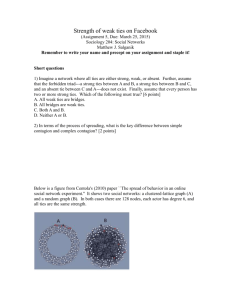
Relationally-Embedded Network Ties
advertisement

Patterns of Multidimensionality of Embedded Network Ties: A Typology of Relational Embeddedness in Emerging Entrepreneurial Firms Published in Strategic Organization! February 2003 - 1(1) Julie M. Hite Brigham Young University 310 MCKB Provo, UT 84602 Email: julie_hite@byu.edu Tel: 801-378-5039 FAX: 801-378-7740 **The author would like to thank William S. Hesterly, Jeffrey H. Dyer, Karin Fladmoe-Lindquist, Janeen Costa, Lee T. Perry, Cliff Mayes, Steven J. Hite, Anu Phene, Kirk Wessel, Lene Foss, Vance E. Randall and Sharon Black, as well as the editors and anonymous reviewers, for their helpful comments and suggestions on earlier drafts of this paper. 2 Patterns of Multidimensionality of Embedded Network Ties: A Typology of Relational Embeddedness in Emerging Entrepreneurial Firms ABSTRACT Assuming heterogeneity among relationally-embedded ties, this study focuses on classification of relationally-embedded ties. Network ties embedded within social relationships influence economic actions and represent a strategic form of organizing for emerging entrepreneurial firms. Research questions include the following: (1) What are the components of the social relationships of relationally-embedded ties? (2) How can relationally-embedded network ties be classified to identify different types of embeddedness based on variations in the social relationships? (3) What strategic implications can be drawn from a multidimensional view of relational embeddedness? This study uses case study methods to examine external network ties of eight emerging firms in the computer industry. A classification typology of seven types of relational-embeddedness emerge based upon combinations of three overarching social components--personal relationship, dyadic economic interaction, and social capital. The typology suggests multidimensionality of both embeddedness type and intensity. Propositions address strategic outcomes of heterogeneity within relational embeddedness. KEYWORDS: Networks, Embeddedness, Entrepreneurship Patterns of Multidimensionality of Embedded Network Ties: A Typology of Relational Embeddedness in Emerging Entrepreneurial Firms Emerging entrepreneurial firms face the central challenge of strategically organizing to obtain resources critical for firm survival and economic performance (Barney, 1991; Dierickx & Cool, 1989; Peteraf, 1993; Wernerfelt, 1995). Typically, these emerging firms are internally resource poor (Jarillo, 1989; Romanelli, 1989; Siegel, Siegel, & MacMillan, 1993), having insufficient internal resources to sustain firm survival and growth due to liabilities of both newness and smallness (Baum, 1996). In order to ensure their survival, emerging firms must find ways to gain access to external resources (Aldrich & Zimmer, 1986). Usually such firms find these external resources within their social network of external dyadic ties (Gnyawali & Madhavan, 2001; Jarillo, 1989; Larson & Starr, 1993). As a result, dyadic network ties of the emerging entrepreneurial firm are often embedded within social relationships. These relationally- embedded network ties represent a critical issue for the strategic organization of emerging firms, particularly given their potential to influence resource acquisition, governance, economic efficiency and, ultimately, firm performance. Yet as social relationships differ, the relationally-embedded network ties that are built upon these social relationships may also differ. While research has identified various characteristics of embedded network ties (e.g. Granovetter, 1982; Uzzi, 1996), a classification framework has not yet been developed for relational embeddedness. The variation within relational embeddedness has been limited to its general representation as a dichotomous construct: that is, a network tie is considered to be either relationally embedded or not. As a result, relationally-embedded ties currently represent a homogenous set of network relationships. However, a critical strategic problem for emerging entrepreneurial firms is that this assumption of homogeneity may lead to ineffective or inefficient homogeneity of resource acquisition strategies and governance mechanisms. If, however, variety exists within relationally-embedded ties, then a broader range 2 of resource and governance strategies may be necessary. Thus the issue to be considered is how relationally-embedded ties are similar to or different from each other, given that the potential differences may have critical strategic implications for the successful emergence of the firm. In response to recent calls for research on qualities of embeddedness, as well as network governance and the relational view of the firm (Dyer & Singh, 1999; Madhok, 1997; Rowley, Behrens, & Krackhardt, 1999; Uzzi, 1996), this study examines the social relationships of relationally-embedded network ties. This research addresses the need for further clarifying and classifying the qualities of relational-embeddedness and, therefore, continues the agenda of unpacking the theoretical construct of embeddedness (McKelvey & Aldrich, 1983; Uzzi, 1996). As emerging firms rely so heavily upon relationally-embedded network ties (Larson & Starr, 1993), this study examines these ties within emerging entrepreneurial firms in the computer industry. Built upon qualitative and case study methods, this research suggests the multidimensionality of relational embeddedness and explores variation in both type and intensity of embeddedness. As a result, a theoretical groundwork is laid for the development of embeddedness measures, thus enabling the future pursuit of network embeddedness within a richer context. The paper will first briefly discuss relationally-embedded network ties and then describe the research methods. The section on findings will describe the social components of relationally-embedded network ties and present a classification typology of types and intensities of relational-embeddedness, based on the various combinations of these social components. Finally, the paper will discuss these findings and suggest directions for future research. Relationally-Embedded Network Ties The recognition of network ties as a viable strategic context for organizational transactions, as an alternative to traditional market and hierarchical ties, has attracted attention to the study of 3 networks and network relationships in strategic organizing (Borch & Arthur, 1995; Dyer & Singh, 1998; Hennart, 1993; Powell, 1987, 1990). For emerging entrepreneurial firms that are characteristically internally resource poor (Jarillo, 1989; Romanelli, 1989; Siegel et al., 1993), external relationally-embedded network ties provide critical strategic avenues for obtaining necessary external resources and establishing conduits for reciprocal patterns of communication and exchange (Hite & Hesterly, 2001). These relationally-embedded ties facilitate resource exchange for the emerging firm as it borrows, leverages, influences, and controls resources that it does not currently own (Hite & Hesterly, 2001; Jarillo, 1989). Thus relationally-embedded ties facilitate the strategic organization and positioning of an emerging firm to acquire external resources needed for successful emergence and performance (Jarillo, 1989).1 The literature of relational embeddedness2 suggests that these ties generally influence two strategic outcomes: (a) ties are embedded within a social relationship that influences the economic actions of the firm (Granovetter, 1985, 1992; Hansen, 1995; Larson & Starr, 1993; Uzzi, 1996, 1997); and (b) ties are governed more through mechanisms of trust and relational contracting than through traditional market governance (Dyer & Singh, 1998; Granovetter, 1985; Macaulay, 1963; Powell, 1990; Uzzi, 1996, 1997). Relational embeddedness highlights the critical strategic role played by personal relationships in economic exchange (Zaheer & Venkataraman, 1995). Given that resource exchanges often reside within a social context that may influence the attributes of transactions (Williamson, 1994), “an exclusive focus on the transaction--rather than the relationship--as the primary unit of analysis is misplaced” (Powell & Smith-Doerr, 1994, p. 323). Indeed, evidence is mounting that “human action is affected by the social relations within which actors are embedded" (Mizruchi, 1994, p. 339) such that “sociologists now take as axiomatic the proposition that economic action, including entrepreneurial behavior, is embedded in interpersonal social networks” (Staber & Aldrich, 1995, p. 442). 4 Thus relationally-embedded network ties contribute to a viable form of strategic organization and can facilitate or hinder the successful emergence, survival and growth of the emerging firm (Borch & Arthur, 1995; Hite & Hesterly, 2001; Larson, 1992; Powell, 1990; Rowley, Behrens, & Krackhardt, 2000; Saxenian, 1990). Relationally-embedded network ties influence the competitive actions of the emerging firm both positively and negatively by providing both opportunities and constraints (Granovetter, 1985; Uzzi, 1996). These ties provide critical opportunities and resources to the emerging firm that would otherwise be unavailable through more traditional market exchange (Portes & Sensenbrenner, 1993; Starr & MacMillan, 1990). Yet an emerging firm may maximize social relationships over economic efficiency or other strategic considerations (Dubini & Aldrich, 1991; Granovetter, 1985; Uzzi, 1996). This shift of focus toward non-economic, relational criteria limits or constrains the emerging firm’s strategic autonomy and thus its emergence and future performance (Curran, Jarvis, Blackburn, & Black, 1993; Portes & Sensenbrenner, 1993). Indeed, emerging firms with relationally-embedded ties, "far from being atomistic entities free to undertake any competitive action within their own resource constraints, are embedded in a network of relationships that influences their competitive behavior" (Gnyawali & Madhavan, 2001, p. 431). For example, exchange across relationally-embedded ties may incur social obligations and expectations beyond the scope of an arm’s-length relationship (Coleman, 1988; Portes & Sensenbrenner, 1993). Thus for an emerging firm, advantages of relationally- embedded ties may often be countered by constraints or disadvantages of these network relations (Burt, 1982; Krackhardt, 1995; Portes & Sensenbrenner, 1993; Powell, 1990; Zhao & Aram, 1995). Successful firm emergence depends upon maximizing the value of both the economic and social exchange within these relationally-embedded network ties (Hansen, 1995; Larson & Starr, 1993; Macneil, 1978; Zaheer & Venkataraman, 1995). Maximizing the value of 5 relationally-embedded ties requires increasing the benefits while minimizing costs of this complex exchange relationship (Madhok, 1997). The critical issue that arises then is why and how relationally-embedded ties can create differential advantages and disadvantages. This question suggests that variation in outcomes may be influenced by variation among the relationally-embedded ties themselves. Given that relationally-embedded network ties operate with more idiosyncratic exchange relationships than do arm’s length market relationships (Dyer & Singh, 1998), the unique nature of the social relationships within relationally-embedded ties may help explain the variation in outcomes. Consideration of the nature of relational embeddedness suggests that characteristics and patterns of social relationships between actors influence the context within which economic exchange occurs (Granovetter, 1985; Uzzi, 1996). Granovetter (1985), therefore, suggests the need to “pay attention to patterns of personal relations by which economic transactions are