Remote Access and Mobile Working Policy
advertisement

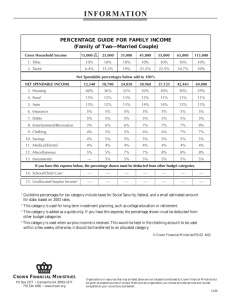
Remote Access and Mobile Working Policy & Guidance COMMERCIALISM INTEGRITY STEWARDSHIP COMMERCIALISM INTEGRITY STEWARDSHIP Document Control Document Details Author Adrian Last Company Name The Crown Estate Division Name Information Services Document Name Remote Access and Mobile Working Policy Version Date 11/08/11 Effective Date 1 November 2012 Issue THREE Review Date October 2013 May 2007 Change Record Modified Date Author Version Description of Changes 12/05/2010 Clare Kelly 1.1 Incorporates amendments by TB, CK and NS 04/05/2011 R McCaughan 1.2 Incorporated VPN policy 06/07/2011 S Smith 1.3 Review on behalf of Service Desk 09/08/2011 S Smith 1.4 References made to Edge and Direct Access 15/10/2012 S Smith 1.5 Removed references soley to Smartphones and replaced with mobile devices. Add statement for Apple’s Common Criteria Certification Security Statement 17/10/2012 A R Last 1.6 Annual review Stakeholder Sign–off Name Position Nigel Spencer Information Services Manager Signature Date July 2011 Clare Kelly IT Support Manager July 2011 Nigel Spencer Head of IS October 2012 Security Sign-off Name Position Signature Date Adrian Last Business Support Manager August 2011 Adrian Last ISMS Manager October 2012 1 COMMERCIALISM INTEGRITY STEWARDSHIP Table of Contents 1. Purpose 3 2. Scope 3 3. Policy 3 3.1. Policy Statement 3 3.2. Policy Objectives 3 3.3. Policy Overview 3 3.4. Policy Maintenance 4 4. Policy Requirements 4 4.1. General 4 4.2. Documentation and Data 4 4.3. Working Remotely 5 4.4. General Rules & Principles of VPN’s (Virtual Private Networks) 5 4.5. Telephone 6 4.6. Direct Access 6 4.7. Edge devices (Homeworker solution) 6 4.8. Reporting Security Incidents 6 4.9. Business Continuity 6 4.10. User Awareness 6 5. Disciplinary Process 6 6. Deviations from Policy 7 7. Glossary of Terms 7 Appendix A – List of related documents, procedures and processes 8 2 COMMERCIALISM INTEGRITY STEWARDSHIP 1. Purpose The purpose of this policy is to protect the confidentiality, integrity and availability of The Crown Estate’s information by controlling remote access to its IT systems and to define standards for connecting to The Crown Estate’s network from any host. 2. Scope The scope of this policy applies to: • The Crown Estate’s personnel, temporary staff, contractors and service providers utilising The Crown Estate’s information system resources from a remote location; and • Information system resources, including data networks, LAN servers and personal computers (stand-alone or network-enabled) located on The Crown Estate and non-Crown Estate locations, where these systems are under the jurisdiction and/or ownership of The Crown Estate, and any personal computers and/ or servers authorised to access The Crown Estate’s data networks. Third parties shall also adhere to this policy. May 2007 • Remote access connections used to do work on behalf of The Crown Estate, including reading, sending email and viewing intranet web resources from all types of equipment. 3. Policy 3.1. Policy Statement The Crown Estate’s information system resources are assets important to The Crown Estate’s business and stakeholders and its dependency on these assets demands that appropriate levels of information security be instituted and maintained. It is The Crown Estate’s policy that appropriate remote access control measures are implemented to protect its information system resources against accidental or malicious destruction, damage, modification or disclosure, and to maintain appropriate levels of confidentiality, integrity and availability of such information system resources. 3.2. Policy Objectives The objectives of this policy with regard to the protection of information system resources against unauthorised access from remote locations are to: • Minimise the threat of accidental, unauthorised or inappropriate access to either electronic or paper-based information owned by The Crown Estate or temporarily entrusted to it; • Minimise The Crown Estate’s network exposure, which may result in a compromise of network integrity, availability and confidentiality of information system resources; and • Minimise reputation exposure, which may result in loss, disclosure or corruption of sensitive information and breach of confidentiality. 3.3. Policy Overview The Crown Estate information system resources are important business assets that are vulnerable to access by unauthorised individuals or unauthorised remote electronic processes. Sufficient precautions are required to prevent and detect unwanted access from unauthorised users in remote locations. Users should be made aware of the dangers of unauthorised remote access, and managers should, where appropriate, introduce special controls to detect or prevent such access. 