WEDI Security Risk Analysis
advertisement

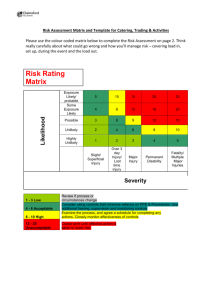
Security Risk Analysis — A Practical Approach From The Perspective of a Medicare Fiscal Intermediary Presented by Todd Fitzgerald, CISSP, CISA, CISM Director of Systems Security and Systems Security Officer for United Government Services, LLC Organizational Overview United Government Services, LLC – Largest Part A (Hospital) Medicare Fiscal Intermediary processing 30+ million claims annually – 1200 employees residing in 12 Offices in 8 states – Headquartered in Milwaukee, WI – Part of the WellPoint (NYSE: WLP) family of companies (20,000+ associates) Security Organization – Systems Security Officer reports to VP, Legal, Compliance & Audit – Multiple security departments (Systems Security, Data Security, Corporate Security) with differing roles Organizational Overview Wisconsin Ashland Milwaukee Monona W A M T O R N V California U T Oakland Camarillo A Z C O M I W I I A N E C A Southfield Lansing M N S D W Y I L OK NM TX HI Hawaii NY PA O H I N M O KS W V K Y A R ME V T N H MA C R T I New York Valhalla N DJ MD E West Virginia Charlston VA NC T N Virginia Richmond Roanoke SC MS AK Mt Vernon Michigan N D ID Illinois A L GA Medicare Part A RHHI L A FQHC covers all fifty states FL Honolulu Puerto Rico HIPAA Security Risk Analysis Deliverables Documented compliance with existing Centers for Medicare & Medicaid Services (CMS) core security requirements Created Systems Security Plans (SSPs) • • • • Business and Technical System Definition Management Controls Operational Controls Technical Controls Information Security Risk Assessment HIPAA Security Rule requirement analysis Document Existing Controls Documented Existing Control Environment with CMS-Directed Contractor Assessment Security Tool – – – – – – – Details of each security requirement (390 requirements, 79 reference HIPAA Security Rule) Status of compliance - Yes/No, Partial, Planned Specifics of ‘ how’ compliance is achieved Primary Point of Contacts (Ownership) Secondary Point of Contacts (Support) Who, What, When, Where Proposed safeguards for deficient requirements Information Security Risk Assessment Approach Utilized CMS Risk Assessment Methodology 1 Document system purpose, environment, security 2 3 4 5 6 7 8 level Identify potential dangers to the system (threats) Identify system weaknesses that could be exploited (vulnerabilities) Identify existing controls to reduce risk Determine exploitation likelihood given existing controls Determine severity impact Establish risk level for threat/vulnerability pair given existing controls. Determined safeguards to reduce risk Examined Threats, Vulnerabilities and Existing Controls Item No. Threat Name 2 Vulnerability Name Risk Description 3 Data Entry Errors Inadvertent Acts or Carelessness Impersonation Shoulder Surfing User Abuse/fraud Theft,Sabotage, Vandalism Espionage Physical Intrusions Sensitive Data Disclosure Terrorism Disgruntled Employees Existing Controls Likelihood of Occurrence Impact Severity Risk Level 4 Environmental Conditions Hazardous Material Power Fluctuation Sensitive Media Disposal Server Rooms Physical Security Misrepresentation of Identity Intrusion/Unauthorized Access Data/System Contamination Eavesdropping Malicious Code Authorized session takeover Failures & Intrusions not properly logged Installation Errors Fire, Flood, Earthquake, Tornado, Hurricane, etc Determined Likelihood and Impact Severity Item No. Threat Name Vulnerability Name 2 Risk Description 3 Existing Controls Likelihood of Occurrence 4 5 Impact Severity 6 5 Likelihood Unlikely to occur. Very Low Likely to occur two/three times every five years. Low Medium High Very High Extreme Likely to occur once per month or less. Description Minor Will have some minor effect on the system. It will require minimal effort to repair or reconfigure the system. Significant Damaging Likely to occur multiple times per month Likely to occur multiple times per day 6 Will have almost no impact if threat is realized and exploits vulnerability. Likely to occur one every year or less. Likely to occur once every six