6 IPSec, SA and Crypto Lists
advertisement

6
IPSec, SA and Crypto Lists
6.1
Introduction
Encryption involves encryption keys using a standard encryption algorithm.
Public key encryption uses asymmetric encryption, where a public and private
key are generated for each side. This is known as asymmetric encryption. This
form of encryption is fairly processor intensive, and tends not to be used in
real-time applications. With private key encryption, a shared key is used which
is either setup on the devices, or is passed in a secure way. In summary the
methods are:
-
-
Symmetric encryption. With this the two devices get their shared key using
IKE, and then use a private key encryption method such as DES, 3DES or
AES.
Asymmetric encryption. With this the two devices generate their own
public and private keys, and pass their public keys to each other, which are
then used to encrypt the data. Only the private keys for the devices can
decrypt the data. The RSA encryption algorithm is a typical asymmetric
algorithm.
IPSec supports many different types of encryption, thus it supports a Security
Association (SA) which negotiates the details of the secure connection. With
this the SA is created when the first packet of a flow matches a defined access
list (ACL) on one endpoint of the SA. This requires IKE (Internet Key exchange),
and uses a technique called ISAKMP, using an asymmetric public key technique.
The next stages are:
-
Authentication. This authenticates the devices to each other.
Encryption. This negotiate the encryption used, using a single exchanged
key using DES or 3DES symmetric encryption.
Notice that public key encryption is only used in the authentication, and
encryption negotiation, as public-key encryption would possibly have a large
processing overhead on large amounts of data. Thus:
IKE:
Authentication:
Encryption:
6.2
Asymmetric public key to secure the connection.
Asymmetric public key.
Single exchanged key. Symmetric encryption algorithm.
Key interchange
If a private, shared-key is used there must be some way to pass this key
securely, such as from the remote host or from a trusted key distribution centre
(as illustrated in Figure 6.1). One of the best methods is to use Diffie-Hellman,
which allows for information to be passed between two hosts, after which they
should both have the same shared-key. This process is relatively secure, where
Unit 6: IPSec, SA and Crypto Lists 1
listeners cannot determine the shared key, even if they listen to both
communications. Figure 6.2 illustrates the process, and Figure 6.3 shows an
example.
The Diffie-Hellman method, unfortunately, suffers from the man-in-themiddle attack, where an intruder could listen for the A and B values which are
passed, and pass its own values. A KDC (key distribution center) overcomes
these problems with a single key and a secure channel for authentication. In a
KDC, the authentication and session keys are managed through the KDC.
Trusted
Key Distribution
Centre
Key distribution
centre sends the
required key
Bank
Of Edinburgh
Internet
Spoof Bank
Of Edinburgh
The Diffie-Hellman method can be
used to pass secret keys between the
parties.
Figure 6.1 Diffie-Hellman process
Untrusted
network
1. Both nodes agree on two values (g and n)
2. Generate a random value (x)
2. Generate a random value (y)
3. A = Gx mod n
3. B = Gy mod n
5. K1 = Bx mod n
4. A and B
Values are
exchanged
5. K2 = Ay mod n
K1 and K2 should be the same and are the secret key
Figure 6.2 Diffie-Hellman process
2
Network security - W.Buchanan
Untrusted
network
1. Both nodes agree on two values (5 and 4)
2. Generate a random value (3)
3. A =
53
2. Generate a random value (4)
3. B = 54 mod 4=1
mod 4=5
This is the remainder
From an integer divide
5. K1 = 15 mod 4 = 1
4. A and B
Values are
exchanged
5. K2 = 54 mod 4 = 1
K1 and K2 should be the same and are the secret key
Figure 6.3 Example Diffie-Hellman process
6.3
IPSec
IPSec is used to create a secure connection for data packets over a public
network. It is basically a framework which supports:
-
-
-
Encryption. IPSec can support symmetric or asymmetric encryption, but
typically uses the method illustrated in Figure 6.4, where a shared key is
used to encrypt the data, and the public key is used to provide
authentication. To generate the secret keys it uses IKE (Internet Key
Exchange - using Diffie-Hellman) which have a certain life time (such as 10
hours), after which new keys are automatically created. Once the secret key
is created, the routers can then use an encryption method such as DES,
3DES or AES to encryption the data packets.
Authentication. Once the secret key has been created the public and private
keys are used to authenticate devices, where the hashed value is generated
using either MD5 or SHA, and is then encrypted using the private key of the
device. Only the device’s public key can be used to decrypt it. The remote
device will check it with its expected hashed value, and if they are the same,
the device which sent the authentication has been authenticated.
