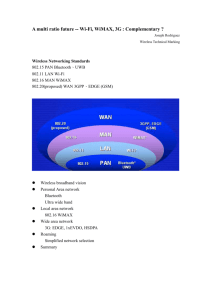
Part B – Market Analysis
advertisement

UNIVERSITY OF OSLO Department of informatics Functionality of Alternative Broadband Access and Impact on Market Master thesis 60 credits Saqib Rana 26. 05. 2007 1 Acknowledgements Thomas Haslestad Josef Noll 2 Abstract Today’s wireless access is dominated by mobile networks with GSM/ UMTS and private WLAN networks based on 802.11 standard. The market situation can change quickly owing to the fact that new access methods are expected to be introduced in the market soon. WIMAX (802.16), 802.20, CDMA2000 and Cognitive Radio (802.22) are such promising technologies. These radio technologies uses methods for better spectrum utilization like MESH network technology, Adhoc routing and dynamic frequency allocation. This thesis is looking into functionality of new access methods, actors in the Nordic market and how these actors plans to use this functionality. 3 Table of Content Acknowledgements ............................................................................................................. 2 Abstract ............................................................................................................................... 3 Table of Content ................................................................................................................. 4 Introduction ......................................................................................................................... 7 Part A – Technical Analysis ............................................................................................... 8 Alternative Access Technologies for Wireless Broadband ............................................ 8 Part B – Market Analysis .................................................................................................... 8 Forord .................................................................................................................................. 9 Innledning ......................................................................................................................... 10 Bakgrunnstoff ................................................................................................................... 11 Overordnet diskusjon ........................................................................................................ 12 Beskrivelse av det man har gjort ....................................................................................... 13 Mer finkornet diskusjon .................................................................................................... 14 Oppsummering og videre arbeid ....................................................................................... 15 Vedlegg ............................................................................................................................. 16 Concluding remarksLiterature references ......................................................................... 17 Literature references ......................................................................................................... 18 Appendices ........................................................................................................................ 20 Wi-Fi: IEEE802.11 Wireless local Area Network (WLAN) ............................................ 20 From Wikipedia, the free encyclopedia .................................................................... 20 Uses ............................................................................................................................... 20 Wi-Fi at home ........................................................................................................... 21 Wi-Fi in Business ...................................................................................................... 21 Wi-Fi at Hotspots ...................................................................................................... 22 Technical information ................................................................................................... 22 Channels .................................................................................................................... 23 Advantages of Wi-Fi ................................................................................................. 23 Disadvantages of Wi-Fi ............................................................................................ 24 Standard Devices .......................................................................................................... 25 Wireless Access Point (WAP) .................................................................................. 25 Wireless Adapter ....................................................................................................... 25 Wireless Router......................................................................................................... 25 Wireless Ethernet Bridge .......................................................................................... 26 Range Extender ......................................................................................................... 26 Antenna connectors ................................................................................................... 26 Non-Standard Devices .................................................................................................. 26 DIY Range Optimizations......................................................................................... 26 Long Range Wi-Fi .................................................................................................... 26 Wi-Fi and its support by operating systems .................................................................. 27 Microsoft Windows .................................................................................................. 27 Apple Mac OS........................................................................................................... 28 Open source Unix-like systems ................................................................................ 28 Embedded systems .................................................................................................... 29 Social concerns ............................................................................................................. 30 4 Unintended and intended use by outsiders................................................................ 30 Wi-Fi vs. amateur radio ............................................................................................ 30 Health risks ................................................................................................................... 31 History........................................................................................................................... 31 Origin and meaning of the term 'Wi-Fi' .................................................................... 32 IEEE 802.11 ...................................................................................................................... 33 From Wikipedia, the free encyclopedia .................................................................... 33 Protocols ....................................................................................................................... 34 Summary ................................................................................................................... 34 802.11 legacy ............................................................................................................ 35 802.11a ...................................................................................................................... 35 802.11b...................................................................................................................... 37 802.11g...................................................................................................................... 38 802.11n...................................................................................................................... 39 Channels and international compatibility ..................................................................... 41 Standard and Amendments ........................................................................................... 41 Standard or Amendment? ......................................................................................... 42 Nomenclature ................................................................................................................ 43 Community networks .................................................................................................... 43 Security ......................................................................................................................... 43 WiMAX: IEE802.16 ......................................................................................................... 45 From Wikipedia, the free encyclopedia .................................................................... 45 Definitions of terms[1] ................................................................................................... 45 Uses ............................................................................................................................... 46 Broadband Access ..................................................................................................... 46 Mobile applications ................................................................................................... 46 Technical information ................................................................................................... 47 MAC layer/ Data Link Layer .................................................................................... 47 Physical layer ............................................................................................................ 47 Comparison with Wi-Fi ............................................................................................ 48 Spectrum Allocations issues ..................................................................................... 48 Standards ....................................................................................................................... 50 IEEE 802.16e-2005 ................................................................................................... 50 WiBro........................................................................................................................ 51 Associations .................................................................................................................. 51 WiMAX Forum ......................................................................................................... 51 WiMAX Spectrum Owners Alliance - WiSOA ........................................................ 51 Competing technologies................................................................................................ 52 3G and 4G Cellular Phone Systems .......................................................................... 52 Mobile Broadband Wireless Access ......................................................................... 54 Internet Oriented Systems ......................................................................................... 54 Comparison ............................................................................................................... 54 Future Development...................................................................................................... 55 Current Deployments .................................................................................................... 55 IEEE 802.16 ...................................................................................................................... 56 From Wikipedia, the free encyclopedia .................................................................... 56 802.16 standards ........................................................................................................... 56 Amendments in progress........................................................................................... 57 5 802.16e-2005 Technology ............................................................................................ 57 PHY........................................................................................................................... 57 MAC ......................................................................................................................... 57 Certification .................................................................................................................. 58 Mesh networking .............................................................................................................. 60 From Wikipedia, the free encyclopedia .................................................................... 60 Examples ....................................................................................................................... 60 Cognitive radio.................................................................................................................. 61 From Wikipedia, the free encyclopedia .................................................................... 61 History........................................................................................................................... 61 Terminology.................................................................................................................. 61 Technology ................................................................................................................... 62 IEEE 802.20 ...................................................................................................................... 64 From Wikipedia, the free encyclopedia .................................................................... 64 IEEE 802.22 ...................................................................................................................... 65 From Wikipedia, the free encyclopedia .................................................................... 65 Technology ................................................................................................................... 65 Overview of the WRAN Topology ............................................................................... 65 An approach to the PHY layer ...................................................................................... 66 An approach to the MAC layer ..................................................................................... 66 IEEE 802 ........................................................................................................................... 67 From Wikipedia, the free encyclopedia .................................................................... 67 6 Introduction The thesis is divided into two segments, a technical analysis part A, and a market analysis part B. In the technical part A new alternative access technologies for Broadband Wireless/ Radio Access is discussed. The focus is on WiFi and WiMax. Factors that make these technologies alternatives to today’s mobile access are emphasized. Especially opportunities that exist in such alternative access are thrown light on. The concepts of Cognitive Radio in the VHF/ UHF bands are described along with regulatory situation in Norway. How Cognitive Radio can be used in public mobile services is also considered. In the market analysis part B an overview of WiFi and WiMax operators in the Nordic Countries is presented. Position in the value chain, size, product portfolio and market position for every major actor are illustrated. This information is then used to predict a picture of the situation in the alternative broadband market. The market analysis part also covers how new functionality in form of chosen features could influence the existing market. These selected features in this regard are MESH Networking and Switched WiFi/ CAPWAP for both WiFi and WiMax. The potential market impact of Cognitive Radio is also evaluated. 