ITEC 4720 Data Communication
advertisement

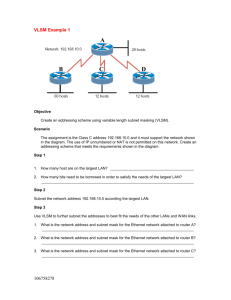
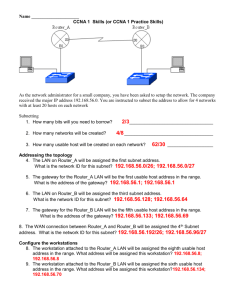
ITEC 3800 Data Communication Test 1 Name: Each multiple choice question is worth 2 points and each short essay question is worth 4 points. There is also a question of 5 extra points. In total there are 105 points. 1. The _____ layer keeps different applications’ data separate from other applications’ data. a. Session b. Data Link c. Network d. Transport 2. The _____ sublayer defines how data is packaged for the network. a. Physical b. LLC c. MAC d. Transport 3. _____ different classes of IP addresses exist on the Internet. a. 3 b. 4 c. 5 d. 6 4. Which layer is represented by frames? a. Session b. Data Link c. Network 5. Routers operate at the _____ layer of the OSI model a. physical b. data link c. network d. Transport d. transport 6. Which of the following are associated with the application layer of the OSI model? (choose two) a. ping b. Telnet c. FTP d. TCP e. IP 7. Your router receives a summary address of 192.168.176.0/21. What address range will your router forward based on this summary address? a. 192.168.0.1 192.168.255.254 b. 192.168.176.1 192.168.176.255 c. 192.168.176.1 192.168.191.254 d. 192.168.176.1 192.168.183.254 8. Well Known TCP Port _____ is for FTP data transfer. a. 20 b. 21 c. 22 d. 23 9. The _____ layer provides the encryption services when data encryption is used in network communications. a. Presentation b. Session c. Network d. Transport 10. Which subnet mask is the most efficient for point-to-point serial links when using VLSM? a. 255.255.255.0 b. 255.255.255.248 c. 255.255.255.252 d. 255.255.255.254 11. For what purpose is an administrative distance (AD) used? a. To administer a remote network b. To administer a remote router 1 c. To rate the trustworthiness of a remote network d. To rate the trustworthiness of routing information received on a router from a neighbor router 12. Segmentation and reassembly of data from the upper-layer applications occurs at what layer? a. Application b. Presentation c. Session d. Transport 13. Which command is used to manually encrypt passwords on a Cisco router? a. Router#service password-encryption b. Router(config)#service-password-encryption c. Router(config)#service password-encryption d. Router(config)#set password encrypt on 14. When data is encapsulated, which is the correct order? a. Data, frame, packet, segment, bit b. Segment, data, packet, frame, bit c. Data, segment, packet, frame, bit d. Data, segment, frame, packet, bit 15. What type of addresses do bridges use? a. MAC b. Logical c. IP d. TCP 16. The Host-to-Host layer of the DoD model maps to the _____ layer of the OSI reference model. a. Data Link b. Network c. Transport d. Session 17. Which of the following is a Class B broadcast? a. 11.255.255.255 b. 127.5.34.255 c. 174.34.255.255 d. 235.49.234.255 18. The _____ layer of the Cisco hierarchical model is responsible for routing. a. Internet b. Core c. Distribution d. Network 19. What type of RJ45 UTP cable is used between switches? a. Straight-through b. Crossover cable c. Rolled d. Twisted cable 20. What protocol is used to find the hardware address of a local device? a. RARP b. ARP c. IARP d. PARP 21. Which two of the following are private IP address? a. 12.0.0.1 b. 168.172.19.39 c. 172.20.14.36 d. 172.33.194.30 e. 192.168.24.43 22. What is the subnetwork address for a host with the IP address 200.10.5.68/28? a. 200.10.5.0 b. 200.10.5.16 c. 200.10.5.32 d. 200.10.5.64 23. You have an interface on a router with the IP address of 192.168.192.10/29. What is the broadcast address the hosts will use on this LAN? 2 a. 192.168.192.7 c. 192.168.192.127 b. 192.168.192.15 d. 192.168.192.255 c. 192.168.192.63 24. Which of the following command will configure all the default VTY ports on a router? a. Router#line vty 0 4 b. Router(config)#line vty 0 4 c. Router(config)# line console 0 4 d. Router(config)#line vty all 25. You have the following five