5475 Syllabus
Tentative Syllabus
NORTH CAROLINA CENTRAL UNIVERSITY
SCHOOL OF LIBRARY AND INFORMATION SCIENCES
SLIS 4470OL1/5475: Communication Science
SEMESTER: Fall, 2010
COURSE TIME & LOCATION: Mondays. 6:00PM-8:30PM
INSTRUCTOR: Dr. Gabriel Peterson
TELEPHONE NUMBER: 919-530-6746
E-MAIL: gpeterson@nccu.edu
OFFICE: 323 Shepard Library
OFFICE HOURS: Mon. & Wed. 4PM-6PM. Call or e-mail anytime.
COURSE DESCRIPTION: Introduction to telecommunications concepts,
applications, and services. This class introduces the TCP/IP protocol suite
along with clients and servers for Internet communication, browsing, and
navigation. Examines policy, management, and implementation issues.
Student learning outcomes:
By the end of this course, students will be conversant with:
● Network architecture
● TCP/IP protocol suite and Internet architecture
● Browsing and navigation
● Policy and regulation in telecommunication systems
● Management and implementation
● Computer-Based Information Networks
● Protocols and Network Management
● Telecommunications Systems
● Network Security
COURSE REQUIREMENTS
The student will:
1. Read and interpret readings relating to each week’s topic.
2. Complete all assignments and exams. No late assignments will be
accepted without the instructor’s prior permission.
3. Demonstrate understanding and comfort with the subjects that undergird
the technical side of Information Science.
REQUIRED TEXTBOOKS
Principles of Computer Networks and Telecommunications
By: M. Barry Dumas, Morris Schwartz
Published 2009 by Pearson Prentice Hall Publishers
ISBN: 0-13-167264-9
EVALUATION
The final grade will be determined as follows:
1. Quizzes: 75%
2. Assignments: 10%
3. Final Exam: 15%
CLASS STRUCTURE
Each week, students will:
1. Read & be prepared to discuss the assigned material in class.
1. Complete all assignments & exams.
SLIS 4470/5470 Class Schedule:
Week of August 16: ONLINE: NO FACE TO FACE MEETING
Introduction to LSIS 5475
READING ASSIGNMENT #1: Dumas et al, Chapter 1
Assignment #1:
1a) Join the SLIS students Yahoo! group listserv.
1b) login to Blackboard, post alternate email, submit academic integrity
statement to Blackboard.
Week of August 23: Chapters 2 & 3
Week of August 30: Chapters 4 & 5
Week of September 6: Labor Day Holiday NO CLASS
Week of September 13: Quiz #1 NO CLASS
Week of September 20: Chapter 6 & 7
Week of September 27: Chapter 8 & 9
Week of October 4: Chapter 10
Week of October 11: Quiz #2 NO CLASS
Week of October 18: Chapters 11 & 12
Week of October 25: Chapters 13 & 14
Week of November 1: Quiz #3 NO CLASS
Week of November 8: Chapters 14 & 15
Week of November 15: Chapters 16 & 17
Week of November 22: Thanksgiving Break NO CLASS
Week of November 29: TBA
December 6: Final Exam Distributed
December 12: Final Exam Due NO EXCEPTIONS
ACADEMIC INTEGRITY:
I have a zero tolerance policy regarding academic dishonesty. If you represent
the work of another person as your own, you will receive a grade of 0 on the
entire assignment or exam in question. This policy applies to cheating and to
plagiarism, as defined in NCCU’s Academic Integrity Statement, found below
and at the following
URL:http://www.nccu.edu/academics/liberalarts/history/gradhandbook.cfm
Plagiarism is the unattributed use of another’s work and includes the
representation as your own of material copied from online sources, such as
the Wikipedia.
Cutting and pasting material from online resources is not acceptable behavior
at any academic level and will not be tolerated.
Because we use Blackboard, your work is done on your own and the
instructor depends on your honesty and integrity to do all the work assigned
alone (unless a team is designated). You are promising that you did the work
without assistance from another student and without assisting any other
student. You can use notes and textbooks, you can study with others, but you
must alone answer questions.
North Carolina Central University is dedicated to instilling in its students the
highest principles of integrity and responsibility. In this regard, students are
expected to demonstrate respect for these principles in the performance of
their academic activities. Academic dishonesty, which is a violation of
academic integrity, will be dealt with according to the provisions of the Student
Code of Academic Integrity.
Academic dishonesty is defined as any conduct which is intended by the
student to obtain for him/her or for others an unfair or false evaluation in
connection with any examination or other work for academic credit. Cheating,
fabrication, plagiarism, and complicity are examples of conduct which is
academically dishonest.
Cheating is the unauthorized use of materials in connection with an
examination or other work for academic credit, including, but not limited to (1)
the use of books, notes, outlines, etc. during an examination where the
instructor has not authorized use of such materials or information; (2)seeking
unauthorized materials or information from others in connection with an
examination; (3) giving or attempting to give unauthorized assistance to a
person in connection with an examination; (4) obtaining or attempting to
obtain unauthorized copies of examinations; (5) bringing to an examination, or
attempting to use during an examination, unauthorized answers which have
been prepared before the examination period; (6) copying or attempting to
copy from the work of another student during an examination; and (7)
submitting for evaluation in a course, part or the whole of a work for which
credit has been given previously.