carried out” (p. 504). Thus as the social relationships in which these ties are embedded differ, the exchange within and governance of these relationally-embedded ties may also be expected to differ and generate differential outcomes. A critical issue, therefore, in the development of theory concerning the strategic organization of emerging firms is to classify the characteristics and patterns of variation in the social relationships within which these critical network ties are embedded (McKelvey & Aldrich, 1983; Rowley et al., 1999; Weick, 1979). Perception of the variation in nature and strategic characteristics of network ties was initially grounded in a dichotomous differentiation between the nature of weak and strong network ties (Granovetter, 1973, 1982). Strong network ties, characterized as having high levels of social relationship or personal interaction, demonstrate high frequency, reciprocity, and affect/philos (Granovetter, 1982; Krackhardt, 1992). As a result, these strong ties carry greater motivation to 6 be of assistance and to be more easily available, as well as greater likelihood to be useful in terms of protection and reduction of uncertainty for actors in insecure positions—a valuable asset for an emerging firm (Hite & Hesterly, 2001). In contrast, weak ties, which are not as heavily based on the social relationship or personal interaction between actors, entail lower frequency, reciprocity, and affect/philos; yet they may provide strategic advantages in terms of resource availability beyond the firm’s egocentric network (Granovetter, 1973, 1982; Gregersen & Black, 1992; Hite & Hesterly, 2001). Network ties were characterized at these extremes and labeled, for example, as “friends, acquaintances, strangers” (Aldrich, Elam, & Reese, 1996; Staber, 1994)—reflecting strong, weak and market ties. Thus strong ties (or “friends”) have generally been represented as a homogeneous set of ties. However, most strong network ties, like most groups of friends, are of sufficient variation to be more precisely classified and differentiated by the specific characteristics, or combination of characteristics, of their social relationships. The focus on affect and philos, characteristic of strong ties (Granovetter, 1985; Krackhardt, 1992), has validated concern with the strategic role of social relationships. Research describing strong ties and embedded ties has identified several characteristics of these ties—in terms of both attributes and outcomes (see Table 1). However, although these studies claim to examine strong or embedded network ties, with the exception of Uzzi (1996), they do not specify whether the population of ties were all relationally-embedded: defined as both having a social relationship that influences economic decision making and being governed through trust and relational contracting (Dyer & Singh, 1998; Granovetter, 1985; Uzzi, 1996). While the list in Table 1 represents an important mosaic of characteristics of strong and/or embedded ties, it does not represent a theoretical classification of the variation within relationally-embedded ties. -----------Insert Table 1 about here ----------- 7 Current literature approaches relational embeddedness with assumptions of homogeneity--that is, while many characteristics have been identified (see Table 1), relational embeddedness is still assumed to represent a single, dichotomous construct: e.g. ties are either relationally embedded or not). The question is whether all the characteristics in Table 1 are present in all relationallyembedded network ties or whether these are characteristics that could be present in some relationally-embedded ties. Without further classification, the homogeneity assumption leads to the conclusion that relationally-embedded ties are all alike--each composed of the characteristics in Table 1. Yet, for example, addressing Granovetter’s (1985) strong tie characteristics of frequency and affect, Alba (1982) suggests that high interaction frequency and high affect do not necessarily reside within the same relationally embedded tie, in contrast to Homan’s (1950) statement “that persons who interact frequently with one another tend to like one another” (p. 111). For example, “some relations involving intense affect may be visible only in very infrequent interaction, as between a parent and his or her adult children” (Alba, 1982, p. 46). Thus the suggestion that all relationally-embedded ties have all the characteristics found in previous embeddedness research may not accurately portray the complexity and range of variation that may actually exist within these ties. In contrast to prior assumptions of homogeneity, current understanding of the nature of relationally-embedded network ties suggests greater variation and heterogeneity than previous research has addressed. First, given the idiosyncratic nature of social relationships (Dyer & Singh, 1998), the network ties embedded within those social relationships are likely also to be idiosyncratic and heterogeneous. Second, given that relationally-embedded ties provide a variety of both advantages and disadvantages to an emerging firm (e.g. Granovetter, 1985; Portes & Sensenbrenner, 1993; Reese & Aldrich, 1995; Uzzi, 1997; Van de Ven, 1993), critical variation in social relationships may exist between these ties and may influence outcomes. Theory 8 development on relational embeddedness needs to address why some relationally-embedded ties provide advantages while other ties generate disadvantages. Third, given that network ties are governed through mechanisms of trust (Bradach & Eccles, 1991; Powell, 1990) and that trust research is identifying variation in types of trust (e.g. Good, 1988; Jones & George, 1998; Zaheer & Venkataraman, 1995), the question arises as to which types or combinations of trust provide effective governance for relationally-embedded ties. One might ask to what extent the variation in governance mechanisms of trust is related to variation and heterogeneity within relationallyembedded ties. Thus assuming greater heterogeneity and variation within relationally-embedded ties may help to capture the idiosyncrasies of social relationships, explain differential outcomes in terms of advantages and disadvantages, and provide critical insights into appropriate governance mechanisms. While relationally-embedded ties are not all alike, they are also not all unique (McKelvey & Aldrich, 1983). Therefore, to classify relational embeddedness as a theoretical construct is a critical step in theoretical development (Chafetz, 1978). Without such classification a satisfactory understanding of network relations and their roles in strategic organizing may not be attained (McKelvey & Aldrich, 1983; Ulrich & McKelvey, 1990). Lack of attention to the potential variation within the construct of relational embeddedness, as either a dependent or independent variable, may inhibit explanations of its causes, influences and strategic outcomes. Advancing the classification of relational embeddedness will aid the identification and description of variations that can create deeper understanding, build foundations for theory development, and provide a base for creating instruments and validating constructs for different types of embeddedness (McKelvey & Aldrich, 1983). 9 As the strategic context of firm emergence is critical and new firms rely so heavily upon external networks for resource acquisition, this research examines the variation of relational embeddedness within this specific context. The overarching problem is that if emerging firms rely on relationally-embedded ties for critical resource acquisition and assume that these ties are all strategically similar, and yet the ties are heterogeneous along critical social dimensions, the emerging firm may encounter difficulties in both governance and resource acquisition that may inhibit its successful emergence and performance. Strategies for resource acquisition, relationship maintenance, and firm governance need to align with the variation within these ties. For example, if relationally-embedded ties differ, to what extent can they still be governed by the same mechanisms of trust? Ungrounded assumptions of homogeneity leave the firm strategically at risk for increased constraints and disadvantages, as well as less able to participate in the advantages and benefits of exchange with relationally-embedded ties. Assuming heterogeneity among relationally-embedded ties, this study focuses on classifying how relationally-embedded ties may be similar to or different from each other. In light of recent calls for research on qualities of embeddedness, the role of social relationships in economic exchange, network governance and the relational view of the firm (e.g. Dyer & Singh, 1999; Madhok, 1997; Rowley et al., 1999; Uzzi, 1996), this study examines relationally-embedded network ties of emerging entrepreneurial firms with three research questions: 1. What are the components of the social relationships of relationally-embedded ties? 2. How can relationally-embedded network ties be classified to identify different types of embeddedness based on variations in the social relationships? 3. What strategic implications can be drawn from multidimensional view of relational embeddedness? 10 These research questions reflect the call to further clarify the qualities of relationalembeddedness and continue the agenda of further unpacking the concept of embeddedness (Uzzi, 1996). The following describes the methods used to examine variation among relationallyembedded ties. Methods This study addresses the variation of relational embeddedness using a post-positivist paradigm, a grounded theory approach, and case study methods (e.g. Eisenhardt, 1989; Glaser & Strauss, 1967; Guba & Lincoln, 1994; Miles & Huberman, 1994; Strauss & Corbin, 1994; Yin, 1994a). Following King, Keohane and Verba’s (1994) suggestion that it is “pointless to seek to explain what we have not described with a reasonable degree of precision” (p. 44), the underlying aim of this study has been to ground theoretical explanations upon thick descriptions of relational embeddedness (Schein, 1987). In an effort to identify the convergence of common themes and patterns across the cases (Huberman & Miles, 1994; Yin, 1994a), the data and the developing theory have been iteratively revisited in a research design that is “spiraling rather than linear in its progression” (Berg, 1995, p. 16). Case Study Design Case study methods provide a relevant approach for the study of the networks of emerging firms (e.g. Curran et al., 1993; Eisenhardt, 1989; Steier & Greenwood, 1998). Case selection of emerging firms was based on theoretical sampling (Erlandson, Harris, Skipper, & Allen, 1993; Yin, 1994a) and specifically controlled for location and industry by selecting all eight cases from the computer industry within the same county of a US western state. The choice of a high-tech entrepreneurial context for this case study builds upon recent research on entrepreneurial networks in high-technology industries (e.g. Hansen, 1995; Saxenian, 1990; Shan, Walker, & Kogut, 1994; Shuman & Buono, 1992; Zhao & Aram, 1995). 