages for proper network operations outbound to the fa0/ while denying all others on the firewall router. access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 echo-reply access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 parameter-problem access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 packet -too-big access-list 107 permit icmp 209.165.200.0 0.0.0.255 192.168.0.0 0.0.255.255 source-quench access-list 107 deny icmp any any log access-list 111 permit ip any 192.168.0.0 0.0.255.255 no cdp run ! control-plane ! banner motd ^CC This switch is the property of FDS Tech. Disconnect now if you are unauthorised access. Any violations will be prosecuted ^C ! line con 0 exec-timeout 2 30 password 7 13061E010803557878707D Page 6-- 51 - of 105 logging synchronous line aux 0 line vty 0 4 exec-timeout 2 30 password 7 1511021F07257A767B6760 logging synchronous transport input ssh line vty 5 exec-timeout 2 30 login authentication TELNET-LOGIN transport input ssh line vty 6 15 exec-timeout 2 30 login authentication TELNET-LOGIN ! scheduler allocate 20000 1000 ntp authentication-key 1 md5 0822455D0A165445415F59 7 ntp authenticate ntp trusted-key 1 ntp update-calendar ntp server 192.168.20.3 key 1 end firewallRouter# A.1.3 Secured Layer 3Switch1 documentation L3switch1#sh run ! !Building configuration... ! Current configuration : 4106 bytes ! ! Last configuration change at 00:28:07 UTC Mon Mar 1 1993 ! version 12.2 no service pad no service timestamps debug uptime service timestamps log datetime msec service password-encryption ! hostname L3switch1 ! boot-start-marker boot-end-marker ! enable secret 5 $1$mERr$WvpW0n5HghRrqnrwXCUUl. ! no aaa new-model system mtu routing 1500 ip routing Page 6-- 52 - of 105 ip arp inspection vlan 1 no ip domain-lookup ip domain-name FDS.com ! ip dhcp excluded-address 192.168.20.1 ip dhcp excluded-address 192.168.20.3 ! ip dhcp pool LAN-POOL-1 network 192.168.20.0 255.255.255.0 default-router 192.168.20.1 ! ip dhcp snooping vlan 2 ip dhcp snooping login block-for 30 attempts 3 within 10 login on-failure log login on-success log ! spanning-tree mode pvst spanning-tree extend system-id spanning-tree vlan 1,20,30 priority 24576 ! vlan internal allocation policy ascending ! ip ssh version 2 ! interface FastEthernet0/1 no switchport ip address 10.20.20.1 255.255.255.0 ! interface FastEthernet0/2 switchport trunk encapsulation dot1q switchport trunk native vlan 99 switchport mode trunk switchport nonegotiate ip arp inspection trust storm-control broadcast level 50.00 spanning-tree guard root ip verify source ip dhcp snooping trust ! interface FastEthernet0/3 no switchport ip address 10.30.30.1 255.255.255.0 storm-control broadcast level 50.00 ! interface FastEthernet0/4 switchport trunk encapsulation dot1q switchport mode trunk switchport nonegotiate storm-control broadcast level 50.00 spanning-tree guard root ! Page 6-- 53 - of 105 ! --- Output omitted interface FastEthernet0/5 switchport access vlan 99 shutdown ! ! --- Output omitted interface GigabitEthernet0/2 switchport access vlan 99 shutdown ! interface Vlan1 no ip address shutdown ! interface Vlan2 description connecting to the managment vlan ip address 192.168.20.2 255.255.255.0 standby 1 192.168.20.1 Standby 1 priority 160 Standby 1 preempt Standby 1 track fa0/3 70 Standby 1 authentication VLAN2 ! interface Vlan3 description connecting HR vlan ip address 192.168.30.3 255.255.255.0 standby 2 192.168.30.1 Standby 2 priority 160 Standby 2 preempt Standby 2 track fa0/3 65 Standby 2 authentication VLAN3 ! interface Vlan99 description connecting native vlan ip address 192.168.10.1 255.255.255.0 ! router eigrp 1 network 10.0.0.0 ! ip http server ip http secure-server ! ip route 0.0.0.0 0.0.0.0 10.20.20.2 ! logging esm config logging 192.168.20.3 no cdp run no cdp tlv location no cdp tlv app ! Page 6-- 54 - of 105 banner login ^C This switch is the property of FDS Tech. Disconnect now if you are unauthorised access. Any violations will be prosecuted. ^C ! line con 0 exec-timeout 2 30 password 7 0822455D0A165445415F59 logging synchronous login line vty 0 4 exec-timeout 2 