Fabrication is the intentional invention, counterfeiting and/or alteration of
quotations, data, procedures, experiments, sources or other information for
which the student claims authorship in an exercise which he or she submits
with the expectation of receiving academic credit.
Plagiarism is the intentional use of the ideas, words, or work of another
without attribution, when the information they provide is not common
knowledge, either in content or form, and includes, but is not limited to (1)
quoting from the published or unpublished work of another without appropriate
attribution; (2) paraphrasing or summarizing in one’s own work any portion of
the published or unpublished materials of another without attribution; and (3)
borrowing from another’s work information which is not in the domain of
common knowledge.
Complicity is the intentional giving of assistance or the attempt to give
assistance to another for the purpose of perpetrating academic dishonesty.
Other Policies:
Student Support Services for Students with Disabilities
Students with disabilities (physical, psychological, learning disability, etc.) who
would like to request accommodations need to register with the Office of
Student Support Services in Suite G20 in the Student Services Building or by
contacting Kesha Lee, Director at (919)530-6325 or klee@nccu.edu. If you
are already registered in the office, you will need to return to the office each
semester to review your information and receive updated accommodations.
Incomplete grades:
The grade of "I" will be given only in unusual cases and must be resolved
within a time frame agreed upon by instructor and student prior to assignation
Late Assignments: Late homework will be penalized at the rate of 5 points
(half a letter grade) per day of lateness.
Late exams will be penalized at the rate of 10 points per day of lateness.
5141 Syllabus
Tentative Syllabus
NORTH CAROLINA CENTRAL UNIVERSITY
SCHOOL OF LIBRARY AND INFORMATION SCIENCES
SLIS 5451 Databases 1
SEMESTER: Fall, 2010
COURSE TIME & LOCATION: 6:00-8:30 W Shepard Library, Room 324
INSTRUCTOR: Dr. Gabriel Peterson
TELEPHONE NUMBER: 919-530-6746
E-MAIL: gpeterson@nccu.edu
OFFICE: 323 Shepard Library
OFFICE HOURS: Mon. & Wed 4PM-6PM. Call or e-mail anytime.
COURSE DESCRIPTION: Student learning outcomes:
LSIS 5451 is an introduction to databases. No prior understanding of database concepts or use is
assumed. Upon completing the course, students will be able to articulate fundamental concepts in
databases and demonstrate the ability to create, modify and query Microsoft Access databases.
COURSE REQUIREMENTS
The student will:
1. Read the chapter prior to class and participate in the lecture and demonstration.
2. Complete weekly assignments.
3. Show facility in creating, modifying and querying databases.
REQUIRED TEXTBOOKS
Database Concepts, 4e By Kroenke & Auer
Prentice Hall, 2010
ISBN-10: 0136086535
EVALUATION
The final grade will be determined as follows:
1. Assignments: 40%
2. Quizzes: 45%
3. Final Exam: 15%
CLASS STRUCTURE
Beginning with class #2, each student will:
1. Read & be prepared to discuss the assigned material in class.
1. Complete all assignments.
SLIS 5451 Class Schedule:
Week of August 18: Introduction to LSIS 5451 (ONLINE - No face to face meeting)
Review Syllabus, buy Textbook, install Microsoft Access 2007 (or Open Office Base)
Week of August 25: Chapter 1 & 2
Week of September 1: Chapter 3a
Week of September 7: Chapter 3b
Week of September 15: Quiz 1 NO CLASS
Week of September 22: Chapter 4
Week of September 29: Chapter 5
Week of October 6: Chapter 6
Week of October 12: Quiz 2 NO CLASS
Week of October 20: Chapter 7
Week of October 27: Chapter 8
Week of November 3: Quiz 3 NO CLASS
Week of November 10: Appendix B & Database Security
Week of November 17: Web Databases & MySQL
Week of November 24: Thanksgiving holiday – NO CLASS
Week of December 1: Wrap-up and review
Week of December 8: Final exam
December 12: Final Exam Due (NO EXCEPTIONS)
POLICIES:
ACADEMIC INTEGRITY:
I have a zero tolerance policy regarding academic dishonesty. If you represent the work of another
person as your own, you will receive a grade of 0 on the entire assignment or exam in question. This
policy applies to cheating and to plagiarism, as defined in NCCU’s Academic Integrity Statement, found
below and at the following URL:http://www.nccu.edu/academics/liberalarts/history/gradhandbook.cfm
Plagiarism is the unattributed use of another’s work and includes the representation as your own of
material copied from online sources, such as the Wikipedia.
Cutting and pasting material from online resources is not acceptable behavior at any academic level and
will not be tolerated.
Because we use Blackboard, your work is done on your own and the instructor depends on your honesty
and integrity to do all the work assigned alone (unless a team is designated). You are promising that you
did the work without assistance from another student and without assisting any other student. You can
use notes and textbooks, you can study with others, but you must alone answer questions.
North Carolina Central University is dedicated to instilling in its students the highest principles of integrity
and responsibility. In this regard, students are expected to demonstrate respect for these principles in the
performance of their academic activities. Academic dishonesty, which is a violation of academic integrity,
will be dealt with according to the provisions of the Student Code of Academic Integrity.