IPSec protocol. The IPSec protocol is either ESP (Encapsulated Security
Protocol), or AH (Authentication Header). ESP takes the original data packet,
and breaks off the IP header. The rest of the packet is encrypted, with the
original header added at the start, along with a new ESP field at the start,
and one at the end (Figure 6.5). It is important that the IP header is not
encrypted as the data packet must still be read by routers as it travels over
the Internet. Only the host at the other end of the IPSec tunnel can decrypt
the contents of the IPSec data packet. The other protocol is AH which
encrypts the complete contents of the IP data packet, and adds a new packet
header.
Unit 6: IPSec, SA and Crypto Lists 3
ESP has the weakness that an intruder can replay previously sent data, whereas
AH provides a mechanism of sequence numbers to reduce this problem.
IPSec can either be used in a tunnel mode, where part of the transmission
is secured, or with a transport mode, where the security is applied from host-to
–host, as illustrated in Figure 6.6.
Kpb1 Public key passed (Kpb1)
Kpb2
Public key passed (Kpb2)
Kpv1
Kpv2
Shared-key passed
(used to encrypt
all data and
authentication)
Hashed
value
Authentication
Encryption
Encryption
Figure 6.4 Using symmetric encryption and asymmetric authentication
ESP
header
IP packet
Contents (enc)
ESP
IP
header header
ESP
header
IP packet
Contents (enc)
ESP
IP
header header
IP packet
contents
IP
header
IP packet
contents
IP
header
Figure 6.5 IPSec packet conversion
4
Network security - W.Buchanan
Hashed
value
Tunnel mode
Transport mode
Figure 6.6 IPSec packet conversion
6.4
PIX Configuration (IKE)
The ends of an IPSec connection can be a router, a PIX device, or any other host
which supports IPSec. In Cisco devices, the main configuration command used
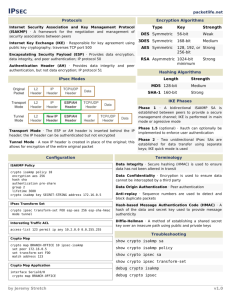
for setting up IPSec is isakmp. On a PIX, the basic usage is:
pixfirewall(config)# isakmp
Usage: isakmp policy <priority> authen <pre-share|rsa-sig>
isakmp policy <priority> encrypt <aes|aes-192|aes-256|des|3des>
isakmp policy <priority> hash <md5|sha>
isakmp policy <priority> group <1|2|5>
isakmp policy <priority> lifetime <seconds>
isakmp key <key-string> address <ip> [netmask <mask>] [no-xauth] [noconfig-mode]
isakmp enable <if_name>
isakmp identity <address|hostname|key-id> [<key-id-string>]
isakmp keepalive <seconds> [<retry seconds>]
isakmp nat-traversal [<natkeepalive>]
isakmp client configuration address-pool local <poolname> [<pif_name>]
isakmp peer fqdn|ip <fqdn|ip> [no-xauth] [no-config-mode]
A PPLY TO IKE TO AN INTERFACE. Initially IKE is enabled on an interface (such as
on the outside interface):
isakmp enable outside
D EFINE SHARED KEY FOR DIFFIE-HELLMAN. Next the Diffie-Hellman process
requires a key-string, such as ABC&FDD, which will be used with a peer at the
address of 176.16.0.2 (which has a subnet mask of 255.255.255.255 so that it is
only one host):
isakmp key ABC&FDD address 176.16.0.2 netmask 255.255.255.255
D EFINE RSA HOST/A DDRESS. The other side will use the same pre-shared key.
Next, if RSA encryption is being used for the public-key encryption, the
Unit 6: IPSec, SA and Crypto Lists 5
hostname, or its address can be used to generate the RSA encryption. This is
achieved using an address with:
isakmp identity address
D EFINE P OLICY NUMBER. Each IKE has a policy number, where a 1 is the highest
priority. Thus a higher value is typically used so that higher priorities can
inserted at a future time. The following defines a policy number of 5 and that a
pre-shared key is used (otherwise rsa-sig can be defined):
isakmp policy 5 authen pre-share
D EFINE ENCRYPTION TYPE. Then the encryption type can be defined, such as for
the DES encryption algorithm (others include aes, aes-192, aes-256, and 3des):
isakmp policy 5 encrypt des
D EFINE HASHING FUNCTION. Next the hashing technique needs to be defined, as
this will be used in the authentication process. The method methods are MD5
and SHA. As SHA has a larger hash code, and thus has less chance of creating
the same signature for different unhashed values, it is typically used for
enhanced security. Thus to define SHA:
isakmp policy 5 hash sha
D EFINE D IFFIE-HELLMAN TYPE. Next the Diffie-Hellman method type is defined.
