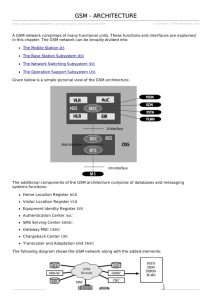
GSM (Global System for Mobile Communications)
advertisement

1 WIRELESS DIGITAL NETWORKS Wireless transmission has found widespread use in communication systems only in the last 15 – 20 years. Currently the field of wireless communications is one of the fastest growing segments of the telecommunications industry. Wireless communication systems, such as cellular, cordless and satellite phones as well as wireless local area networks (WLANs) and personal area networks (PANs) have become an essential tool in many people’s every-day life. It is expected that the number of worldwide wireless subscribers in the years to come will be well over the number of wired line subscribers. The most important advantages of wireless communication systems are mobility and cost savings. In the following we briefly overview different types of wireless networks. Some of these are discussed more deeply later in this course. Digital Cellular Telephony Compared to analog systems, digital systems have a number of advantages: Digitized traffic can easily be encrypted in order to provide privacy and security. Analog systems are susceptible to interference, leading to a highly variable quality of voice calls. In digital systems, it is possible to apply error detection and error correction to the bitstream. A number of 2G (second generation) systems are employed in various parts of the world: GSM. Global Systems for Mobile Communications (GSM) is the most popular 2G technology. The first commercial deployment of GSM used the 900 MHz band. The system that uses the 1800 MHz band is known as DCS 1800 (digital cellular system). GSM can also operate in the 1900 MHz band used in USA for several digital networks. A more exact structure of GSM is describe later in the course. D-AMPS. In the United States, a time-slot-bases system known as IS-54 was employed in 1993. It provided a three-fold increase in the system capacity compared to analog systems. IS-136 was introduced in 1996 and supported additional features. These standards are known as the Digital AMPS (D-AMPS) family. Extensions of D-AMPS offers data rates ranging from 9.6 to 19.2 kbit/s. Used frequencies are 800 and 1900 MHz. TDMA is the chosen access method. cdmaOne. This system based on IS-95 was standardized in 1993, and the first commercial system was deployed in South Korea and Hong Kong in 1995. This was followed by deployment in the United States in 1996. IS-95 utilizes Code Division Multiple Access (CDMA). IS-95 is designed to support dual-mode terminals that can operate either under an IS-95 or an AMPS network. IS-95 supports data traffic at rates of 4.8 and 14.4.kbps. An extension, known as IS-95b (cdmaTwo), offers support for 115.2 kbps. 2 GPRS. GSM supports an extension technologies that achieve higher rates for data application. GPRS (General Packet Radio Service) is a simple upgrade to GSM. This is a so called 2.5 generation system. GPRS gives more than one time slot per frame to a user; hence the increased data rates. The difference is that GPRS is packet-switched. Whereas GSM is circuit-switched. GPRS uses bandwidth on demand and a single 14.4.kbps link can be shared by more than one user. GPRS terminals support a variety of rates, ranging from 14.4 to 115.2 kbps, both in symmetric and asymmetric configuration. More about GPRS later on. HSCSD. High Speed Circuit Switched Data (HSCSD) is also an upgrade to GSM. HSCSD allows a phone to use two, three or four slots per frame to achieve rates of 57.6, 43.2 and 28.8 kbps, respectively. Support for asymmetric links is also provided, meaning that the uplink can be different from that of the downlink. HSCSD decreases battery life, due to the fact that increases slot use makes terminals spend more time in transmission and reception modes. However, because reception requires significantly less power consumption than transmission, HSCSD can be efficient for web browsing, which entails much more downloading than uploading. HSCSD is a 2.5G system. IMT-2000. 2G systems are inefficient. A transfer of a 2 Mbit would take approximately 28 minutes employing the 9.6 kbps GSM data transmission. To provide for efficient transmission, work on the Third generation (3G) of cellular systems was initiated by ITU (International Telecommunication Union) in 1992. The outcome, called International Mobile telecommunications 2000 (IMT-2000), comprises a number of different 3G standards. Such standards are EDGE and WCDMA. 3G systems are discussed later on in this text. Wireless Data Systems Cellular telephony is oriented towards voice transmission. These systems are characterized by bursty transmission; unless there is a packet to transmit, terminals remain idle. The first wireless data system was developed in 1971 at the University of Hawaii under the research project ALOHANET. The idea of the project was to offer bidirectional communications between computers spread over four islands. The system was simple. Although mobility was not part of ALOHA, it was the basis for today’s mobile wireless data systems. Wireless Local Area Networks (WLANs). These systems provide high-speed data within a relatively small region, such as a small building or campus. US Federal Communications Commission (FCC) authorized license-free use of the industrial, Scientific and Medical (ISM) bands in the mid-1980s. The first attempt to define a standard was made in the late 1980s by IEEE Working Group 802.4, which was responsible for the development of the token-passing bus access method. The group suggested the development of an alternative method because the token passing was an inefficient method. As a result, Working group 802.11 was established and has been since then responsible for the definition of physical and MAC sub-layer standards for WLANs. The first 802.11 standard offered data rates up to 2 Mbps using either spread spectrum 3 transmission in the ISM bands or infrared transmission. In 1999, two supplements to the original standard were approved by the IEEE Standard Board. The first standard, 802.11b, extends the performance of the existing 2.4 GHz physical layer, with potential data rates up to 11 Mbps. The second standard, 802.11a, aims to provide a new, higher data rate (from 20 to 54 Mbps) physical layer in the 5 GHz ISM band. These standards use the same medium Access Control (MAC) protocol, known as Distributed Foundation Wireless MAC (DFWMAC). This protocol belongs to the family of Carrier Sense Multiple Access (CSMA). More about 802.11 standards later. In addition, another WLAN standard, High Performance European Radio LAN (HIPERLAN) was developed by ETSI (European Telecommunications Standards Institute for high speed WLANs. The standard covers the physical and MAC layers, offering data rates between 2 and 25 Mbps by using narrowband radio modulation in the 5.2 GHz band HIPERLAN 1 utilizes a CSMA-like protocol Personal Area Networks. These networks, PANs, are the next step down from LANs and target applications that demand very short-range communication, a few meters. The first attempt to define a standard for PANs dates back to an Ericsson project in 1994, which aimed to find a solution for wireless communication between mobile phones and related accessories (e.g. hands-free kit). The procect was named Bluetooth after the name of a Danish Viking- It is now an open standard. Bluetooth operates in the 2.4 MHz ISM band, it supports 64 kbps voice channels and asynchronous data channels with rates ranging up to 721 kbps. Supported ranges of operation are 10 m at 1 mW transmission power and 100 m at 1 Mw. More about Bluetooth later. HomeRF is another PAN project. It offers 32 kbps voice connection and data rates up to 10 Mbps. HomeRF operates in the 2.4 MHz band and support ranges around 50 m. The 802.15 Working Group has the target to achieve interoperability between Bluetooth and HomeRF. Wireless ATM. WATM combines the advantage of freedom of movement of wireless networks with the statistical multiplexing (flexible bandwidth allocation) and Quality of Service (QoS) guarantees by traditional ATM (Asynchronous Transfer Mode). Satellite Communication Systems The era of satellite systems began in 1957 with the launch of Sputnik. The first real communication satellite was the AT&T telstar 1, which was launched by NASA in 1962. Today, satellite communications offer services such as data, paging, voice, TV broadcasting, Internet access and a number of mobile services. More about mobile satellite communication systems later. 4 GSM (Global System for Mobile Communications) In 1980 the European Telecommunications Standards Institute (ETSI) formed the Groupe Speciale Mobile (GSM). Today, the acronym GSM means Global System for Mobile Communications. The first trial version of GSM was developed in 1991, and the commercial systems were launched in 1992. The task was to develop standards for mobile communication systems. The primary goal was to provide a mobile phone system that allows roaming of users through Europe and provides voice services compatible to ISDN (Integrated Service Digital Network) and other PSTN (Public Service Telephone Network) systems. The following brief introduction to GSM is mainly taken from the reference ‘Dreamtech Software Team. Cracking the Code. WAP, Bluetooth and 3G Programming. Hungry Minds, New York, 2002’. Feautures. The main features of GSM are: GSM has all the advantages of digital communication system, such as better noise immunity and better data capability. Security can be easily built into the system. The architecture interfaces are standardized. This implies that network elements manufactured by different equipment vendors can work with one another, thereby paving way for competition. The calling capacity (~125 calls per cell) is high compared to analog systems (~55 calls per cell). GSM supports international roaming In addition to voice services, data services are also supported. Specifications. Main specifications of the GSM system are: Frequency band: 900 MHz (890 – 915 MHz for uplink, 935 –960 for downlink), 1800 MHz (1710 – 1785 MHz, 1805 – 1880) and 1900 MHz (1850 – 1910 MHz, 1930 – 1990 MHz). Duplex distance: The distance between uplink and downlink frequencies is 45 MHz. Channel spacing: The spacing between adjacent carrier frequencies is 200 kHz. Modulation: A special form of MSK (Minimum Shift Keying) called Gaussian MSK is used. In MSK, 1s and 0s are presented by shifting the RF carrier plus or minus 67.708 kHz. The modulation spectrum is reduced by applying a Gaussian filter to avoid spreading of energy into adjacent channels. Transmit data rate: The air bit rate is 270.833 kbit/s. Access