Certified Ethical Hacker
Version Comparison
Exam 312-50
Version Comparison
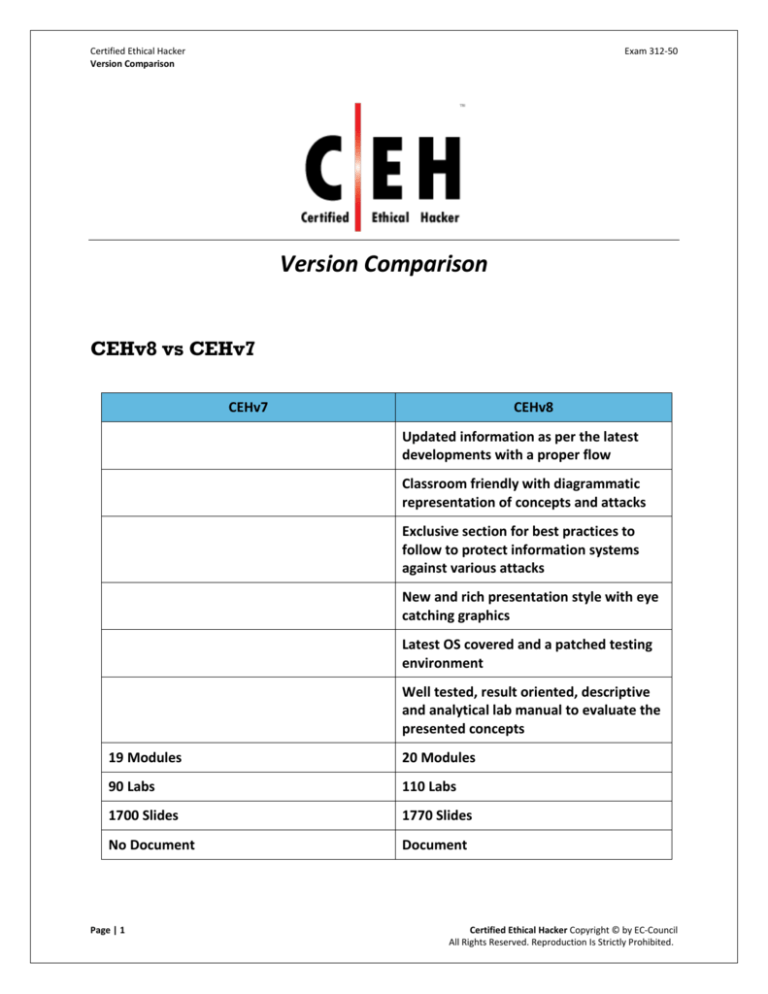
CEHv8 vs CEHv7
CEHv7
CEHv8
Updated information as per the latest
developments with a proper flow
Classroom friendly with diagrammatic
representation of concepts and attacks
Exclusive section for best practices to
follow to protect information systems
against various attacks
New and rich presentation style with eye
catching graphics
Latest OS covered and a patched testing
environment
Well tested, result oriented, descriptive
and analytical lab manual to evaluate the
presented concepts
19 Modules
20 Modules
90 Labs
110 Labs
1700 Slides
1770 Slides
No Document
Document
Page | 1
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Module Comparison of CEHv8 with CEHv7
Introduction to Ethical Hacking
Hacking refers to exploiting system vulnerabilities and compromising security controls to gain
unauthorized or inappropriate access to the system resources. The topics highlighted in red
under CEHv8 Module 01: Introduction to Ethical Hacking are the new additions.
CEHv7 Module 01: Introduction to Ethical
Hacking
CEHv8 Module 01: Introduction to Ethical
Hacking
Data Breach Investigations Report
Data Breach Investigations Report
Essential Terminologies
Essential Terminologies
Elements of Information Security
Elements of Information Security
Effects of Hacking on Business
Top Information Security Attack Vectors
Who Is a Hacker?
Motives, Goals, and Objectives of
Information Security Attacks
Hacking Phases
Information Security Threats
Types of Attacks on a System
Information Warfare
Why Ethical Hacking is Necessary
IPv6 Security Threats
Skills of an Ethical Hacker
Hacking vs. Ethical Hacking
Vulnerability Research
Effects of Hacking on Business
What Is Penetration Testing?