11 In addition, emerging entrepreneurial firms provide a rich context for the study, given their heavy reliance on network ties that stem from and are embedded within social relationships (Larson & Starr, 1993). The pecific location was selected as prime for the emergence of new entrepreneurial firms with high potential for networking activity due to current employment upheaval in the computer industry within this county (Saxenian, 1990). Recent downsizing and firm closures in the county had increased unemployment in the local computer industry, increasing the likelihood of new firms emerging as attempts to reestablish equilibrium in the local industry (Kirzner, 1973, 1997). Another criterion for theoretical sampling was the number of the firm’s entrepreneurial founders, given that the number of entrepreneurial partners differs across firms and influences firm strategy (Chandler & Hanks, 1998). The identification of an emerging entrepreneurial firm was based upon the working definition of an entrepreneur as the founder, owner, and manager of a private firm between 18 and 24 months old. Thus the theoretical sampling design controlled for industry, location and number of founders. Publicly-available lists of new business licenses provided the pool of 18-24-month-old firms at the time of data collection.3 Of these firms, the list identified 80 out of 982 (8%) as being within the computer industry. The researcher screened these 80 firms by telephone to gather preliminary data regarding the industry, the number of founders, and the fit with eligibility and exclusion criteria. The researcher classified firms based on the number of founders (range: 1-3) and the firm’s eligibility within the definition of an emerging entrepreneurial firm. These eligibility criteria included founder creation, majority ownership by founder, founder management, age of firm as 18-24 months since business licensure, and classification of the firm as a new business rather than a renamed previous business. Exclusion criteria eliminated firms no longer in business or those with non-profit licensing, headquarters out of the county, or 12 disconnected phones. Based on the screening, the researcher created three lists of eligible firms classified according to the number of founders (1, 2 or 3). Finally, the researcher recontacted the firms on each list in alphabetical order to further inform them about the research, to obtain their verbal agreement to participate in the study, and to arrange for the first interview appointment. Initially, the first two firms on each list that were both willing to participate and accessible during the data collection timeframe were selected for the study. This process provided 6 cases; 2 additional cases were later included in the process of reaching theoretical saturation. These 8 cases encompassed 17 individual entrepreneurial partners, with 2 firms having solo entrepreneurs, 3 firms having two partners, and 3 firms having three partners. See Table 2 for comparative information on the cases. ------------------------------------------Insert Table 2 about here ------------------------------------------- Data Collection The first phase of data collection entailed an open-ended interview with each of the 17 entrepreneurs across the 8 case study firms. During the interview, the researcher sought to understand the firm’s history and to identify all of the direct dyadic network tie relationships that the entrepreneur determined to be relevant to the firm’s success. The informants described their network history as well as their experiences and exchanges with these network ties. Each interview continued until the informant had completed the description of his or her network; most lasted about two hours. Based on this initial interview and on concepts of graph theory, the researcher created a network map for each firm’s network system to facilitate visualizing and communicating about the firm’s network. The network map enabled the researcher to visualize the potential influence of network-level structural embeddedness on relational embeddedness at the dyadic level. 13 The second phase of data collection entailed a follow-up interview to further explore each network, clarify ambiguous relationships, and conduct a member check (Miles & Huberman, 1994). The member check, a followup interview, allowed the informants the opportunity to confirm the accuracy of the researcher’s rendition of the network map, along with a second chance to clarify the network relationships. Brief descriptive quantitative data were collected regarding characteristics of the network ties. In addition, both interviews and network data yielded further descriptive quantitative data in the form of counts, percentages and categorical distributions. Data Analysis The data analysis and generation of themes and patterns were iterative with the data collection (Gough & Scott, 2000), and theoretical models were continually modified to incorporate new data and new themes (Miles & Huberman, 1994). Data analysis included within-case, withingroup, across-case, and across-group pattern matching (Denzin & Lincoln, 1994; Miles & Huberman, 1994). The use of Word, NVivo and MacFlow software programs facilitated the computer analysis of textual, tabular, and network data (Fisher, 1997; "NVivo," 2000; Richards & Richards, 1994). Identification of relationally-embedded ties. During data collection, each of the 8 emerging entrepreneurial firms represented a case. With data analysis, the level of analysis shifted to examine each dyadic network tie as its own case, initially exploring over 300 ties. Ties were identified as embedded or non-embedded, based on meeting at least one of the two outcome criteria. The first embeddedness criterion, evidence of the influence of the social relationship upon economic actions of the firm (Granovetter, 1992; Uzzi, 1996), was demonstrated as the social relationship having influenced expectations, communication, decision making, and 14 provision of services before terms of exchange were clarified, particularly in regards to buying, hiring, development, financial and other resource decisions. The second criterion of embeddedness, evidence of relational contracting as opposed to traditional market contracting (Dyer & Singh, 1998; Williamson, 1985), was demonstrated by the absence of written contracts: by reliance on verbal agreements, handshake agreements, and assumed agreements. If the relationship did not demonstrate either of these embeddedness outcomes, the tie was identified as non-embedded. The entrepreneurs initially identified over 300 dyadic network ties; however, only 160 of those ties generated sufficient information to support screening for characteristics of relational embeddedness. The screening of these 160 ties, based on the two embeddedness criteria, identified 66 relationally-embedded ties (41%) drawn from across all eight firm cases (see Table 3). Data analysis then focused on these relationally-embedded ties and their social relationships. Identifying non-embedded ties provided a source of contrast enabling the researcher to iteratively test the findings against non-embedded network ties. To this point in the analysis, however, the dichotomy between embedded and non-embedded ties merely echoed previous research. The question still remained as to how these relationally-embedded ties were similar to or different from each other: that is, whether relational embeddedness represents a homogeneous construct or whether important variations exist between these ties that should be considered when relational embeddedness is used as research variable. ---------------------Insert Table 3 about here ---------------------- Textual analysis and coding. During data analysis, NVivo software was used to facilitate the researcher’s coding of key classification themes and patterns found within the informants’ descriptions of their relationally-embedded ties (Gough & Scott, 2000; MacQueen, McLellan, 15 Kay, & Milstein, 1998). Coding is “a process of interpretation that…breaks the text down into meaningful chunks or segments” (MacQueen et al., 1998, p. 33). The researcher’s coding identified and labeled the informants’ descriptions of the social relationships based upon the ideas, concepts, vocabulary and linguistic cues that emerged from the descriptions themselves (Coffey & Atkinson, 1996; MacQueen et al., 1998). For example, the description “We get together and talk for like an hour just to catch up on how his life is” (4-4:1959) was coded into several categories: Getting Together, Catching Up, Non-Work Communication, Knows Personally, and Familiar with Tie’s Life. This inductive and emic coding method facilitated the exploratory research design based upon grounded theory (Lincoln & Guba, 1985; Strauss & Corbin, 1994). From this approach, categories or themes from previous research may provide a “pre-understanding” (Gummesson, 1991) but are not directly imposed upon the initial analysis of the data to avoid researcher bias. MacQueen et al (1998) suggest that bias may stem from reliance on previous research, as substantial reference to professional jargon (i.e. etic codes) encourages the inclusion of coders’ preconceptions in the data analysis, and also that use of etic coding may generate difficulty in distinguishing the voice of the respondent from that of the analyst. Etic coding may make implicit assumptions that are not supported in the text. Therefore, coding was focused on using the informants’ “own terms and semantics to guide the construction of codes” (MacQueen et al., 1998, p. 33). Hierarchical coding structure. NVivo facilitated the researcher’s emic coding of text into emergent categories and themes based on its text management, marking, searching and organization functions. Initially, over 200 separate descriptive categories emerged from the emic coding process. The text and the category labels were continually re-examined for labeling, content, clarity and potential overlap. The categories were continually and iteratively reorganized through combining and splitting, as necessary to create a set of non-redundant 16 characteristics. If a new description did not fit into an existing category, a new category was created. After all of the texts had been coded twice, each category was examined for the overall number of references, the number of references to different tie cases, and, most importantly, the number of firms in which the description occurred. To be included as its own coding category, a description needed to occur in at least 2 of the 8 firm cases and in at least 3 different tie cases. These inclusion criteria controlled for potential linguistic patterns which would cause a description to have a high number of references all provided by the same entrepreneur or all about the same tie. Given that the research was exploring for variation, the initial analysis included many very specific descriptions that did not necessarily meet these cross-case criteria. These descriptions were eventually either dropped or, if appropriate, aggregated into one of the emerging 35 descriptive elements (see Table 4). ---------------------Insert Table 4 about here ---------------------The 35 descriptive elements were aggregated to broader descriptive attributes, with the criterion that the attribute be represented by at least 6 of the 8 firms: that is, the attribute needed to capture the descriptions that were common across a majority of the firms. Throughout the analysis, dynamic recoding and relabeling provided flexibility to the coding structure so it could be adapted to either include or exclude descriptive references. This recoding is not seen as a step backwards, but rather “is always indicative of forward movement in the analysis” (MacQueen et al., 1998, p. 36). Thus meaningful categories emerged through an iterative, dynamic analysis and through organization of the informants’ own textual descriptions. During textual analysis, themes began to emerge that characterized various aspects of the entrepreneurs’ relationally-embedded ties. To reduce data and to further explore the patterns and themes (Gough & Scott, 2000; Miles & Huberman, 1994), the characteristics of the relationally- 17 embedded ties were iteratively organized into an hierarchical tree structure. This tree structure was composed of specific characteristics, aggregated elements, broad attributes, and