NETWORK MANAGEMENT SYSTEMS
advertisement

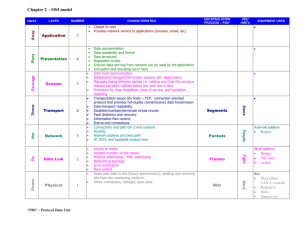
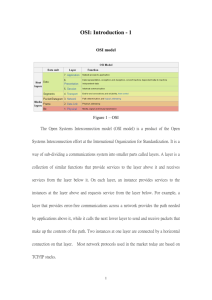
NETWORK MANAGEMENT SYSTEMS UNIT-I 1.1 Syllabus Data communications and Network Management Overview : Analogy of Telephone Network Management, Communications protocols and Standards, Case Histories of Networking and Management, Challenges of Information Technology Managers, Network Management: Goals, Organization, and Functions, Network and System Management, Network Management System Platform, Current Status and future of Network Management. 1.2 Objectives: Learn about data communications and networks Learn about telephone networks and data networks Understand the usage of different protocols and standards Learn the case histories of network management Understand the functionalities and goals of network management Learn about the different platforms of NMS Analogy of Telephone Network Management The reason for reliability, dependability and quality is more than the careful planning, design and implementation of a good telephone network using good and reliable components. The key is the management and operations of the network. The architecture of the telephone network is hierarchical. There are five levels of network switches and three types of trunks that connect these switches. A trunk is a logical link between two switches that my traverse one or more physical links. The direct distance dialing (DDD) network which enables us to dial the far-end telephone without an operator’s assistance, comprises three transmission trucks. A direct trunk connects two end offices, a toll-connecting trunk connects an end office to any too office, and a toll trunk connects any two toll offices. A circuit connection is setup either directly using a local trunk or via the higher level switches and routes. Primary and secondary routes are already programmed into the switch. If the primary route is broken or the facilities over the primary routes are filled to capacity, an alternative route is automatically assigned. Operations support systems ensure the quality of service in the telephone network. (bandwidth, traffic at switches) For a given region, there is a network operations center (NOC) where the global status of the network is monitored. The telephone network is managed from the user’s prospective, not that of the system or service provider, even through the objective of both are the same. To manage a network remotely, i.e., to monitor and control the network components from a central location, network management functions need to be considered in building the components of the network. 1 The computer communication network, however, has not matured to the same extent as the telephone network. The data communication technology is still evolving and as merging with telephone technology. Regional Center Class 1 switch Regional Center Class 1 switch Sectional Center Class 2 switch Sectional Center Class 2 switch Primary Center Class 3 switch Primary Center Class 3 switch Toll Center Class 4 switch Toll Center Class 4 switch End Office Class 5 switch End Office Class 5 switch To other Regional centers Sectional centers Primary centers Toll centers End offices To other Primary centers Toll centers End offices To other Class 4 toll points End offices Legend: Loop Direct Trunk Toll-Connecting Trunk Voice Toll Trunk Voice Figure 1.1 Telephone Network Model Communications Protocols and Standards. Architecture can be defined as the basic structure of a system that shows its functional components and the relationships among them. Communication architecture describes the functional components of a communication network, as well as the operational interfaces among them. Operational procedures – both intra and inter modules- are specified in terms of protocols. 2 Communication Architectures. User A User Z Peer-Protocol Interface Application Layers Application Layers Transport Layers Transport Layers Physical Medium (a) Direct Communication between End Systems System A Intermediate system System Z User A User Z Peer-Protocol Interface Application Layers Application Layers Transport Layer Transport Layers Transport Layers Conversion Physical Medium Physical Medium (b) Communication between End Systems via an Intermediate System Figure 1.11 Basic Communication Architecture Each system can be divided into two broad sets of communication layers. The top set of layers consists of the application layers and the bottom set of the transport layers. Direct communication occurs between the corresponding co-operation layers of each system. Thus transport layers can exchange information, and so can the application layers and the users. The end systems communicating via an intermediate system N, which enables the use of different physical media for the two end systems. System N converts the transport-layer information into the appropriate protocols. Thus, system A could be on a copper-wire LAN and system z could be on a fiberoptic cable. The International standards organization (ISO) has developed a highly modular, or layered, architecture for communication protocols that is called the open systems interconnection (OSI) Reference Model, published as OSIRM-ISO7498. 