method. Time Division Multiple Access (TDMA) with eight time slots is used, i.e., the same frequency is shared by eight users. Each subscriber is 5 allocated a small time slot. In this time slot the user will send his data and then wait for the next time slot, which he will get after the seven others finish transmitting data in their time slots. Each subscriber will transmit his data in bursts. Speech coding. Speech is transmitted at 13 kbit/s, not at 64 kbit/s as in normal telephony networks. The low data rate implies that the quality of the speech is low compared to the voice quality in a normal telephone network. Signaling. In GSM a separate signaling network is used for carrying signaling information. Signaling System 7 (SS7) based on a standard developed by the International Telecommunications Union (ITI) is used. Services. GSM services are divided into teleservices and data services. In addition, the following are also supported: Fax transmission through a special interface provided to the handsets Short Message Service (SMS) to transmit a maximum of 160 alphanumeric characters. Cell broadcast can transmit maximum of 93 characters to all handsets in a particular cell. The service is used to transmit information regarding traffic congestion, accident information, and so forth. Voice mail Fax mail The GSM system supports among others the following supplementary services: Call forwarding, a call to another mobile handset or a fixed line Blocking outgoing calls Blocking incoming calls. (All incoming or only incoming calls when roaming outside the operator’s region) Advice of charge Call hold (interrupt a call and reestablish it again) Call waiting (notify an incoming call when a conversation is in progress) Calling Line Identification Presentation (CLIP) to display the telephone number of the calling party 6 Architecture. The GSM network can be divided into three main parts, the NSS (Network and Switching System) , the BSS (Base Station Subsystem) and the OSS (Operations SubSystem). The layout of a generic GSM network with its main interfaces are illustrated in Figure 1. Figure 1. General architecture of the GSM network. The mobile network of the entire region is known as PLMN (Public Land Mobile Network). PLMN consists of Mobile Stations (MS), Base Station Subsystems (BSS) and the Network Subsystem. The administrative control of PLMN is handled by an operator. Network Subsystem MSC (Mobile Services Switching Center) is the main center. Its main task is to connect an incoming call to the right base Station Subsystem (BSS) and from the BSS to other networks. HLR (Home Location Register) is a database containing information of constant or variable type. Constant information contains the MSISDN (Mobile Station ISDN Number, the publicly available phone book number), the IMSI, the security parameters for authentication and ciphering, and the type of subscribed connection. Variables contains information of the current location area (VLR) of the MS, call forward information and supplementary service information. VLR (Visitor Location Register) contains subscription information of every visiting user in the geographical area controlled by the MSC/VLR, information for call control and provision of the subscribed services. Once a roaming mobile is logged in the VLR, the MSC sends the necessary information to the visiting 7 subscriber’s HLR. As a subscriber moves to another MSC/VLR area, the information is deleted from the old VLR and transferred to the new. EIR (Equipment Identity Register) is a database that contains lists of all mobile equipments in the network, where each MS is identified by its IMEI. An IMEI could be marked in the EIR as invalid, stolen or as an MS that is under supervision (under observation from the network for possible problems). AuC (Authentication Center) is a protected database that stores a copy of the secret key, Ki, which is used for authentication and ciphering (see GSM Security). Base Station Subsystem The BSS is in direct contact with the mobile station through the Um interface (radio link). On the other hand, BSS is connected to NSS over the A interface. BTS (Base Station Station) houses the radio transceiver that defines a cell and handles the radio-link protocols with the MS. In a large urban area, there will potentially be a large number of BTSs deployed. Therefore the requirements for a BTS are ruggedness, reliability, portability and minimum cost BSC (Base Station Controller) manages the radio resources for its own area. BTC controls BTSs underneath and handles radio-channel setup, frequency hopping, and handovers. TRAU /Transcoder / Rate Adapter Unit) decodes data transmitted from the MS, to a form that could be understood by the fixed network. It also adapts the speed of the data between BSS and other networks. Network areas. The following areas are defined: Cell – A cell forms the basic service area. BTS (base Transceiver Station) covers one cell. Each cell is given a Cell Global Identity (CGI), a number that uniquely identifies the cell. Location Area – A group of cells forms a Location Area. When a subscriber gets an incoming call the area is paged. Each Location Area is assigned a Location Area Identity (LAI). Each Location Area is served by one or more BSCs (Base Station Controllers). MSC/VLR Service Area – The area