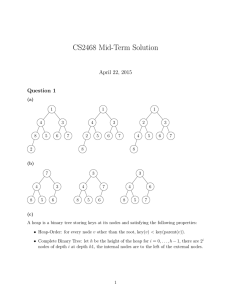
數值方法
advertisement

第1頁共8頁 計算機概論 課堂作業六 系級: 座號: 姓名: 一、 是非題 (每題 2 分) ( ) 1. If there is not enough room for another element in the queue, the queue is in an underflow state. ( ) 2. If pop is called when the stack is empty, it is in an underflow state. ( ) 3. In trees, nodes that have degree zero are called internal nodes. ( ) 4. A loop is a path of at least three vertices that starts and ends with the same vertex. ( ) 5. In the breadth-first traversal, you process all nodes in a level before proceeding to the next level. ( ) 6. In a linear list, each element has a unique successor. ( ) 7. An index file is a random-access file in which a function maps a key to an address. ( ) 8. In the digit extraction hashing method, selected digits are extracted from the key and used as the address. ( ) 9. A text file is a file of characters. ( ) 10. In the linked list collision resolution method, a node can hold multiple pieces of data. ( ) 11. Collisions are keys that hash to the same location in the data file. ( ) 12. A database is a collection of data that is logically. ( ) 13. A database management system (DBMS) defines, creates, and maintains a database and allows controlled access to users. ( ) 14. The internal level of a DBMS interacts directly with the user. ( ) 15. Each column in a relation is called an attribute, and each row in a relation is called a tuple. 二、 選擇題 (每題 3 分) A stack may be regarded as a railway switching network like the one in the figure. Cars numbered 1, 2, …, n are on the line at the left, and it is desired to rearrange (permute) the cars as they leave on the right-hand track. A car that is on the spur 1 第2頁共8頁 (stack) can be left there or sent on its way down the right track, but it can never be sent back to the incoming track. For example, if n=3, and we have the cars 1,2,3 on the left track, then 3 first goes to the spur. We could then send 2 to the spur, then on its way to the right, then send 3 on the way, then 1, obtaining the new order 1,3,2. (本題請依題 意作答,以本題為例,1,2,3 表示 3 先輸入 stack 中;而輸出時,先輸出者寫在右方, 如本例中 2 為先輸出者) ( ) 1. If we have the cars 1,2,3 on the left track, which permutations that can not be obtained by using the stack? (A) 3,1,2 ( ) (B) 1,2,3 ) (B) 4,1,2,3 ) ( ) ) ) (B) 1,4,3,2,5 (B) 1 (C) 4,3,2,1,5 (C) 2 5. After a sequence file is updated, the current data. (A) new master (B) old master (C) transaction (D) error report (D) all of the above . (D) 3 file contains the most 6. The DBMS code that allows the user to access, maintain, and update is the . (A) hardware ( (D) 2,1,4,3 4. A node of a tree has a degree of 3. this means its indegree is (A) 0 ( (C) 4,3,2,1 3. If we have the cars 1,2,3,4,5 on the left track, which permutations that can be obtained by using the stack? (A) 5,2,4,3,1 ( (D) 2,3,1 2. If we have the cars 1,2,3,4 on the left track, which permutations that can not be obtained by using the stack? (A) 1,3,2,4 ( (C) 3,2,1 (B)data (C) software (D) user 7. In DBMS, if you need to delete an attribute in a relation, you can use the operation. (A) join ( ) ) (C) union (D) intersection 8. In DBMS, if you want to change the value of an attribute of a tuple, you use the operation. (A) join ( (B) project (B) project (C) update (D) select 9. In DBMS, which operator is unary? (A) difference (B) union (C) join 2 (D) update 第3頁共8頁 系級: ( ) 座號: 姓名: 10. Of the various database models, the prevalent today. (A) hierarchical (B)network model is the most (C) relational (D) link list 三、 填充、問答、計算題 1. (4%) How many different 4-node binary trees can be created? ANS: 2. (4%) A binary tree of level k has at most nodes, k 0 . 3. (4%) A binary tree of level k has at least nodes, k 0 . 4. (3%) The maximum height of a binary tree having n nodes is at most 5. (4%) The minimum height of a binary tree having n nodes is . 