Who Is a Hacker?
Hacking Phases
Types of Attacks on a System
Why Ethical Hacking is Necessary
Skills of an Ethical Hacker
Incident Management Process
Types of Security Policies
Page | 2
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Vulnerability Research
What Is Penetration Testing?
Footprinting and Reconnaissance
Footprinting refers to uncovering and collecting as much information as possible about a target
network, for identifying various ways to intrude into an organization’s network system. The
topics highlighted in red under CEHv8 Module 02: Footprinting and Reconnaissance are the
new additions.
CEHv7 Module 02: Footprinting and
Reconnaissance
CEHv8 Module 02: Footprinting and
Reconnaissance
Footprinting Terminologies
Footprinting Terminologies
What Is Footprinting?
What Is Footprinting?
Objectives of Footprinting
Objectives of Footprinting
Footprinting Threats
Footprinting Threats
Footprinting through Search Engines
Footprinting through Search Engines
Website Footprinting
Website Footprinting
Email Footprinting
Email Footprinting
Competitive Intelligence
Competitive Intelligence
Footprinting Using Google
Footprinting Using Google
WHOIS Footprinting
WHOIS Footprinting
DNS Footprinting
DNS Footprinting
Network Footprinting
Network Footprinting
Footprinting Tools
Footprinting through Social Engineering
Footprinting Countermeasures
Footprinting through Social Networking
Sites
Page | 3
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Footprinting Pen Testing
Exam 312-50
Footprinting Tools
Footprinting Countermeasures
Footprinting Pen Testing
Footprinting Terminologies
What Is Footprinting?
Scanning Networks
Network scanning refers to a set of procedures for identifying hosts, ports, and services in a
network. The topics highlighted in red under CEHv8 Module 03: Scanning Networks are the
new additions
CEHv7 Module 03: Scanning Networks
CEHv8 Module 03: Scanning Networks
Overview of Network Scanning
Overview of Network Scanning
CEH Scanning Methodology
CEH Scanning Methodology
Checking for Live Systems
Checking for Live Systems
Scanning Techniques
Scanning IPv6 Network
IDS Evasion Techniques
Scanning Techniques
Banner Grabbing
IDS Evasion Techniques
Vulnerability Scanning
Banner Grabbing
Drawing Network Diagrams
Vulnerability Scanning
Proxy Chaining
Drawing Network Diagrams
HTTP Tunneling Techniques
Proxy Chaining
SSH Tunneling
HTTP Tunneling Techniques
Anonymizers
SSH Tunneling
IP Spoofing Detection Techniques
Anonymizers
Scanning Countermeasures
IP Spoofing Detection Techniques
Scanning Pen Testing
Scanning Countermeasures
Scanning Pen Testing
Latest Network Scanning Tools Added
Page | 4
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
6 more Labs Added
Enumeration
In the enumeration phase, attacker creates active connections to system and performs directed
queries to gain more information about the target. The topics highlighted in red under CEHv8
Module 04: Enumeration are the new additions.
CEHv7 Module 04: Enumeration
CEHv8 Module 04: Enumeration
What Is Enumeration?
What Is Enumeration?
Techniques for Enumeration
Techniques for Enumeration
NetBIOS Enumeration
Services and Ports to Enumerate
Enumerate Systems Using Default Passwords NetBIOS Enumeration
SNMP Enumeration
Enumerate Systems Using Default
Passwords
UNIX/Linux Enumeration
SNMP Enumeration
LDAP Enumeration
Working of SNMP
NTP Enumeration
UNIX/Linux Enumeration
SMTP Enumeration
LDAP Enumeration
DNS Enumeration
NTP Enumeration
Enumeration Countermeasures
SMTP Enumeration
Enumeration Pen Testing
DNS Enumeration
Enumeration Countermeasures
Enumeration Pen Testing
Latest Enumeration Tools Added
1 more Lab Added
Page | 5
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
System Hacking
Password cracking techniques are used to recover passwords from computer systems. The
topics highlighted in red under CEHv8 Module 05 System Hacking are the new additions.