3 This model was developed based on premise that the different layers of protocol provide different services, and that each layer can communicate with only its own neighboring level. Layers 1 through 4 are the transport system protocol layers and layers 5,6 and 7 are application support protocol layers. The OSI protocol layers User / Application program Layer 7 Application Layer 6 Presentation Layer 5 Session Layer 4 Transport Layer 3 Network Layer 2 Data link Layer 1 Physical Physical medium Figure 1.12 OSI Protocol Layers 4 OSI Layers and Services Layer No. Layer Name Salient services provided by the layer 1 Physical -Transfers to and gathers from the physical medium raw bit data -Handles physical and electrical interfaces to the transmission medium 2 Data link -Consists of two sublayers: Logical link control (LLC) and Media access control (MAC) -LLC: Formats the data to go on the medium; performs error control and flow control -MAC: Controls data transfer to and from LAN; resolves conflicts with other data on LAN 3 Network Forms the switching / routing layer of the network 4 Transport -Multiplexing and de-multiplexing of messages from applications -Acts as a transparent layer to applications and thus isolates them from the transport system layers -Makes and breaks connections for connection-oriented communications -Flow control of data in both directions 5 Session -Establishes and clears sessions for applications, and thus minimizes loss of data during large data exchange 6 Presentation -Provides a set of standard protocols so that the display would be transparent to syntax of the application -Data encryption and decryption 7 Application -Provides application specific protocols for each specific application and each specific transport protocol system The message in each layer is contained in message units called protocol data units (PDUs), which consists of two parts - protocol control information (PCI) and user data (UD). PCI consists of header information about the layer UD contains the data that the layer, acting as service provider, receives from or transmits to the upper layer / service user layer. 5 End System A User A End System Z User Z UD Application (A) PCI Presentation (P) PCI Session (S) PCI Transport (T) PCI Network (N) PCI Data link (D) PCI Application UD Presentation (A) PDU Session (P) PDU Transport (S) PDU Network (T) PDU Data link (N) PDU Physical Physical (D)PDU Data stream Physical Medium Figure 1.14 PDU Communication Model between End Systems The size of the PDU increases as it goes towards lower layers. The size of PDU exceeds the maxsize of layers specifications, it is fragmented into multiple packets. Protocol layers and Services. Layer 1, Physical Layer There are various protocol standards for physical layer interface, depending on the transmission medium and type of signal. Two classes of standards have been established by (i) the International Telecommunications Union Telecommunications Sector (ITU-T) (ii) (ii) Electronics Industries Association (EIA) Layer 2, Data Link Control Layer. The data communication between two data terminating equipment (DTE)s is controlled by this layer. Two sub layer LLC (logical link control) and MAC ( Medium Access Control) are there. 6 LLC – it performs link management & data transfer MAC - Controls the access and transmittal of data to the physical layer in an algorithmic manner. There are two types of Physical medium algorithms we are using. (i) LAN – bustype – distributed probabilistic algorithm- (CSMA / CD) (ii) LAN – token ring – deterministic token –passing algorithm – Token ring(TR), Fiber distributed data Interface (FDDI) Layer 3, Network Layer. It controls and managers the switching facric of the network. It provides connection oriented network service (CONS) and network service (CLNS). CONS – for long message transmission, not reliable. CLNS – for short message transmission, it is reliable. 7 connectionless SNICP – Subnetwork Independent convergence Protocol, that interfaces to the transport layer. Internet Communicates between nodes using an Internet address and SNICP SNDCP – Subnetwork-Dependent Convergence Protocol, which depends on the subnetwork protocol and could be any proprietary protocol. SNDCP - It communicates with its data link layer via SNDAP SNDAP – Subnetwork-dependent Access Protocol. DTE-A A N DTE-N1 Z N1 N2 A-N-Z Standard Network N-N1-N2-N3 Subnetwork under Node N N3 (a) Network configuration System A Gateway System N Transport Transport SNICP SNICP Subnet system N1 Transport SNICP SNDCP SNDCP SNDAP SNDAP SNDAP-SN SNDAP-SN Data link Data link Data link-SN Data link-SN Physical Physical Physical-SN Physical-SN SNDCP-SN Network Medium SNDCP-SN Subnetwork Medium (b) Protocol Communication Figure 1.17 Gateway Communication to Proprietary Subnetwork 8 Gateway Communication to a proprietary subnetwork. Examples are Connection Oriented OSI Protocol is X.25 packet layer protocol, ISO CLNP is TCP/IP. 4th Layer, Transport Layer. It multiplexes the user data provided by the application layers and passes the packets to the network layer. Connection oriented protocol TCP (Transmission Control Protocol). Connectionless protocol UDP (User datagram Protocol). ISO has five transport-layer specifications, TP0 to TP4 An application Process Communicates with another application process during a session 5th Layer, Session Layer The session-layer establish the communication at the beginning of the session, monitor, synchronize and error-correct the information exchanged during the session, and release the logical link at the end of the session. 