6. (4%) Write the postfix form of the following expressions: A / B – C + D * (E – A) * C / F ANS: 7. Given a binary tree, please answer the following questions. A B D H C G E I J (1) Please show the results of its K F (4%) inorder traversal : (4%) preorder traversal : (4%) postorder traversal : (4%) breadth-first traversal : (2) (3%) The maximum balance factor of the binary tree is (3) (3%) The children of the binary tree are (4) (3%) The parents of the binary tree are (5) (3%) The sibling(s) of node D : (6) (3%) The leaves of the binary tree are 3 . 第4頁共8頁 8. Given a weighted graph. Please answer the following questions. 17 16 C E B 3 10 8 15 9 4 D A G 40 F H 3 23 (1) Let node A be the root, please show the results of its (4%) depth-first traversal : (4%) breadth-first traversal : (2) (5%) Draw the adjacency matrix of this graph. (3) (5%) Draw the adjacency list of this graph. (4) (4%) The distance of the shortest path from node A to node H is (5) (3%) The degree of node E is . . (6) (8%) If all the weights of the graph are set to 1, and let the length of the path be h, then how many paths are there from node C to node F? (a) If h 4, then there are paths, else (b) if h = 5, then there are paths. 4 第5頁共8頁 系級: 座號: 姓名: 9. (4%)Show the result of the following operations on a stack S. (1) push (S , 10) (2) if not empty (S), then pop (S) (3) push (S , 12) (4) push (S , 8) (5) if not empty (S), then pop (S) (6) push (S , 2) 10.(4%)Show the result of the following operations on a queue Q. (1) enqueue (Q , 11) (2) enqueue (Q , 23) (3) if not empty (Q), dequeue (Q) (4) enqueue (Q , 20) (5) enqueue (Q , 19) (6) if not empty (Q), dequeue (Q) 11. (5%)A binary tree has eight nodes. The inorder and postorder traversal of the tree follow. Can you draw the tree? If not, explain. Postorder: FECHGDBA Inorder: FECABHDG 12.(5%)A binary tree has nine nodes. The inorder and postorder traversal of the tree follow. Can you draw the tree? If not, explain. Preorder: EDCBAFGHI Inorder: ABCDEFGHI 5 第6頁共8頁 13. (5%)Given the old master file and the transaction file as follows, fine the new master file. (where A : add; R: revise; D : delete) Old Master File 14 John Transaction File 17.00 D 14 16 George 18.00 A 18 Martha 17.00 17 Due 11.00 D 20 20 Li 12.00 R 26 Tedd 26 Ted 23.00 R 31 31 Joanne 27.00 D 45 45 Bruce 12.00 A 89 Orva New Master File 28.00 20.00 14.(5%) Find the address of the following keys using the modulo division method and a file of size 411. If there is a collision, use open addressing to resolve it. Draw a figure to show the position of the records. (1) 10278 (2) 08222 (3) 20553 (4) 17526 6 第7頁共8頁 系級: 座號: 姓名: 15.Given a COURSES relation table as follows: COURSES No Course-Name Unit CIS15 Intro to C 5 CIS17 Intro to Java 7 CIS19 Unix 7 CIS51 Networking 5 (1) (10%) Please show the results after the following operations. (a) Inserts a new course CIS52 after the CIS51. CIS52 TCP/IP Protocols 6 (b) Delete the course CIS19. (c) Update the number of units for CIS51 to 7. (d) Inserts a new course CIS62 after the CIS52. CIS62 Data Structure (e) Select the seven-unit courses. ANS: 7 7 第8頁共8頁 16.Given two relation tables as follows: CIS51-Roster ID CIS52-Roster F-Name L-Name ID F-Name L-Name 6754 John Brown 9999 Rich White 5690 George Yellow 6754 John Brown 6580 Anne Green 5690 George Yellow 6789 Ted Purple 4477 Andy Brown (1) (5%) Show the intersection results of CIS51-Roster and CIS52-Roster relation tables. (2) (5%) Show the union results of CIS51-Roster and CIS52-Roster relation tables. (3) (5%) Show the results of CIS51-Roster difference CIS52-Roster. 8





![Question#4 [25 points]](http://s3.studylib.net/store/data/007289590_1-57e227b5dac30eb17dd4115b9416253c-300x300.png)