UMKC Information Services Log Retention, Access, and
advertisement

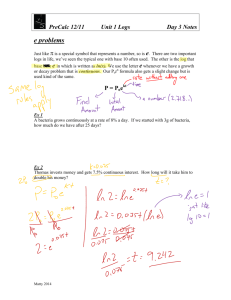
UMKC Information Services Log Retention and Authorization Practices UMKC Information Services handles several types of log files related to computer systems on the UMKC campus. These log files have varying authorized user lists, and varying retention times. This document will cover the majority of the log types, and the related access and retention. This document does not cover the activity of the distributed IT support personnel who are not employed by Information Services, and thus are not directly managed by Information Services. Individual departments may have different practices and policies for these decentralized staff members based on departmental needs. ---------------------------------------------------------------------------Computer Event Logs: Function: These particular log files exist on each local computer, and are not centralized. These logs record errors and low-level system functions on campus computer, program crashes, computer startup/shutdown, program installation, and hard drive pre-failure warnings. These logs are required to troubleshoot events that may otherwise require a computer to be completely rebuilt to overcome. Who has access: The computer user has access to these logs, as well as anyone else they have allowed to logon to their physical machine. Campus workstation administrators are authorized to use these logs to gather information to correct a problem reported by the user, or to gather other information as authorized by the user. It is anticipated that in the future a technology will exist to allow the collection of ‘severe events’ (such as disk pre-failure warnings), at which point workstation administrators will be authorized to access the troubleshooting and preventative maintenance portion of this data, in order to proactively help the user. Who gives permission to access: Campus information security workers are allowed additional access these logs to gather information in an open investigation as authorized by the CIO, or as authorized by the user. Future technology may allow collecting the hard drive pre-failure warnings, to ensure that workstation drives are replaced before failing. Lifespan of logs: These logs are retained on a machine indefinitely, up until a certain size limit is reached. Once this size limit is reached, old entries are automatically removed. Since this information is valuable for troubleshooting over a period of several months, these logs are generally not purged. Computer Logon and Startup Logs: Function: These logs record logon, logoff, startup, and shutdown of campus computers. These logs record information such as username, computer name, date/time, and computer metrics (such as speed, memory, and disk space free; these are items needed to know if the computer is at the point of replacement based on performance standards). Periodically additional non-personal troubleshooting information is collected, for example, to detect if automatic updates and similar automatic repair functions are working properly. Who has access: Campus workstation administrators have authorization to use this information to determine which machines are in need of replacement based on collected metrics, and to determine the owning department’s computer count based on matching up username and computer name. Campus workstation administrators have authorization to use this information while assisting a user, by looking up the current computer they are on based on last logon, so that they can offer remote assistance to the specific computer. The campus call center is authorized to access this information when assisting the user, by looking up the current computer they are on based on last logon, so that they can offer remote assistance to the specific computer. Who gives permission to access: Campus information security workers are authorized to use these logs to gather information in an open investigation as authorized by the CIO, or as authorized by the user. Either of the authorized groups may use the information in aggregate to collect statistical information, such as population of machines with a certain speed, or average percent of free space on machines. Either group is granted additional authorization to detect and submit for repair any machine failing to automatically update. Lifespan of logs: These logs are currently retained for 6 to 12 months for statistical trending. Email Logs: Function: There are two types of logs related to email systems. The first type are email transaction logs. The second type are web access logs, which will be discussed below under the section for web access log handling. The email transaction logs are valuable for determining traffic volume, and patterns of traffic flow. (i.e. heavy traffic from a specific foreign country may indicate an attempt to guess all of the email addresses in the system.) Who has access: Campus email administrators have authorization to these logs for troubleshooting, general statistics gathering. Additional access is granted upon request of a user, tracing of a lost sent or received message tied to the specific user (not upon request of a user asking about information on another user). Who gives permission to access: Campus information security workers have authorization to these logs to assist in backup of the Campus email administrators. Additional authorization is allowed for handling open investigations as authorized by the CIO. Lifespan of logs: These logs are currently retained for up to 6 months for statistical