Academic dishonesty is defined as any conduct which is intended by the student to obtain for him/her or
for others an unfair or false evaluation in connection with any examination or other work for academic
credit. Cheating, fabrication, plagiarism, and complicity are examples of conduct which is academically
dishonest.
Cheating is the unauthorized use of materials in connection with an examination or other work for
academic credit, including, but not limited to (1) the use of books, notes, outlines, etc. during an
examination where the instructor has not authorized use of such materials or information; (2)seeking
unauthorized materials or information from others in connection with an examination; (3) giving or
attempting to give unauthorized assistance to a person in connection with an examination; (4) obtaining
or attempting to obtain unauthorized copies of examinations; (5) bringing to an examination, or attempting
to use during an examination, unauthorized answers which have been prepared before the examination
period; (6) copying or attempting to copy from the work of another student during an examination; and (7)
submitting for evaluation in a course, part or the whole of a work for which credit has been given
previously.
Fabrication is the intentional invention, counterfeiting and/or alteration of quotations, data, procedures,
experiments, sources or other information for which the student claims authorship in an exercise which he
or she submits with the expectation of receiving academic credit.
Plagiarism is the intentional use of the ideas, words, or work of another without attribution, when the
information they provide is not common knowledge, either in content or form, and includes, but is not
limited to (1) quoting from the published or unpublished work of another without appropriate attribution;
(2) paraphrasing or summarizing in one’s own work any portion of the published or unpublished materials
of another without attribution; and (3) borrowing from another’s work information which is not in the
domain of common knowledge.
Complicity is the intentional giving of assistance or the attempt to give assistance to another for the
purpose of perpetrating academic dishonesty.
Other Policies:
Student Support Services for Students with Disabilities
Students with disabilities (physical, psychological, learning disability, etc.) who would like to request
accommodations need to register with the Office of Student Support Services in Suite G20 in the Student
Services Building or by contacting Kesha Lee, Director at (919)530-6325 or klee@nccu.edu. If you are
already registered in the office, you will need to return to the office each semester to review your
information and receive updated accommodations.
Incomplete grades:
The grade of "I" will be given only in unusual cases and must be resolved within a time frame agreed
upon by instructor and student prior to assignation
Late Submissions: Late assignments will be penalized at the rate of 5 points (out of 100) per day. Late
exams will not be accepted.
5442 Syllabus
TENTATIVE SYLLABUS
NORTH CAROLINA CENTRAL UNIVERSITY
SCHOOL OF LIBRARY AND INFORMATION SCIENCES
COURSE: NETWORK SECURITY (LSIS 5442-01)
SEMESTER: Fall 2010
TIME & LOCATION:
MONDAYS, 6:00-8:30PM,
325 SHEPARD LIBRARY & OTHER LOCATIONS AS ANNOUNCED
INSTRUCTOR: DR. GABRIEL PETERSON
TELEPHONE NUMBER: (919) 530-4676
E-MAIL (Preferred): GPETERSON@NCCU.EDU
OFFICE HOURS: 4-6PM M-Tu. E-mail anytime.
COURSE DESCRIPTION: The principal concepts of network security will be
introduced. Topics such as cryptography, encryption, authentication, denial-ofservice attacks, worms, viruses, intrusion detection, firewalls, virtual private
network, Web security, and access control of the network systems.
STUDENT LEARNING OUTCOMES:
By the end of this course, students will understand threats to network security
and how to defend and harden systems and networks.
Upon completion of SLIS 5442, students will be able to demonstrate skills in
the analysis of security weaknesses in computer systems and in the defense
of such weaknesses. Students will gain practical experience in the defense of
networks and network equipment and be able to detail the primary areas of
network defense through the use of the program NMAP and others.
COURSE INTRODUCTION:
This course is intended to give students a practical introduction to the tools
and skills required of a network security analyst. Such tools are often
perceived by networks (and their administrators) as being security threats.
Hence, we will not be able to use all of the tools if we limit ourselves to
NCCU’s tightly secured network; we will need to find open networks where we
can work with the security tools available to network security analysts.
Network security tools used by professionals are typically UNIX or Linuxbased. We will use these tools. Thus, you will need to develop a working
knowledge of Linux. You must therefore start using Linux, either as an
installed operating system it as a live USB or CD CD.
I strongly recommend that you prepare a 4Gb (or larger) live USB drive.
Information about this process can be found
here: http://www.ubuntu.com/desktop/get-ubuntu/download
For more information about Ubuntu, please visit this
website: http://www.ubuntu.com/
COURSE REQUIREMENTS:
HARDWARE REQUIREMENTS:
IN ORDER TO USE THE TECHNOLOGY THAT UNDERPINS THIS CLASS
YOU MUST HAVE (AT THE MINIMUM)
* A LAPTOP EQUIPPED WITH WIRELESS INTERNET CAPABILITY
* A DISTRIBUTION OF LINUX INSTALLED OR AVAILABLE VIA LIVE BOOT
The student will:
Read and interpret selected material relating to each week’s topic.
Complete all assignments. No late assignments will be accepted without the
instructor’s knowledge.