3 COMMERCIALISM INTEGRITY STEWARDSHIP 3.4. Policy Maintenance Supporting standards, guidelines and procedures will be issued on an ongoing basis by The Crown Estate. Users will be informed of any subsequent changes or updated versions of such standards, guidelines and procedures by way of e-mail or other relevant communication media. Users shall then have the obligation to obtain the current information systems policies from The Crown Estate intranet (i-site) or other relevant communication media on an ongoing basis and accept the terms and conditions contained therein. 4. Policy Requirements The Crown Estate’s information system resources shall be appropriately protected to prevent unauthorised remote access. May 2007 4.1. General • It is the responsibility of The Crown Estate’s employees, contractors, vendors and agents with remote access privileges to The Crown Estate’s corporate network to ensure that their remote access connection is given the same consideration as their on-site connection to The Crown Estate. • IT equipment provided to the employee to support working from home is for the exclusive use of that employee alone • The only permitted remote access method for non Crown Estate computers is via terminal services or The Crown Estate Extranet or the Guest Wireless Network if at one of The Crown Estate Office’s offering that facility. • Mobile devices e.g Blackberrys, smartphones, iPhones and iPads are managed and supported by The Crown Estate IT Service Desk. • Users are permitted to connect their personal mobile devices to The Crown Estate email system. However, the IT Service Desk will only provide support for this method of connection on a goodwill basis. Furthermore, it is the responsibility of the user to ensure that their personal mobile device is protected by a password. If that device is lost or stolen then it is the responsibility of the user to advise their mobile provider and arrange for the device to be removed from the service. If the IT Service Desk believes that access to The Crown Estate email systems is occurring without adequate security provisions, this facility will be withdrawn immediately and a request for the mobile device to be wiped will be issued. • The use of external email accounts (i.e. Hotmail, Yahoo, AOL), or other external resources to conduct The Crown Estate business is forbidden. • The ISMS Committee will be the final arbiter for methods of connection to The Crown Estate corporate IT network. 4.2. Documentation and Data • All sensitive and business critical documentation belonging to The Crown Estate and being used at a remote location must be securely stored and not displayed in a manner which allows its content to be viewed by unauthorised persons. • Data and documents belonging to The Crown Estate must not be stored on personal equipment unless permission from the Line Manager has been obtained. Any data stored on personal equipment must be encrypted, using advice obtained from the IT Service Desk. • iPhones and iPads are managed and supported using Apple’s “Common Criteria Certification” 4 COMMERCIALISM INTEGRITY STEWARDSHIP Security Statement. 4.3. Working Remotely • Employees wishing to work away from the office occasionally must secure the agreement of their Line Manager prior to the actual date of working remotely. When approving requests, Line Managers are responsible for ensuring that there is a clear business requirement for the employee to undertake work remotely rather than attending the office. • Retrospective requests will not normally be agreed and any absence may be considered as unauthorised, which may lead to disciplinary action being taken. • Employees wishing to work from their own equipment should ensure that their hardware and software configuration complies with The Crown Estate’s minimum requirements. This check should be done before the date on which they have booked to work remotely to ensure that any necessary patches or updates can be implemented. See Remote Access Via Terminal Services User Guide on I-Site. It is the responsibility of the user to ensure their own equipment is patched accordingly. The IT Service Desk will advise the user only on suggested actions but they will not action any changes to non-Crown Estate equipment. May 2007 • Subject to line management approval and hardware availability a laptop or other equipment may be provided if the employee intends to work remotely on a more frequent basis. • The Crown Estate will retain ownership of the equipment and also insure and maintain the equipment. • The employee must take good care of the equipment and ensure that it be used in accordance with The Crown Estate’s full range of policies. • Alternatively, the employee has access to pool laptops which, subject to availability, can be used when required. • When working in a public area, for instance on a train, the employee must take all reasonable steps to ensure that The Crown Estate’s information remains confidential and secure. The employee must ensure that any documents/laptop screens are, as much as possible, not readily visible to members of the public. 