CEHv7 Module 05 System Hacking
CEHv8 Module 05 System Hacking
System Hacking: Goals
System Hacking: Goals
CEH Hacking Methodology (CHM)
CEH Hacking Methodology (CHM)
Password Cracking
Password Cracking
Microsoft Authentication
Stealing Passwords Using Keyloggers
How to Defend against Password Cracking
Microsoft Authentication
Privilege Escalation
How to Defend against Password Cracking
Types of Privilege Escalation
Privilege Escalation
Executing Applications
Types of Privilege Escalation
Types of Keystroke Loggers and Spywares
Executing Applications
Anti-Keylogger and Anti-Spywares
Methodology of Attacker in using Remote
Keylogger
Detecting Rootkits
Types of Keystroke Loggers and Spywares
NTFS Stream Manipulation
Anti-Keylogger and Anti-Spywares
Classification of Steganography
Various methods to place a rootkit
Steganalysis Methods/Attacks on
Steganography
Detecting Rootkits
Covering Tracks
NTFS Stream Manipulation
Penetration Testing
Application of steganography
Classification of Steganography
Audio Steganography Methods
Issues in Information hiding
Steganalysis Methods/Attacks on
Steganography
Detecting Text, Image, Audio, and Video
Steganography
Covering Tracks
Penetration Testing
Page | 6
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Trojans and Backdoors
It is a program in which the malicious or harmful code is contained inside apparently harmless
programming or data in such a way that it can get control and cause damage, such as ruining
the file allocation table on your hard disk. The topics highlighted in red under CEHv8 Module
06: Trojans and Backdoors are the new additions.
CEHv7 Module 06: Trojans and Backdoors
CEHv8 Module 06: Trojans and Backdoors
What Is a Trojan?
What Is a Trojan?
What Do Trojan Creators Look For
What Do Trojan Creators Look For
Indications of a Trojan Attack
Indications of a Trojan Attack
Common Ports used by Trojans
Common Ports used by Trojans
How to Infect Systems Using a Trojan
How to Infect Systems Using a Trojan
Different Ways a Trojan can Get into a
System
Different Ways a Trojan can Get into a
System
How to Deploy a Trojan
How to Deploy a Trojan
Types of Trojans
Types of Trojans
How to Detect Trojans
Trojan Analysis
Trojan Countermeasures
How to Detect Trojans
Trojan Horse Construction Kit
Trojan Countermeasures
Anti-Trojan Software
Trojan Horse Construction Kit
Pen Testing for Trojans and Backdoors
Anti-Trojan Software
Pen Testing for Trojans and Backdoors
Latest Trojan Detection Tools Added
2 more Labs Added
Page | 7
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Viruses and Worms
A virus is a self-replicating program that produces its own code by attaching copies of itself into
other executable codes. The topics highlighted in red under CEHv8 Module 07: Viruses and
Worms are the new additions.
CEHv7 Module 07: Viruses and Worms
CEHv8 Module 07: Viruses and Worms
Introduction to Viruses
Introduction to Viruses
Stages of Virus Life
Stages of Virus Life
Working of Viruses
Working of Viruses
Indications of Virus Attack
Common Techniques Used to Distribute
Malware on the Web
How does a Computer Get Infected by
Viruses
Indications of Virus Attack
Types of Viruses
How does a Computer Get Infected by
Viruses
Virus Maker
Virus Analysis
Computer Worms
Types of Viruses
Worm Analysis
Virus Maker
Worm Maker
Computer Worms
Malware Analysis Procedure
Worm Analysis
Online Malware Analysis Services
Worm Maker
Virus and Worms Countermeasures
Malware Analysis Procedure
Antivirus Tools
Online Malware Analysis Services
Penetration Testing for Virus
Virus Detection Methods
Virus and Worms Countermeasures
Antivirus Tools
Penetration Testing for Virus
Page | 8
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Sniffers
Packet sniffing is a process of monitoring and capturing all data packets passing through a given
network using software (application) or hardware device. The topics highlighted in red under
CEHv8 Module 08: Sniffing are the new additions.