Demonstrate increasing understanding and comfort with the subjects that
undergird of network security
TEXTBOOKS:
(*Note: I recommend getting some of these books at the local library. Some
are former bestsellers, so you should be able to find them for free or close to
it. All texts are available for sale used online. )
CompTIA Security + Study Guide
BY: Mike Pasture & Emmett Delaney
Wiley Publishing, Inc. (Skybox)
ISBN-10: 0470036680
ISBN-13: 978-0470036686
Cyber War: The Next Threat to National Security
by Richard A. Clarke, Robert Knake
ISBN-10: 0061962236
(*Note: I recommend getting this book at the local library. Its a current
bestseller, so you should be able to find it for free or close to it)
Secrets and Lies by Bruce Schneier
ISBN-10: 0471453803
Wiley Publishing, Inc.
Hacking Exposed: Network Security Secrets and Solutions, Sixth Edition
by Stuart McClure, Joel Scambray, and George Kurtz
Publisher: McGraw-Hill Osborne Media; 6 edition (January 5, 2009)
ISBN-10: 0071613749
The Art of Deception
by Kevin Mitnick
Publisher: Wiley
ISBN-10: 076454280X
Suggested Supplemental Readings:
The Code Book by R.Singh
The Linux Pocket Guide O’Reilly Publishers
Nmap Reference Guide - http://nmap.org/book/man.html
COURSE EVALUATION
Quizzes: 40%
Assignments: 30%
Final Exam: 30%
COURSE SCHEDULE
SLIS 5442OL1 Readings Schedule:
Week of August 18:
Prepare bootable Ubuntu USB drive or CD.
Begin reading Cyber War: The Next Threat to National Security by Richard A.
Clarke
Week of August 25:
Pasture & Delaney GENERAL SECURITY CONCEPTS (CHAPTERS 1 & 2)
HACKING EXPOSED CHAPTER 1 & 2 (Scanning & Footprinting)
Command line assignment distributed: (Ping, ifconfig, etc)
Week of September 1:
HACKING EXPOSED CHAPTER 3 - Enumeration
Pasture & Delaney INFRASTRUCTURE AND CONNECTIVITY (CHAPTER 3)
Work on Command line assignment: (Ping, ifconfig, etc)
Week of September 7:
Quiz 1 (Includes Clark, Pasture & Delaney & hacking exposed to Ch. 3)
Assignment Due: Command line assignment: (Ping, ifconfig, etc)
Week of September 15:
Pasture & Delaney MONITORING ACTIVITY AND INTRUSION DETECTION
(CHAPTER 4)
HACKING EXPOSED CHAPTER 4 - Hacking Windows
Week of September 22:
Pasture & Delaney IMPLEMENTING AND MAINTAINING A SECURE
NETWORK (CHAPTER 5)
HACKING EXPOSED CHAPTER 5 - Hacking UNIX
Week of September 29: Quiz 2
Week of October 6:
Pasture & Delaney SECURING THE NETWORK AND ENVIRONMENT
(CHAPTER 6)
HACKING EXPOSED (CHAPTER 6) - Remote Connectivity
Week of October 12:
HACKING EXPOSED Chapter 7 - Network Devices
Begin reading Secrets and Lies Schneier
Pasture & Delaney (CHAPTER 7) – CRYPTOGRAPHY
Week of October 20:
Pasture & Delaney (CHAPTER 8) - Policies & procedures
HACKING EXPOSED Chapter 8 - Wireless Hacking
NMAP assignment distributed
Week of October 27:
Pasture & Delaney (CHAPTER 9) - Security management
Security Management H ACKING EXPOSED Chapter 9 - Hacking Hardware
Week of November 3: Quiz 3
Week Of November 10:
HACKING EXPOSED Chapter 10 & 11 (Hacking Code & Web Hacking)
Pasture & Delaney - Appendix A
Week of November 17:
HACKING EXPOSED CHAPTER 12 - Hacking the Internet User
Finish Supplemental Readings: The Art of Deception by Kevin Mitnick
Week of November 24: Thanksgiving holiday – NO CLASS
Week of December 1: Quiz 4
Week of November 17:
NMAP Assignment Due
Week of December 8: Final exam
ACADEMIC INTEGRITY:
I have a zero tolerance policy regarding academic dishonesty. If you represent
the work of another person as your own, you will receive a grade of 0 on the
entire assignment or exam in question. This policy applies to cheating and to
plagiarism, as defined in NCCU’s Academic Integrity Statement, found below
and at the following
URL:http://www.nccu.edu/academics/liberalarts/history/gradhandbook.cfm
Plagiarism is the unattributed use of another’s work and includes the
representation as your own of material copied from online sources, such as
the Wikipedia.
Cutting and pasting material from online resources is not acceptable behavior
at any academic level and will not be tolerated.
Because we use Blackboard, your work is done on your own and the
instructor depends on your honesty and integrity to do all the work assigned
alone (unless a team is designated). You are promising that you did the work
without assistance from another student and without assisting any other
student. You can use notes and textbooks, you can study with others, but you
must alone answer questions.
North Carolina Central University is dedicated to instilling in its students the
highest principles of integrity and responsibility. In this regard, students are
expected to demonstrate respect for these principles in the performance of
their academic activities. Academic dishonesty, which is a violation of
academic integrity, will be dealt with according to the provisions of the Student
Code of Academic Integrity.
