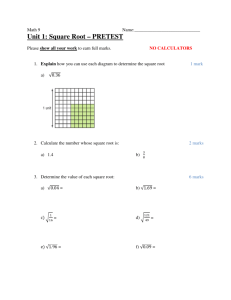
Describe any 3 of the 5 main advantages of using a network over
advertisement

Year 11 Software Development Unit 2 Solutions Marks Section A 12 Section B 34 Total 46 % Actual Marks Section A: Define the following terms (12 marks) 1. Antivirus program - program that protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media or on incoming files 2. Cybercrime - online or Internet-based illegal activities 3. Denial of service attack - assault on a computer or network whose purpose is to disrupt computer access to an Internet service such as the Web or email 4. Encryption– the process of encoding data and information to an unreadable form 5. Firewall– hardware and/or software that protects a network’s resources from intrusions by users on another network such as the Internet. 6. Hacker– someone who accesses a computer or network illegally 7. Passphrase - private combination of words, often containing mixed capitalisation and punctuation, associated with a user name that allows access to certain computer resources 8. Pharming– scam, similar to phishing, where a perpetrator attempts to obtain your personal or financial information, except they do so via spoofing 9. Phishing– scam where a perpetrator attempts to obtain your personal or financial information 10. Trojan horse– malicious logic program named after the Greek myth that hides within or looks like a legitimate program 11. Virus– potentially damaging computer program that affects, or infects, a computer negatively by altering the way the computer works without a user’s knowledge or permission 12. Worm– malicious logic program that copies itself repeatedly, using up system resources and possibly shutting down the system Section B: Short Answer Questions marks) (34 1. What is a network? A network is a collection of computers and devices connected by communications channels that facilitates communications among users. (1 mark) 2. Describe the main difference between a Local Area Network and a Wide Area Network. LAN is a network that connects computers and devices in a limited geographical area. WAN is a network that connects computers and devices in a limited geographical area using telephone lines, microwave, satellites or a combination of these. (2 marks) Page 2 of 4 3. List and describe 3 advantages of using a network over stand-alone computers. Facilitating communications – communicating via email, instant messaging, video conferencing, etc. Sharing hardware – can access and use hardware on a network eg printer. Sharing data and information – can access data and information stored on other computers. Sharing software – can access software on the network. Transferring funds – EFT allows users to transfer money from one bank account to another via transmission media. (3 marks) 4. Describe the peer-to-peer network? Allows any computer to share software, data and hardware located on any other computer in the network. (1 mark) 5. Describe the client/server network? Is a network in which one or more computers acts as a server and the other computers can request services from the computer. A server controls acess to the hardware and software on the network and provides a centralised storage area for programs, data and information. (2 marks) 6. Draw the following network topologies and list one advantage and one disadvantage of each: a. Star Contains a central computer and one or more devices connected to it forming a star. Devices can be added to, or removed from the network with little or no disruption to the network (4 marks) a. Mesh Is a network where every device is connected to every other device on the network (4 marks) b. Bus All devices in the network are connected to and share a single cable. Information is transmitted in either direction from any one personal computer to another (4 marks) 7. Describe the following protocols: a. Ethernet Uses a bus technology where a packet of data that contains the destination address and the sending address travels along the network until it arrives at the designated receiving address. (1 mark) Page 3 of 4 b. Transmission Control Protocol/Internet Protocol (TCP/IP) Manages transmission of data by breaking it up into packets and transmitting the packets over the Internet. (1 mark) 8. Briefly describe the following types of communication devices: a. Network Interface Card (NIC) Fits in an expansion slot of a computer and attaches to the cable or wireless technology used to connect the devices to the network. (1 mark) b. Hub A central device that provides a central point for cables in a LAN. Transmits data to all devices connected to it (1 mark) c. Switch Enables a packet reach its destination faster by storing addresses in memory and using logic to direct the transmission (1 mark) d. Firewall A firewall is a program on a gateway or proxy server or hardware device such as a router, which filters information coming through an Internet connection into a network. If a piece of information is marked as having a virus or not allowed into the network because it comes from suspect sources it is not allowed through. (1 mark) 9. Briefly describe the following physical transmission media: a. Twisted-pair cable Consists of one or more twisted-pair copper wires bundled together. (1 mark) b. Fibre-optic cable Uses smooth, hair-thin strands of glass or plastic to conduct light with high efficiency. (1 mark) 10. List and describe two types of servers. Application servers - a server dedicated to running certain software applications File servers - provides file services and are the most common server type Proxy servers - provides database IT server in services Print servers - provides printer services Web/FTP servers - a server that HTTP clients connect to in order to send commands and receive responses along with data contents (2 marks) 11. What is a Network Operating System? A NOS operates in the same way to the operating system of a PC; however it has special capabilities that enable it to connect computers and peripheral devices, such as printers, to a LAN. (1 mark) 12. List and describe two main functions of a Network Operating System. Administration - the management of users is the main task. Their authorisation details need to be added, deleted and organised into groups. Backup procedures need to be run. File Management - the location and transfers of files being used needs to be managed between users and storage locations. Other Resource Management - such as printer management that involves the spooling of print tasks and the allocation of these tasks to the appropriate printer. Security - the access rights of users need to be set up and monitored. (2 marks) Page 4 of 4