CEHv7 Module 08: Sniffers
CEHv8 Module 08: Sniffing
Packet Sniffing
Packet Sniffing
Sniffing Threats
Sniffing Threats
Types of Sniffing Attacks
Types of Sniffing Attacks
Hardware Protocol Analyzers
Hardware Protocol Analyzers
MAC Flooding
IPv6 Addresses
How DHCP Works
MAC Flooding
Rogue DHCP Server Attack
How DHCP Works
ARP Spoofing Techniques
Rogue DHCP Server Attack
ARP Poisoning Tools
ARP Spoofing Techniques
How to Defend Against ARP Poisoning
ARP Poisoning Tools
Spoofing Attack Threats
How to Defend Against ARP Poisoning
How to Defend Against MAC Spoofing
Spoofing Attack Threats
DNS Poisoning Techniques
MAC Spoofing Technique
How to Defend Against DNS Spoofing
IRDP Spoofing
Sniffing Tools
How to Defend Against MAC Spoofing
Sniffing Pen Testing
DNS Poisoning Techniques
How to Defend Against DNS Spoofing
Sniffing Tools
Sniffer Detection Technique
Sniffing Pen Testing
Page | 9
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Social Engineering
Social engineering is the art of convincing people to reveal confidential information. Social
engineers depend on the fact that people are unaware of their valuable information and are
careless about protecting it. The topics highlighted in red under CEHv8 Module 09: Social
Engineering are the new additions.
CEHv7 Module 09: Social Engineering
CEHv8 Module 09: Social Engineering
What Is Social Engineering?
What Is Social Engineering?
Factors that Make Companies Vulnerable to
Attacks
Factors that Make Companies Vulnerable
to Attacks
Warning Signs of an Attack
Warning Signs of an Attack
Phases in a Social Engineering Attack
Phases in a Social Engineering Attack
Common Targets of Social Engineering
Common Targets of Social Engineering
Human-based Social Engineering
Human-based Social Engineering
Computer-based Social Engineering
Computer-based Social Engineering
Social Engineering Through Impersonation
on Social Networking Sites
Mobile-based Social Engineering
Identify Theft
Mobile-based Social Engineering Using
SMS
Social Engineering Countermeasures
Social Engineering Through
Impersonation on Social Networking Sites
How to Detect Phishing Emails
Identify Theft
Identity Theft Countermeasures
Social Engineering Countermeasures
Social Engineering Pen Testing
How to Detect Phishing Emails
Identity Theft Countermeasures
Social Engineering Pen Testing
Social Engineering Toolkit
Page | 10
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Denial of Service
Denial of Service (DoS) is an attack on a computer or network that prevents legitimate use of its
resources. The topics highlighted in red under CEHv8 Module 10: Denial-of-Service are the new
additions.
CEHv7 Module 10: Denial of Service
CEHv8 Module 10: Denial-of-Service
What Is a Denial of Service Attack?
What Is a Denial of Service Attack?
What Are Distributed Denial of Service
Attacks?
What Are Distributed Denial of Service
Attacks?
Symptoms of a DoS Attack
Symptoms of a DoS Attack
DoS Attack Techniques
DoS Attack Techniques
Botnet
Botnet
Botnet Ecosystem
Botnet Ecosystem
DDoS Attack Tools
Botnet Trojans
DoS Attack Tools
DDoS Attack Tools
Detection Techniques
DoS Attack Tools
DoS/DDoS Countermeasure
Detection Techniques
Techniques to Defend against Botnets
DoS/DDoS Countermeasure
Advanced DDoS Protection Appliances
Techniques to Defend against Botnets
Denial of Service (DoS) Attack Penetration
Testing
Advanced DDoS Protection Appliances
Denial of Service (DoS) Attack Penetration
Testing
Latest DDoS and DoS attack tools added
Latest DoS/DDoS Protection Tools added
Page | 11
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Session Hijacking
Session Hijacking refers to the exploitation of a valid computer session where an attacker takes
over a session between two computers. The topics highlighted in red under CEHv8 Module 11:
Session Hijacking are the new additions.
CEHv7 Module 11: Session Hijacking
CEHv8 Module 11: Session Hijacking
What Is Session Hijacking?