overarching components of the social relationships (see Table 4 and Figure 1). This structure retains details while also providing for a few more homogeneous categories that more easily support generalizability (McKelvey & Aldrich, 1983). For example, the first reduction using the hierarchical tree structure organized the initial characteristics of the relationally-embedded ties into 35 categories consisting of aggregated elements of the social relationships. These 35 elements were then grouped under 14 superordinate broad attributes. Finally, the 14 attributes were grouped under three overarching component categories: personal relationship, dyadic economic interaction and social capital (see Table 4). The researcher further validated this hierarchical coding structure and the assignment of text references to these codes through review with and feedback from five independent, external research reviewers. ---------------------Insert Figure 1 about here ---------------------This hierarchical organization of the descriptions of relationally-embedded ties highlights the potential range of social relationship characteristics of the ties in this case study. However, this hierarchical tree does not, in itself, create a typology—rather it is useful in organizing a census of characteristics. While each of these characteristics was found within at least one relationallyembedded tie, not all relationally-embedded ties had all of these characteristics. Classification typology. Grounded in the hierarchical organization and grounded theory methods, a classification typology emerged that identified seven potential types of relational embeddedness based on combinations of the three overarching social components. Grounded theory methods (Strauss & Corbin, 1990) themselves are based on systematic analysis. 18 [These methods involve] the systematic comparison of small units of data (incidents) and the gradual construction of a system of categories that describe the phenomena…. The categories may have several subcategories…which are gradually elaborated and refined as specific incidents are examined, systematically coded, and compared….The analysis should eventually result in the identification of a small number of core categories which serve to tightly integrate all the theoretical concepts into a coherent whole firmly rooted (grounded) in the original evidence. (Langley, 1999, pp. 699-700) While the coding was systematic, the typology emerged as a result of the researcher’s immersion in the data and modeling of the data. While “no analysis strategy will produce theory without an uncodifiable creative leap” (Langley, 1999, p. 691), the final classification typology of relational embeddedness does serve to tightly integrate the descriptions of relational embeddedness into a useful model. Typology models are an important form of “classification methods [that] identify populations and arrange them in a classification framework” (McKelvey & Aldrich, 1983, p. 116). Each of the 160 relationally-embedded ties was re-evaluated against this classification typology to ensure that each of the ties had a place within the classification system and to “enable verification of the properties of the emerging category system” (Langley, 1999, p. 700). The typology was checked against the previous literature on embeddedness to provide additional validity. Each of the descriptions in Table 1 has a place within a component of the typology, at the level of a characteristic, an element, or an attribute. The validity of the typology is increased as knowledge of specific problems and contexts aligns with more abstract theoretical knowledge found across other contexts (Gough & Scott, 2000; Robinson, 1993). While “not all researchers will want to conduct…taxonomic studies before getting to the substance of the problem that interests them” (McKelvey & Aldrich, 1983, p. 116), this classification work identifies the potential variation and facilitates more accurate reflection on the complexity of relational 19 embeddedness. The next sections will first present the findings regarding the components of relationally-embedded network ties and then present the typology of relational embeddedness. Components of Embedded Network Ties This section describes the findings in terms of the three components of the social relationships of relationally-embedded ties, as identified in Table 4: personal relationship, dyadic economic interaction, and social capital. Each of the three components represents a label for the categorization of several more specific subordinate attributes. Personal Relationship A personal relationship with the dyadic network tie was a pervasive thread that ran, predictably, through the descriptions of relationally-embedded ties. Concrete personal relations constitute a critical element of social relationships within embedded network ties (Coleman, 1988; Granovetter, 1985; Krackhardt, 1992; Uzzi, 1996). While a personal relationship alone is often considered to be the equivalent of a social relationship, the personal relationship discussed herein represents just one of three components. The informants’ descriptions of the personal relationships with their embedded network ties demonstrated three main attributes—Personal Knowledge, Affect, and Sociality (see Table 5). ---------------------Insert Table 5 about here ---------------------Personal knowledge. Personal knowledge was defined as the extent to which the dyadic partners were aware of each other’s persona, needs, and interests: “They know my personality. They can cut to the quick on me, and read me and I can read them” (6-4, 6-5: 3828).4 Personal knowledge was based on knowing the tie personally, identifying with the dyadic partner, and having a sense of similarity. For example, informants indicated that they identified with their embedded 20 network ties--that is, they “had the same mentality” (5-16, 5-17:2004), “had common interests” (8-5:1396), or were “in kind of the same boat” (7-4:1271). Affect. Affect was represented in the extent to which feelings and emotions were considered an integral part of the dyadic relationship (Krackhardt, 1992). These feelings and emotions included respect, loyalty to the tie, and caring that “definitely goes a lot deeper that just business” (3-1:4501). Informants described their ties as being “like the son she never had” (31:3796) or indicated their “willingness to stick by them through thick and thin” (3:4530). This affect was “genuine” (3-22:7391), as opposed to merely being “a lip service deal” (3:7382). Sociality. Sociality, or the degree to which the dyadic economic interaction takes on a social and personal nature, was demonstrated in knowing about the dyadic partner’s personal life and family, as well as engaging in social activities together: “We get together and talk for like an hour just to catch up on how his life is” (4-4:1959). Genuine and sincere sociality was considered to provide an important foundation for the personal relationship component. Informants also discussed sociality as a potentially controversial attribute, noting that mixing sociality and business can be detrimental. Considering sociality to be a leverage point, they expressed the need to be especially careful in using sociality ethically with their embedded ties. The three attributes of personal relationship--i.e. personal knowledge, affect and sociality--are also reflected in previous research on personal ties (Burt, 1997), providing additional construct validity to the face validity of these attributes. The presence or development of this personal relationship can motivate entrepreneurs to carry the relationship into the context of business exchange. Emerging entrepreneurial firms, in particular, use preexisting social relationships to obtain necessary resources and to begin dyadic economic interaction (Larson, 1992; Larson & 21 Starr, 1993). For this study, the attributes of the dyadic economic interaction represented another social component of relationally-embedded network ties. Dyadic Economic Interaction The economic interaction of the dyadic partners within a business relationship was the second social component represented in the relationally-embedded ties. Dyadic economic interaction was based upon the history of the exchange relations between two partners (Emerson, 1976; Macaulay, 1963; Ring & Van de Ven, 1989). This social component focused on the processes of exchange rather than on the specific content of the economic transactions or the contractual bases for exchange. “The result of the various kinds of exchanges . . . [is] the formation of social relationships having some persistence over time” (Coleman, 1990, p. 300). The entrepreneurs described the interactions and exchanges with relationally-embedded network ties both in the context of the history of their current emerging firm and in the context of the history of interactions at previous firms. Four attributes of dyadic economic interaction emerged: extent, effort, ease, and quality (see Table 6). ---------------------Insert Table 6 about here ---------------------Interaction extent. Interaction extent, the range, scope and comprehensiveness of the patterns of exchange between dyadic partners, was composed in this study of the elements of frequency, amount, intensity, reciprocal interdependence, multiplexity and duration. Relationally-embedded network ties demonstrated higher levels of interaction in terms of these elements. For example, Chad at DataTools described the multiplexity and reciprocal interdependence of an embedded tie: I’m selling my products through them. But I’m also doing work for them. So it kind of goes both ways . . . . They are [also] a competitor . . . . In this whole 22 relationship, they are actually every single one of these that I can think of [supplier, customer, vendor, broker, previous employer]. (3-2:1585, 5404) Interaction effort. Interaction effort was defined in this study as the level of energy and resource expenditure of one dyadic partner on behalf of the other dyadic partner, specifically that which is beyond what is due, usual or expected: e.g., “I really went out of my way to help her” (3-1:6206). This extra effort often resulted from the dyadic partner’s dedication to the history of the economic relationship. This dedication and extra effort represented asymmetrical investments that maintained the dyadic economic interaction and functioned as the glue to bind and motivate the continuing interaction. The data suggest that the relationally-embedded partners almost intentionally created this condition of perpetual asymmetry through interaction effort. Problem solving, characterized by asymmetry of effort, often became interactive and cyclical rather than simply a being one-time search for a solution. For example, several entrepreneurs reported providing extra effort on behalf of a tie and then later receiving extra effort from that tie. The elements of interaction effort included work for the partner, education, responsiveness, helpfulness, and problem solving. Interaction ease. Interaction ease was defined as the facilitation and comfort of interaction between dyadic partners and acted as a lubricant in the relationship. Five elements of ease that emerged from the data were proximity, technological compatibility, goal congruence, convenience and communication quality. These elements of ease increased the level of comfort within the interaction by reducing stress, tension and difficulty, and by enhancing both extent and effort of interaction. The ease of the dyadic economic interaction, built upon dyadic history and familiarity, assured the continuation of a smooth interaction. described this ease: Kevin, at CustomSoft, 23 Once you develop a good relationship with a client, then it’s going to