4.4. General Rules & Principles of Virtual Private Networks (VPNs) • It is the responsibility of employees with VPN privileges to ensure that unauthorized users are not allowed access to The Crown Estate internal networks. • VPN use is to be controlled using either a one-time password authentication such as a token device or a public/private key system with a strong passphrase. • When actively connected to the corporate network, VPNs will force all traffic to and from the PC over the VPN tunnel: all other traffic will be dropped. • Dual (split) tunnelling is NOT permitted; only one network connection is allowed. • VPN gateways will be set up and managed by The Crown Estate network operational groups. • All computers connected to The Crown Estate internal networks via VPN or any other technology must use the most up-to-date anti-virus software that is the corporate standard (provide URL to this software); this includes personal computers. • VPN users will be automatically disconnected from The Crown Estate’s network after thirty minutes of inactivity. The user must then logon again to reconnect to the network. Pings or other artificial network processes are not to be used to keep the connection open. • Users of computers that are not The Crown Estate-owned equipment must configure the 5 COMMERCIALISM INTEGRITY STEWARDSHIP equipment to comply with The Crown Estate’s Network related policies. • Only Crown Estate approved VPN clients may be used. • By using VPN technology with personal equipment, users must understand that their machines are a de facto extension of The Crown Estate’s network, and as such are subject to the same rules and regulations that apply to The Crown Estate-owned equipment, i.e., their machines must be configured to comply with The Crown Estate’s information security policies. 4.5. Telephone • The Crown Estate will provide external access to voicemail (via Outlook Web Access via the extranet) which the employee will be required to check on a regular basis when working away from the office. • Any application for a mobile phone will need to be agreed by the employee’s Line Manager and reviewed by the IT Service Desk on a case-by-case basis. May 2007 4.6. Direct Access • The Crown Estate will provide external access to members of the business who use a laptop via the Microsoft “Direct Access” method. • See 4.4 “General Rules & Principles of Virtual Private Networks (VPNs)” for expectations and responsibilities. 4.7. Edge devices (Homeworker solution) • Where The Crown Estate provides exceptionally a full Homeworker solution it is expected that that all equipment provided will be used solely for work on behalf of The Crown Estate. • See 4.4 “General Rules & Principles of VPN’s (Virutal Private Networks)” • Management and HR approval is required for the above solution. 4.8. Reporting Security Incidents All security incidents, including actual or potential unauthorised access to The Crown Estate’s information systems via remote access, should be reported immediately to the ISMS Manager or Head of IS. 4.9. Business Continuity Business continuity plans may include provision for working from home or other remote locations in the event of The Crown Estate’s corporate headquarters or other premises being unavailable for a significant period of time. 4.10. User Awareness Users commencing remote working will be made aware by their Line Manager of this policy and all its provisions. 5. Disciplinary Process The Crown Estate reserves the right to audit compliance with this policy from time to time. Any disciplinary action, arising from breach of this policy, shall be taken in accordance with The Crown Estate’s Rules and Disciplinary Code as amended from time to time. Disciplinary action may ultimately lead to dismissal. 6 COMMERCIALISM INTEGRITY STEWARDSHIP May 2007 7 COMMERCIALISM INTEGRITY STEWARDSHIP 6. Deviations from Policy Unless specifically approved, any deviation from this policy is strictly prohibited. Any deviation from or non-compliance with this policy will be reported to the ISMS Manager & Head of IS. 7. Glossary of Terms The terms used in this policy document are to be found in ISMS Glossary of Terms. In particular, “Remote Access and Mobile Working” is defined as the means of using The Crown Estate’s electronic information resources from a remote location in a way which ensures that they are available only to persons authorised to view or process that information in accordance with predetermined rules. May 2007 8