What Is Session Hijacking?
Why Session Hijacking Is Successful?
Why Session Hijacking Is Successful?
Key Session Hijacking Techniques
Key Session Hijacking Techniques
Brute Forcing Attack
Brute Forcing Attack
Session Hijacking Process
Session Hijacking Process
Types of Session Hijacking
Types of Session Hijacking
Application Level Session Hijacking
Application Level Session Hijacking
Session Sniffing
Session Sniffing
Man-in-the-Middle Attack
Man-in-the-Middle Attack
Network Level Session Hijacking
Network Level Session Hijacking
TCP/IP Hijacking
TCP/IP Hijacking
Session Hijacking Tools
Session Hijacking Tools
Protecting against Session Hijacking
Protecting against Session Hijacking
IPsec Architecture
IPsec Architecture
Session Hijacking Pen Testing
Session Hijacking Pen Testing
Latest Session Hijacking Tools Added
Page | 12
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Hacking Webservers
Web server pen testing is used to identify, analyze, and report vulnerabilities such as
authentication weaknesses, configuration errors, protocol related vulnerabilities, etc. in a web
server. The topics highlighted in red under CEHv8 Module 12: Hacking Webservers are the new
additions.
CEHv7 Module 11: Session Hijacking
CEHv8 Module 11: Session Hijacking
IIS Webserver Architecture
IIS Webserver Architecture
Why Web Servers are Compromised?
Why Web Servers are Compromised?
Impact of Webserver Attacks
Impact of Webserver Attacks
Webserver Attacks
Webserver Attacks
Webserver Attack Methodology
Webserver Attack Methodology
Webserver Attack Tools
Webserver Attack Tools
Metasploit Architecture
Metasploit Architecture
Web Password Cracking Tool
Web Password Cracking Tool
Countermeasures
Countermeasures
How to Defend Against Web Server Attacks
How to Defend Against Web Server
Attacks
Patch Management
How to Defend against HTTP Response
Splitting and Web Cache Poisoning
Patch Management Tools
Patch Management
Webserver Pen Testing
Patch Management Tools
Latest Webserver Security Tools Added
Latest Webserver Pen Testing Tools Added
Webserver Pen Testing
Page | 13
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Hacking Web Applications
Web applications provide an interface between end users and web servers through a set of web
pages that are generated at the server end or contain script code to be executed dynamically
within the client web browser. The topics highlighted in red under CEHv8 Module 13: Hacking
Web Applications are the new additions.
CEHv7 Module 13: Hacking Web
Applications
CEHv8 Module 13: Hacking Web
Applications
How Web Applications Work
How Web Applications Work
Web Attack Vectors
Web Attack Vectors
Web Application Threats
Web Application Threats
Web App Hacking Methodology
Web App Hacking Methodology
Footprint Web Infrastructure
Footprint Web Infrastructure
Hacking Web Servers
Hacking Web Servers
Analyze Web Applications
Analyze Web Applications
Attack Authentication Mechanism
Attack Authentication Mechanism
Attack Authorization Schemes
Attack Authorization Schemes
Session Management Attack
Session Management Attack
Attack Data Connectivity
Attack Data Connectivity
Attack Web App Client
Attack Web App Client
Attack Web Services
Attack Web Services
Web Application Hacking Tools
Latest Web Application Hacking Tools
Countermeasures
Countermeasures
Web Application Security Tools
Latest Web Application Security Tools Added
Web Application Firewall
Web Application Firewall
Web Application Pen Testing
Web Application Pen Testing
Page | 14
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
SQL Injection
SQL Injection is the most common website vulnerability on the Internet. It is a flaw in Web
Applications and not a database or web server issue. The topics highlighted in red under CEHv8
Module 14: SQL Injection are the new additions.