30 password 7 0822455D0A165445415F59 logging synchronous login transport input ssh line vty 5 15 exec-timeout 2 30 password 7 0822455D0A165445415F59 login transport input ssh ! ntp authentication-key 1 md5 0822455D0A165445415F59 7 ntp authenticate ntp trusted-key 1 ntp server 192.168.20.3 key 1 end L3switch1# A.1.4 Secured Layer 3Switch2 documentation L3switch2#sh run Building configuration... Current configuration : 3673 bytes ! ! Last configuration change at 00:07:06 UTC Mon Mar 1 1993 ! version 12.2 no service pad no service timestamps debug uptime service timestamps log datetime msec service password-encryption ! hostname L3switch2 ! boot-start-marker boot-end-marker ! enable secret 5 $1$mERr$WvpW0n5HghRrqnrwXCUUl. ! no aaa new-model system mtu routing 1500 Page 6-- 55 - of 105 ip routing no ip domain-lookup ip domain-name FDS.com ! ip dhcp excluded-address 192.168.30.1 ! ip dhcp pool LAN-POOL-1 network 192.168.30.0 255.255.255.0 default-router 192.168.30.1 ! ip dhcp snooping vlan 1 ip dhcp snooping login block-for 30 attempts 3 within 10 login on-failure log login on-success log ! spanning-tree mode pvst spanning-tree extend system-id spanning-tree vlan 1 priority 28672 ! vlan internal allocation policy ascending ! ip ssh version 2 ! interface FastEthernet0/1 no switchport ip address 10.10.10.1 255.255.255.0 ! interface FastEthernet0/2 switchport trunk encapsulation dot1q switchport trunk native vlan 99 switchport mode trunk switchport nonegotiate ip arp inspection trust storm-control broadcast level 50.00 ip verify source ip dhcp snooping trust ! interface FastEthernet0/3 no switchport ip address 10.30.30.2 255.255.255.0 ! interface FastEthernet0/4 switchport trunk encapsulation dot1q switchport mode trunk switchport nonegotiate storm-control broadcast level 50.00 ! interface FastEthernet0/5 switchport access vlan 99 shutdown ! Page 6-- 56 - of 105 ! --- Output omitted interface GigabitEthernet0/2 switchport access vlan 99 shutdown ! interface Vlan1 no ip address shutdown ! interface Vlan2 description connecting to the management vlan ip address 192.168.20.2 255.255.255.0 standby 1 192.168.20.1 Standby 1 preempt Standby 1 track fa0/3 70 Standby 1 authentication VLAN2 ! interface Vlan3 description connecting to the HR vlan ip address 192.168.30.3 255.255.255.0 standby 2 192.168.30.1 Standby 2 preempt Standby 2 track fa0/3 65 Standby 2 authentication VLAN3 ! interface Vlan99 description connecting native vlan ip address 192.168.10.1 255.255.255.0 ! router eigrp 1 network 10.0.0.0 ! ip http server ip http secure-server ! ip route 0.0.0.0 0.0.0.0 10.10.10.2 ! logging esm config logging 192.168.20.3 no cdp run no cdp tlv location no cdp tlv app ! banner login ^C This switch is the property of FDS Tech. Disconnect now if you are unauthorised access. Any violations will be prosecuted. ^C ! line con 0 exec-timeout 2 30 password 7 0822455D0A165445415F59 logging synchronous Page 6-- 57 - of 105 login line vty 0 4 exec-timeout 2 30 password 7 0822455D0A165445415F59 transport input ssh logging synchronous login line vty 5 15 exec-timeout 2 30 password 7 0822455D0A165445415F59 transport input ssh logging synchronous login ! end L3switch2# A.1.5 Secured Layer 2Switch1 documentation L2switch1#sh run ! !Building configuration... ! Current configuration : 3494 bytes ! version 12.1 no service pad no service timestamps debug uptime service timestamps log datetime msec service password-encryption ! hostname L2switch1 ! ip subnet-zero no ip domain-lookup ! spanning-tree mode pvst no spanning-tree optimize bpdu transmission spanning-tree extend system-id no spanning-tree vlan 2 ! interface FastEthernet0/1 switchport trunk native vlan 99 switchport mode trunk switchport nonegotiate no ip address storm-control broadcast level 50.00 ! interface FastEthernet0/2 switchport access vlan 2 Page 6-- 58 - of 105 switchport mode access switchport port-security switchport port-security mac-address sticky switchport port-security mac-address sticky 00e0.a3dd.0752 no ip address spanning-tree portfast spanning-tree bpduguard enable ! interface FastEthernet0/3 switchport mode trunk