take a tremendous amount of bad experiences for them to turn away from you. Once they become familiar and comfortable, then that’s a part of their business they no longer have to worry about. It’s like a channel. Once they get down in that, then actually getting up and out and going to find somebody else is a huge amount of work and a lot of risk. And so once you get that established, then you’re home free with them. (5:3404) Interaction quality. Interaction quality was defined as the degree of excellence, merit or superiority of the dyadic economic interaction. The entrepreneur continually evaluates and compares the interaction with other network ties in terms of extent, effort, and ease. The elements of interaction quality in this study were having knowledge of business needs, being a known entity, understanding one another, working well together, experiencing satisfaction, having loyalty to the interaction and anticipating future interaction and synergy. High interaction quality was subjectively described as having “that magic” (4-21:4381). In several cases, external ties displayed such high degrees of interaction quality that the network partner was eventually hired or integrated into the firm. Dyadic economic interaction clearly matters, given that commitment and coordinated adaptation flourished under high interaction quality (Jones, Hesterly, & Borgatti, 1997). High interaction quality generally influenced the desire to continue the relationship. But even with poor interaction quality, a dyadic economic interaction might still be constrained to continue under conditions of high interaction extent (e.g. concentrated exchange, reciprocal interdependence), high interaction effort (asymmetry of effort creating obligations), or high interaction ease (e.g. value of the ease outweighing the costs of poor quality). 24 Social Capital A third component of the social relationships of relationally-embedded ties in this study was social capital, as manifested in the four attributes of obligations, resource accessibility, brokering, and structural embeddedness (see Table 7). These four attributes represented both the dyadic and network levels of social capital. Dyadic level: Obligations and resource accessibility. Tthe first two attributes of social capital at the dyadic level were obligations and resource accessibility (Coleman, 1988). At this dyadic level, social capital resides within the relationship between the dyadic partners (Coleman, 1990) and “inheres in the structure of relations between actors . . . [and] constitutes a particular kind of resource available to an actor . . . [making] possible the achievement of certain ends that in its absence would not be possible” (Coleman, 1988, p. 98). The first dyadic attribute, obligations, was defined as the extent of social indebtedness which binds or constrains the course of interaction between dyadic partners. This attribute was manifested in three elements: asymmetry (including gift giving), expectations and norms--“I killed myself after hours trying to get as much as I could done [for him]. And that bought me a lot of points” (5-8:1168). The second dyadic attribute, resource accessibility, was defined as the extent to which dyadic partners could acquire available resources or credit from each other (Bourdieu, 1986; Emerson, 1976; Nahapiet & Ghoshal, 1998)--“They could call [us] at any time if they had any problems” (3-8:883). ---------------------Insert Table 7 about here ---------------------Network level: Brokering and structural embeddedness. In addition, two attributes of social capital touched on the broader network level of analysis: brokering and structural embeddedness (Burt, 1998; Burt, 2000, 2002; Granovetter, 1985, 1992; Uzzi, 1996, 1997). While often 25 considered as contrasting perspectives of social capital (e.g. compare Burt (1992) and Coleman (1990)), both mechanisms contributed to the social capital of these relationally-embedded ties (Burt, 2000, 2002). Brokering was defined as the extent to which Partner A acts to connect Partner B to additional parties, creating a common tie: for example, “We stay with Steve [when he moves to a new bank] because nobody knows us at the [new] bank. But then Steve can help us at the next bank . . . . He bridges relationships and things with the other people we don’t even know” (6-7:1107, 1637). Structural embeddedness was defined as the extent to which dyadic partners have common ties that provide information flow and create greater redundancy within the network (Feld, 1997; Granovetter, 1985): We all worked together at Frameworks and now everyone is spread out all over…. So we have a personal relationship with these folks that allows us to kind of seed around in other places…. [Also] Frameworks has developed a whole channel of vendors that work for them….I know the people in that channel. So they become my channel…. Now I just go directly to them. (3-2:6403, 1573, 1582, 6388) While this study focused mainly on the dyadic relationship, the attributes of social capital at the network levels—brokering and structural embeddedness—reinforced the social capital attributes at the dyadic level--obligations and resource access. In summary, the relationally-embedded network ties of the emerging firms demonstrated three main components with their social relationships: personal relationship, dyadic economic interaction and social capital. Each of these components was an umbrella concept encompassing more specific attributes (see Table 4). However, each relationally-embedded tie did not necessarily display all three social components equally. Further analysis of each tie case suggested that different combinations of social combinations may create different types of relational embeddedness. 26 Types of Embeddedness The different combinations of the three social components suggested a potential classification typology of seven types or patterns of embeddedness that may explain this evident variety (see Figure 2). To further refine and validate the typology as descriptive of this data, each relationally-embedded tie was reanalyzed and classified in terms of this theoretical typology. Each relationally-embedded tie was coded by the degree (high, medium or low) that each social component was demonstrated within the informant’s description. In this process, only ties with social characteristics that were very clearly evident were classified as having that characteristic. If the characteristic was not consistent or was not clearly present within the informant’s descriptions of the tie, the tie was not categorized as having a high degree of that characteristic. Ties were then classified into the typology based upon the patterns of their high-degree social components. For example, one tie might have high degrees of both personal relationship and dyadic economic interaction, while another tie might have high degrees of social capital without high degrees of personal relationship or dyadic economic interaction. These two social relationships might both have developed relational embeddedness in terms of the influence of the social relationship on the firm’s economic actions or the evidence of relational contracting; yet these network ties may actually have different strengths and vulnerabilities in terms of benefits, costs and governance controls under relational contracting. For each of the seven types of embedded network ties indicated in Figure 2, Table 8 indicates social components of the ties, the percentage of ties found, and a brief example from the data. ------------------------------------------Insert Figure 2 about here ------------------------------------------------------------------------------------Insert Table 8 about here ------------------------------------------In the typology, when a tie demonstrated a high degree of only one of the three social components, the tie was classified as unidimensionally embedded. When two of the three social 27 components were clearly demonstrated, the tie was classified as bidimensionally embedded. Only when high levels of all three social components were demonstrated by the embedded relationship was the tie considered to be fully embedded. Each classification category within the typology is represented by at least one tie, and the typology encompasses all of the 66 relationally-embedded ties in the data. Embedded network ties were represented well by both fully-embedded ties (42%) and bidimensionally-embedded ties (46%), while much lower representation was found for unidimensionally-embedded ties(12%). This typology provides an initial framework for describing and classifying the variety of relationally-embedded ties and allows one to address the question of what kind of social relationship, and thus embeddedness, exists within a specific relationally-embedded network tie. While this model cannot be generalized to other contexts, it has validity for accurately classifying these data. The following sections will further discuss each of these types of embeddedness in more detail. Unidimensional Embeddedness A few of the embedded network ties (12%) in the data demonstrated high degrees of only one social component and were thus classified as unidimensionally embedded. Within this typology, unidimensionally-embedded ties correspond with each social component and have been labeled as personal, competent and hollow embeddedness. Personal embeddedness. Personal embeddedness was built solely upon the personal knowledge, affect, or sociality based on personal relationship. These relationships are likely to have developed high levels of personal goodwill trust (Barney & Hansen, 1994; Ring & Van de Ven, 1989); however, embedded ties with only a personal relationship may not necessarily have the 28 bases for high levels of personal competency or social trust (Burt & Knez, 1996; Larson, 1992; Ring & Van de Ven, 1989). Personal embeddedness may be represented by the common situation of bringing a friend into the business without direct knowledge of his or her competency. In such a case, maintaining the personal relationship becomes more salient than the economic exchange, and the entrepreneur may make economic decisions that are both inefficient and ineffective. If the tie proves to be incompetent, the entrepreneur may nevertheless be constrained to keep the tie in the business network and, therefore, may experience disadvantages (Coleman, 1988; Dubini & Aldrich, 1991; Granovetter, 1985; Portes & Sensenbrenner, 1993). The disadvantages, or dark side, of embeddedness can include issues of decision constraint, inefficiency, exchange asymmetry or political hostage-taking such that the entrepreneur loses critical strategic autonomy. Competency embeddedness. Competency embeddedness was built upon a history of dyadic interaction. Under competency embeddedness, a high degree of interaction extent and quality exist, the tie provides business value, and the interaction is comfortable and familiar with routines having stabilized. As a result, the entrepreneur is loyal to the dyadic economic interaction over time. Previous experience with the tie has proven the competency of the dyadic partner. Yet there are dangers in assuming that ties with competency embeddedness can effectively sustain relational contracting. For example, without high levels of personal relationship the goodwill and moral controls of personal trust may not be available. Competency embeddedness also lacks social capital and the resulting social trust. In addition, competency embeddedness is based upon the history and quality of the interaction as perceived by the dyadic partners. If this perception changes, the basis for this type of relational embeddedness will be lost. 29 Hollow embeddedness. Hollow ties were built upon social capital alone. They lack high