7 Part A – Technical Analysis Alternative Access Technologies for Wireless Broadband Part B – Market Analysis 8 Forord (ca 1/3 side) 9 Innledning (5 sider) Problemestilling Kort gjennomgang av kapitlene 10 Bakgrunnstoff (20 sider) Innføring i støtteområder etc. for oppgaven 11 Overordnet diskusjon (ca 15) Hovedvalg og vurderinger for disse 12 Beskrivelse av det man har gjort (ca 25 sider) Gå gjennom hovedlinjene 13 Mer finkornet diskusjon(ca 20 sider) Diskusjon trenger “kontekst” Se på alternative utvidelser 14 Oppsummering og videre arbeid (5- 10 sider) Tilbakeblikk, med kommentarer (gjerne kritiske) Hvor står man i forhold til problemstillingen Retninger å gå videre I (Råd til neste hovedfagsrtudent) 15 Vedlegg 16 Concluding remarks 17 Literature references [1] Wikipedia. (2006).Internet [online]. Available at <URL: http://en.wikipedia.org/wiki/Internet> [2] Philippe Le Hégaret. (2006). Web Services Activity [online]. Available at URL:http://www.w3.org/2002/ws/ [3] Haas H. (2006). Web Services Activity Statement [online]. Available at <URL: http://www.w3.org/2002/ws/Activity> [4] Wikipedia. (2006). Web service [online]. Available at <URL: http://en.wikipedia.org/wiki/Web_service> [5] Bayer j et el. (2006). Implementation Roadmap for ASG-based services[online]. Internally available at<URL:https://asg-platform.org/cgibin/ twiki/viewauth/Internal/RoadmapForSemanticServices> [6] http://www.scientificamerican.com/article.cfm?articleID=00048144-10D2-1C7084A9809EC588EF21&catID=2By Tim Berners-Lee, James Hendler and Ora Lassila [7] Wikipedia. (2006). Common Object Request Broker Architecture [online]. Available at URL:http://en.wikipedia.org/wiki/CORBA [8] Wikipedia. (2006). Java remote method invocation [online]. Available at <URL: http://en.wikipedia.org/wiki/Java_remote_method_invocation > [9] Wikipedia. (2006). Distributed component object model [online]. Available at <URL: http://en.wikipedia.org/wiki/Distributed_component_object_model> [10] Brown P et al. (2006). Reference Model for Service Oriented Architecture 1.0 [online]. Available at <URL: http://www.oasis-open.org/committees/download.php/18486/pr2changes.pdf> [11] Panda D. (2005). An Introduction to Service-Oriented Architecture from a Java Developer Perspective [online]. Available at <URL: http://www.onjava.com/pub/a/onjava/2005/01/26/soa-intro.html> [12] By Raghu R. Kodali. (2005). What is service-oriented architecture? [online]. Available at <URL: http://www.javaworld.com/javaworld/jw-06-2005/jw-0613-soa.html> [13] Wikipedia. (2006). SOA [online]. Available at <URL: Wikipedia. http://en.wikipedia.org/wiki/SOA > [14] Updegrove A. (2005). The Semantic Web [online]. Available at <URL: 18 http://www.consortiuminfo.org/bulletins/semanticweb.php> [15] Wikipedia. (2006). Semantics [online]. Available 19 Appendices Wi-Fi: IEEE802.11 Wireless local Area Network (WLAN) From Wikipedia, the free encyclopedia Official Wi-Fi logo Wi-Fi, popularly known as an acronym for wireless fidelity (see below for origin), but, in actuality is simply a play on the term "Hi-Fi," was originally a brand licensed by the WiFi Alliance to describe the embedded technology of wireless local area networks (WLAN) based on the IEEE 802.11 specifications. Use of the term has now broadened to generically describe the wireless interface of mobile computing devices, such as laptops in LANs. Wi-Fi is now increasingly used for more services, including Internet and VoIP phone access, gaming, and basic connectivity of consumer electronics such as televisions, DVD players, and digital cameras. More standards are in development that will allow Wi-Fi to be used by cars on highways in support of an Intelligent Transportation System to increase safety, gather statistics, and enable mobile commerce (see IEEE 802.11p). Wi-Fi and the Wi-Fi CERTIFIED logo are registered trademarks of the Wi-Fi Alliance - the trade organization that tests and certifies equipment compliance with the 802.11x standards. Uses A person with a Wi-Fi enabled device such as a pc, cell phone or PDA can connect to the Internet when in proximity of an access point. The region covered by one or several access points is called a hotspot. Hotspots can range from a single room to many square miles of overlapping hotspots. Wi-Fi can also be used to create a mesh network. Both architectures are used in community networks. Wi-Fi also allows connectivity in peer-to-peer (wireless ad-hoc network) mode, which enables devices to connect directly with each other. This connectivity mode is useful in consumer electronics and gaming applications. When the technology was first commercialized there were many problems because consumers could not be sure that products from different vendors would work together. The Wi-Fi Alliance began as a community to solve this issue so as to address the needs of the end user and allow the technology to mature. The Alliance created the branding Wi-Fi CERTIFIED to show consumers that products are interoperable with other products displaying the same branding. 20 Wi-Fi at home Home Wi-Fi clients come in many shapes and sizes, from stationary PCs to digital cameras. The trend today is to incorporate wireless into every electronic where mobility is desired. Wi-Fi devices in home or consumer-type environments connect in the following ways: Via a broadband Internet connection into a single router which can serve both wired and wireless clients Ad-hoc mode for client to client connections Built into non-computer devices to enable wireless connectivity to other devices or the Internet Wi-Fi in Gaming Gaming consoles and handhelds make use of Wi-Fi technology to enhance the gaming experience. Examples include: The Nintendo DS handheld is Wi-Fi compatible, and is compatible with WEP encryption. The Wii is Wi-Fi compatible, and is compatible with WEP and WPA encryption. The PlayStation 3 Premium model features built-in Wi-Fi which is compatible with WEP and WPA encryption, while the Basic model can be upgraded with a separate wireless adapter. The PlayStation Portable is Wi-Fi compatible, and is compatible with WEP and WPA encryption. The Xbox 360 can be made Wi-Fi compatible if the user purchases a separate wireless adapter. Wi-Fi in Business Business and industrial Wi-Fi has taken off, with the trends in implementation varying greatly over the years. Current technology trends in the corporate wireless world are: Dramatically increasing the number of Wi-Fi Access Points in an environment, in order to provide redundancy,support fast roaming and increasing overall network capacity by using more channels and/or creating smaller cells Designing for wireless voice applications (VoWLAN or WVOIP) Moving toward 'thin' Access Points, with more of the network intelligence housed in a centralized network appliance; relegating individual Access Points to be simply 'dumb' radios Outdoor applications utilizing true mesh topologies A proactive, self-managed network that functions as a security gateway, firewall, DHCP server, intrusion detection system, and a myriad of other features not previously considered relevant to a wireless network. 21 Wi-Fi at Hotspots The most publically visible use of Wi-Fi is at hotspots. These trends include: Free Wi-Fi at venues like Panera Bread, It's a Grind Coffee House, and over 100,000 locations in the USA has been growing in popularity. According to a door-to-door survey in San Jose, CA, the number of venues and users is growing fast. Paid Wi-Fi at venues like Starbucks, McDonalds, and at hotels. This trend is flat. According to Muni Wireless, metropolitan-wide WiFi (Mu-Fi) already has more than 300 projects in process. Technical information Wi-Fi: How it Works Wi-Fi networks use radio technologies called IEEE 802.11 to provide secure, reliable, fast wireless connectivity. A typical Wi-Fi setup contains one or more Access Points (APs) and one or more clients. An AP broadcasts its SSID (Service Set Identifier, "Network name") via packets that are called beacons, which are usually broadcast every 100 ms. The beacons are transmitted at 1 Mbit/s, and are of relatively short duration and therefore do not have a significant effect on performance. Since 1 Mbit/s is the lowest rate of Wi-Fi it assures that the client that receives the beacon can communicate at at least 1 Mbit/s. Based on the settings (e.g. the SSID), the client may decide whether to connect to an AP. If two APs of the same SSID are in range of the client, the client firmware might use signal strength to decide with which of the two APs to make a connection. The Wi-Fi standard leaves connection criteria and roaming totally open to the client. This is a strength of Wi-Fi, but also means that one wireless adapter may perform substantially better than another. Since Wi-Fi transmits in the air, it has the same properties as a nonswitched wired Ethernet network, and therefore collisions can occur. Unlike a wired Ethernet, and like most packet radios, Wi-Fi cannot do collision detection, and instead uses an acknowledgment packet for every data packet sent. If no acknowledgement is received within a certain time a retransmission occurs. Also, a medium reservation protocol can be used when excessive collisions are experienced or expected (RequestToSend/ClearToSend used for Collision Avoidance or CA) in an attempt to try to avoid collisions. A Wi-Fi network can be used to connect computers to each other to the internet and to wired networks (which use IEEE 802.3 or Ethernet). Wi-Fi networks operate in the unlicensed 2.4 (802.11b/g) and 5 GHz (802.11a/h) radio bands, with an 11 Mbps (802.11b) or 54 Mbps (802.11a or g) data rate or with products that contain both bands (dual band). They can provide real world performance similar to the basic 10BaseT wired Ethernet networks. 22 Channels Except for 802.11a/h, which operates at 5GHz, Wi-Fi devices historically primarily use the spectrum in 2.4GHz, which is standardized and unlicensed by international agreement, although the exact frequency allocations and maximum permitted power vary slightly in different parts of the world. Channel numbers, however, are standardized by frequency throughout the world, so authorized frequencies can be identified by channel numbers. The 2.4 GHz band is also used by microwave ovens, cordless phones, baby monitors and Bluetooth devices. The maximum number of available channels for Wi-Fi enabled devices are: 13 for Europe 11 for North America. Only channels 1, 6, and 11 are recommended for 802.11b/g to minimize interference from adjacent channels.[1] 14 for Japan [2] Advantages of Wi-Fi Wireless Internet on the beach, Taba, Egypt Allows LANs to be deployed without cabling for client devices, typically reducing the costs of network deployment and expansion. Spaces where cables cannot be run, such as outdoor areas and historical buildings, can host wireless LANs. Built into most modern laptops, getting a laptop without a built in WiFi has become an exception. Wi-Fi chipset pricing continues to come down, making Wi-Fi a very economical networking option and driving inclusion of Wi-Fi in an ever-widening array of devices. Wi-Fi products are widely available in the market. Different competitive brands of access points and client network interfaces are inter-operable at a basic level of service. Products designated as Wi-Fi CERTIFIED by the Wi-Fi Alliance are backwards inter-operable. 23 Wi-Fi is a global set of standards. Unlike cellular carriers, the same Wi-Fi client works in different countries around the world. Widely available in more than 250,000 public hot spots and tens of millions of homes and corporate and university campuses worldwide. As of 2007, WPA is not easily cracked if strong passwords are used and WPA2 encryption has no known weaknesses. New protocols for Quality of Service (WMM) and power saving mechanisms (WMM Power Save) make Wi-Fi even more suitable for latency-sensitive applications (such as voice and video) and small Form-Factor Disadvantages of Wi-Fi Spectrum assignments and operational limitations are not consistent worldwide; most of Europe allows for an additional 2 channels beyond those permitted in the US (1-13 vs 1-11); Japan has one more on top of that (1-14) - and some countries, like Spain, prohibit use of the lower-numbered channels. Furthermore some countries, such as Italy, used to require a 'general authorization' for any Wi-Fi used outside an operator's own premises, or require something akin to an operator registration. Equivalent isotropically radiated power (EIRP) in the EU is limited to 20 dBm (0.1 W). Power consumption is fairly high compared to some other low bandwidth standards (Zigbee and Bluetooth), making battery life a concern. The most common wireless encryption standard, Wired Equivalent Privacy or WEP, has been shown to be easily breakable even when correctly configured. WiFi Protected Access (WPA and WPA2) which began shipping in 2003 aims to solve this problem and is now available on most products. Wi-Fi Access Points typically default to an open (encryption-free) mode. Novice users benefit from a zero configuration device that works out of the box but without security enabled providing open wireless access to their LAN. To turn security on requires the user to configure the device, usually via a software GUI. Many 2.4 GHz 802.11b and 802.11g Access points default to the same channel on initial start up, contributing to congestion on certain channels. To change the channel of operation for an access point requires the user to configure the device. Wi-Fi networks have limited range. A typical Wi-Fi home router using 802.11b or 802.11g with a stock antenna might have a range of 45 m (150 ft) indoors and 90 m (300 ft) outdoors. Range also varies with frequency band. Wi-Fi in the 2.4 GHz frequency block has slightly better range than Wi-Fi in the 5 GHz frequency block. Outdoor range with improved antennas can be several kilometres or more with line-of-sight. Wi-Fi pollution, of an excessive number of an access point with other access points in the area, especially on the same or neighboring channel, can prevent access and interfere with the use of other access points by others caused by overlapping channels in the 802.11g/b spectrum as well as with decreased signalto-noise ratio (SNR) between access points. This can be a problem in high-density areas such as large apartment complexes or office buildings with many Wi-Fi access points. Additionally, other devices use the 2.4 GHz band: microwave 24 ovens, cordless phones, baby monitors, security cameras, and Bluetooth devices can cause significant additional interference. It is also an issue when municipalities[3] or other large entities such as universities seek to provide large area coverage. Everyone is considered equal for the base standard without 802.11e/WMM when they use the band. This openness is also important to the success and widespread use of 2.4 GHz Wi-Fi, but makes it unsuitable for "must have" public service functions or where reliability is required. Users sometimes suffer network "frustrations" or a total network breakdown if gaming because a neighbour microwaves some pop corn. Interoperability issues between brands or proprietary deviations from the standard can disrupt connections or lower throughput speeds on other user's devices that are within range. And, Wi-Fi devices do not presently pick channels to avoid interference. Wi-Fi networks that are open (unencrypted) can be monitored and used to read and copy data (including personal information) transmitted over the network unless another security method is used to secure the data like a VPN or a secure web page. Standard Devices Wireless Access Point (WAP) Main article: Wireless access point A wireless access point connects a group of wireless devices to an adjacent wired LAN. An access point is similar to an ethernet hub, relaying data between connected wireless devices in addition to a (usually) single connected wired device, most often an ethernet hub or switch, allowing wireless devices to communicate with other wired devices. Wireless Adapter A wireless adapter allows a device to connect to a wireless network. These adapters connect to devices using various external or internal interconnects such as PCI, miniPCI, USB, ExpressCard, Cardbus and PC card. Most newer laptop computers are equipped with internal adapters. Internal cards are generally more difficult to install. Wireless Router A wireless router integrates a WAP, ethernet switch, and internal Router firmware application that provides IP Routing, NAT, and DNS forwarding through an integrated WAN interface. A wireless router allows wired and wireless ethernet LAN devices to connect to a (usually) single WAN device such as cable modem or DSL modem. A wireless router allows all three devices (mainly the access point and router) to be configured through one central utility. This utility is most usually an integrated web server which serves web pages to wired and wireless LAN clients and often optionally to WAN clients. This utility may also be an application that is run on a desktop computer such as Apple's AirPort. 