switchport nonegotiate no ip address storm-control broadcast level 50.00 spanning-tree guard root ! interface FastEthernet0/4 switchport access vlan 2 switchport mode access switchport port-security switchport port-security mac-address sticky switchport port-security mac-address sticky 0001.c9da.0939 no ip address ! interface FastEthernet0/5 switchport access vlan 99 no ip address shutdown ! ! --- Output omitted interface GigabitEthernet0/2 switchport access vlan 99 no ip address ! interface Vlan1 no ip address no ip route-cache shutdown ! interface Vlan2 no ip address no ip route-cache shutdown ! interface Vlan99 no ip address no ip route-cache ! ip default-gateway 192.168.20.1 ip http server ! banner login ^C This switch is the property of FDS Tech. Disconnect now if you are Page 6-- 59 - of 105 unauthorised access. Any violations will be prosecuted. ^C ! line con 0 exec-timeout 2 30 password 7 104D000A061843595F507F logging synchronous login line vty 0 4 exec-timeout 2 30 password 7 1511021F07257A767B6760 transport input ssh logging synchronous login local line vty 5 15 exec-timeout 2 30 password 7 1511021F07257A767B6760 transport input ssh login local ! end L2switch1# A.1.6 Secured Layer 2Switch2 documentation L2switch2#sh run Building configuration... Current configuration : 3347 bytes ! version 12.1 no service pad no service timestamps debug uptime service timestamps log datetime msec service password-encryption ! hostname L2switch2 ! ip subnet-zero no ip domain-lookup ! spanning-tree mode pvst no spanning-tree optimize bpdu transmission spanning-tree extend system-id no spanning-tree vlan 3 ! interface FastEthernet0/1 switchport trunk native vlan 99 switchport mode trunk switchport nonegotiate no ip address storm-control broadcast level 50.00 ! Page 6-- 60 - of 105 interface FastEthernet0/2 switchport mode trunk switchport nonegotiate no ip address storm-control broadcast level 50.00 ! interface FastEthernet0/3 switchport access vlan 3 switchport mode access switchport port-security switchport port-security mac-address sticky switchport port-security mac-address sticky 00e0.f9a9.bab6 no ip address spanning-tree portfast spanning-tree bpduguard enable ! interface FastEthernet0/4 switchport access vlan 99 no ip address shutdown ! ! --- Output omitted interface GigabitEthernet0/2 switchport access vlan 99 no ip address ! interface Vlan1 no ip address no ip route-cache shutdown ! interface Vlan3 no ip address no ip route-cache ! interface Vlan99 no ip address no ip route-cache ! ip default-gateway 192.168.30.1 ip http server ! logging 192.168.20.3 banner motd ^C This switch is the property of FDS Tech. Disconnect now if you are unauthorised access. Any violations will be prosecuted. ^C ! line con 0 exec-timeout 2 30 password 7 104D000A061843595F507F logging synchronous login line vty 0 4 Page 6-- 61 - of 105 exec-timeout 2 30 password 7 1511021F07257A767B6760 transport input ssh logging synchronous login local line vty 5 15 exec-timeout 2 30 password 7 1511021F07257A767B6760 transport input ssh login local end L2switch2# Page 6-- 62 - of 105 Appendix B: B.1 Glossary Authentication, authorization, and accounting (AAA) Provides a mechanism to address the unauthorised access to a network through systematic, scalable access security. Demilitarized zone (DMZ) sometimes referred to as a screened subnet. Denial of service (DOS) A class of attack in which the attacker seeks to make a given resource such as a server unavailable to legitimate users by overwhelming the resources with requests for services that appear to legitimate. Default Gateway It’s the route used by the devices when it has no other explicitly defined route to the destination network. Encryption Applying a specific algorithm to data to alter its appearance, making it incomprehensible to those who are not authorised to see the information. Endpoint The final point of connection in a communication channel. Firewall Allows the segmentation of the network into different physical subnet works, thereby limiting the potential damage that could spread from one subnet to another. Firewalls may be a piece