levels of both personal relationship and previous dyadic interaction. The dyadic relationship is based upon a common third party recommendation. Since this type of network tie has yet to offer perceived business value and is not built upon a personal relationship, the embedded tie is considered to be hollow. Yet even these hollow ties are embedded. This type of dyadic partner can influence the economic actions of the entrepreneur due to third-party obligations or social capital, possibly causing the entrepreneur to remain in the relationship even when he or she prefers not to and when remaining is not the most economically efficient decision. Although the social relationship of unidimensionally-embedded ties is built upon only one social component, these relationships have the potential to influence the economic actions of the firm and thus reflect embeddedness (Uzzi, 1996). The potential challenge with unidimensional embeddedness is that it may not support the development of sufficient trust to sustain effective relational contracting. Thus the entrepreneur must identify and acknowledge these unidimensionally-embedded ties to avoid assuming more relational embeddedness than may actually exist. The low number of ties in this category of unidimensional embeddedness may suggest that relationally-embedded network ties tend to develop additional social components. Such a trend would support a more evolutionary perspective on embeddedness. Thus while unidimensionally-embedded ties do demonstrate embedded outcomes, they may be neither as stable nor as effective as more developed relationally-embedded ties. Bidimensional Embeddedness Bidimensionally embedded network ties (46%) exhibited high degrees of two social components. As illustrated in Figure 2, there were three types of bidimensional embeddedness: functional, isolated and latent. 30 Functional embeddedness. Functional embeddedness, present in 11% of the embedded network ties across five cases, was built upon dyadic economic interaction and social capital. While these ties demonstrated high degrees of loyalty to the interaction and to their common ties, the relationship was not based upon high levels of personal relationship. Yet they functioned very well as embedded business ties. Functionally-embedded ties assumed higher levels of trust and demonstrated fewer governance problems than did the unidimensionally embedded ties. Isolated embeddedness. Isolated embeddedness had high degrees of both personal goodwill and personal competency trust. While present in only 5% of the ties, isolated embeddedness was discussed in all 8 cases based on the informants’ past experiences. Isolated embeddedness represents high levels of loyalty both to the tie and to the interaction. Isolated ties are, however, not well connected to the rest of the dyadic partner’s network. Thus the dyad exists in a state of relative isolation from other network ties. The low frequency of isolated embeddedness of ties is actually not surprising considering isolated dyads with strong ties tend to gravitate toward greater connectedness with the larger network, given Granovetter’s (1973) concept of the forbidden triad: that is, strong dyads will eventually create links to the other strong dyads in the network, thus creating triads. Latent embeddedness. Latent embeddedness, the most common form of bidimensionally embedded ties (30%), was found across 7 cases. Latent embeddedness means that although the network tie may be perceived to be in the business network, the relationship is actually characterized by very low levels of dyadic economic interaction. Latent embedded ties had the highest number of family members when compared to other types of embedded network ties. This finding reflects a common perception that entrepreneurs use family and friends in the 31 business network. Yet while the entrepreneur may be willing to work with the network tie, either as a friend or as a favor, the competency and interaction quality of the tie were yet unproven or were not providing the high dyadic interaction quality of other ties. Full Embeddedness In contrast to unidimensionally- or bidimensionally-embedded ties, fully embedded ties demonstrated high degrees of all three social components (42%). Thus the more social components that exist within the dyadic relationship, the more the network tie is embedded within the social relationship. Many of these fully-embedded ties had been pre-existing network ties. Trust Outcomes: Beyond the Typology Although the typology focuses on the components of the social relationships, patterns of trust outcomes also emerged. Trust outcomes were not surprising, since an inclusion criterion was relational contracting. However, the relationally-embedded ties demonstrated three different types of trust: good-will trust, personal competency trust, and social trust. These categories of trust are echoed in the trust literature: personal goodwill trust is a direct, personal knowledge of and trust of each other’s good will (Hesterly, Jones, & Madhok, 1998; Larson, 1992); personal competency trust is a direct, personal knowledge of and trust of each other’s competency (Hesterly et al., 1998; Larson, 1992; Zaheer & Venkataraman, 1995); and social trust is grounded upon a common third party or larger sociological identity (Portes & Sensenbrenner, 1993; Zucker, 1986). This variation in trust outcomes further supports the heterogeneity of relationally-embedded ties in that different types of ties generated different types of trust. In the reanalysis of the ties, three patterns emerged suggesting that (1) personal relationships may 32 influence personal good-will trust, (2) dyadic economic interaction may influence personal competency trust, and (3) social capital may influence social trust. Discussion Relationally-embedded network ties represent a crucial and common component of the external network of an emerging firm (Hite & Hesterly, 2001; Johannisson & Monsted, 1998). This study illuminates the complexity of these social relationships and suggests that these ties include more variety than previous research has detailed. The data suggest that the source of this variety is found in the social components of the network relationships (see Table 4), and each of the seven types of relational embeddedness is revealed through critical compositional differences as represented in the typology (see Figure 2). The typology lays the groundwork for this expanded view of the qualities of relational embeddedness and provides a classification system for its multidimensionality, recognizing variation in both type and intensity. While previous literature has identified several characteristics of embeddedness (see Table 1), these characteristics are easily encompassed within the typology model at the level of either an element or an attribute (see Table 4). Specifically, the three social components of the typology encompass Granovetter’s (1985) three attributes of strong ties: (1) personal relationship incorporates affect; (2) dyadic economic interaction, specifically interaction extent, incorporates frequency; and (3) social capital at the individual level incorporates reciprocity. However, the typology of relational embeddedness provides more depth and includes additional characteristics not indicated by Granovetter (1985), Uzzi (1996), or other research. For example, dyadic economic interaction broadens beyond extent to the ease, effort and quality of the interaction. Thus this typology of relational embeddedness supports previous research on strong ties, while adding greater depth and breadth to the social dimensions of relational embeddedness. This 33 typology argues for relational embeddedness as a broader construct than strong ties, given that a tie could be relationally-embedded but not necessarily strong. Contrary to the assumptions of previous research, this data suggest that relationally-embedded network ties may not be assumed to be similar, given the variety of social characteristics in which the tie may be embedded. An assumption of heterogeneity suggests that relational embeddedness represents a multidimensional construct. Theoretical Implications The main theoretical implication of this research is that in emerging firms relational embeddedness is a multidimensional construct in which the variation may now be more clearly specified. While the classification of the variation within the theoretical construct of relational embeddedness is a critical step in theoretical development (Chafetz, 1978), the typology presented can and should be subjected to further empirical testing (Doty & Glick, 1994; McKelvey & Aldrich, 1983). A classification typology of relational embeddedness, absent in existing models, facilitates the identification and description of variation within this strategically critical construct (McKelvey & Aldrich, 1983). Variation within relational embeddedness is a function of both the type and intensity of embeddedness. That seven types of relational embeddedness emerge in the typology suggests that relational embeddedness is not a dichotomous variable, but that different combinations of social components contribute to its multidimensionality. The typology also addresses the potential intensity or magnitude of embeddedness, given the possibility of a different number of social components within each tie. While some ties demonstrate high levels of only one social component, other ties may demonstrate high degrees of two or even all three social components. Fully-embedded ties, demonstrating all three components, represent the greatest intensity of embeddedness. The greater the embeddedness intensity, the greater the reliance may be upon a 34 balance of social components and a broader range of trust. Given access to more types of trust in the network relationship, embeddedness intensity is likely related to more effective relational governance. This research supports the need to consider more variation when using relational embeddedness as a theoretical construct. The typology lays the foundation for greater specificity in building theoretical models regarding the strategic outcomes and implications of relational embeddedness. One critical challenge in clarifying the construct of relational embeddedness, as seen in the previous work on embeddedness, is the need to clearly distinguish between its descriptive characteristics and its outcomes. This typology represents a descriptive classification of characteristics of relational-embeddedness and provides the basis for clearer identification of relational embeddedness as an independent variable. Considering different types of embeddedness facilitates the examination of relational embeddedness as a complex categorical variable, while examining varying embeddedness intensity reveals that relational embeddedness can also be explored as a continuous variable. The typology, therefore, enables the development of instrumentation for greater specificity in describing relational embeddedness. As a result, future research may find better explanations for variation in the strategic outcomes of relational embeddedness. Another theoretical implication is that the typology lays a foundation for understanding potential advantages and disadvantages of relational embeddedness (e.g. Dubini & Aldrich, 1991; Granovetter, 1973; Hite & Hesterly, 2001; Portes & Sensenbrenner, 1993). The seven types of relational embeddedness may have varying advantages and disadvantages, depending on their specific composition of social components and on the variation in both type and intensity of relational embeddedness. For example, ties with greater intensity of relational embeddedness 35 (e.g. fully embedded) may provide more of the benefits generally attributed to embeddedness, such as resource