networks on your router: 172.16.4.0/25, 172.16.4.128/25, 172.16.5.0/24, 172.16.6.0/24 and 172.16.7.0/24. What would be the best summary address you can configure on your router? a. 127.0.0.0/8 b. 172.16.0.0/16 c. 172.16.4.0/24 d. 172.16.4.0/22 26. Which of the following are methods of connection to a Cisco router? a. Console port b. Telnet c. Auxiliary port d. All of the above 27. When a router first powers up it will look for and load a valid configuration file from _______? a. ROM b. Flash Memory c. NVRAM d. DRAM 28. Which mode enables you to view and change the configuration of a Cisco router? a. Basic Management mode b. Extended Setup mode c. User mode d. Privileged mode 29. On what type of networks can default routing be used? a. Dynamic b. Static c. Stub d. Homogeneous 30. If you wanted to have 16 subnets with a Class C network ID, which subnet mask would you use? a. 255.255.255.252 b. 255.255.255.248 c. 255.255.255.240 d. 255.255.255.255 The objectives of this part of the exam are to test your understanding of subnetting and also the CIDR and bit-count notation used to express the subnet mask. In this part you will decode the IP address 126.46.255.255/14 and determine the subnet mask, the multiplier, the network number, and usuable subnetwork addresses and broadcast addresses. Determine the class of the network by examining the first octet of the network address given. 31. What are the network class and the default network mask? Please write the default network mask and the new subnet mask in decimal. Class A; Default mask: 255.0.0.0 New mask: 255.252.0.0 3 32. How many usable subnetworks can be created? How many usable hosts per subnetwork can be created? In this case, the number of borrowed bits is 6, so: 2^6 = 64 subnets In this case, the number of remaining bits is 18, therefore: 2^18 – 2 = 262144 – 2 = 262142 hosts 33. What is the multiplier (incremental number) for this subnetting? Since the new subnet mask written in binary is: 11111111.11111100.00000000.00000000 The last borrowed bit in the second octet is the sixth bit, so that the block size is 4 (256-252 = 4). 34. How many hosts were lost due to subnetting? (math equation is enough) 2^24 – 2 – 64 * 262142 = 16777214 - 16777088 = 126 hosts 35. Use the multiplier determined in Q33 to determine the first six usable subnetwork addresses. 126.0.0.0, 126.4.0.0, 126.8.0.0, 126.12.0.0, 126.16.0.0, 126.20.0.0 36. Determine the broadcast addresses on the usable subnetworks listed in last step. 126.3.255.255, 126.7.255.255, 126.11.255.255, 126.15.255.255, 126.19.255.255, 126.23.255.255, 37. What does the address 126.46.255.255 / 14 represent? On what network is this IP address? Host address 126.44.0.0 4 38. Starting from the user mode, how to set up the router name to be ITEC3800? Also please add a banner message “Welcome to LabConnection!” Please write all the commands starting from the user mode, and finally back to the user mode. Router> Ans: Router>en Router#config t Router(config)#hostname ITEC3800 ITEC3800(config)#banner motd # Welcome to LabConnection!# ITEC3800(config)#exit ITEC3800#disable 39. Starting from user mode, set the enable password to be “itec3800” and set the enable secret password to be “datacomm”, then remove them. Please write all the commands starting from the user mode, and finally back to the user mode. Router> Ans: Router>en Router#config t Router(config)#enable password itec3800 Router(config)#enable secret datacomm Router(config)#no enable password Router(config)#no enable secret Router(config)#exit Router#disable 40. Starting from user mode, setup E0 to be 219.101.110.1 with subnet mask 255.255.255.0. Router> Ans: Router>en Router#config t Router(config)#interface ethernet 0 Router(config-if)#ip address 219.101.110.1 255.255.255.0 5 Extra Points (5pts) 41. For the following two figures, do they have correct IP settings? If not, explain the reasons. Figure 1. Ans: 192.168.1.91/27 is not in the same subnet as the 192.168.1.100/27. 6 Figure 2. Ans: Correct. 7