Academic dishonesty is defined as any conduct which is intended by the
student to obtain for him/her or for others an unfair or false evaluation in
connection with any examination or other work for academic credit. Cheating,
fabrication, plagiarism, and complicity are examples of conduct which is
academically dishonest.
Cheating is the unauthorized use of materials in connection with an
examination or other work for academic credit, including, but not limited to (1)
the use of books, notes, outlines, etc. during an examination where the
instructor has not authorized use of such materials or information; (2)seeking
unauthorized materials or information from others in connection with an
examination; (3) giving or attempting to give unauthorized assistance to a
person in connection with an examination; (4) obtaining or attempting to
obtain unauthorized copies of examinations; (5) bringing to an examination, or
attempting to use during an examination, unauthorized answers which have
been prepared before the examination period; (6) copying or attempting to
copy from the work of another student during an examination; and (7)
submitting for evaluation in a course, part or the whole of a work for which
credit has been given previously.
Fabrication is the intentional invention, counterfeiting and/or alteration of
quotations, data, procedures, experiments, sources or other information for
which the student claims authorship in an exercise which he or she submits
with the expectation of receiving academic credit.
Plagiarism is the intentional use of the ideas, words, or work of another
without attribution, when the information they provide is not common
knowledge, either in content or form, and includes, but is not limited to (1)
quoting from the published or unpublished work of another without appropriate
attribution; (2) paraphrasing or summarizing in one’s own work any portion of
the published or unpublished materials of another without attribution; and (3)
borrowing from another’s work information which is not in the domain of
common knowledge.
Complicity is the intentional giving of assistance or the attempt to give
assistance to another for the purpose of perpetrating academic dishonesty.
Other Policies:
ADA compliance: Please inform the instructor if you have special needs that
need to be accommodated; every effort will be made to accommodate
individuals with special needs.
Incomplete grades: The grade of "I" will be given only in unusual cases and
must be resolved within a time frame agreed upon by instructor and student
prior to assignation
Late Assignments: Late homework will be penalized at the rate of 5 points
(half a letter grade) per day of lateness.
Late exams will be penalized at the rate of 10 points per day of lateness.
TENTATIVE Syllabus for LSIS 5110 Information Policy
Summer 2010
North Carolina Central University
School of Library and Information Sciences
COURSE: Information Policy (LSIS 5110-D)
SEMESTER: Summer Session 1 2010 – May 21-June 25
TIME & LOCATION: Online
INSTRUCTOR: Dr. Gabriel Peterson
TELEPHONE NUMBER: (919) 530-6746
E-MAIL: gpeterson@nccu.edu
OFFICE HOURS: By appointment. Call or e-mail anytime.
COURSE INTRODUCTION: The course will examine information policies, particularly at
the federal and international levels with special emphasis on cyber-warfare and the US's
current posture regarding that issue. Other issues of interest include policy issues such
as net neutrality and personal rights.
COURSE DESCRIPTION: Matching information systems policy to the information
needs of an organization, and investigating issues relating to management and
administration of the information systems functions.
STUDENT LEARNING OUTCOMES: Upon completing LSIS 5110, students will be able
to articulate the need for and practices of implementation of Information Policy in
diverse organizations.
COURSE REQUIREMENTS: The student will read and interpret selected material
relating to each week’s topic and complete all assignments. No late assignments will be
accepted without the instructor’s prior approval.
BLACKBOARD & CLASS COMMUNICATION: All class interactions will occur on
Blackboard and via nccu.edu email. You should check both Blackboard and your
NCCU email daily. Assignments can be submitted via the Digital Dropbox in .doc or .rtf
format. All class communication will be mediated via the discussion board so that all
information can be shared universally. Further, because campus email employs an
aggressive spam filter, email sent to my nccu.edu account may not arrive in a timely
manner. Thus, PLEASE POST ANY CLASS RELATED QUESTIONS TO THE “DR.
PETERSON'S OFFICE” FORUM ON BLACKBOARD
REQUIRED TEXTS :
Cyber War: The Next Threat to National Security and What to Do About It
By Richard Clarke ISBN-10: 0061962236
Inside Cyber Warfare: Mapping the Cyber Underworld
By Jeffrey Carr ISBN-10: 0596802153
Note: Start reading these books as soon as you get them so that you will be able
to discuss them in a few weeks
Grading criteria:
Class participation: 20%
Final: 20% (Due June 25)
Critical reviews: 60%
Critical reviews: Students will prepare critical reviews based on the readings and class
discussions. Critical reviews will be prepared for each of the 4 major subject areas:
Due May 30: Information Policy in Organizations – Introduction to policy issues
Due June 6: US-Domestic Information Policy – Net Neutrality & Spectrum Regulation
Due June 13: US-International Information Policy – National Security & Cyber-war
Due June 20: Information Policy and the Individual – Privacy, censorship & the open
society
Critical reviews will consist of an analysis of course material with special attention given
to discussion topics outlined week-by-week. Reviews should be thorough,
grammatically correct and properly cited. (Secondary and tertiary online sources such
as Google, Wikipedia, or Slashdot are not acceptable source material for academic
work). I will not give you a word maximum or minimum, just do a complete and thorough
job, and remember that your work will be graded on a curve, in comparison to that of
your peers, so do your best.