CEHv7 Module 14: SQL Injection
CEHv8 Module 14: SQL Injection
SQL Injection
SQL Injection
SQL Injection Attacks
SQL Injection Attacks
SQL Injection Detection
SQL Injection Detection
SQL Injection Attack Characters
SQL Injection Attack Characters
Testing for SQL Injection
Testing for SQL Injection
Types of SQL Injection
Types of SQL Injection
Blind SQL Injection
Blind SQL Injection
SQL Injection Methodology
SQL Injection Methodology
Advanced SQL Injection
Advanced SQL Injection
Password Grabbing
Bypass Website Logins Using SQL Injection
Network Reconnaissance Using SQL Injection
Password Grabbing
SQL Injection Tools
Network Reconnaissance Using SQL Injection
Evasion Technique
Latest SQL Injection Tools Added
How to Defend Against SQL Injection Attacks
Evasion Technique
SQL Injection Detection Tools
How to Defend Against SQL Injection Attacks
Latest SQL Injection Detection Tools Added
2 more Labs Added
Page | 15
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Hacking Wireless Networks
Wi-Fi is developed on IEEE 802.11 standards, and it is widely used in wireless communication. It
provides wireless access to applications and data across a radio network. The topics highlighted
in red under CEHv8 Module 15: Hacking Wireless Networks are the new additions.
CEHv7 Module 15: Hacking Wireless
Networks
CEHv8 Module 15: Hacking Wireless
Networks
Types of Wireless Networks
Types of Wireless Networks
Wireless Terminologies
Wireless Terminologies
Types of Wireless Encryption
Types of Wireless Encryption
How to Break WEP Encryption
How to Break WEP Encryption
Wireless Threats
Wireless Threats
Footprint the Wireless Network
Footprint the Wireless Network
GPS Mapping
Mobile-based Wi-Fi Discovery Tools
Wireless Traffic Analysis
GPS Mapping
What Is Spectrum Analysis?
Wireless Traffic Analysis
How to Reveal Hidden SSIDs
What Is Spectrum Analysis?
Crack Wi-Fi Encryption
How to Reveal Hidden SSIDs
Wireless Hacking Tools
Crack Wi-Fi Encryption
Bluetooth Hacking
Latest Wireless Hacking Tools Added
How to BlueJack a Victim
Bluetooth Hacking
How to Defend Against Wireless Attacks
How to BlueJack a Victim
Wireless Security Tools
How to Defend Against Wireless Attacks
Wireless Penetration Testing
Latest Wireless Security Tools Added
Wireless Penetration Testing
1 more Lab Added
Page | 16
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Hacking Mobile Platforms
CEHv8 Module 16 Hacking Mobile Platforms is a new module which covers the following topics:
CEHv8 Module 16 Hacking Mobile Platforms
Mobile Attack Vectors
Guidelines for Securing Windows OS
Devices
Mobile Platform Vulnerabilities and
Blackberry Attack Vectors
Risks
Android OS Architecture
Guidelines for Securing BlackBerry
Devices
Android Vulnerabilities
Android Trojans
Mobile Device Management (MDM)
General Guidelines for Mobile
Platform Security
Securing Android Devices
Jailbreaking iOS
Mobile Protection Tools
Mobile Pen Testing
Guidelines for Securing iOS Devices
Windows Phone 8 Architecture
Evading IDS, Firewalls, and Honeypots
An intrusion detection system (IDS) gathers and analyzes information from within a computer
or a network, to identify the possible violations of security policy, including unauthorized
access, as well as misuse. The topics highlighted in red under CEHv8 Module 17: Evading IDS,
Firewalls, and Honeypots are the new additions.
CEHv7 Module 16: Evading IDS, Firewalls,
and Honeypots
CEHv8 Module 17: Evading IDS, Firewalls,
and Honeypots
Ways to Detect an Intrusion
Ways to Detect an Intrusion
Types of Intrusion Detection Systems
Types of Intrusion Detection Systems
General Indications of Intrusions
General Indications of Intrusions
Firewall Architecture
Firewall Architecture
Types of Firewall
Types of Firewall
Firewall Identification
Firewall Identification
Page | 17
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
How to Set Up a Honeypot
How to Set Up a Honeypot
Intrusion Detection Tools
Latest Intrusion Detection Tools Added
How Snort Works
How Snort Works
Firewalls
Firewalls
Honeypot Tools
Latest Honeypot Tools Added
Evading IDS
Evading IDS
Evading Firewalls
Evading Firewalls
Detecting Honeypots
Detecting Honeypots
Firewall Evasion Tools
Latest Firewall Evasion Tools Added
Packet Fragment Generators
Packet Fragment Generators
Countermeasures
Countermeasures
Firewall/IDS Penetration Testing
Firewall/IDS Penetration Testing
1 more Lab Added
Page | 18
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Buffer Overflow
A generic buffer overflow occurs when a program tries to store more data in a buffer than it
was intended to hold. The topics highlighted in red under CEHv8 Module 18: Buffer Overflow
are the new additions.