months or less. Risk Level Insignificant Description Negligible Impact Severity Serious Critical Will result in some tangible harm, albeit negligible and perhaps only noted by a few individuals or agencies. May cause political embarrassment. Will require some expenditure of resources to repair. May cause damage to the reputation of system management, and/or notable loss of confidence in the system’s resources or services. It will require expenditure of significant resources to repair. May cause considerable system outage, and/or loss of connected customers or business confidence. May result in compromise or large amount of Government information or services. May cause system extended outage or to be permanently closed, causing operations to resume in a Hot Site environment. May result in complete compromise of Government agencies’ information or services. Determined Risk Level and Safeguards Item No. Threat Name Vulnerability Name Risk Description Existing Controls Likelihood of Occurrence Impact Severity Risk Level 7 Likelihood of Occurrence Item No 8 Impact Severity Insignificant Minor Significant Damaging Serious Critical Negligible Low Low Low Low Low Very Low Low 7 Low Low Low Low Low Moderate Moderate Low Low Moderate Moderate High High Medium High Low Low Moderate High High High Low Moderate High High High High Very High Low Moderate High High High High Extreme Low Moderate High High High High Recommended Safeguard Description Residual Likelihood of Occurrence Residual Impact Severity Residual Risk L Cross-validation with HIPAA Security Assessment Tool Evaluated overall compliance using 165 HIPAA security question tool Question, Gap Analysis Based Useful for documenting current state of HIPAA Compliance Several vendors offer low cost tools ($300-$500 range) HIPAA Collaborative WEDI SNIP affiliates developing similar spreadsheet versions at no cost NIST 800-66 (DRAFT) HIPAA Resource Guide Results/Lessons Learned External consultants effective in creating initial objective viewpoint. Qualitative approaches are much more useful than rigorous Quantitative exercises. Formal project Kick-off important to ensure availability of internal subject matter experts Matrices avoid debate over the appropriate “risk level” by focusing on likelihood & severity of impact. Fully document how the implementation satisfies the requirement Explain the risks in business terms with respect to Confidentiality, Integrity & Availability. Results/Lessons Learned Senior Management must review and agree to the documented Risk Assessment Risk determinations and safeguard implementations must be monitored to maintain energy. Risk Management is ongoing, assessments must also be, as they are only a snapshot in time. Policy, Procedure, Standard.. And most importantly, Practice. HIPAA Risk Assessment should be integrated with Information Security Risk Management Program. Closing Thoughts Risk Analysis results will be different for each organization based upon existing controls, resources available and complexity of the environment. Important to share with other HIPAA Collaboratives and Security Associations on specific security issues to understand the “norms” that have been implemented. Real data on specific “current state” or implementation approaches may be difficult to obtain, as organizations need to maintain confidentiality around vulnerablities. Document and re-review, to ensure organization is practicing adequate security. Resources CMS Risk Assessment Methodology, Threat Identification Resource, Acceptable Risk Safeguards www.cms.hhs.gov/it/security HIPAA Security evaluation tool www.nchica.org/HIPAAResources/EV HIPAA Collaborative no cost matrices such as www.hipaacow.org* NIST 800-66 HIPAA Resource Guide for Implementing the HIPAA Security Rule (DRAFT) www.csrc.nist.gov/publications *Full Disclosure: Todd is a member of the Board of Directors and co-chair of the security taskforce for the WEDI Regional SNIP Affiliate HIPAA Collaborative of Wisconsin (www.hipaacow.org) Thanks ! Contact Information: Todd Fitzgerald, CISSP, CISA, CISM todd.fitzgerald@cobalt-corp.com todd_fitzgerald@yahoo.com