I have a zero tolerance policy for plagiarism, (the unattributed use of
another's work as your own). Plagiarism will result in the receipt of a
zero for an assignment for a first offense and a second offense will
result in ejection from the MIS program. See the end of the syllabus
for details.
Course schedule/calendar:
Week 1: May 21 - Introduction to Information Policy:
Readings: Rubin, Ch 4 (pdf available on Blackboard)
Read: US Government Information Policy by Varian and Shapiro:
http://people.ischool.berkeley.edu/~hal/Papers/policy/policy.html
“Analysis of The Telecommunications Act of 1996”
http://www.oswego.edu/~messere/telcom1.html
Begin reading the Cyber-war texts
Critical Review #1 (Due May 30): Information Policy in Organizations – Introduction to
policy issues
Discussion questions:
What areas must an information policy for an organization encompass?
What are the information policies of your employer?
What are your personal information policies?
Week 2: May 28 – Federal Information Policy US-Domestic Information Policy – Net Neutrality & Spectrum Regulation
Readings: The "New economy" and Information Technology Policy by Pamela
Samuelson &
Hal Varian available at:
http://people.ischool.berkeley.edu/~pam/papers/infopolicy
Network Neutrality, Broadband Discrimination
Journal of Telecommunications and High Technology Law, Vol. 2, p. 141, 2003
by Tim Wu
(available from:
http://papers.ssrn.com/sol3/cf_dev/AbsByAuth.cfm?per_id=159088)
Critical Review #2 (Due June 6): US-Domestic Information Policy – Net Neutrality &
Spectrum Regulation
Discussion questions:
What are the challenges regulators face when dealing with technological
innovation?
Net neutrality is a hotly contested subject at the moment with various industry
and consumer groups vying to shape public policy to their liking.
What is net neutrality?
How is net neutrality defined by the parties involved?
What is the current regulatory posture of the US government regarding net
neutrality?
Weeks 3 & 4: June 4 - 11 – US-International Information Policy
Reading assignment:
Cyber War: The Next Threat to National Security and What to Do About It
By Richard Clarke ISBN-10: 0061962236
Inside Cyber Warfare: Mapping the Cyber Underworld
By Jeffrey Carr ISBN-10: 0596802153
Critical Review #3 (Week of June 13): US-International Information Policy – National
Security & Cyber-war
Discussion questions:
What are the primary threats identified by the Cyber-War texts you have read?
What is the US policy towards each of these threats?
What transnational information flow issues confront the US?
What transnational information flow issues confront the global Internet
community?
Week 5: June 14 – Information Policy and the Individual – Privacy, censorship &
the open society
Reading assignment:
http://www.schneier.com/blog/archives/2006/05/the_value_of_pr.html
FURTHER READINGS TO BE ASSIGNED
Critical Review #4 (Due June 20): Information Policy and the Individual – Privacy,
censorship & the open society
Discussion questions:
What is privacy?
What is the nature of privacy on the Internet from an engineering perspective?
What is the nature of privacy on the Internet from a business perspective?
What is the nature of privacy on the Internet from a personal perspective?
Week 6: June 25 – Final exam due
POLICIES:
ACADEMIC INTEGRITY:
I have a zero tolerance policy regarding academic dishonesty. If you represent the
work of another person as your own, you will receive a grade of 0 on the entire
assignment or exam in question. This policy applies to cheating and to plagiarism, as
defined in NCCU’s Academic Integrity Statement, found below and at the following
URL: http://www.nccu.edu/academics/liberalarts/history/gradhandbook.cfm
Plagiarism is the unattributed use of another’s work and includes the representation as
your own of material copied from online sources, such as the Wikipedia.
Cutting and pasting material from online resources is not acceptable behavior at any
academic level and will not be tolerated.
Because we use Blackboard, your work is done on your own and the instructor
depends on your honesty and integrity to do all the work assigned alone (unless a
team is designated). You are promising that you did the work without assistance from
another student and without assisting any other student. You can use notes and
textbooks, you can study with others, but you must alone answer questions.
North Carolina Central University is dedicated to instilling in its students the highest
principles of integrity and responsibility. In this regard, students are expected to
demonstrate respect for these principles in the performance of their academic
activities. Academic dishonesty, which is a violation of academic integrity, will be dealt
with according to the provisions of the Student Code of Academic Integrity.
Academic dishonesty is defined as any conduct which is intended by the student to
obtain for him/her or for others an unfair or false evaluation in connection with any
examination or other work for academic credit. Cheating, fabrication, plagiarism, and
complicity are examples of conduct which is academically dishonest.
Cheating is the unauthorized use of materials in connection with an examination or
other work for academic credit, including, but not limited to (1) the use of books, notes,
outlines, etc. during an examination where the instructor has not authorized use of
such materials or information; (2)seeking unauthorized materials or information from
others in connection with an examination; (3) giving or attempting to give unauthorized
assistance to a person in connection with an examination; (4) obtaining or attempting
to obtain unauthorized copies of examinations; (5) bringing to an examination, or
attempting to use during an examination, unauthorized answers which have been
prepared before the examination period; (6) copying or attempting to copy from the
work of another student during an examination; and (7) submitting for evaluation in a
course, part or the whole of a work for which credit has been given previously.