acquisition, while ties with less intensity of relational embeddedness (e.g. unidimensionally- or bidimensionally-embedded) may experience more of the disadvantages, such as increased exposure to potential governance hazards. Thus this typology provides a rationale for understanding how different relationally-embedded network ties may provide differential advantages and costs as well as opportunities and constraints for the emerging firm. A third theoretical implication is that full embeddedness is different from Uzzi’s (1997) concept of overembeddedness in which the high extent of social relationship is harmful to the economic exchange. Full embeddedness in this typology is identified when the social relationship is a balance of all three social components, likely resulting in a broader spectrum of trust and other control mechanisms. Overembeddedness generally refers to a high proportion of embedded ties at a more aggregated egocentric network level of analysis. Overembeddedness may not necessarily derive from simply having too many ties embedded within social relationships as much as it may result from the over-reliance of these ties on any one social component alone. As such, overembeddedness may result from an imbalance among the three social components such that the network tie remains unchecked by the potential governance controls found within a greater balance of social components. Strategic Implications The variation among relationally-embedded network ties may have critical strategic implications for emerging firms, specifically in terms of issues of governance and resource acquisition. As emerging firms are able to better recognize specific types and intensity of embeddedness, they may be more able to maximize the value in these strategic external network relationships (Madhok, 1997). 36 The typology suggests several potential influences of multidimensional relational embeddedness on strategic organization and outcomes for emerging firms. Governance, trust and relational embeddedness. The typology of seven different types of relational embeddedness enables further clarification of the connection between the social relationship and the resulting trust within the embedded network tie. The strategic implication is that different combinations of trust may result from the different types of embedded ties. Given that trust supports critical governance mechanisms for embeddedness (Granovetter, 1985; Jones et al., 1997; Powell & Smith-Doerr, 1994; Uzzi, 1996), these different combinations of trust may influence the effective governance of relationally-embedded ties (Dyer & Singh, 1998; Zaheer & Venkataraman, 1995). Fully-embedded network ties, for example, may more effectively sustain relational contracting based on more types of trust and a greater redundancy of governance controls (Jones et al., 1997; Rowley et al., 1999). On the other hand, a mismatch between governance controls and type of embeddedness may make the emerging firm more vulnerable. Thus future research should examine the extent to which governance mode may be most effectively chosen through considering the characteristics of the dyadic relationship as well as the characteristics of the transaction (Williamson, 1985). Specifying different types of relational embeddedness challenges the notion that a single governance mode of relational contracting, based upon generic or unspecified types of trust, can provide equally effective governance for all types of relationally-embedded ties. Rather, the multidimensionality of relational embeddedness may affect significantly the stability and effectiveness of the governance of these ties, particularly in emerging firms that may too easily rely on relational contracting alone (Larson, 1992). Strategically, fully-embedded ties built upon all three social components would be expected to demonstrate more types of trust and, therefore, be more effectively governed through 37 relational governance than a uni-dimensionally embedded tie based on only one social component. Resource acquisition and relational embeddedness. Another strategic implication of the multidimensionality of relational embeddedness is that emerging firms rely on relationallyembedded ties for critical resource acquisition. While relationally-embedded network ties generally provide greater resource access to emerging entrepreneurial firms (Hite & Hesterly, 2001; Jarillo, 1989), this resource access may be tempered by the effectiveness of the governance mechanisms (Powell & Smith-Doerr, 1994). The more effective the governance mechanisms, the more likely that resource exchange will continue to occur through a particular relationship over time (Poppo & Zenger, 2000). Given that fully-embedded ties demonstrated three types of trust, providing more overlapping governance safeguards than other types of relational embeddedness, these ties may have better access to the resources of their network partners. Practical Implications The patterns of the multidimensionality of relational embeddedness suggest that emerging firms need to carefully and effectively manage their external network relationships in five specific ways. First, emerging firms need to carefully examine their network ties to identify different types and intensities of relationally-embedded ties rather than making ungrounded assumptions that these ties are all strategically similar. Second, emerging firms may be able to adapt the relational embeddedness of network ties through the development or reduction of social components over time. Third, emerging firms may need to strategically invest in their network ties, considering that inefficiencies may stem from spending efforts appropriate to fullyembedded tie on non-relationally-embedded ties (Aldrich, 1989). Fourth, based on the 38 realization that not all relationally-embedded ties are alike, the emerging firm may be better able to build in—at an earlier point—necessary additional mechanisms to ensure effective governance for these ties. Lastly, as emerging firms realize that these relationally-embedded ties may require different strategies for relationship maintenance, resource acquisition, and governance, they may be better able to access strategically-critical resources through these ties in a way that will enhance advantages and alleviate potential disadvantages. These network management strategies may enable emerging entrepreneurial firms to better recognize, analyze and manage the relational embeddedness of their network ties. Future Research While the grounded theory approach and the case study design limit the generalization of these findings to these specific cases and, based upon analytical generalization, to the development of theoretical models (Gummesson, 1991; King et al., 1994; Yin, 1994b), this study provides a classification framework that should be tested across other contexts. The current typology represents unjustified variation in which “truth has not yet been established, but one for which truth is not precluded. Justification comes after a belief has been generated and tested" (Weick, 1979, p. 123). Thus future research should produce replications across broader geographical, industrial, and organizational populations to further confirm and refine the classification model (McKelvey & Aldrich, 1983). As the mosaic of context studies grows regarding relational embeddedness, and as the theoretical knowledge of its specific constructs aligns with knowledge found across other contexts, the generalizability of the findings increases (Gough & Scott, 2000; McKelvey & Aldrich, 1983; Robinson, 1993). In addition to testing this typology, future research should pursue four additional streams for future inquiry on relational embeddedness. The first stream for future research is to use the typology to develop instruments to better support the identification and measurement of different types and intensity of relational embeddedness 39 across other contexts. These development efforts will contribute to the construct validity of different types and intensities of embeddedness and, as a result, the multidimensionality within relational embeddedness can be more accurately taken into account when this construct is used as either a dependent or independent variable in future research. Second, future research should incorporate the dyadic partner’s perspective on the relationallyembedded tie to add depth to the typology and possibly explain even more variation within relationally-embedded ties. Assuming that the typology classification holds for the partner’s perspective, the combination of the two perspectives could theoretically create up to 42 possible combinations or types of relationally-embedded ties. For example, Partner A may classify a dyadic relationship with Partner B as a latent tie, while Partner B classifies the relationship as functionally embedded. While the number of actually-occurring combinations is likely much less, the question is to what extent Partner B’s perspective of the social relationship affects the type and intensity of relational embeddedness experienced by Partner A. The inclusion of the partner’s perspective may further characterize the relationship as well as further increase the potential variation within relational embeddedness. Third, future research should examine the strategic implications of variation in relational embeddedness. Specifically, research should explore the relationship between both the types and intensity of relational embeddedness and various outcomes of trust, governance, resource acquisition, and successful firm emergence. A further need is to identify effective governance mechanisms for different types of relational embeddedness and to determine what, if any, additional forms of governance are necessary beyond trust to provide for effective governance for each type. 40 Fourth, future research should examine how relational embeddedness develops over time. Given variation in type and intensity, to what extent and in what ways do different types of relationallyembedded ties adapt or change? The number of ties in each category suggests an underlying evolutionary process in that very few ties were embedded based upon only one social component (unidimensionally embedded). Rather, this type of tie tended to be less stable and to move toward the development of a second social component, raising the question of what processes and paths are involved in the evolution of relational embeddedness. In addition, a few of the ties lost social components and actually reduced their relational embeddedness. This finding raises the question that if relationally-embedded ties evolve, either towards more or less embeddedness, then how do governance and resource-acquisition strategies need to be adapted? The typology provides the groundwork for further exploring the evolution of relational embeddedness. Conclusion Relational embeddedness has extensive ramifications for the strategic organization of emerging entrepreneurial firms. This study examined the multidimensional components of relationallyembedded network ties of emerging entrepreneurial firms in the computer industry, using a qualitative case study method. A typology is derived for classifying seven different types of relational embeddedness along three degrees of intensity, suggesting that critical variation in the type and intensity of embeddedness may be an important source of heterogeneity among relationally-embedded network ties in this context. This study lays the foundation for construct validity of different types of relational embeddedness. These findings address the call for a clearer understanding of both the qualities of relational embeddedness (Coleman, 1988; Uzzi, 1996) and the multidimensional nature of these ties (Larson & Starr, 1993). This