25 Wireless Ethernet Bridge A wireless Ethernet bridge connects a wired network to a wireless network. This is different from an access point in the sense that an access point connects wireless devices to a wired network at the data-link layer. Two wireless bridges may be used to connect two wired networks over a wireless link, useful in situations where a wired connection may be unavailable, such as between two separate homes. Range Extender A wireless range extender or wireless repeater can extend the range of an existing wireless network. Range extenders can be strategically placed to elongate a signal area or allow for the signal area to reach around barriers such as those created in L-shaped corridors. Wireless devices connected through repeaters will suffer from an increased latency for each hop. Additionally, a wireless device at the end of chain of wireless repeaters will have a throughput that is limited by the weakest link within the repeater chain. Antenna connectors Most commercial devices (routers, access points, bridges, repeaters) designed for home or business environments use either RP-SMA or RP-TNC antenna connectors. PCI wireless adapters also mainly use RP-SMA connectors. Most PC card and USB wireless only have internal antennas etched on their printed circuit board while some have MMCX connector or MC-Card external connections in addition to an internal antenna. A few USB cards have a RP-SMA connector. Most Mini PCI wireless cards utilize Hirose U.FL connectors, but cards found in various wireless appliances contain all of the connectors listed. Many high-gain (and homebuilt antennas) utilize the Type N connector more commonly used by other radio communications methods. Non-Standard Devices DIY Range Optimizations USB-Wi-Fi adapters, food container "Cantennas", parabolic reflectors, and many other types of self-built antennae are increasingly made by do-it-yourselvers. For minimal budgets, as low as a few dollars, signal strength and range can be improved dramatically. There is also a type of optimization by polarizing the signal to achieve a planar coverage like a plate. Many of these high-gain aftermarket modifications are technically illegal under FCC and other regulatory guidelines. Long Range Wi-Fi For more details on this topic, see Long Range Wi-Fi. 26 Recently, long range Wi-Fi kits have begun to enter the market. Companies like RadioLabs and BroadbandXpress offer long range, inexpensive kits that can be setup with limited knowledge. These kits utilize specialized antennas which increase the range of Wi-Fi dramatically, in the case of the world record 137.2 miles (220km). These kits are commonly used to get Broadband internet to a place that cannot access the service itself.[4] The longest link ever achieved was by the Swedish space agency. They attained 310 km, but used 6 watt amplifiers to reach an overhead stratospheric balloon. The longest link without amplification was 279 km in Venezuela, 2006 Read PDF by www.eslared.org Wi-Fi and its support by operating systems There are two sides to Wi-Fi support under an operating system: driver level support, and configuration and management support. Driver support is usually provided by the manufacturer of the hardware or, in the case of Unix clones such as Linux and FreeBSD, sometimes through open source projects. Configuration and management support consists of software to enumerate, join, and check the status of available Wi-Fi networks. This also includes support for various encryption methods. These systems are often provided by the operating system backed by a standard driver model. In most cases, drivers emulate an ethernet device and use the configuration and management utilities built into the operating system. In cases where built in configuration and management support is non-existent or inadequate, hardware manufacturers may include their own software to handle the respective tasks. Microsoft Windows Microsoft Windows has comprehensive driver-level support for Wi-Fi, the quality of which depends on the hardware manufacturer. Hardware manufactures almost always ship Windows drivers with their products. Windows ships with very few Wi-Fi drivers and depends on the original equipment manufacturers (OEMs)and device manufacturers to make sure users get drivers. Configuration and management depend on the version of Windows. Earlier versions of Windows, such as 98, ME and 2000 do not have built-in configuration and management support and must depend on software provided by the manufacturer Microsoft Windows XP has built-in configuration and management support. The original shipping version of Windows XP included rudimentary support which was dramatically improved in Service Pack 2. Support for WPA2 and some other security protocols require updates from Microsoft. There are still problems with XP support of Wi-Fi. (One simple interface problem is that if the user makes a mistake in the (case sensitive) passphrase, XP keeps trying to connect but never tells the user that the passphrase is wrong. A second problem is not allowing the 27 user to see different BSSID's for the same ESSID; that is, it provides no way for the user to differentiate access points with the same name.) To make up for Windows’ inconsistent and sometimes inadequate configuration and management support, many hardware manufacturers include their own software and require the user to disable Windows’ built-in Wi-Fi support. See article "Windows XP Bedevils Wi-Fi Users" in Wired News. Microsoft Windows Vista has improved Wi-Fi support over Windows XP. The original betas automatically connected to unsecured networks without the user’s approval. The release candidate (RC1 or RC2) does not continue to display this behavior, requiring user permissions to connect to an unsecured network, as long as the user account is in the default configuration with regards to User Account Control. Apple Mac OS Apple was an early adopter of Wi-Fi, introducing its AirPort product line, based on the 802.11b standard, in July 1999. Apple then introduced AirPort Extreme as an implementation of 802.11g. All Macs starting with the original iBook included AirPort slots for which an AirPort card can be used, connecting to the computer's internal antenna. All Intel-based Macs either come with built-in Airport Extreme or a slot for an AirPort card. In late 2006, Apple began shipping Macs with Broadcom Wi-Fi chips that also supported the Draft 802.11n standard which can be unlocked through buying a $2 driver released by Apple at the January 2007 Macworld Expo. The driver is also included for free with Apple's 802.11n AirPort Extreme. Apple makes the Mac OS operating system, the computer hardware, the accompanying drivers, AirPort WiFi base stations, and configuration and management software, simplifying Wi-Fi integration. The built-in configuration and management is integrated throughout many of the operating system's applications and utilities. Mac OS X has WiFi support, including WPA2, and ships with drivers for Apple’s Broadcom-based AirPort cards. Many third-party manufacturers make compatible hardware along with the appropriate drivers which work with Mac OS X’s built-in configuration and management software. Other manufacturers distribute their own software. Apple's older Mac OS 9 does not have built in support for Wi-Fi configuration and management nor does it ship with Wi-Fi drivers, but Apple provides free drivers and configuration and management software for their AirPort cards for OS 9, as do a few other manufacturers. Versions of Mac OS before OS 9 predate Wi-Fi and do not have any Wi-Fi support, although some third-party hardware manufacturers have made drivers and connection software that allows earlier OSes to use Wi-Fi.[5] Open source Unix-like systems Linux, FreeBSD and similar Unix-like clones have much coarser support for Wi-Fi. Due to the open source nature of these operating systems, many different standards have been developed for configuring and managing Wi-Fi devices. The open source nature also fosters open source drivers which have enabled many third party and proprietary devices 28 to work under these operating systems. See Comparison of Open Source Wireless Drivers for more information on those drivers. Linux has patchy Wi-Fi support[6]. Native drivers for many Wi-Fi chipsets are available either commercially or at no cost[7], although some manufacturers don't produce a Linux driver, only a Windows one. Consequently, many popular chipsets either don't have a native Linux driver at all, or only have a half-finished one. For these, the freely available NdisWrapper and its commercial competitor DriverLoader[8] allow Windows x86 and 64 bit variants NDIS drivers to be used on x86-based Linux systems but not on other architectures. As well as the lack of native drivers, some Linux distributions do not offer a convenient user interface and configuring Wi-Fi on them can be a clumsy and complicated operation compared to configuring wired Ethernet drivers[9]. This is changing with NetworkManager, a utility that allows users to automatically switch between networks without using the command line. FreeBSD has Wi-Fi support similar to Linux. Support under FreeBSD is best in the 6.x versions, which introduced full support for WPA and WPA2, although in some cases this is driver dependent. FreeBSD comes with drivers for many wireless cards and chipsets, including those made by Atheros, Ralink, Cisco, Dlink, Netgear, and many Centrino chipsets, and provides support for others through the ports collection. FreeBSD also has "Project Evil", which provides the ability to use Windows x86 NDIS drivers on x86-based FreeBSD systems as NdisWrapper does on Linux, and Windows amd64 NDIS drivers on amd64-based systems[2]. NetBSD, OpenBSD, and DragonFly BSD have Wi-Fi support similar to FreeBSD. Code for some of the drivers, as well as the kernel framework to support them, is mostly shared among the 4 BSDs. Haiku has no Wi-Fi support at all as of April 2007. Embedded systems Wi-Fi availability in the home is on the increase. This extension of the Internet into the home space will increasingly be used for remote monitoring. Examples of remote monitoring include security systems and tele-medicine. In all these kinds of implementation, if the Wi-Fi provision is provided using a system running one of operating systems mentioned above, then it becomes unfeasible due to weight, power consumption and cost issues. Increasingly in the last few years (particularly as of early 2007), embedded Wi-Fi modules have become available which come with a real-time operating system and provide a simple means of wireless enabling any device which has and communicates via a serial port. This allows simple monitoring devices, for example a portable ecg monitor hooked up to a patient in the home, to be created. This Wi-Fi enabled device effectively becomes part 29 of the internet cloud and can communicate with any other node on the internet. The data collected can hop via the home's Wi-Fi access point to anywhere on the internet. These Wi-Fi modules are designed so that minimal Wi-Fi knowledge is required by designers to wireless enable their product. Social concerns Unintended and intended use by outsiders Measures to deter unauthorized users include suppressing the AP's service set identifier (SSID) broadcast, allowing only computers with known MAC addresses to join the network, and various encryption standards. Access points and computers using no encryption are vulnerable to eavesdropping by an attacker armed with packet sniffer software. If the eavesdropper has the ability to change his MAC address then he can potentially join the network by spoofing an authorised address. WEP encryption can protect against casual snooping but may also produce a misguided sense of security since freely available tools such as AirSnort can quickly recover WEP encryption keys. Once it has seen 5-10 million encrypted packets, AirSnort will determine the encryption password in under a second.[10] The newer Wi-Fi Protected Access (WPA) and IEEE 802.11i (WPA2) encyption standards do not have the serious weaknesses of WEP encryption, but require strong passphrases for full security. Recreational exploration of other people's access points has become known as wardriving, and the leaving of graffiti describing available services as warchalking. These activities may be illegal in certain jurisdictions, but existing legislation and caselaw is often unclear. However, it is also common for people to unintentionally use others' Wi-Fi networks without explicit authorization. Operating systems such as Windows XP SP2 and Mac OS X automatically connect to an available wireless network, depending on the network configuration. A user who happens to start up a laptop in the vicinity of an access point may find the computer has joined the network without any visible indication. Moreover, a user intending to join one network may instead end up on another one if the latter's signal is stronger. In combination with automatic discovery of other network resources (see DHCP and Zeroconf) this could possibly lead wireless users to send sensitive data to the wrong destination, as described by Chris Meadows in the February 2004 RISKS Digest. [3] In Singapore, using another person's Wi-Fi network is illegal under the Computer Misuse Act. A 17 year old has been arrested for simply tapping into his neighbor's wireless Internet connection and faces up to 3 years' imprisonment and a fine.[11] Wi-Fi vs. amateur radio In the US, Canada and Australia, a portion of the 2.4 GHz Wi-Fi radio spectrum is also allocated to amateur radio users. In the US, FCC Part 15 rules govern non-licensed 30 operators (i.e. most Wi-Fi equipment users). Under Part 15 rules, non-licensed users must "accept" (i.e. endure) interference from licensed users and not cause harmful interference to licensed users. Amateur radio operators are licensed users, and retain what the FCC terms "primary status" on the band, under a distinct set of rules (Part 97). Under Part 97, licensed amateur operators may construct their own equipment, use very high-gain antennas, and boost output power to 100 watts on frequencies covered by Wi-Fi channels 2-6. However, Part 97 rules mandate using only the minimum power necessary for communications, forbid obscuring the data, and require station identification every 10 minutes. Therefore, output power control is required to meet regulations, and the transmission of any encrypted data (for example https) is questionable. In practice, microwave power amplifiers are expensive. On the other hand, the short wavelength at 2.4 GHz allows for simple construction of very high gain directional antennas. Although Part 15 rules forbid any modification of commercially constructed systems, amateur radio operators may modify commercial systems for optimized construction of long links, for example. Using only 200 mW link radios and high gain directional antennas, a very narrow beam may be used to construct reliable links with minimal radio frequency interference to other users. Health risks There has been some debate about the effects of Wi-Fi transmissions on human health. Although the radiated energy is very low the use of laptops and PDAs may bring the sources very close to parts of the body for prolonged periods of time. There is no consensus amongst scientists, although there appears to be no evidence of harm it is impossible to prove the technology is completely safe. [12] History Wi-Fi uses both single carrier direct-sequence spread spectrum radio technology (part of the larger family of spread spectrum systems) and multi-carrier OFDM (Orthogonal Frequency Division Multiplexing) radio technology. These regulations then enabled the development of Wi-Fi, its onetime competitor HomeRF, and Bluetooth. Unlicensed spread spectrum was first made available by the Federal Communications Commission in 1985 and these FCC regulations were later copied with some changes in many other countries enabling use of this technology in all major countries.