of software or hardware that acts as a barrier between the internal (trusted) and the external (untrusted) network, such as the internet. FTP This is a standard network protocol used to transfer files from one host to another host over a TCP-based network, such as the Internet GNS3 It is a graphical network simulator that allows simulation of complex networks. Page 6-- 63 - of 105 HTTP The underlying protocol used by the World Wide Web. HTTP defines how messages are formatted and transmitted, and what actions Web servers and browsers should take in response to various commands IEEE 802.5 A standard that defines Token Ring technology as a LAN protocol where all stations are connected in a ring and each station can directly hear transmissions only from its immediate neighbour. IP Is the primary protocol in the Internet Layer of the Internet Protocol Suite that is responsible for the delivering datagrams from the source host to the destination host basing on their addresses. Intrusion Prevention System (IPS) This monitors systems activities for malicious or unwanted behaviours. It can react in real time to block or prevent those activities. LAN storms Is when packets floods the LAN creating excessive traffic, and degrading the network performance Network Address Translation (NAT) Employed by networks that use private IP addresses. It is used to translate embedded addresses and to update any checksum or other fields that are affected by the translation. MAC Short for Media Access Control address, a hardware address that uniquely identifies each node of a network. MAC address spoofing occurs when one host poses as another to receive otherwise inaccessible data, or to circumvent security configurations. MAC address table overflows MAC flooding takes advantage of this limitation by flooding the switch with fake source MAC addresses until the switch MAC address table is full. As a result the switch begins to flood all incoming traffic to all ports due to lack of space Page 6-- 64 - of 105 to learn any legitimate MAC addresses. At this point the attacker with access to LAN can see all of the frames sent from one host to another. OSI Open System Interconnection, model defines a networking framework for implementing protocols in seven layers. PAT Sometime called NAT overloading. It maps multiple private IP addresses to a single public IP address or a few addresses. POP3 It is a client/server protocol in which e-mail is received and held for you by your Internet server. Syslog A protocol used to collect log information. It consists of two primary components: syslog servers and syslog clients. A syslog server receives and stores log messages sent from syslog clients. STP manipulation attack In an STP manipulation attack, the attacking host broadcasts STP configurations, with BPDUs of a lower bridge priority in an attempt to be elected as the root bridge by forcing spanning-tree recalculations. If the attack is successfully done, the attacking host becomes the root bridge and sees a number of frames wouldn’t have been accessible. Secure Shell (SSH) A protocol that provides encryption and authentication functions for remote terminal sessions via telnet. STP a link management protocol that is part of the IEEE 802.1 standard for media access control bridges. Transmission Control Protocol (TCP) One of the internet protocol suite that provides reliable, in-order delivery of a stream of bytes – transport protocol, suitable for applications such as file transfer and e-mails. Page 6-- 65 - of 105 VPN it is a means to securely and privately transmits data over an unsecured and shared network infrastructure. VLAN A group of hosts with a common set of requirements that communicate as if they were attached to the same wire regardless of their physical location. VLAN attacks the attacker accesses works vulnerable trunk port enabling him to spoof DTP messages and causes the switch to enter into trunking mode, or bring up a rogue switch and enable trunking as a result access all the VLANs on the victim switch. Page 6-- 66 - of 105 Appendix C: C.1 Project proposal Page 6-- 67 - of 105