Fabrication is the intentional invention, counterfeiting and/or alteration of quotations,
data, procedures, experiments, sources or other information for which the student
claims authorship in an exercise which he or she submits with the expectation of
receiving academic credit.
Plagiarism is the intentional use of the ideas, words, or work of another without
attribution, when the information they provide is not common knowledge, either in
content or form, and includes, but is not limited to (1) quoting from the published or
unpublished work of another without appropriate attribution; (2) paraphrasing or
summarizing in one’s own work any portion of the published or unpublished materials
of another without attribution; and (3) borrowing from another’s work information which
is not in the domain of common knowledge.
Complicity is the intentional giving of assistance or the attempt to give assistance to
another for the purpose of perpetrating academic dishonesty.
Other Policies:
Student Support Services for Students with Disabilities
Students with disabilities (physical, psychological, learning disability, etc.) who would
like to request accommodations need to register with the Office of Student Support
Services in Suite G20 in the Student Services Building or by contacting Kesha Lee,
Director at (919)530-6325 or klee@nccu.edu. If you are already registered in the
office, you will need to return to the office each semester to review your information
and receive updated accommodations.
Incomplete grades:
The grade of "I" will be given only in unusual cases and must be resolved within a time
frame agreed upon by instructor and student prior to assignation
Late Assignments: Late homework will be penalized at the rate of 5 points (half a letter
grade) per day of lateness.
Late exams will be penalized at the rate of 10 points per day of lateness.
Academic Integrity Policy:
Plagiarism, fabrication and cheating, (including the representation of material copied
from online sources such as Wikipedia.org) are not acceptable academic
behaviors. Such behavior on any assigned class activity will result in the receipt of a
grade of 0 for the entire assignment or exam.
Affirmation:
I have read, understand, and accept the academic integrity policy for this course.
Name (Print):_____________________________
Signature:________________________________
North Carolina Central University
School of Library and Information Science
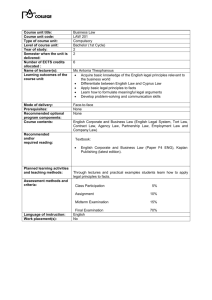
LSIS 5115-01D: Intellectual Property
Semester: Spring 2009
LOCATION: Tuesdays, 6:00-8:30PM 325 Shepard Library
Instructor: Dr. Peterson
email: gpeterson@nccu.edu
Phone: 919-530-6746
Office hours: By appointment
Course Information
COURSE DESCRIPTION: This course provides a basic understanding of how
copyright, patent and trademark law impact technology and individuals. It
considers legal theory and IT concepts as applied through business system
models to specific patent and copyright issues in workforce situations within
the context of Internet data communications.
STUDENT LEARNING OUTCOMES: Upon completing LSIS 5115, students will
demonstrate understanding of the role of intellectual property issues in
information science and will complete a critical reviews regarding aspects of
the rights of the individual or the academy in the use of intellectual property.
Course Requirements
REQUIRED TEXTS :
Intellectual Property: The Law of Copyrights, Patents and Trademarks by Roger E.
Schechter and John R. Thomas ISBN-10:0314065997
Copyright Law for Librarians And Educators: Creative Strategies And
Practical Solutions by Kenneth CrewsISBN-10: 083890906X
SUPPLEMENTAL TEXTS
Bound By Law? (Tales from the Public Domain) by Aoki,
Boyle, Jenkins Available for free
from:http://www.law.duke.edu/cspd/comics/pdf/cspdcomichigh.pdf
Free Culture: The Nature and Future of Creativity by Lawrence Lessig
Available for free from: http://www.free-culture.cc/freeculture.pdf
Essentials of Intellectual Property by Poltorak ISBN-10: 0471432334
Class points & grading criteria:
Class participation & Online forums - 10%
3 Critical reviews - 10% each
3 Database exercises - 10% each
Midterm exam 15%
Final exam 15%
Course Overview:
MODULE 1: Introduction to Intellectual Property
Definitions of Information technology and intellectual property
The economic & legal issues of Intellectual Property - What it is for, how it
is used
The past, present and future of Intellectual Property and IP law
International issues
MODULE 2: Copyright
Purpose of copyright, who and what copyright law protects
Limits of copyright
Copyright databases
Copyright infringement & remedies
The role of technology in copyright law - Sharing, piracy and backups
Fair use and the rights of the individual
The Creative Commons
The US Code
MODULE 3: Patents
The purpose of patent law, who and what patent law protects
Duration of patents
Obtaining a patent
Patent infringement & remedies
Software patents and the role of technology in patent law
Patent databases
MODULE 4: Trademarks
The purpose of trademark law, who and what trademark law protects
Obtaining a Trademark
Trademark infringement & remedies
The role of technology in trademark law
Trademark databases
Course schedule/calendar:
Week of January 13: Module 1: Introduction to Intellectual Property:
Introduction to IP
Readings: http://www.copyright.iupui.edu/IPPrimer.pdf
Week of January 20:
Module 1, Part 1
Readings: Jolly Ch. 1-3, Schechter & Thomas Ch1
TOPICS: Introduction to IP: History, types of IP, alternatives
Online forum
Week of January 27:
Module 1, Part 2
Jolly Ch 4-8
Week of February 3: Module 2: Copyright
Critical Review #1 (Introduction to IP) Due
Readings: Hornbook: Ch. 2-5
Bound By Law
Online Forum
Week of February 10, 2008:
Readings: Hornbook: Ch. 6-8, Kenneth Crewes
TOPICS: Copyright law, rights, products covered by copyright, duration of
protection, US Code Article 17, WIPO
Weeks of February 17 (Online) & February 24:
Readings: Hornbook Ch. 9 & 10, Kenneth Crewes
TOPICS: Research Paper topic selection, Infringement & the DMCA, First
sale, Fair Use & Other exceptions, Libraries & the ALA, Digital Libraries, the
future of libraries, The RIAA & the MPAA, Lessig, EFF, International Issues
Week of March 3: Copyright & the Internet & the future:
Readings: Lawrence Lessig
TOPICS: Searching copyright Databases, mashups & allowable uses,
copyright in cyberspace.