[13] The FCC action was proposed by Michael Marcus of the FCC staff in 1980 and the subsequent controversial regulatory action took 5 more years. It was part of a broader proposal to allow civil use of spread spectrum technology and was opposed at the time by main stream equipment manufacturers and many radio system operators. The precursor to Wi-Fi was invented in 1991 by NCR Corporation/AT&T (later Lucent & Agere Systems) in Nieuwegein, the Netherlands. It was initially intended for cashier systems; the first wireless products were brought on the market under the name WaveLAN with speeds of 1 Mbit/s to 2 Mbit/s. Vic Hayes, who held the chair of IEEE 802.11 for 10 years and has been named the 'father of Wi-Fi,' was involved in designing standards such as IEEE 802.11b, 802.11a and 802.11g. 31 Origin and meaning of the term 'Wi-Fi' Despite the similarity between the terms 'Wi-Fi' and 'Hi-Fi', statements reportedly made by Phil Belanger of the Wi-Fi Alliance contradict the popular conclusion that 'Wi-Fi' stands for 'Wireless Fidelity.'[14] According to Mr. Belanger, the Interbrand Corporation developed the brand 'Wi-Fi' for the Wi-Fi Alliance to use to describe WLAN products that are based on the IEEE 802.11 standards. In Mr. Belanger's words, "Wi-Fi and the yin yang style logo were invented by Interbrand. We [the founding members of the Wireless Ethernet Compatibility Alliance, now called the Wi-Fi Alliance] hired Interbrand to come up with the name and logo that we could use for our interoperability seal and marketing efforts. We needed something that was a little catchier than 'IEEE 802.11b Direct Sequence'." One possibility for the origin of the actual term is a simplified spelling of "Wi-Phy" or "Wireless Physical Network Layer". The Wi-Fi Alliance themselves invoked the term 'Wireless Fidelity' with the marketing of a tag line, "The Standard for Wireless Fidelity," but later removed the tag from their marketing. The Wi-Fi Alliance now seems to discourage the propagation of the notion that 'Wi-Fi' stands for 'Wireless Fidelity', but it has been referred to as such by the Wi-Fi Alliance in White Papers currently held in their knowledge base: "... a promising market for wireless fidelity (Wi-Fi) network equipment." [15] "A Short History of WLANs... The association created the Wi-Fi (Wireless Fidelity) logo to indicate that a product had been certified for interoperability." [16] 32 IEEE 802.11 From Wikipedia, the free encyclopedia IEEE 802.11 also known by the brand Wi-Fi, denotes a set of Wireless LAN/WLAN standards developed by working group 11 of the IEEE LAN/MAN Standards Committee (IEEE 802). The term 802.11x is also used to denote the set of amendments to the standard. The term IEEE 802.11 is also used to refer to the original 802.11 (1997), which is now sometimes called "802.11 legacy". For the application of these standards see WiFi. A Linksys Residential gateway with a 802.11b radio and a 4-port ethernet switch. A Compaq 802.11b PCI card The 802.11 family currently includes multiple over-the-air modulation techniques that all use the same basic protocol. The most popular techniques are those defined by the b/g and are amendments to the original standard; security was originally purposefully weak due to multi-governmental meddling on export requirements and was later enhanced via the 802.11i amendment after governmental and legislative changes. 802.11n is a new multi-streaming modulation technique that has recently been developed; the standard is still under draft development, although products designed based on proprietary pre-draft versions of the standard are being sold. Other standards in the family (c–f, h, j) are service amendments and extensions or corrections to previous specifications. 802.11b was the first widely accepted wireless networking standard, followed by 802.11g and then 802.11n. 802.11b and 802.11g standards use the 2.4 GHz (gigahertz) band, operating (in the United States) under Part 15 of the FCC Rules and Regulations. Because of this choice of frequency band, 802.11b and 802.11g equipment will suffer interference from microwave ovens, cordless telephones, Bluetooth devices, baby and security monitors, amateur radio 33 and other appliances using this same band. The 802.11a standard uses a different 5 GHz band, which is clean by comparison. 802.11a devices are not affected by products operating on the 2.4 GHz band. The segment of the radio frequency spectrum used varies between countries. While it is true that in the U.S. 802.11a and g devices may be legally operated without a licence. Unlicensed (legal) operation of 802.11 a & g is covered under Part 15 of the FCC Rules and Regulations. Frequencies used by channels one (1) through six (6) (802.11b) fall within the range of the 2.4 gigahertz amateur radio band. Licensed amateur radio operators may operate 802.11b/g devices under Part 97 of the FCC Rules and Regulations, allowing increased power output but not allowing any commercial content or encryption.[1] Protocols Summary Protocol Release Date Legacy 1997 Op. Frequency 2.4-2.5 GHz Throughput (Typ) 0.7 Mb/s Data Rate (Max) Range Range (Indoor) (Outdoor) 2 Mb/s ~25 meters ~75 meters 802.11a 1999 5.15-5.35/5.475.725/5.72523 Mb/s 5.875 GHz 54 Mb/s ~30 meters ~100 meters 802.11b 1999 2.4-2.5 GHz 4 Mb/s 11 Mb/s ~35 meters ~110 meters 802.11g 2003 2.4-2.5 GHz 19 Mb/s 54 Mb/s ~35 meters ~110 meters 248Mb/s ~70 = 2x2 ant meters ~160 meters 2007 (TGn draft 2.0) 802.11n 2.4 GHz and/or 74 Mb/s ratification 5 GHz timeline pushed to late 2008. 34 802.11 legacy The original version of the standard IEEE 802.11 released in 1997 specifies two raw data rates of 1 and 2 megabits per second (Mbit/s) to be transmitted via infrared (IR) signals or by either Frequency hopping or Direct-sequence spread spectrum in the Industrial Scientific Medical frequency band at 2.4 GHz. IR remains a part of the standard but has no actual implementations. The original standard also defines Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) as the medium access method. A significant percentage of the available raw channel capacity is sacrificed (via the CSMA/CA mechanisms) in order to improve the reliability of data transmissions under diverse and adverse environmental conditions. At least six different, somewhat-interoperable, commercial products appeared using the original specification, from companies like Alvarion (PRO.11 and BreezeAccess-II), BreezeCom, Digital / Cabletron (RoamAbout) , Lucent, Netwave Technologies (AirSurfer Plus and AirSurfer Pro), Symbol Technologies (Spectrum24), and Proxim (OpenAir). A weakness of this original specification was that it offered so many choices that interoperability was sometimes challenging to realize. It is really more of a "betaspecification" than a rigid specification, initially allowing individual product vendors the flexibility to differentiate their products but with little to no inter-vendor operability. Legacy 802.11 was rapidly supplemented (and popularized) by 802.11b. Widespread adoption of 802.11 networks only occurred after 802.11b was ratified and multiple product became available from multiple vendors and as a result few networks ran on the 802.11-1997 standard. 802.11a Release Date Op. Frequency Data Rate (Typ) Data Rate (Max) Range (Indoor) October 1999 5 GHz 23 Mb/s 54 Mb/s ~30 meters The 802.11a amendment to the original standard was ratified in 1999. The 802.11a standard uses the same core protocol as the original standard, operates in 5 GHz band, and uses a 52-subcarrier orthogonal frequency-division multiplexing (OFDM) with a maximum raw data rate of 54 Mb/s, which yields realistic net achievable throughput in the mid-20 Mb/s. The data rate is reduced to 48, 36, 24, 18, 12, 9 then 6 Mb/s if required. 802.11a originally had 12/13 non-overlapping channels, 12 that can be used indoor and 4/5 of the 12 that can be used in outdoor point to point configurations. Recently many countries of the world are allowing operation in the 5.47 to 5.725 GHZ Band as a secondary user using a sharing method derived in 802.11h. This will add another 12/13 Channels to the overall 5 GHz band enabling significant overall wireless capacity enabling the possibilty of 24+ channels in some countries. 802.11a is not interoperable with 802.11b as they operate on separate bands, except if using equipment that has a dual band capability. Nearly all enterprise class Access Points have dual band capability. 35 Since the 2.4 GHz band is heavily used, using the 5 GHz band gives 802.11a a significant advantage. However, this high carrier frequency also brings a slight disadvantage. The effective overall range of 802.11a is slightly less then 802.11b/g, it also means that 802.11a cannot penetrate as far as 802.11b since it is absorbed more readily when penetrating walls, or any other solid object. On the other hand, OFDM has fundamental propagation advantages when in a high multipath environment such as an indoor office. And the higher frequencies enable the building of smaller antennae with higher RF system gain which counteract the disadvantage of a higher band of operation. The increased number of usable channels (4 to 8 times as many in FCC countries) and the near absence of other interfering systems (microwave ovens, cordless phones, bluetooth products, baby monitors) makes the 5 GHz band the preferred WLAN band for professionals and businesses who require more capacity and reliability and are willing to pay a small premium for it. Different countries have different regulatory support, although a 2003 World Radiotelecommunications Conference made it easier for use worldwide. 802.11a is now approved by regulations in the United States and Japan, but in other areas, such as the European Union, it had to wait longer for approval. European regulators were considering the use of the European HIPERLAN standard, but in mid-2002 cleared 802.11a for use in Europe. In the U.S., a mid-2003 FCC decision may open more spectrum to 802.11a channels. Of the 52 OFDM subcarriers, 48 are for data and 4 are pilot subcarriers with a carrier separation of 0.3125 MHz (20 MHz/64). Each of these subcarriers can be a BPSK, QPSK, 16-QAM or 64-QAM. The total bandwidth is 20 MHz with an occupied bandwidth of 16.6 MHz. Symbol duration is 4 microseconds with a guard interval of 0.8 microseconds. The actual generation and decoding of orthogonal components is done in baseband using DSP which is then upconverted to 5 GHz at the transmitter. Each of the subcarriers could be represented as a complex number. The time domain signal is generated by taking an Inverse Fast Fourier transform (IFFT). Correspondingly the receiver downconverts, samples at 20 MHz and does an FFT to retrieve the original coefficients. The advantages of using OFDM include reduced multipath effects in reception and increased spectral efficiency. 802.11a products started shipping in late 2001, lagging 802.11b products due to the slow availability of the harder to manufacture 5 GHz components needed to implement products. 802.11a has not been widely adopted in the consumer market primarily because the less-expensive 802.11b was already widely adopted along with the arrival of less expensive early 802.11g product on the market, also some poor initial product implementations further limited its success. Manufacturers of 802.11a equipment responded to the lack of market success by significantly improving the implementations (current-generation 802.11a technology has range characteristics nearly identical to those of 802.11b), and by making technology that can use more than one band and 802.11 standard. There are dual-band, or dual-mode Access Points and NIC cards that can automatically handle 802.11a and b, or a and b/g, as available. Similarly, there are mobile adapters and access points which can support all these standards. 36 1472 byte Data rate Number of data Modulation Coding rate transfer duration (Mb/s) bits per symbol (µs) 6 BPSK 1/2 24 2012 9 BPSK 3/4 36 1344 12 QPSK 1/2 48 1008 18 QPSK 3/4 72 672 24 16-QAM 1/2 96 504 36 16-QAM 3/4 144 336 48 64-QAM 2/3 192 252 54 64-QAM 3/4 216 224 802.11b Release Date Op. Frequency Data Rate (Typ) Data Rate (Max) Range (Indoor) October 1999 2.4 GHz 4 Mb/s 11 Mb/s ~35 meters The 802.11b amendment to the original standard was ratified in 1999. 802.11b has a maximum raw data rate of 11 Mb/s and uses the same CSMA/CA media access method defined in the original standard. Due to the CSMA/CA protocol overhead, in practice the maximum 802.11b throughput that an application can achieve is about 5.9 Mb/s using TCP and 7.1 Mb/s using UDP. 802.11b products appeared on the market in early 2000, since 802.11b is a direct extension of the DSSS (Direct-sequence spread spectrum) modulation technique defined in the original standard. Technically, the 802.11b standard uses Complementary code 37 keying (CCK) as its modulation technique. The dramatic increase in throughput of 802.11b (compared to the original standard) along with simultaneous substantial price reductions led to the rapid acceptance of 802.11b as the definitive wireless LAN technology. 802.11b is normally used in a point-to-multipoint configuration, wherein an access point communicates via an omni-directional antenna with one or more clients that are located in a coverage area around the access point. Typical indoor range is 30 m (100 ft) at 11 Mb/s and 90 m (300 ft) at 1 Mb/s. The overall bandwidth is dynamically shared across all the users on a channel. With high-gain external antennas, the protocol can also be used in fixed point-to-point arrangements, typically at ranges up to 8 kilometers (5 miles) although some report success at ranges up to 80–120 km (50–75 miles) where line of sight can be established. This is usually done in place of costly leased lines or very cumbersome microwave communications equipment. Designers of such installations who wish to remain within the law must however be careful about legal limitations on effective radiated power. 802.11b cards can operate at 11 Mb/s, but will scale back to 5.5, then 2, then 1 Mb/s (also known as Adaptive Rate Selection), if signal quality becomes an issue. Since the lower data rates use less complex and more redundant methods of encoding the data, they are less susceptible to corruption due to interference and signal attenuation. Many companies created proprietary extensions and called them enhanced versions "802.11b+". These extensions have been largely obviated by the development of 802.11g, which has data rates up to 54 Mb/s and is backwards-compatible with 802.11b. 802.11g Release Date Op. Frequency Data Rate (Typ) Data Rate (Max) Range (Indoor) June 2003 2.4 GHz 19 Mbps 54 Mbps ~35 meters In June 2003, a third modulation standard was ratified: 802.11g. This flavor works in the 2.4 GHz band (like 802.11b) but operates at a maximum raw data rate of 54 Mb/s, or about 19 Mb/s net throughput (like 802.11a except with some additional legacy overhead). 