6th Layer, Presentation Layer. Presentation layer is a context-sensitive layer. A common syntax semantics is Abstract Syntax Notation Number One (ASN.1) Primary function of presentation layer is conversion of syntax, data encryption and data compression are also generally done in that layer. SNA OSI End User Application Application Presentation Services Presentation Data Flow Control Session Transmission Control INTERNET Transport SNICP Path Control Network Application Specific Protocols Transport Connection- Connectionless: UDP oriented: TCP Network IP SNDCP SNDAP Data Link Data Link Physical Physical Not Specified Figure 1.18 Comparison of OSI, Internet, and SNA Protocol Layer Models 9 OSI User Internet User VT Terminal Application TELNET FTAM FTP MOTIS SMTP CMIP Mail / Message Transfer Management Application SNMP Presentation Layer File Transfer Transport Layer Figure 1.19 Application Specific Protocols in ISO and Internet Models The above figure compares four common application-specific protocols in the OSI and Internet models. There are more OSI application-specific protocols, which we do not discuss here. All application-specific protocols services in OSI are sandwiched between the user and presentation layers. In the Internet model, they are sandwiched between the user and the transport layers. Case Histories of Networking and Management. Case History 1: The Importance of Topology (“the case of the Footprint”) Case History 2: Filtering Does Not Reduce Load on Node. 10 Repeater Repeater Repeater Repeater Bridge ISP Backup ServerMail Server (a) Multi-Segment Bus LAN with Single Port Bridge Connection Repeater Repeater Repeater Repeater Bridge ISP Backup ServerMail Server (b) Dual Multi-Segment Bus LANs with Two-port Bridge Connection Backup Server Mail Server Hub Hub Hub Bridge ISP (c) Multi-Segment Hub Configuration Figure 1.20 Case History 2: Network Configuration Evolution (a) most of the traffic was internal to the LAN segment, except for e-mail and back up operations, which went across the bridge. (b) LAN segment was split into two and used two ports of the bridge. This decreased the rate of failure from two per day to two per week. (c) All three hubs and the bridge are in a central place. Some Common Network Problems The most common and serious problems of networks are connectivity failure, which are in the category of fault management. The network failure is caused more often by a node failure than by failure of passive links. The node failures manifest as connectivity failures to the user. Another cause of network connectivity failure is procedural, but very common (like IP address) 11 A host or system interface problem in a shared medium can bring the entire segment down. The intermittent problems could also occur as a result of traffic overload, which could cause packets to be lost. Power hits could reset network component configuration, causing network failure. A performance problem could manifest as a network delay and is an annoyance to the network manager. With the ever increasing size of networks and connectivity to the Internet, security violation is a frequent problem. Perspectives of Network Managers Learning network management involves more than understanding networks and network management protocols. General: People expect all networks to be like telephone networks Network reliability equal to telephone reliability is unrealizable. The telephone network was monopolistic and had expensive redundancy. Data network is adhoc, decentralized, has loosely specified interfaces, and has dynamic routing. Thus, it is more flexible than a telephone network, through less reliable. The latest user satisfaction for an ISP is 16 percent and the ISPs are still growing. Some of the data communications are non-real time such as execution of instructions like Mars Rover. Thus, when a problem is detected it is too late to fix it. 1. What are your top challenges in managing the network? Saying abreast of the rapid advance of technology, depending on trade journals, vendor product info, and conversations with colleagues. Analyzing problems, which requires intuition and skill. Anticipating customers’ demands Acquiring resources Sustainable network that is scaleable and maintainable Managing the client/server environment Networking with emerging technology as part of continuing education Collaborative research between academic institutions and industry Maintaining reliability, that is, making changes, upgrades, and such without disrupting the network and affecting business Diagnosing problems or outages in a nondisruptive manner Estimating the value of a technology transition Maintaining a secure firewall between the internal network and the Internet while gaining the value of the information and services available from the Internet. Determining responsibility for outages to the WAN, coordinating telephone company repair efforts. 