Assignment: Copyright databases
Week of March 10:
Fall Break – No Class
Week of March 17:
Midterm
Critical review #2 (Copyright) Due
Week of March 24: Module 3: Patents
Readings: Schecter & Thomas Ch 13 -17
TOPICS: Types & requirements, duration & rights, software patents – EFF
Week of March 31:
Readings: Schecter & Thomas Ch 20-23
TOPICS: Rights, registration & patent searching, International Aspects
Assignment: Patent Databases
Online Forum
Week of April 7:
Critical Review #3 (Patents) Due
Weeks of April 14 & 21: Module 4, Trademark, Trade Secret & other
protections
Readings: Hornbook Ch 24-28
TOPICS: Infringement & Defenses, Registration & licensing & the USPTO,
Database searching & Image retrieval
Assignment: Trademark databases
Week of April 28
Class review
Final exam distributed
Week of May 5 – Final Exam Due
POLICIES:
ADA compliance: Please inform the instructor if you have special needs that
need to be accommodated; every effort will be made to accommodate
individuals with special needs
INCOMPLETES: The University has a policy of allowing a student to receive a
grade of Incomplete one time for a given class. If the student wishes, they
may opt to re-take the class at a later time, but they have only one chance
to do so; thus it is imperative that the student finish the course on the
second attempt. This is particularly the case with Core Courses, with which
2 incomplete grades will result in being removed from the program. The
department strongly encourages you to avoid any Incompletes if at all
possible.
LATE HOMEWORK: Late homework will be penalized at the rate of 5 points
(half a letter grade) per day of lateness.
ACADEMIC INTEGRITY: Because we use Blackboard, your work is done on
your own and the instructor depends on your honesty and integrity to do all
the work assigned alone (unless a team is designated). You are promising
that you did the work without assistance from another student and without
assisting any other student. You can use notes and textbooks, you can study
with others, but you must alone answer questions.
Any violations will require a meeting with senior faculty and/or the Dean of
the SLIS. The imposition of the penalty for academic dishonesty shall be
made by the instructor responsible for assigning the final grade in the
course. The penalty will be assessed in relation to the gravity of the offense,
the type of academic exercise on which the offense occurred, and the weight
of that exercise in the computation of the final grade. The following excerpt
from the NC Central University catalogue covers the honor code applied in
this course:
North Carolina Central University is dedicated to instilling in its students the
highest principles of integrity and responsibility. In this regard, students are
expected to demonstrate respect for these principles in the performance of
their academic activities. Academic dishonesty, which is a violation of
academic integrity, will be dealt with according to the provisions of the
Student Code of Academic Integrity.
Academic dishonesty is defined as any conduct which is intended by the
student to obtain for him/her or for others an unfair or false evaluation in
connection with any examination or other work for academic credit.
Cheating, fabrication, plagiarism, and complicity are examples of conduct
which is academically dishonest.
Cheating is the unauthorized use of materials in connection with an
examination or other work for academic credit, including, but not limited to
(1) the use of books, notes, outlines, etc. during an examination where the
instructor has not authorized use of such materials or information;
(2)seeking unauthorized materials or information from others in connection
with an examination; (3) giving or attempting to give unauthorized
assistance to a person in connection with an examination; (4) obtaining or
attempting to obtain unauthorized copies of examinations; (5) bringing to an
examination, or attempting to use during an examination, unauthorized
answers which have been prepared before the examination period; (6)
copying or attempting to copy from the work of another student during an
examination; and (7) submitting for evaluation in a course, part or the whole
of a work for which credit has been given previously.
Fabrication is the intentional invention, counterfeiting and/or alteration of
quotations, data, procedures, experiments, sources or other information for
which the student claims authorship in an exercise which he or she submits
with the expectation of receiving academic credit.
Plagiarism is the intentional use of the ideas, words, or work of
another without attribution, when the information they provide is not
common knowledge, either in content or form, and includes, but is not
limited to (1) quoting from the published or unpublished work of another
without appropriate attribution; (2) paraphrasing or summarizing in one’s
own work any portion of the published or unpublished materials of another
without attribution; and (3) borrowing from another’s work information
which is not in the domain of common knowledge.
Complicity is the intentional giving of assistance or the attempt to give
assistance to another for the purpose of perpetrating academic dishonesty.
For further information please consult: http://nccuslis.org/faq/faqgrades.php#plagiarism