For 768-bit Diffie-Hellman a Group 1 is used, while 1024-bit Diffie-Hellman
uses Group 2, and 1582-bit Diffie-Hellman uses Group 5. Thus to setup Group
1 settings:
isakmp policy 5 group 1
D EFINE L EASE TIME. Finally the default lifetime is defined in terms of seconds.
Thus to setup a period of 1 day (86,400 seconds) the following can be defined:
isakmp policy 5 lifetime 86400
6.5
PIX Configuration (IPSec)
Once the IKE is setup, the IPSec parameters can be defined. First we must allow
the IPsec packets to pass through the PIX. Normally these would be interrupted
by ACLs, which must be bypassed. To do this the following is used:
sysopt connection permit-ipsec
The crypto command is then used to define the encryption used, and define a
mapping. Its usage is:
Usage:
6
[ show ] crypto { ca | dynamic-map | ipsec | isakmp | map | sa } ...
Network security - W.Buchanan
show crypto engine [verify]
[ show | clear ] crypto interface [counters]
The first configuration defines the security protocol defined between the peers.
The following defines a transform set named MYIPSECFORMAT which uses DES
for encapsulating security payload (ESP) and SHA for the authentication:
crypto ipsec transform-set MYIPSECFORMAT esp-des esp-sha-hmac
D EFINE CRYPTO MAP. Next a crypto map can be defined, where MYIPSEC defines
the name associated with the map and 10 is a sequence number. These
sequence numbers allow different crypto combinations to be set for different
peers which make connections on the interface that has the crypto map applied.
There can only be crypto map on each interface, thus sequence number blocks
can apply different policies to a specific crypto map:
crypto map MYIPSEC 10 ipsec-isakmp
D EFINE A CCESS CONTROL L IST. Next the access control list (number 111) can be
defined to specify the traffic which will be encrypted. In the following traffic
from 10.0.0.0/24 to 176.16.0.0/24 will be encrypted.
access-list 111 permit ip 10.0.0.0
255.255.255.0
176.16.0.0
255.255.255.0
A SSOCIATE A CCESS C ONTROL L IST. After this, an access list number can be defined
(in this case it is 111), where anything matching this list will either be encrypted
(for outgoing data) or decrypted (for incoming data) as defined by the crypto
map block (which is sequence number 10). Thus we can have different security
settings depending on the sequence number:
crypto map MYIPSEC 10 match address 111
D EFINE P EER FOR C RYPTO L IST. Next the peer which is associated with the crypto
map security policy defined:
crypto map MYIPSEC 10 set peer 176.16.0.2
D EFINE PEER FOR C RYPTO L IST. Next the type of hashing and/or encoding is
defined using the transform mapping:
crypto map MYIPSEC 10 set transform-set MYIPSECFORMAT
A PPLY ON AN INTERFACE. Next the crypto map can be applied onto an interface
(only one is allowed on each interface):
crypto map MYIPSEC interface outside
Unit 6: IPSec, SA and Crypto Lists 7
6.6
Router Configuration (IPSec)
Once the PIX is setup, the router on the other end can be setup for IPSec. The
commands used on Router 2 are then:
crypto isakmp policy 100
hash sha
authentication pre-share
and then the pre-share key for Diffie-Hellman is setup:
crypto isakmp key ABC&FDD address 176.16.0.1
and the transform set is defined with:
crypto ipsec transform-set mine esp-des
Next the crypto map can be setup with:
crypto map mymap 110 ispec-isakmp
set peer 176.16.0.1
set transform-set mine
match address 110
The access lists can be applied with:
access-list
access-list
access-list
access-list
access-list
101
101
101
110
110
permit ahp host
permit esp host
permit udp host
permit tcp host
deny ip any any
172.16.0.1
172.16.0.1
172.16.0.1
172.16.0.0
host 172.1.0.2
host 172.1.0.2
host 172.1.0.2 eq isakmp
0.0.0.255 172.1.0.2 0.0.0.255
This and the crypto map can then be applied to an interface with:
interface fa0/1
ip address access-group 101 in
crypto map mymap
6.7
Debug commands
The main debug commands are:
show crypto ipsec sa
show crypto isakmp sa
debug crypto isakmp
debug crypto ipsec
clear crypto ipsec sa
6.8
Show security associations.
Shows ISAKMP policy
Shows debug information for ISAKMP.
Show debug information for IPSec.
Clears associations.
Tutorial
6.8.1 Show for the Diffie-Hellman method, that if G=5, N=6, and the random
numbers are x=7 and y=5, that the shared key will be 5.
8
Network security - W.Buchanan