12 Keeping the topology as simple as possible within the confines of the technology in order to reduce administrative effort and chance for mistakes. 2. Which elements of managing your network require most of your time? What percentage of time do you spend on maintenance compared to growth? Configuring the management system itself Expanding the network Gathering and analyzing statistics for presentation to upper management. Traditional maintenance 30% (Manager of Organization X) Mandatory maintenance 40% Growth 30% Growth 50% (Manager of Organization Y) Maintenance 50% 3. How did you or would you manage your network without an NMS? Reactively, not proactively, firefighting Troubleshooting tools Home-grown systems Managed the network in the spare time after installation Human intuition Rely on consultant advice and technical information for growth decisions 4. Do you need an NMS? If so, why? Yes, for proactive management of the network Yes, to verify customer configuration Yes, to diagnose problems Yes, to provide statistics on performance Yes, to help remove bottlenecks Yes, because an NMS formalizes the manual practice of network management Yes, because NMS products reflect the practices of the company that develops them Yes, but remember NMS does not solve problems, people do Yes, but a low-end NMS is adequate Yes, the configuration and operation of NMS reflects the person who sets it up Yes, to see the trend in growth 5. How would you use NMS and why/ Save time and use human resources effectively Saved time goes into improving network management Turn-around time for problem resolution smaller Monitor the status and performance of the network Gather statistics to improve OAM&P 13 Document events for auditing purposes Troubleshooting Remove constraints and bottlenecks Fault isolation I would expect the NMS to help me evaluate load on network segments and pinpoint failures 6. what does a network failure cost the user? There are tangible and intangible losses The losses of academic and research(A&R) laboratories differ from the losses of business corporations. A&R labs need high technology and tolerate low reliability. Business accept lower and proven technology but require high reliability. The cost is a function of the dependence of the business upon shared data. If we have a general network failure, our ability to conduct business is severely impacted because we cannot get access to the data. 7. What are your expectations of a newly graduated student with networking as area of specialization? Prefer to hire candidates with networking experience Need to be familiar with protocols Possess the drive to understand and to envision Be a self-starter Lab experience at school is essential Knowledge of basic networking Know the differences between system, applications, and network Technical: knowledge foundations, applications, tools, utilities, and so forth Be technically current with the common protocols, wiring topologies, and common network equipment Be professional, have more than just technical skill Know how to succeed in commercial organizations Recognize the importance of customer service, and see IT as the service provider Know how to stay ahead of demand curve Possess personal communication skills Be cost conscious Have a sense of business risk reduction. Network Management: Goals, Organization and Functions Network management can be defined as OAM&P (Operations, administration, maintenance and provisioning) Operations group – daily operations Administration – establishing and administering the over all goals, policies, and procedures of network. 14 Installation & maintenance group – installation and repairs of facilities & equipment Provisioning – network planning and circuit provisioning, traditionally handled by provisioning department. Goal of Network Management Network Management Network Provisioning Network Operations Network Maintenance Planning Fault Management / Service Restoration Fault Management Design Configuration Management Trouble Ticket Administration Performance Management / Traffic Management Network Installation Security Management Network Repairs Accounting Management Facilities Installation Reports Management & Maintenance Routine Network Inventory Management Tests Data Gathering & Analyses Figure 1.21 Network Management Functional Groupings The goal of network management is to ensure that the users of a network receive the information technology services with the quality of service that they expect. Toward meeting this goal, management should establish policy to either formally or informally contract a service level agreement with the user. (Eg. 2X7 services or 8X5 services) 15 Network Users Configuration Data Management Decision Performance & Traffic Data New Technology Engineering Group - Network Planning & Design TT Restoration Operations Group NOC I & M Group -Network Installation & Maintenance - Network Operations Fault TT Installation Figure 1.22. Network Management Functional Flow Chart Network Provisioning It consists of network planning and design and is the responsibility of engineering group. Network Operations and NOC NOC – Network operations center They are concerned with daily operation s of the network and providing network services ISO has defined fine OSI network management applications. Trouble ticket Administration It is part of fault management and is used to track problems in the network. Configuration Management There are three types of configuration managements. 