CEHv7 Module 17: Buffer Overflow
CEHv8 Module 18: Buffer Overflow
Heap-Based Buffer Overflow
Heap-Based Buffer Overflow
Knowledge Required to Program Buffer
Overflow Exploits
Why Are Programs and Applications
Vulnerable to Buffer Overflows?
Buffer Overflow Steps
Knowledge Required to Program Buffer
Overflow Exploits
Overflow Using Format String
Buffer Overflow Steps
Buffer Overflow Examples
Overflow Using Format String
How to Mutate a Buffer Overflow Exploit
Buffer Overflow Examples
Identifying Buffer Overflows
How to Mutate a Buffer Overflow Exploit
How to Detect Buffer Overflows in a
Program
Identifying Buffer Overflows
BoF Detection Tools
How to Detect Buffer Overflows in a
Program
Defense Against Buffer Overflows
Latest BoF Detection Tools Added
Buffer Overflow Security Tools
Defense Against Buffer Overflows
Buffer Overflow Penetration Testing
Programming Countermeasures
Latest Buffer Overflow Security Tools
Added
Buffer Overflow Penetration Testing
Page | 19
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Cryptography
Cryptography is the conversion of data into a scrambled code that is decrypted and sent across
a private or public network. The topics highlighted in red under CEHv8 Module 19:
Cryptography are the new additions.
CEHv7 Module 18: Cryptography
CEHv8 Module 19: Cryptography
Cryptography
Cryptography
Encryption Algorithms
Encryption Algorithms
Ciphers
Ciphers
What Is SSH (Secure Shell)?
What Is SSH (Secure Shell)?
Cryptography Tools
Latest Cryptography Tools Added
Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI)
Certification Authorities
Certification Authorities
Digital Signature
Digital Signature
Disk Encryption
Disk Encryption
Disk Encryption Tool
Disk Encryption Tool
Cryptography Attacks
Cryptography Attacks
Code Breaking Methodologies
Code Breaking Methodologies
Cryptanalysis Tools
Latest Cryptanalysis Tools Added
Online MD5 Decryption Tools
Online MD5 Decryption Tools
2 more Labs Added
Page | 20
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.
Certified Ethical Hacker
Version Comparison
Exam 312-50
Penetration Testing
Penetration testing assesses the security model of the organization as a whole. It reveals
potential consequences of a real attacker breaking into the network. The topics highlighted in
red under CEHv8 Module 20: Penetration Testing are the new additions.
CEHv7 Module 19: Penetration Testing
CEHv8 Module 20: Penetration Testing
Security Assessments
Security Assessments
Vulnerability Assessment
Vulnerability Assessment
What Should be Tested?
Introduction to Penetration Testing
ROI on Penetration Testing
Comparing Security Audit, Vulnerability
Assessment, and Penetration Testing
Types of Penetration Testing
What Should be Tested?
Common Penetration Testing Techniques
ROI on Penetration Testing
Pre-Attack Phase
Types of Penetration Testing
Attack Phase
Common Penetration Testing Techniques
Post-Attack Phase
Pre-Attack Phase
Penetration Testing Deliverable Templates
Attack Phase
Pen Testing Roadmap
Post-Attack Phase
Web Application Testing
Penetration Testing Deliverable Templates
Outsourcing Penetration Testing Services
Pen Testing Roadmap
Web Application Testing
Outsourcing Penetration Testing Services
Page | 21
Certified Ethical Hacker Copyright © by EC-Council
All Rights Reserved. Reproduction Is Strictly Prohibited.