802.11g hardware is backwards compatible with 802.11b hardware. Details of making b and g work well together occupied much of the lingering technical process. In an 11g network, however, the presence of an 802.11b participant does significantly reduce the speed of the overall 802.11g network. The modulation scheme used in 802.11g is orthogonal frequency-division multiplexing (OFDM) for the data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mb/s, and reverts to CCK (like the 802.11b standard) for 5.5 and 11 Mb/s and DBPSK/DQPSK+DSSS for 1 and 2 Mb/s. Even though 802.11g operates in the same frequency band as 802.11b, it can achieve higher data rates because of its similarities to 802.11a. The maximum range of 802.11g devices is slightly greater than that of 802.11b devices, but the range in which a 38 client can achieve the full 54 Mb/s data rate is much shorter than that of which a 802.11b client can reach 11 Mb/s. The 802.11g standard swept the consumer world of early adopters starting in January 2003, well before ratification due to fierce competition along with dramatic reductions in manufacturing costs. Corporate users held back - Cisco and other big equipment makers waited until ratification. By summer 2003, announcements were flourishing. Most of the dual-band 802.11a/b products became dual-band/tri-mode, supporting a, and b/g in a single mobile adapter card or access point. Despite its major acceptance, 802.11g suffers from the same interference as 802.11b in the already crowded 2.4 GHz range. Devices operating in this range include microwave ovens, Bluetooth devices, baby monitors and cordless telephones. Interference issues, and related problems within the 2.4 GHz band have become a major concern and frustration for users. Additionally the success of the standard has caused usage problems related to crowding in urban areas. This crowding can cause a dissatified user experience as the number of non-overlapping usable channels is only 3 in FCC nations (ch 1, 6, 11)or 4 in European nations (ch 1, 5, 9, 13). Also, the 802.11/11g MAC protocol doesn't share efficiently with more then a few users per channel. 802.11n Release Date Mid 2008 Op. Frequency 5 GHz and/or 2.4 GHz Data Rate (Typ) 74 Mbps Data Rate (Max) 248 Mbps (2 stream) Range (Indoor) ~70 meters Timeline Work on the 802.11n standard dates back to 2004. Publication is currently expected in September 2008, but major manufacturers are now releasing 'pre-N', 'draft n' or 'MIMObased' products based on early specs. [2] In January 2004, IEEE announced that it had formed a new 802.11 Task Group (TGn) to develop a new amendment to the 802.11 standard for wireless local-area networks. The real data throughput will reach a theoretical 270 Mbit/s for the required dual stream MIMO device. (which may require an even higher raw data rate at the physical layer), and should be up to 20 times faster than 802.11b, and up to 3 times faster than 802.11a and up to 4 times faster than 802.11g. In late July 2005, previous competitors TGn Sync, WWiSE, and a third group, MITMOT, said that they would merge their respective proposals as a draft. The standardization process is expected to be completed by the second quarter of 2009. 39 802.11n builds upon previous 802.11 standards by adding MIMO (multiple-input multiple-output). MIMO uses multiple transmitter and receiver antennas to allow for increased data throughput via spatial multiplexing and increased range by exploiting the spatial diversity, perhaps through coding schemes like Alamouti coding. Antennae are listed in a format of 2x2 for two receivers and two transmitters. A 4x4 is four receivers and four transmitters. The number of antennae relate to the number of simultaneous streams. The standards requirement is a 2x2 with two streams. The standard does optionally allow for the potential of a 4x4 with four streams. The Enhanced Wireless Consortium (EWC)[3] was formed to help accelerate the IEEE 802.11n development process and promote a technology specification for interoperability of next-generation wireless local area networking (WLAN) products. On 19 January 2006, the IEEE 802.11n Task Group approved the Joint Proposal's specification, based on EWC's draft specification. At the March 2006 meeting, the IEEE 802.11 Working Group sent the 802.11n Draft to its first letter ballot, allowing the 500+ 802.11 voters to review the document and suggest bugfixes, changes and improvements. On 2 May 2006, the IEEE 802.11 Working Group voted not to forward Draft 1.0 of the proposed 802.11n standard. Only 46.6% voted to approve the ballot. To proceed to the next step in the IEEE standards process, a majority vote of 75% is required. This letter ballot also generated approximately 12000 comments -- much more than anticipated. In November 2006, TGn voted to accept draft version 1.06, incorporating all accepted technical and editorial comment resolutions prior to this meeting. An additional 800 comment resolutions were approved during the November session which will be incorporated into the next revision of the draft. As of this meeting, three of the 8 comment topic ad hoc groups chartered in May have had completed their work and 88% of the technical comments had been resolved with approximately 370 remaining. On 19 January 2007, the IEEE 802.11 Working Group unanimously (100 yes, 0 no, 5 abstaining) approved a request by the 802.11n Task Group to issue a new Draft 2.0 of the proposed standard. Draft 2.0 was based on the Task Group's working draft version 1.10. Draft 2.0 was at this point in time the cumulative result of thousands of changes to the 11n document as based on all previous comments. On 7 February 2007, the results of Letter Ballot 95, a 15-day Procedural vote passed with 97.99% approval and 2.01% disapproval. On the same day, 802.11 Working Group announced the opening of Letter Ballot 97. It invited detailed technical comments to closed on 9 March 2007. On 9 March 2007, Letter Ballot 97, the 30-day Technical vote to approve Draft 2.0, closed. They were announced by IEEE 802 leadership during the Orlando Plenary on 12 March 2007. The ballot passed with an 83.4% approval, above the 75% minimum approval threshold. There were still approximately 3,076 unique comments, which will be individually examined for incorporation into the next revision of Draft 2. 40 According to the IEEE 802.11 Working Group Project Timelines, [4] the estimated 802.11n publish date is now September 2008. An 802.11 access point may operate in one of three modes: 1. Legacy (only 802.11a, and b/g) 2. Mixed (both 802.11a, and b/g, and n) 3. Greenfield (only 802.11n) - maximum performance See also: 802.11 non-standard equipment#Pre-802.11n equipment Channels and international compatibility See also: Wi-Fi#Technical information 802.11b and 802.11g -- as well as 802.11n when using the 2.4 GHz band -- divide the 2.4 GHz spectrum into 14 overlapping, staggered channels whose center frequencies are 5 megahertz (MHz) apart. The 802.11b, and 802.11g standards do specify the center frequency of the channel and a spectral mask width to a power level for that channel. The spectral mask for 802.11b requires that the signal be attenuated by at least 30 dB from its peak energy at ±11 MHz from the center frequency. This means that an 802.11b/g product occupies five channels to an energy level of 30 dB down from the peak or center of the signal. For an FCC country the valid channels are one through eleven: this limits the number of non-overlapped channels to three. The normal system level channel configurations for deployments are channels 1, 6 and 11. Since the spectral mask only defines power output restrictions up to ±22 MHz from the center frequency to be attenuated by 50dB, it is often assumed that the energy of the channel extends no further than these limits. It is more correct to say that, given the separation between channels 1, 6, and 11, the signal on any channel should be sufficiently attenuated to minimally interfere with a transmitter on any other channel. However, a typical transmitter on an adjacent channel can impact a weaker signal on a nonoverlapping channel only if it is closely placed to the victim radio (well within a meter). Although the statement that channels 1, 6, and 11 are "non-overlapping" is limited to a spacing or product density, the 1-6-11 guideline has merit. If transmitters are closer together than channels 1, 6, and 11 (for example, 1, 4, 7, and 10), overlap between the channels may cause unacceptable degradation of signal quality and throughput.[5] The channels that are available for use in a particular country differ according to the regulations of that country. In the United States, for example, FCC regulations only allow channels 1 through 11 to be used. In Europe channels 1-13 are licensed for 802.11b operation (with 1, 5, 9 and 13 usually deployed). In Japan, all 14 channels are licensed for 802.11b operation. Standard and Amendments Within the IEEE 802.11 Working Group[4], the following IEEE Standards Association Standard and Amendments exist: 41 IEEE 802.11 - THE WLAN STANDARD was original 1 Mbit/s and 2 Mb/s, 2.4 GHz RF and IR standard (1997), all the others listed below are Amendments to this standard, except for Recommended Practices 802.11F and 802.11T. IEEE 802.11a - 54 Mbit/s, 5 GHz standard (1999, shipping products in 2001) IEEE 802.11b - Enhancements to 802.11 to support 5.5 and 11 Mb/s (1999) IEEE 802.11c - Bridge operation procedures; included in the IEEE 802.1D standard (2001) IEEE 802.11d - International (country-to-country) roaming extensions (2001) IEEE 802.11e - Enhancements: QoS, including packet bursting (2005) IEEE 802.11F - Inter-Access Point Protocol (2003) Withdrawn February 2006 IEEE 802.11g - 54 Mb/s, 2.4 GHz standard (backwards compatible with b) (2003) IEEE 802.11h - Spectrum Managed 802.11a (5 GHz) for European compatibility (2004) IEEE 802.11i - Enhanced security (2004) IEEE 802.11j - Extensions for Japan (2004) IEEE 802.11k - Radio resource measurement enhancements (proposed - 2007?) IEEE 802.11l - (reserved and will not be used) IEEE 802.11m - Maintenance of the standard; odds and ends. (ongoing) IEEE 802.11n - Higher throughput improvements using MIMO (multiple input, multiple output antennas) (pre-draft - 2009?) IEEE 802.11o - (reserved and will not be used) IEEE 802.11p - WAVE - Wireless Access for the Vehicular Environment (such as ambulances and passenger cars) (working - 2009?) IEEE 802.11q - (reserved and will not be used, can be confused with 802.1Q VLAN trunking) IEEE 802.11r - Fast roaming Working "Task Group r" - 2007? IEEE 802.11s - ESS Extended Service Set Mesh Networking (working - 2008?) IEEE 802.11T - Wireless Performance Prediction (WPP) - test methods and metrics Recommendation (working - 2008?) IEEE 802.11u - Interworking with non-802 networks (for example, cellular) (proposal evaluation - ?) IEEE 802.11v - Wireless network management (early proposal stages - ?) IEEE 802.11w - Protected Management Frames (early proposal stages - 2008?) IEEE 802.11x - (reserved and will not be used, can be confused with 802.1x Network Access Control) IEEE 802.11y - 3650-3700 Operation in the U.S. (early proposal stages - ?) There is no standard or task group named "802.11x". Rather, this term is used informally to denote any current or future 802.11 amendment, in cases where further precision is not necessary. (The IEEE 802.1x standard for port-based network access control, is often mistakenly called "802.11x" when used in the context of wireless networks.) 802.11F and 802.11T are stand-alone documents, rather than amendments to the 802.11 standard and are capitalized as such. Standard or Amendment? Both the terms "standard" and "amendment" are used when referring to the different variants of IEEE 802.11. Which is correct? 42 As far as the IEEE is concerned there is only one standard - IEEE 802.11. This standard is continuously updated by means of amendments such as IEEE 802.11a, IEEE 802.11b etc. Periodically a new version of the IEEE 802.11 standard is produced combining the previous version of the standard and all amendments published up to that date. For example, there is a 2003 edition of the standard available for purchase[6] that incorporates the IEEE 802.11a, IEEE 802.11b, and IEEE 802.11d amendments. It is possible that at some point, only this version will be made available for free download replacing the six year old version of the base standard and the first three amendments. So the correct term for the base standard called "802.11 legacy" on this page would in fact be 802.11-1999. But outside the working group that produces IEEE 802.11 such accuracy is probably unnecessary. Nomenclature Various terms in 802.11 are used to specify aspects of wireless local-area networking operation, and may be unfamiliar to some readers. For example, Time Unit (usually abbreviated TU) is used to indicate a unit of time equal to 1024 microseconds. Numerous time constants are defined in terms of TU (rather than the nearly-equal millisecond). Also the term "Portal" is used to describe an entity that is similar to an IEEE 802.1D bridge. A Portal provides access to the WLAN by non-802.11 LAN STAs. Community networks With the proliferation of cable modems and DSL, there is an ever-increasing market of people who wish to establish small networks in their homes to share their high speed Internet connection. Wireless office networks are unsecured for guests outside a firewall or rarely secured with WEP, as the security can be very easily broken or WPA AES which is a government strength encryption method. Many hotspot or free networks frequently allow anyone within range, including passersby on the street outside, to connect to the Internet. There are also efforts by volunteer groups to establish wireless community networks to provide free wireless connectivity to the public. Security In 2001, a group from the University of California, Berkeley presented a paper describing weaknesses in the 802.11 Wired Equivalent Privacy (WEP) security mechanism defined in the original standard; they were followed by Fluhrer, Mantin, and Shamir's paper entitled "Weaknesses in the Key Scheduling Algorithm of RC4". Not long after, Adam Stubblefield and AT&T publicly announced the first verification of the attack. In the 43 attack they were able to intercept transmissions and gain unauthorized access to wireless networks. The IEEE set up a dedicated task group to create a replacement security solution, 802.11i (previously this work was handled as part of a broader 802.11e effort to enhance the MAC layer). The Wi-Fi Alliance announced an interim specification called Wi-Fi Protected Access (WPA) based on a subset of the then current IEEE 802.11i draft. These started to appear in products in mid-2003. IEEE 802.11i (also known as WPA2) itself was ratified in June 2004, and uses the Advanced Encryption Standard, instead of RC4, which was used in WEP and WPA. In January 2005, IEEE set up yet another task group TGw to protect management and broadcast frames, which previously were sent unsecured. See IEEE 802.11w 44 WiMAX: IEE802.16 From Wikipedia, the free encyclopedia WiMAX is defined as Worldwide Interoperability for Microwave Access by the WiMAX Forum, formed in June 2001 to promote conformance and interoperability of the IEEE 802.16 standard, officially known as WirelessMAN. WiMAX aims to provide wireless data over long distances, in a variety of different ways, from point to point links to full mobile cellular type access. In practical terms this enables you, for example, to browse the internet on a laptop computer without physically connecting the laptop to a socket in a wall. The Forum describes WiMAX as "a standards-based technology enabling the delivery of last mile wireless broadband access as an alternative to cable and DSL." Definitions of terms[1] The terms "fixed WiMAX", "mobile WiMAX", "802.16d" and "802.16e" are frequently used incorrectly. Correct definitions are: 802.16d Strictly speaking, 802.16d has never existed as a standard. The standard is correctly called 802.16-2004. However, since this standard is frequently called 802.16d, that usage also takes place in this article to assist readability. 