1. Static Configuration – it is permanent configuration of the network. Come up if network started from idle status. 2. current running configuration. 16 3. planned configuration – for future. Security Management physically securing the network and controlling access to the network by the users, a security database is established and maintained by the NOC for access to the network and network information. Performance Management Network statistics include data on traffic, network availability and network delay. Accounting Management The NOC administers costs and allocates the use of the network. Metrics are established to measure the usage of resources and services. System reports – for network operations to track the activities Management reports – performance of NOC & network User reports – status of network performance Network Installation and Maintenance Takes care of all installation and maintenance of equipment and cables. Network and System Management System management as the management of systems and system resources in the network. Network management is concerned with network resources such as hubs, switches, bridges, routers and gateways, and the connectivity among them via a network. It is relatively simple for a vendor to develop a network management system to manage a network of components it produced. To connect different vendor components require installation of multiple network management systems. Common management system as well as the integration of different management systems ad their inter operability has played a major role in the network management arena in the past decade. Transport Protocols are the first 4 layers of OSI model and TCP/IP over any of the first two layers of the seven-layer OSI model. 17 Network management Components NMS Network Agent Network Agent Network Objects Network Objects Figure 1.24 Network Management Components Each network agent monitors its respective objects. Interoperability NMS Vendor A Messages Services & Protocols NMS Vendor B Network Agent Network Agent Network Agent Network Agent Network Objects Network Objects Network Objects Network Objects 18 Application Services Objects Objects Management Protocol Vendor A Objects Vendor B Objects Transport Protocols (b) Services and Protocols Figure 1.23 Network Management Dumbbell Architecture (b) application services are the management related applications such as fault and configuration management. The management protocols are CMIP (Common management information protocol) for OSI model and SNMP for Internet model. As the two NMS’s communicate, each NMS can superimpose the data from the other and present an integrated picture to the network administrator. Another area of system management is logging and archiving events. Network Management System Platform High – end systems are housed either on SUN or HP unix-based workstations. Some run on windows-NT based PC. Low-end NMS run either on Windows 95/98 or NT. Common troubleshooting and monitoring network element parameters could be done by using simple networking and network management tools. These are part of TCP/IP stack. Current Status and future of Network Management The current network management systems are based on the SNMP Protocol. Current NMS has several limitations. 1. They need a dedicated NMS monitoring station, which must be on a specific type of platform 2. limit of an SNMP- based management system is that the values of the managed objects should be defined as scalar values. 3. CMIP (OSI model) is object- oriented. Complexity of specifications of managed objects, enormous memory required to handle CMIP. 4. SNMP – a polling based system. NMS polls each agent as to its status, or for any data that it needs for network management. 19 5. SNMP – have been overcome by the emerging web-based management. A web-based system is plat form – independent for the management software using java language in the managed components, for the web-based NMS server, as well as for web-browser monitors. Object-oriented technology is reaching a mature state and hardware capacity to handle object-oriented stacks is now commercially available. Two potential web-based management schemes 1. JMX – Java management extensions – developed by SUN 2. WBEM – Web based enterprise management – based on common information model developed by Microsoft. Another re-emerging technology on the horizon for network management is wireless technology. This is being deployed widely for WAN, mobile and broadband access services. An active network, which is the direction of the next generation network, would include embedded network management applications. A single failure in a network can cause multiple symptoms and manifest itself in multiple locations. The fault can propagate in space and time across the network. With the proliferation of the Internet, securing networks and communication has become extremely important. Existing management standards do not go far enough in this. Prepared By Sivakumar P V 20