trending. Web Access Logs: Function: These logs record the address of machines connecting to campus web servers, and record the web file requested. These logs are very valuable in determining site usage patterns, traffic ratings for sites, and other usage-based patterns. These logs are also critical for tracking down missing/broken web pages, and tracking attempted attacks on the web server. Who has access: Electronic Communications Services (campus web master) is authorized to processes these logs on request of a department, for the department’s web pages. (This information is used to help the department understand the usage of their web site.) The web master is also authorized to processes general statistics to determine short-term and long term trends, most frequently visited pages, and similar statistical uses. Campus server administrators are authorized to use this information for troubleshooting, and detecting attacks on the campus web servers. Who gives permission to access: Campus information security workers are authorized to use this information when tracking attacks on the campus web servers. Additional authorization is allowed for handling open investigations as authorized by the CIO. Lifespan of logs: These logs are currently retained for 6 to 12 months for statistical trending. Network Attack Event Logs: Function: These logs record attacks and attempted attacks on the UMKC network. These logs are necessary to track down both current and past attack on the UMKC network. Long term logs are retained for both forensics, and statistical analysis to determine attack volume trends. These logs are not the same as short-term network flow logs, or network statistics logs which are statistically processed and the source log entry discarded. (Only statistical information is retained after processing.) Some short-term network flow logs are combined into the network attack log, only if the attack log processing server determines the information is critical to the recorded attack information. Who has access: Campus network administrators are authorized to access the network attack logs for all purposes. Since these logs only store attack type traffic, any information is considered unrelated to personal privacy, as attack traffic is unwanted traffic. Who gives permission to access: Campus information security workers are authorized to access to the network attack logs for all purposes. Since these logs only store attack type traffic, any information is considered unrelated to personal privacy, as attack traffic is unwanted traffic. Lifespan of logs: These logs are currently retained for up to 12 months for incident handling and statistical trending. Guest/Student Network Logon Logs: Function: These logs record the logon and logoff of accounts on the varying guest networks on campus. This includes the residence halls, wireless access, and plug-in points that require a logon. This does not include faculty/staff connections on campus. Who has access: Campus network administrators are authorized to access the network logon logs when assisting and troubleshooting logon and connection problems. Authorization is granted to use this information to disable a logon, when tracking down reports of network abuse, such as attacks on other Universities that are reported first to the network group, as opposed to the security group. Authorization is also granted for statistical analysis of this information. The campus call center is authorized to access this information when assisting the user with a logon and connection problem. Who gives permission to access: Campus information security workers are authorized to access this information to process reports of network abuse, such as peer to peer file sharing, and reported attacks from outside entities. Additional authorization is allowed for handling open investigations as authorized by the CIO. (This would be open investigations beyond simple network attacks.) Definitions: Campus workstation administrators: Includes all members of the Information Services Desktop Support team. This also includes members of the Server Support team as needed in assisting with desktop support and related requests from the user. This also includes members of the Information Services Security and Research group as needed in assisting with desktop support and related requests from the user. Campus server administrators: Includes all members of the Information Services Server Support team. This also includes members of the Information Services Security and Research group as needed in assisting with desktop support and related requests from the user. Campus email administrators: Includes those members of the Information Services Server Support team who are assigned to e-mail server management. This also includes members of the Networking voicemail support team, who need to have access necessary to the proper functioning of the e-mail-integrated voicemail system. This also includes members of the Information Services Security and Research group as needed in assisting with e-mail related support issues. Campus network administrators: Includes all members of the Information Services Networking team. This also includes members of the Information Services Security and Research group, both for assisting with networking issues as needed, and also for analyzing traffic patterns through automation to detect active attacks such as slow-probes of the campus, and distributed attacks against systems on campus. Campus information security workers: Includes all members of the Information Services Information Security and Research team.