802.16e Just as 802.16d has never existed, a standard called 802.16e hasn't either. It's an amendment to 802.16-2004, so is not a standard in its own right. It's properly referred to as 802.16e-2005. Fixed WiMAX This is a phrase frequently used to refer to systems built using 802.16-2004 as the air interface technology. Mobile WiMAX A phrase frequently used to refer to systems built using 802.16e-2005 as the air interface technology. "Mobile WiMAX" implementations are therefore frequently used to deliver pure fixed services. 45 Uses The bandwidth and reach of WiMAX make it suitable for the following potential applications: Connecting Wi-Fi hotspots with each other and to other parts of the Internet. Providing a wireless alternative to cable and DSL for last mile (last km) broadband access. Providing high-speed data and telecommunications services. Providing a diverse source of Internet connectivity as part of a business continuity plan. That is, if a business has a fixed and a wireless internet connection, especially from unrelated providers, they are unlikely to be affected by the same service outage. Providing nomadic connectivity. Broadband Access Many companies are closely examining WiMAX for "last mile" connectivity at high data rates. This could result in lower pricing for both home and business customers as competition lowers prices. In areas without pre-existing physical cable or telephone networks, WiMAX may be a viable alternative for broadband access that has been economically unavailable. Prior to WiMAX, many operators have been using proprietary fixed wireless technologies for broadband services. WiMAX access was used to assist with communications in Aceh, Indonesia, after the tsunami in December 2004. All communication infrastructures in the area were destroyed making the survivors unable to communicate with people outside the disaster area and vice versa. WiMAX provided broadband access that helped regenerate communication to and from Aceh so that condition post-tsunami can be retrieved. Subscriber Units WiMAX subscriber units are available in both indoor and outdoor versions from several manufacturers. Self-install indoor units are convenient, but radio losses mean that the subscriber must be significantly closer to the WiMAX base station than with professionally installed external units. As such, indoor installed units require a much higher infrastructure investment as well as operational cost (site lease, backhaul, maintenance) due to the high number of base stations required to cover a given area. Indoor units are comparable in size to a cable modem or DSL modem. Outdoor units are roughly the size of a textbook, and their installation is comparable to a residential satellite dish. Mobile applications Some cellular companies are evaluating WiMAX as a means of increasing bandwidth for a variety of data-intensive applications; indeed, Sprint Nextel announced in mid-2006 46 that it would invest about US$ 3 billion in a WiMAX technology buildout over the next few years[2]. In line with these possible applications is the technology's ability to serve as a high bandwidth "backhaul" for Internet or cellular phone traffic from remote areas back to an Internet backbone. Although the cost per user/point of WiMAX in a remote application will be higher, it is not limited to such applications, and may be an answer to reducing the cost of T1/E1 backhaul as well. Given the limited wired infrastructure in some developing countries, the costs to install a WiMAX station in conjunction with an existing cellular tower or even as a solitary hub are likely to be small in comparison to developing a wired solution. Areas of low population density and flat terrain are particularly suited to WiMAX and its range. For countries that have skipped wired infrastructure as a result of prohibitive costs and unsympathetic geography, WiMAX can enhance wireless infrastructure in an inexpensive, decentralized, deployment-friendly and effective manner. Technical information WiMAX is a term coined to describe standard, interoperable implementations of IEEE 802.16 wireless networks, in a rather similar way to Wi-Fi being interoperable implementations of the IEEE 802.11 Wireless LAN standard. However, WiMAX is very different from Wi-Fi in the way it works. MAC layer/ Data Link Layer In Wi-Fi the media access controller (MAC) uses contention access — all subscriber stations that wish to pass data through a wireless access point (AP) are competing for the AP's attention on a random interrupt basis. This can cause subscriber stations distant from the AP to be repeatedly interrupted by closer stations, greatly reducing their throughput. This makes services such as Voice over IP (VoIP) or IPTV, which depend on an essentially constant Quality of Service (QoS) depending on data rate and interruptibility, difficult to maintain for more than a few simultaneous users. In contrast, the 802.16 MAC uses a scheduling algorithm for which the subscriber station need compete once (for initial entry into the network). After that it is allocated an access slot by the base station. The time slot can enlarge and contract, but remains assigned to the subscriber station which means that other subscribers cannot use it. The 802.16 scheduling algorithm is stable under overload and over-subscription (unlike 802.11). It can also be more bandwidth efficient. The scheduling algorithm also allows the base station to control QoS parameters by balancing the time-slot assignments among the application needs of the subscriber stations. Physical layer The original WiMAX standard (IEEE 802.16) specified WiMAX for the 10 to 66 GHz range. 802.16a, updated in 2004 to 802.16-2004, added specifications for the 2 to 11 GHz range. 802.16-2004 was updated to 802.16e in 2005 and uses scalable orthogonal frequency-division multiple access (SOFDMA) as opposed to the OFDM version with 47 256 sub-carriers (of which 200 are used) in 802.16d. More advanced versions including 802.16e also bring Multiple Antenna Support through Multiple-input multiple-output communications. This brings potential benefits in terms of coverage, self installation, power consumption, frequency re-use and bandwidth efficiency. 802.16e also adds a capability for full mobility support. The WiMAX certification allows vendors with 802.16d products to sell their equipment as WiMAX certified, thus ensuring a level of interoperability with other certified products, as long as they fit the same profile. Most commercial interest is in the 802.16d and .16e standards, since the lower frequencies used in these variants suffer less from inherent signal attenuation and therefore give improved range and in-building penetration. Already today, a number of networks throughout the World are in commercial operation using certified WiMAX equipment compliant with the 802.16d standard. Comparison with Wi-Fi Possibly due to the fact both WiMAX and Wi-Fi begin with the same two letters, and are based upon IEEE standards beginning with 802., and both have a connection to wireless connectivity and the Internet, comparisons and confusion between the two are frequent. Despite this, both standards are aimed at different applications. WiMAX is a long range (many kilometers) system that uses licensed or unlicensed spectrum to deliver a point-to-point connection to the Internet from an ISP to an end user. Different 802.16 standards provide different types of access, from mobile (analogous to access via a cellphone) to fixed (an alternative to wired access, where the end user's wireless termination point is fixed in location.) Wi-Fi is a shorter range (range is typically measured in hundreds of m) system that uses unlicensed spectrum to provide access to a network, typically covering only the network operator's own property. Typically Wi-Fi is used by an end user to access their own network, which may or may not be connected to the Internet. If WiMAX provides services analogous to a cellphone, Wi-Fi is more analogous to a cordless phone. WiMAX is highly scalable from what are called 'femto' scale remote stations to multi-sector 'maxi' scale base that handle complex tasks of management and mobile handoff functions and include MIMO-AAS smart antenna subsystems. Due to the ease and low cost with which Wi-Fi can be deployed, it is sometimes used to provide Internet access to third parties within a single room or building available to the provider, sometimes informally, and sometimes as part of a business relationship. For example, many coffee shops, hotels, and transportation hubs contain Wi-Fi access points providing access to the Internet for patrons. Spectrum Allocations issues The 802.16 specification applies across a wide swath of the RF spectrum. However, specification is not the same as permission to use. There is no uniform global licensed spectrum for WiMAX. In the US, the biggest segment available is around 2.5 GHz[3], and is already assigned, primarily to Sprint Nextel and Clearwire. Elsewhere in the world, the 48 most likely bands used will be around 3.5 GHz, 2.3/2.5 GHz, or 5 GHz, with 2.3/2.5 GHz probably being most important in Asia. Some countries in Asia like India, Vietnam and Indonesia will use 3.3 GHz. There is some prospect in the United States that some of a 700 MHz band might be made available for WiMAX use, but it is currently assigned to analog TV and awaits the complete rollout of digital TV before it can become available, likely by 2009. In any case, there will be other uses suggested for that spectrum when it actually becomes open. The FCC auction for this spectrum is scheduled for the end of 2007. It seems likely that there will be several variants of 802.16, depending on local regulatory conditions and thus on which spectrum is used, even if everything but the underlying radio frequencies is the same. WiMAX equipment will not, therefore, be as portable as it might have been - perhaps even less so than WiFi, whose assigned channels in unlicensed spectrum vary little from jurisdiction to jurisdiction. Manufacturers are compelled to provide multi-spectrum devices that can be used across different regions and regulatory requirements. WISOA is an organization that promotes roaming among service providers. However, this is no different than current mobile phones with dual band, triband and even quadband capabilities. Equipment vendors have already announced the development of multiband subscriber units. WiMax profiles define channel size, TDD/FDD and other necessary attributes in order to have interoperating products. The current fixed profiles define for both TDD and FDD profiles. At this point, all of the mobile profiles are TDD only. The fixed profiles have channel sizes of 3.5 MHz, 5 MHz, 7 MHz and 10 MHz. The mobile profiles are 5 MHz and 10 MHz. One of significant advantages of WiMax is spectrum efficiency. For example, 802.16-2004 (fixed) has a spectral efficiency of 3.7 bits/hertz. Compared to similar technologies that often are less than 1 bit/hertz efficient such as WiFi. Limitations A commonly held misconception is that WiMAX will deliver 70 Mbit/s, over 30 miles (48 kilometers). Each of these is true individually, given ideal circumstances, but they are not simultaneously true. In practice this means that in line-of-sight environments you could deliver symmetrical speeds of 10 Mbit/s at 10 km but in urban environments it is more likely that 30% of installations may be non-line-of-sight and therefore users may only receive 10 Mbit/s over 2 km. WiMAX has some similarities to DSL in this respect, where one can either have high bandwidth or long reach, but not both simultaneously. The other feature to consider with WiMAX is that available bandwidth is shared between users in a given radio sector, so if there are many active users in a single sector, each will get reduced bandwidth. However, unlike SDSL where contention is very noticeable at a 5:1 ratio (if you are sharing your connection with a large media firm for example), WiMAX does not have this problem. Typically each cell has a whole 100 Mbit/s backhaul so there is no contention here. In practice, many users will have a range of 2-, 4, 6-, 8- or 10 Mbit/s services and the bandwidth can be shared. If the network becomes busy the business model is more like GSM or UMTS than DSL. It is easy to predict capacity requirements as you add customers. Additional radio cards can be added on the same sector to increase the capacity. 49 Standards The current WiMax incarnation, Mobile WiMax, is based upon IEEE Std 802.16e2005[4], approved in December 2005. It is an amendment of IEEE Std 802.16-2004[5] and so the actual standard is 802.16-2004 as amended by 802.16e-2005 - the specifications need to be read together to understand them. IEEE Std 802.16-2004 addresses only fixed systems. It replaced IEEE Standards 802.162001, 802.16c-2002, and 802.16a-2003. IEEE 802.16e-2005 IEEE 802.16e-2005 improves upon IEEE 802.16-2004 by: Scaling of the Fast Fourier Transform (FFT) to the channel bandwidth in order to keep the carrier spacing constant across different channel bandwidths (1.25-20 MHz). Constant carrier spacing results in a higher spectrum efficiency in wide channels, and a cost reduction in narrow channels. Also known as Scalable OFDMA (SOFDMA). Improving NLOS coverage by utilizing advanced antenna diversity schemes, and hybrid-Automatic Retransmission Request (hARQ) Improving coverage by introducing Adaptive Antenna Systems (AAS) and Multiple Input Multiple Output (MIMO) technology Increasing system gain by use of denser sub-channelization, thereby improving indoor penetration Introducing high-performance coding techniques such as Turbo Coding and LowDensity Parity Check (LDPC), enhancing security and NLOS performance Introducing downlink sub-channelization, allowing administrators to trade coverage for capacity or vice versa Enhanced Fast Fourier Transform algorithm can tolerate larger delay spreads, increasing resistance to multipath interference Adding an extra QoS class (enhanced real-time Polling Service) more appropriate for VoIP applications. Adding support for mobility (soft and hard handover between base stations). This is seen as one of the most important aspects of 802.16e-2005, and is the very basis of 'Mobile WiMax'. 802.16d vendors point out that fixed WiMAX offers the benefit of available commercial products and implementations optimized for fixed access. It is a popular standard among alternative service providers and operators in developing areas due to its low cost of deployment and advanced performance in a fixed environment. Fixed WiMAX is also seen as a potential standard for backhaul of wireless base stations such as cellular, WiFi or even mobile WiMAX. SOFDMA (used in 802.16e-2005) and OFDM256 (802.16d) are not compatible so most equipment will have to be replaced if an operator wants or needs to move to the later standard. However, some manufacturers are planning to provide a migration path for older equipment to SOFDMA compatibility which would ease the transition for those 50 networks which have already made the OFDM256 investment. This affects a relatively small number users and operators. WiBro South Korea’s electronics and telecommunication industry spearheaded by Samsung Electronics and ETRI has developed its own standard, WiBro. In late 2004, Intel and LG Electronics have agreed on interoperability between WiBro and WiMAX. WiBro has South Korean government support with the requirement for each carrier to spend over US$1 billion for deployments. Korea sought to develop WiBro as a regional and potentially international alternative to 3.5G or 4G cellular systems. But given the lack of momentum as a standard, WiBro has joined WiMAX and agreed to harmonize with the similar OFDMA 802.16e version of the standard. What makes WiBro roll-outs a good 'test case' for the overall WiMAX effort is that it is mobile, well thought out for delivery of wireless broadband services, and the fact that the deployment is taking place in a highly sophisticated, broadband-saturated market. WiBro will go up against 3G and very high bandwidth wire-line services rather than as gap-filler or rural under-served market deployments as is often exampled as the 'best fit' markets for WiMAX. Associations WiMAX Forum The WiMAX Forum is the organization dedicated to certifying the interoperability of WiMAX products. Those that pass conformance and interoperability testing achieve the "WiMAX Forum Certified" designation and can display this mark on their products and marketing materials. Some vendors claim that their equipment is "WiMAX-ready", "WiMAX-compliant", or "pre-WiMAX", if they are not officially WiMAX Forum Certified. [6] WiMAX Spectrum Owners Alliance - WiSOA WiSOA is the first global organization composed exclusively of owners of WiMAX spectrum without plans to deploy WiMAX technology in those bands. WiSOA is focussed on the regulation, commercialisation, and deployment of WiMAX spectrum in the 2.3–2.5 GHz and the 3.4–3.5 GHz ranges. WiSOA are dedicated to educating and 51 informing its members, industry representatives and government regulators of the importance of WiMAX spectrum, its use, and the potential for WiMAX to revolutionise broadband.