covered by one MSC (Mobile Switching Centre)is called the MSC/VLR (Visitor Location Register) service area. PLMN – The area covered by one network is called PLMN (Public Land Mobile Network). A PLMN can contain one or more MSCs. Operation. In the following we study the sequence of events that take place when a call is initiated from the MS. MSC/VLR receives the message of a call request 8 MSC/VLR checks if the mobile station is authorized to access the network. If so, the MS is activated and if not,service will be denied. MSC/VLR analyzes the number and initiates a call setup with the PSTN MSC/VLR asks the corresponding BSC to allocate a traffic channel (radio channel + time slot) BSC allocates the traffic channel and passes the information to the mobile station The called party (A) answers the call and the conversation takes place The mobile is taking measurements of the radio channels in the present cell and neighboring cells and passes the information to the BSC. BSC decides if handover is required; if so, a new traffic channel is allocated to the MSC. Channels. GSM specifies two basic groups of logical channels, i.e., traffic channels and control channels. Traffic channels (TCH) transmit user data (voice, fax, data) and control channels (CCH) control medium access, allocation of traffic channels and mobility management. 9 GSM SECURITY The security features in the GSM network can be divided into three sub parts: subscriber identity authentication, user and signaling data confidentiality, and subscriber identity confidentiality. The security mechanisms include secret keys, algorithms and computed numbers. Some definitions: Authentication – any technique that enables the receiver to automatically identify and reject messages that have been altered deliberately or by channel errors Confidentiality – only the sender and intended receiver should be able to understand the contents of the transmitted message Ciphertext – plaintext is encrypted to ciphertext with the help of a key and an encryption algorithm Key – a string of numbers or characters as input to the encryption algorithm The base mechanism (Figure 1) shows where the different keys and algorithms are stored. The secret key Ki is used to authenticate the identity of a subscriber. The key Ki is given to the subscriber when he opens a new network account. Only the network operator knows the key. The Ki is stored in the subscribers SIM card and the authentication center (AuC) of the subscribers home network. The Ki is never transmitted over the network. Figure 2. Base of the security mechanism. 10 A3 is the algorithm used to authenticate the subscriber. Data transmitted between the MS (Mobile Station) and the BTS (Base Transceiver Station) is encrypted by the A5 algorithm. The A8 algorithm generates the needed ciphering key Kc used by A5. Subscriber Identity Authentication. The procedure consists of three phases, (1) the network must identify the subscriber, (2) needed security parameters from the home network are asked for and (3) the actual authentication is taking place. Figure 3. Subscriber identification process. In order to identify the subscriber the MS sends the IMSI (International Mobile Subscriber Identity) to the visited network. With the IMSI the subscriber is identified to the system. The IMSI is up to 15 digits and comprises the following parts: A 3-digit Mobile Country Code (MCC). This identifies the country where the GSM system operates. Finland has number 244. A 2-digit Mobile Network Code (MNC). This uniquely identifies each cellular provider. Sonera has number 91. The Mobile Subscriber Identification Code (MSIC).This uniquely identifies each customer of the provider. The length is 10 digits. So called security triplets are calculated in the AuC. The triplets consist of a random number (RAND), a signed response (SRES) and a ciphering key (Kc). The SRES is used to authenticate the subscriber and Kc is used as input by the ciphering algorithm A5. 11 Figure 4. Calculating the security triplets. As the visited network has received the security triplets the actual authentication can take place (see Figure 5). If the number sent by the MS to the BTS is the same as the one calculated by the AuC, the subscriber is authenticated. Figure 5. Authentication the subscriber. User and Signaling Data Confidentiality. The Ciphering key (Kc) is used for the final encryption of the radio link. One copy of the needed Kc is stored in the VLR and an other copy is calculated in the MS by the A8 algorithm. The same Ki and RAND numbers are used as in the authentication process. The A5 algorithm creates 114-bit sequence. This sequence is then XORed with every 114 user data bits and the resulting bitstreams are sent over the two 57 bit parts of every GSM slot. All traffic between the MS and the BTS is then secured. Subscriber Identity Confidentiality. The IMSI is the primary key for subscriber identification. However a temporary identity, TMSI (Temporary Mobile Subscriber 12 Identity) can be given to a subscriber for identification. After initial registration done with the IMSI, the serving network stores the IMSI in the VLR and generates a TMSI for the subscriber. The TMSI is then transmitted back to the MS and it will be used for identification as long as the subscriber is registered in that specific network.