[7] Competing technologies Within the marketplace, WiMAX's main competition comes from existing widely deployed wireless systems such as UMTS and CDMA2000, as well as a number of Internet oriented systems such as HIPERMAN and WiBro. 3G and 4G Cellular Phone Systems Both of the two major 3G systems, CDMA2000 and UMTS, compete with WiMAX. Both offer DSL-class Internet access in addition to phone service. UMTS has also been enhanced to compete directly with WiMAX in the form of UMTS-TDD, which can use WiMAX oriented spectrum and provides a more consistent, if lower bandwidth at peak, user experience than WiMAX. 3G cellular phone systems usually benefit from already having entrenched infrastructure, being upgrades from earlier systems. Users can usually fall back to older systems when they move out of range of upgraded equipment, often relatively seamlessly. The major cellular standards are being evolved to so-called 4G, high bandwidth, low latency, all-IP networks with voice services built on top. With GSM/UMTS, the move to 4G is the 3GPP Long Term Evolution effort. For AMPS/TIA derived standards such as CDMA2000, a replacement called Ultra Mobile Broadband is under development. In both cases, existing air interfaces are being discarded, in favour of OFDMA for the downlink and a variety of OFDM based solutions for the uplink. These will bring Internet access speeds comparable to, or better than, WiMAX. In some areas of the world the wide availability of UMTS and a general desire for standardization has meant spectrum has not been allocated for WiMAX: in July 2005, the EU-wide frequency allocation for WiMAX was blocked. 52 Comparison of Mobile Internet Access methods Standard Family Primary Use Radio Tech Notes Quoted speeds only achievable at very short ranges, more practically 10 Mbps at 10 km. 70 70 HIPERMAN Mobile Internet OFDM 56.9 56.9 WiBro WiBro 50 50 Mobile range (900 m) iBurst iBurst 802.20 Mobile Internet HC-SDMA 64 64 3-12 km .384 5.76 HSDPA widely deployed. Typical downlink rates today 12Mbps, ~200kbps uplink; future downlink up to 28.8Mbps. 16 Reported speeds according to IPWireless using 16QAM modulation similar to HSDPA+HSUPA >50 Still in development 802.16e HIPERMAN WiMAX Mobile Internet MIMO-SOFDMA Downlink Uplink (Mbps) (Mbps) Mobile Internet OFDMA UMTS WUMTS/3GSM Mobile phone CDMA HSDPA+HSUPA CDMA/FDD UMTS-TDD UMTS/3GSM Mobile Internet CDMA/TDD LTE UMTS UMTS/4GSM General 4G .384 14.4 16 OFDMA/MIMO/SC>100 FDMA (HSOPA) 53 1xRTT EVDO 1x Rev. 0 EVDO 1x Rev.A EV-DO Rev.B CDMA2000 CDMA2000 Mobile phone CDMA Mobile Internet CDMA/FDD 0.144 2.45 3.1 4.9xN 0.144 Obsoleted by EV-DO 0.15 1.8 1.8xN Rev B note: N is the number of 1.25 MHz chunks of spectrum used. Not yet deployed. Mobile Broadband Wireless Access Mobile Broadband Wireless Access (MBWA) is a technology being developed by IEEE 802.20 and is a aimed at wireless mobile broadband for operations from 120 to 350 km/h. The 802.20 standard has taken on many of the methods behind Mobile WiMAX, including high speed dynamic modulation and similar scalable OFDMA capabilities. It apparently retains fast hand-off, Forward Error Correction (FEC) and cell edge enhancements. The Working Group was temporarily suspended in mid 2006 by the IEE-SA Standards Board since it had been the subject of a number of appeals, and a preliminary investigation of one of these "revealed a lack of transparency, possible 'dominance,' and other irregularities in the Working Group" [8]. In September 2006 the IEE-SA Standards Board approved a plan to enable the working group to continue under new conditions, and the standard is now expected to be finalized in Q4 2007. Internet Oriented Systems Early WirelessMAN standards, the European standard HIPERMAN and Korean standard WiBro have been harmonized as part of WiMAX and are no longer seen as competition but as complementary. All networks now being deployed in South Korea, the home of the Wibro standard, are now WiMAX. As a short-range mobile internet solution, such as in cafes and at transportation hubs like airports, the popular WiFi 802.11b/g system is widely deployed, and provides enough coverage for some users to feel subscription to a WiMAX service is unnecessary. The following table should be treated with caution as it only shows peak rates which are potentially very misleading. Comparison Main article: Comparison of wireless data standards 54 v•d•e Notes: All speeds are theoretical maximums and will vary by a number of factors, including the use of external antennae, distance from the tower and the ground speed (i.e. communications on a train may be poorer than when standing still.) Usually the bandwidth is shared between several terminals. The performance of each technology is determined by a number of constraints, including the spectral efficiency of the technology, the cell sizes used, and the amount of spectrum available. For more information, see Comparison of wireless data standards. Future Development Mobile WiMAX based upon 802.16e-2005 has been proposed as IP-OFDMA for inclusion as the sixth wireless link system under IMT-2000. If accepted in September 2007 ITU session, which looks likely, this stands to hasten acceptance by regulatory authorities for use in cellular spectrum. WiMAX II, 802.16m will be proposed for IMTAdvanced 4G. The goal for the long term evolution of both WiMAX and LTE is to achieve 100 Mbit/s mobile and 1 Gbit/s fixed-nomadic bandwidth as set by ITU for 4G NGMN (Next Generation Mobile Network) systems through the adaptive use of MIMO-AAS and smart, granular network topologies. 3GPP LTE and WiMAX-m are concentrating much effort on MIMO-AAS, mobile multi-hop relay networking and related developments needed to deliver 10X and higher Co-Channel reuse multiples. Since the evolution of core air-link technologies has approached the practical limits imposed by Shannon's Theorem, the evolution of wireless has embarked on pursuit of the 3X to 10X+ greater bandwidth and network efficiency gains that are expected by advances in the spatial and smart wireless broadband networking technologies. What will clearly define 4G more than either WCDMA or OFDMA wireless link methods will be wireless networks that more effectively adapt to and take advantage of available spectrum. Current Deployments Main article: List of Deployed WiMAX networks (Country by Country List) The WiMAX Forum now lists over 250 WiMAX trials and deployments. Current and planned deployments and the bands in which they operate and the standards they use are listed in above article. On May 1, 2007, FCC Approves First WIMAX-class Laptop Card. [9] 55 IEEE 802.16 From Wikipedia, the free encyclopedia Jump to: navigation, search The IEEE 802.16 Working Group on Broadband Wireless Access Standards, which was established by IEEE Standards Board in 1999, aims to prepare formal specifications for the global deployment of broadband Wireless Metropolitan Area Networks. The Workgroup is a unit of the IEEE 802 LAN/MAN Standards Committee. A related future technology Mobile Broadband Wireless Access (MBWA) is under development in IEEE 802.20. Although the 802.16 family of standards is officially called WirelessMAN, it has been dubbed “WiMAX” (from "Worldwide Interoperability for Microwave Access") by an industry group called the The WiMAX Forum. The mission of the Forum is to promote and certify compatibility and interoperability of broadband wireless products. 802.16 standards The first 802.16 standard was approved in December 2001. It delivered a standard for point to multipoint Broadband Wireless transmission in the 10-66 GHz band, with only a Line of Sight (LOS) capability. It uses a single carrier (SC) physical (PHY) standard. 802.16a was an amendment to 802.16 and delivered a point to multipoint capability in the 2-11 GHz band. For this to be of use, it also required a non line of sight (NLOS) capability, and the PHY standard was therefore extended to include Orthogonal Frequency Division Multiplex (OFDM) and Orthogonal Frequency Division Multiple Access (OFDMA). 802.16a was ratified in January 2003 and was intended to provide "last mile" fixed broadband access. 802.16c, a further amendment to 802.16, delivered a system profile for the 10-66 GHz 802.16 standard. In September 2003, a revision project called 802.16d commenced aiming to align the standard with aspects of the European Telecommunications Standards Institute (ETSI) HIPERMAN standard as well as lay down conformance and test specifications. This project concluded in 2004 with the release of 802.16-2004 and the withdrawal of the earlier 802.16 documents, including the a/b/c amendments. An amendment to 802.16-2004, IEEE 802.16e-2005 (formerly known as IEEE 802.16e), addressing mobility, was concluded in 2005. This implemented a number of enhancements to 802.16-2004, including better support for Quality of Service and the use of Scalable OFDMA, and is sometimes called “Mobile WiMAX”, after the WiMAX forum for interoperability. 56 Amendments in progress Active amendments: 802.16f – Management Information Base Amendments under development: 802.16g - Management Plane Procedures and Services Amendments at pre-draft stage: 802.16h - Improved Coexistence Mechanisms for License-Exempt Operation 802.16i - Mobile Management Information Base 802.16j - Multihop Relay Specification 802.16k - Bridging of 802.16 802.16 m - Advanced Air Interface. Data rates of 100 Mbit/s for mobile applications and 1 Gbit/s for fixed applications, cellular, macro and micro cell coverage, with currently no restrictions on the RF bandwidth (which is expected to be 20 MHz or higher). [1]. The proposed work plan would allow completion of the standard by Sept 2008 for approval by Dec 2008. 802.16e-2005 Technology The 802.16 standard essentially standardizes 2 aspects of the air interface - the physical layer (PHY) and the Media Access Control layer (MAC). This section provides an overview of the technology employed in these 2 layers in the current version of the 802.16 specification (which is strictly 802.16-2004 as amended by 802.16e-2005, but which will be referred to as 802.16e for brevity). PHY 802.16e uses Scalable OFDMA to carry data, supporting channel bandwidths of between 1.25 MHz and 20 MHz, with up to 2048 sub-carriers. It supports adaptive modulation and coding, so that in conditions of good signal, a highly efficient 64 QAM coding scheme is used, whereas where the signal is poorer, a more robust BPSK coding mechanism is used. In intermediate conditions, 16 QAM and QPSK can also be employed. Other PHY features include support for Multiple-in Multiple-out (MIMO) antennas in order to provide good NLOS characteristics (or higher bandwidth) and Hybrid automatic repeat request (HARQ) for good error correction performance. MAC The 802.16 MAC describes a number of Convergence Sublayers which describe how wireline technologies such as Ethernet, ATM and IP are encapsulated on the air interface, and how data is classified, etc. It also describes how secure communications are delivered, by using secure key exchange during authentication, and encryption using AES or DES as the encryption mechanism) during data transfer. Further features of the MAC 57 layer include power saving mechanisms (using Sleep Mode and Idle Mode) and handover mechanisms. A key feature of 802.16 is that it is a connection oriented technology. The subscriber station (SS) cannot transmit data until it has been allocated a channel by the Base Station (BS). This allows 802.16e to provide strong support for Quality of Service (QoS). QoS QoS in 802.16e is supported by allocating each connection between the SS and the BS (called a service flow in 802.16 terminology) to a specific QoS class. In 802.16e, there are 5 QoS classes: 802.16e-2005 QoS classes Service Abbrev Definition Typical Applications Unsolicited Grant UGS Service Real-time data streams comprising fixed-size data packets issued at periodic intervals T1/E1 transport Extended Realtime Polling Service Real-time service flows that generate variable-sized data packets on a periodic basis VoIP Real-time Polling rtPS Service Real-time data streams comprising variable-sized data packets that are issued at periodic intervals MPEG Video Non-real-time Polling Service nrtPS Delay-tolerant data streams FTP with guaranteed comprising variable-sized data packets minimum for which minimum data rate is throughput required BE Data streams for which no minimum service level is required and therefore may be handled on a space-available basis Best Effort ertPS HTTP The BS and the SS use a service flow with an appropriate QoS class (plus other parameters, such as bandwidth and delay) to ensure that application data receives QoS treatment appropriate to the application. Certification Because the IEEE only sets specifications but does not test equipment for compliance with them, the WiMAX Forum runs a certification program wherein members pay for certification. WiMAX certification by this group is intended to guarantee compliance 58 with the standard and interoperability with equipment from other manufacturers. The mission of the Forum is to promote and certify compatibility and interoperability of broadband wireless products. 59 Mesh networking From Wikipedia, the free encyclopedia Image showing mesh network layout Mesh networking is a way to route data, voice and instructions between nodes. It allows for continuous connections and reconfiguration around broken or blocked paths by “hopping” from node to node until the destination is reached. A mesh network whose nodes are all connected to each other is a fully connected network. Mesh networks differ from other networks in that the component parts can all connect to each other via multiple hops, and they generally are not mobile. Mesh networks can be seen as one type of ad hoc network. Mobile ad-hoc networking (MANet), and mesh networking are therefore closely related, but mobile ad hoc networks also has to deal with the problems introduced by the mobility of the nodes. Mesh networks are self-healing: the network can still operate even when a node breaks down or a connection goes bad. As a result, a very reliable network is formed. This concept is applicable to wireless networks, wired networks, and software interaction. Examples A MIT project is developing the XO-1 laptop or "Children's Machine" which is intended for under-privileged schools in developing nations and plans to use mesh networking to create a robust and inexpensive infrastructure. The instantaneous connections made by the laptops are claimed by the project to reduce the need for an external infrastructure such as the internet to reach all areas, because a connected node could share the connection with nodes nearby. A similar concept has also been implemented by Greenpacket by its application called SONbuddy. In Cambridge, UK, on the 3rd June 2006, mesh networking was used at the “Strawberry Fair” to run mobile live television, radio and internet services to an estimated 80,000 people. The Champaign-Urbana Community Wireless Network (CUWiN) project is developing mesh networking software based on open source implementations of the Hazy-Sighted Link State Routing Protocol and Expected Transmission Count metric. 60 Cognitive radio From Wikipedia, the free encyclopedia Cognitive radio is a paradigm for wireless communication in which either a network or a wireless node changes its transmission or reception parameters to communicate efficiently without interfering with licensed users. This alteration of parameters is based on the active monitoring of several factors in the external and internal radio environment, such as radio frequency spectrum, user behaviour and network state. History The idea of cognitive radio was first presented officially in an article by Joseph Mitola III and Gerald Q. Maguire, Jr. [1]. It was a novel approach in wireless communications that Mitola later described as: The point in which wireless personal digital assistants (PDAs) and the related networks are sufficiently computationally intelligent about radio resources and related computer-to-computer communications to detect user communications needs as a function of use context, and to provide radio resources and wireless services most appropriate to those needs.[2] It was thought of as an ideal goal towards which a software-defined radio platform should evolve: a fully reconfigurable wireless black-box that automatically changes its communication variables in response to network and user demands. Regulatory bodies in various countries (including the Federal Communications Commission in the United States) found that most of the Radio frequency spectrum was inefficiently utilized [3]. For example, cellular network bands are overloaded in most parts of the world, but amateur radio and paging frequencies are not. Independent studies performed in some countries confirmed that observation [4], [5] and concluded that spectrum utilization depends strongly on time and place. Moreover, fixed spectrum allocation prevents rarely used frequencies (those assigned to specific services) from being used by unlicensed users, even when their transmissions would not interfere at all with the assigned service. This was the reason for allowing unlicensed users to utilize licensed bands whenever it would not cause any interference (by avoiding them whenever legitimate user presence is sensed). This paradigm for wireless communication is known as Cognitive Radio. Terminology Depending on the set of parameters taken into account in deciding on transmission and reception changes, and for historical reasons, we can distinguish certain types of cognitive radio. The main two are: Full Cognitive Radio ("Mitola radio"): in which every possible parameter observable by a wireless node or network is taken into account. Spectrum Sensing Cognitive Radio: in which only the radio frequency spectrum is considered. 61 Also, depending on the parts of the spectrum available for cognitive radio, we can distinguish: Licensed Band Cognitive Radio: in which cognitive radio is capable of using bands assigned to licensed users, apart from unlicensed bands, such as UNII band or ISM band. One such system is described in the IEEE 802.15 Task group 2 [6] specification. Unlicensed Band Cognitive Radio: which can only utilize unlicensed parts of radio frequency spectrum. An example of Unlicensed Band Cognitive Radio is IEEE 802.19 [7]. Technology Although cognitive radio was initially thought of as a software-defined radio extension (Full Cognitive Radio), most of the research work is currently focusing on Spectrum Sensing Cognitive Radio, particularly in the TV bands. The essential problem of Spectrum Sensing Cognitive Radio is in designing high quality spectrum sensing devices and algorithms for exchanging spectrum sensing data between nodes. It has been shown [8] that a simple energy detector cannot guarantee the accurate detection of signal presence, calling for more sophisticated spectrum sensing techniques and requiring information about spectrum sensing to be exchanged between nodes regularly. Increasing the number of cooperating sensing nodes decreases the probability of false detection [9]. Filling free radio frequency bands adaptively (OFDM) seems to be the ideal approach. In fact, Timo A. Weiss and Friedrich K. Jondral of the University of Karlsruhe proposed a Spectrum Pooling system [10] in which free bands sensed by nodes were immediately filled by OFDM subbands. Applications of Spectrum Sensing Cognitive Radio include emergency networks and WLAN higher throughput and transmission distance extensions. The main functions of Cognitive Radios are [11]: Spectrum Sensing: detecting the unused spectrum and sharing it without harmful interference with other users, it is an important requirement of the Cognitive radio network to sense spectrum holes, detecting primary users is the most efficient way to detect spectrum holes. Spectrum sensing techniques can be classified into three categories: o Transmitter detection: cognitive radios must have the capability to determine if a signal from a primary transmitter is locally present in a certain spectrum, there are several approaches proposed: matched filter detection energy detection cyclostationary feature detection o Cooperative detection: refers to spectrum sensing methods where information from multiple Cognitive radio users are incorporated for primary user detection. o Interference based detection. 62 Spectrum Management: Capturing the best available spectrum to meet user communication requirements. Cognitive radios should decide on the best spectrum band to meet the Quality of service requirements over all available spectrum bands, therefore spectrum management functions are required for Cognitive radios, these management functions can be classified as: o spectrum analysis o spectrum decision Spectrum Mobility: is defined as the process when a cognitive radio user exchanges its frequency of operation. Cognitive radio networks target to use the spectrum in a dynamic manner by allowing the radio terminals to operate in the best available frequency band, maintaining seamless communication requirements during the transition to better spectrum Spectrum Sharing: providing the fair spectrum scheduling method, one of the major challenges in open spectrum usage is the spectrum sharing. It can be regarded to be similar to generic media access control MAC problems in existing systems 63 IEEE 802.20 From Wikipedia, the free encyclopedia IEEE 802.20 (IEEE802.20) or Mobile Broadband Wireless Access (MBWA) Working Group, the establishment of which was approved by IEEE Standards Board on December 11, 2002, aims to prepare a formal specification for a packet-based air interface designed for IP-based services. It is hoped that such an interface will allow the creation of low-cost, always-on, and truly mobile broadband wireless networks, nicknamed as Mobile-Fi. IEEE 802.20 will be specified according to a layered architecture, which is consistent with other IEEE 802 specifications. The scope of the working group consists of the physical (PHY), medium access control (MAC), and logical link control (LLC) layers. The air interface will operate in bands below 3.5 GHz and with a peak data rate of over 1 Mbit/s. The goals of 802.20 and 802.16e, the so-called "mobile WiMAX", are similar. A draft 802.20 specification was balloted and approved on January 18th, 2006. The baseline specifications that have been proposed for this specification aim considerably higher than those available on our current mobile architecture. The draft standard's proposed benefits: IP roaming & handoff (at more than 1 Mbit/s) New MAC and PHY with IP and adaptive antennas Optimized for full mobility up to vehicular speeds of 250 km/h Operates in Licensed Bands (below 3.5 GHz) Utilizes Packet Architecture Low Latency On 8 June 2006, the IEEE-SA Standards Board directed that all activities of the 802.20 Working Group be temporarily suspended. This suspension is effective immediately and will continue in effect until 1 October 2006. [1] [2] On 15 September 2006, the IEE-SA Standards Board approved a plan to enable the IEEE 802.20 Working Group to move forward with its work to develop a mobile broadband wireless access standard and provide the best opportunity for its completion and approval. [3] 64 IEEE 802.22 From Wikipedia, the free encyclopedia IEEE 802.22 is a new working group of IEEE 802 LAN/MAN standards committee which aims at constructing Wireless Regional Area Network utilizing white spaces (channels that are not used in the frequency band) in the already allocated TV frequency spectrum. The use of the spectrum will be used in an opportunistic way in order not interfere with any TV channel that is transmitting. Technology The IEEE 802.22 working group on Wireless Regional Area Networks (WRAN) is the youngest group of the IEEE 802 LAN/MAN standards committee. Its project, formally called as Standard for Wireless Regional Area Networks (WRAN) - Specific requirements - Part 22: Cognitive Wireless RAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Policies and procedures for operation in the TV Bands focuses on constructing a consistent, national fixed point-to-multipoint WRAN that will utilize UHF/VHF TV bands between 54 and 862 MHz. Specific TV channels as well as the guard bands of these channels are planned to be used for communication in IEEE 802.22. Because the IEEE 802.22 working group was formed in 2004, nothing has yet been specified regarding the particular functionalities of PHY/MAC layer. However the IEEE, together with the FCC, is pursuing a centralized approach for available spectrum discovery. Specifically each Access Point (AP) would be armed with a GPS receiver which would allow its position to be reported. This information would be sent back to centralized servers (in the USA these would be managed by the FCC), which would respond with the information about available free TV channels and guard bands in the area of the AP. Other proposals would allow local spectrum sensing only, where the AP would decide by itself which channels are available for communication. A combination of these two approaches is also envisioned. Overview of the WRAN Topology 802.22 specifies that the network should operate in a point to multipoint basis (P2MP). The system will be formed by base stations (BS) and customer premise equipments (CPE, above mentioned as Access Points, AP's). The CPE's will be attached to a BS via a wireless link in the frequencies mentioned above. The BS's will control the medium access for all the CPE's attached to it. One key feature of the WRAN Base Stations is that they will be capable of performing a distributed sensing. This is that the CPE's will be sensing the spectrum and will be sending periodically reports to the BS informing it about what they sense. The BS, with the information gathered, will evaluate if it is necessary a change in the utilized channel, or on the contrary, stay transmitting and receiving in the same one. 65 An approach to the PHY layer The goal of this layer is to provide an excellent performance while keeping a simple complexity. The PHY layer must be able to adapt to the different conditions and also needs to be flexible for jumping from channel to channel without errors in transmission or losing clients (CPE's). This flexibility is also required for being able to dynamically adjust the bandwidth, modulation and coding schemes. OFDMA will be the modulation scheme for transmission in up and downlinks. With OFDMA it will be possible to achieve this fast adaptation needed for the BS's and CPE's. By using just one TV channel (a TV channel has a bandwidth of 6 MHz, in some countries they can be of 7 or 8 MHz) the approximate maximum bit rate is 19 Mbps at a 30 km distance. The speed and distance achieved is not enough to fulfil the requirements of the standard. The feature Channel Bonding deals with this problem. Channel Bonding consists in utilizing more than one channel for Tx / Rx. This allows the system to have a bigger bandwidth which will be reflected in a better system performance. An approach to the MAC layer This layer will be based in Cognitive Radio Technology. It needs to be also able to adapt dynamically to changes in the environment by sensing the spectrum. The MAC layer will consist of two structures: Frame and Superframe. A superframe will be formed by many frames. The superframe will have a SCH (Superframe Control Header) and a preamble. These will be sent by the BS in every channel that it's possible to transmit and not cause interference. When a CPE is turned on, it will sense the spectrum, find out which channels are available and will receive all the needed information to attach to the BS. Two different types of spectrum measurement will be done by the CPE: in-band and outof-band. The in-band measurement consists in sensing the actual channel that is being used by the BS and CPE. The out-of-band measurement will consist in sensing the rest of the channels. The MAC layer will perform two different types of sensing in either inband or out-of-band measurements: fast sensing and fine sensing. Fast sensing will consist in sensing at speeds of under 1ms per channel. This sensing is performed by the CPE and the BS and the BS's will gather all the information and will decide if there is something new to be done. The fine sensing takes more time (aprox. 25 ms per channel or more) and it is utilized based on the outcome of the previous fast sensing mechanism. These sensing mechanisms are primarily used to identify is there is an incumbent transmitting, and if there is to avoid interfering with it. 66 IEEE 802 From Wikipedia, the free encyclopedia Jump to: navigation, search IEEE 802 refers to a family of IEEE standards dealing with local area networks and metropolitan area networks. More specifically, the IEEE 802 standards are restricted to networks carrying variable-size packets. (By contrast, in cell-based networks data is transmitted in short, uniformly sized units called cells. Isochronous networks, where data is transmitted as a steady stream of octets, or groups of octets, at regular time intervals, are also out of the scope of this standard.) The number 802 was simply the next free number IEEE could assign, though "802" is sometimes associated with the date the first meeting was held - February 1980. The services and protocols specified in IEEE 802 map to the lower two layers (Data Link and Physical) of the seven-layer OSI networking reference model. In fact, IEEE 802 splits the OSI Data Link Layer into two sub-layers named Logical Link Control (LLC) and Media Access Control, so that the layers can be listed like this: Data link layer o LLC Sublayer o MAC Sublayer Physical layer The IEEE 802 family of standards is maintained by the IEEE 802 LAN/MAN Standards Committee (LMSC). The most widely used standards are for the Ethernet family, Token Ring, Wireless LAN, Bridging and Virtual Bridged LANs. An individual Working Group provides the focus for each area. See its working groups: IEEE 802.1 Higher layer LAN protocols IEEE 802.2 Logical link control IEEE 802.3 Ethernet IEEE 802.4 Token bus (disbanded) IEEE 802.5 Token Ring IEEE 802.6 Metropolitan Area Networks (disbanded) IEEE 802.7 Broadband LAN using Coaxial Cable (disbanded) IEEE 802.8 Fiber Optic TAG (disbanded) IEEE 802.9 Integrated Services LAN (disbanded) IEEE 802.10 Interoperable LAN Security (disbanded) IEEE 802.11 Wireless LAN (Wi-Fi certification) IEEE 802.12 demand priority IEEE 802.13 (not used) IEEE 802.14 Cable modems (disbanded) IEEE 802.15 Wireless PAN o IEEE 802.15.1 (Bluetooth certification) o IEEE 802.15.4 (ZigBee certification) 67 IEEE 802.16 Broadband Wireless Access (WiMAX certification) o IEEE 802.16e (Mobile) Broadband Wireless Access IEEE 802.17 Resilient packet ring IEEE 802.18 Radio Regulatory TAG IEEE 802.19 Coexistence TAG IEEE 802.20 Mobile Broadband Wireless Access IEEE 802.21 Media Independent Handoff IEEE 802.22 Wireless Regional Area Network 68