research has further unpacked the concept of relational embeddedness to discover “components of social organization” (Coleman, 1988, p. 101) that may contribute to the effective strategic organization of emerging firms. Table 1 Characteristics of Strong and/or Relationally-Embedded Ties Affect/Philos/Passions (Granovetter, 1985; Krackhardt, 1992; Uzzi, 1999) Frequency/Frequent contact (de Burca, Brannick, Fynes, & Glynn, 2001; Granovetter, 1985) Reciprocity (Granovetter, 1985; Portes & Sensenbrenner, 1993; Powell, 1990; Uzzi, 1999) Trust/Enforceable Trust (Portes & Sensenbrenner, 1993; Powell, 1990; Uzzi, 1996) Complementarity (Powell, 1990) Accommodation/Adaptation (Powell, 1990) Indebtedness/Imbalance (Powell, 1990) Collaboration (Powell, 1990) Transaction investments (Powell, 1990) Strong history (Powell, 1990) Fungible skills (Powell, 1990) Expectations (Portes & Sensenbrenner, 1993) Social capital (Portes & Sensenbrenner, 1993) Bounded solidarity (Portes & Sensenbrenner, 1993) Lower opportunistic behavior (Provan, 1993) Density (Staber, 1994) Maximize relationship over org (Powell & Smith-Doerr, 1994) Fine-grained information transfer (Uzzi, 1996) Problem Solving (Uzzi, 1996) Duration (de Burca et al., 2001; Uzzi, 1999) Multiplexity (de Burca et al., 2001; Uzzi, 1999) Diffusion (MacLean, 2001) Facilitation (MacLean, 2001) Personal involvement (de Burca et al., 2001) Low formality (few contracts) (de Burca et al., 2001) Connectedness (de Burca et al., 2001) 42 Table 2 Comparative Case Data # Partners Partner Relationships Product Gross Sales 1998 ($000) Growth Goals (estimated) Corporate Structure Board Capital Structure Ties: # Embedded # Discussed # Total Full v. Part Time Firm Office- v. Home-based Prev. Experience Data Net 3 2 Spouses 1 Referred Service: Data Storage & Retrieval (Internet) $225 Last Word 3 Prev. Work Associates Software: Software Development (application) $123 Data Tools 3 Prev Work Associates Service: Custom Programming (application) $4,000 Animators 2 Brothers Custom Soft 2 Spouses Comm Net 2 Brothers Web Design 1 -- Ram Part 1 -- Service: Custom Programming (data) $200 Service: Custom Programming (application) $50 Software: Software Development (Internet app) $10 Service: Custom Programming (Internet) $9 Hardware: Hardware Retail Sales Moderate Low High Moderate Decline Moderate Low High S-Corp C-Corp C-Corp S-Corp S-Corp C-Corp Sole Prop. LLC Partners Partners Partners Partners Partners -- Partners Self; Credit cards Self Partners /SrMgt Self; Considering VC Self Self; Home equity Prev. Bus.; Pursuing VC Self Self; Supplier Credit 3 9 36+ Full 6 9 37+ Full 15 39 95+ Full 7 30 39+ Full 8 21 42+ Part 7 14 30+ Full 7 14 25+ Part 13 24 35+ Full Home Office Office Office Home Office Home Home High; 2nd ENT firm in industry Medium; 1st ENT firm; Worked in industry prev. Medium; 1st ENT firm; Worked in industry prev. Low; 1st firm in industry Medium; 1st ENT firm; Worked in industry prev. High; 2nd firm in industry Low; 1st firm in industry Low; 1st firm in industry $450 43 Table 3 Number of Embedded and Non-Embedded Network Ties by Case 1-DataNet 3 33% 6 66% Total Number of Ties 9 2-LastWord 6 66% 3 33% 9 3-DataTools 15 38% 24 62% 39 4-Animators 7 23% 23 77% 30 5-CustomSoft 8 38% 13 62% 21 6-CommNet 7 50% 7 50% 14 7-WebDesign 6 43% 8 57% 14 8-RamPart 14 58% 10 42% 24 TOTAL 66 41% 94 59% 160 Case Embedded Number Ratio Non-Embedded Number Ratio 44 Table 4 Components, Attributes and Elements of Social Relationships Among Embedded Network Ties SOCIAL COMPONENT Personal Relationship Dyadic Interaction Social Capital (network level) Social Capital (dyadic level) ATTRIBUTES Personal Knowledge ELEMENTS Identifies with Knows personally Affect Respect Loyalty to Tie Caring Sociality Knowledge of tie’s life and family Social activities Extent Frequency Amount Intensity Reciprocal Interdependence Multiplexity Duration Effort Working for Partner Education Responsiveness Helpful Problem Solving Ease Proximity Technological Compatibility Convenience Goal Congruence Communication Quality Quality Familiarity Knowledge of Business Needs Working Well Together Satisfaction Loyalty to Interaction Brokering Introductions to Third Party Structural Connectedness of Dyad’s Mutual Embeddedness Ties Obligations Asymmetry Expectations Norms Resource Accessibility Ability to Access Resources 45 TABLE 5 Definitions and Examples of Personal Relationship Attributes of Embedded Network Ties PERSONAL KNOWLEDGE : The extent to which the dyadic partners are aware of each other’s personal needs and interests: e.g., “They know my personality. They can cut to the quick on me and read me and I can read them” (6-4, 6-5: 3828). Identifies The degree to which dyadic partners have a sense of similarity; e.g., homophily, with similar backgrounds and experiences Knows The degree to which dyadic partners are aware of and familiar with each other personally AFFECT: The extent to which emotion and feeling are integral parts of both business and non-business interactions: e.g., “definitely goes a lot deeper that just business” (3-1:4501). Respect The degree to which dyadic partners esteem and appreciate one another Loyalty to Tie The degree to which the dyadic partners are loyal to interaction with each other as individuals, often following the person from firm to firm Caring The degree to which the dyadic partners are genuinely interested in the well-being of the other, like each other, and seek each other’s society and friendship SOCIALITY: The degree to which the dyadic economic interaction takes on a social and personal nature: e.g., “We get together and talk for like an hour just to catch up on how his life is” (4-4:1959). Knows tie’s The degree to which dyadic partners are aware of, know, and discuss each other’s life and personal lives and families family Social The extent to which dyadic partners engage together in events and activities outside activities of business functions 46 TABLE 6 Definitions and Examples of Dyadic Economic Interaction Attributes of Embedded Network Ties INTERACTION EXTENT: The range, scope and comprehensiveness of interaction between dyadic partners. Frequency Amount Intensity Reciprocal Interdependence Multiplexity Duration How often the dyad interacts The degree of interaction between dyadic partners, as indicated by size, by anticipated payment, or by comparison to other ties; at the extreme, concentrated exchange is the extent to which dyadic partners rely solely upon the other to fill the function, through either choice or lack of options The amount of interaction between dyadic partners over a specific time period, particularly under sense of deadline or pressure The degree to which interaction between dyadic partners entails outputs becoming inputs for the other or posing contingency upon the other, thereby requiring an adjustment to other actions (Thompson, 1967) The degree to which interaction between dyadic partners occurs in more than one sphere, fulfilling more than one function; may entail business & non-business interaction The extent to which dyadic partners have had previous interaction with each other or the length of the dyadic interaction INTERACTION EFFORT: The level of expenditure of energy and resources of one dyadic partner on behalf of the other dyadic partner, beyond that which is due, usual, or expected. Work for the Partner Education Responsiveness Helpful Problem Solving The degree to which dyadic partners expend energy for the accomplishment of the partner’s goals, as if they were hired by the partner The degree to which dyadic partners teach, train, or educate the other partner The degree to which dyadic partners react quickly to address concerns of the other The degree to which the actions of dyadic partners further the goals of the other The extent to which dyadic partners engage in trying to solve the problems of the other or that they do so jointly INTERACTION EASE: The level of facilitation and comfort of interaction between dyadic partners due to the reduction of effort, stress, tension, and difficulty Proximity Technological compatibility Convenience Goal congruence Communication Quality The degree of physical distance or space between the dyadic partners The extent to which dyadic partners use and/or work with the same technology, including both hardware, software, and other electronic media The extent to which the interaction between dyadic partners is advantageous or may entail the more efficient use of some resources The degree to which dyadic partners agree upon mutual goals or vision for interaction The extent to which the amount, type, and frequency of communication facilitates positive interaction INTERACTION QUALITY: The degree of excellence, merit, or superiority of the dyadic interaction. Familiarity Knowledge of business needs Working well Satisfaction Loyalty to Interaction The extent to which dyadic partners are acquainted with each other’s routines, interaction style, and broader scope of business (beyond just the current transaction) The extent that they are aware and act on the business needs of the other The extent to which dyadic partners interact effectively to achieve their goals together The degree to which dyadic partners are satisfied and content with the interaction patterns and routines The degree to which dyadic partners will stay in the interaction versus pursuing other options 47 TABLE 7 Definitions and Examples of Social Capital Attributes of Embedded Network Ties BROKERING : The extent to which dyadic partners introduce one another to new third parties. STRUCTURAL EMBEDDEDNESS: The extent to which a dyad’s mutual contacts are connected to one another” (Granovetter, 1992, p. 35). OBLIGATION The extent of social indebtedness which binds or constrains the course of interaction between dyadic partners. Asymmetry The extent to which the reciprocity between dyadic partners is unbalanced, either consistently or at a given point in time Expectations The degree to which dyadic partners anticipate, think, or believe that certain outcomes will occur Norms The degree to which the relationship between dyadic partners is governed by an ideal standard stemming from group memberships of either partner RESOURCE ACCESSIBILITY: The extent to which dyadic partners can access the available resources from each other (Bourdieu, 1986; Putnam, 1993). 48 Table 8 Taxonomy of Embedded Network Ties (N=66) Types of Embeddedness % N 2% 1 2% 1 8% 3 11% 7 5% 3 30% 20 42% 28 Description Example UNIDIMENSIONAL EMBEDDEDNESS Personal Competency Hollow High Personal Relationship Trust: Personal Goodwill High Dyadic Economic Interaction Trust: Personal Competency High Social Capital Trust: Social Peter: Hired a good friend who needed a job but had no experience. Kevin: Depends on and is loyal to independent graphic artist due to high quality and service over time. He had worked with him in his previous employment. Casey: Uses the insurance agent his father recommended and uses. Service was terrible, and the agent was hard to get along with. Casey couldn’t “quit” using him. BI-DIMENSIONAL EMBEDDEDNESS Functional Isolated Latent High Dyadic Economic Interaction High Social Capital Low Personal Relationship Trust: Social &Pers Competency High Personal Relationship High Dyadic Economic Interaction Low social capital Trust: Pers Goodwill & Competency High Personal Relationship High Social Capital Low Dyadic Economic Interaction Trust: Personal Goodwill & Social Kathryn: Uses great graphic artist, used in her previous venture, who always comes through with quality and goes the extra mile. She refers many people to this artist but doesn’t consider him a “friend” (low personal relationship). Mike: Contracts with high school friend, who recently moved to Mike’s town, to become an independent sales rep for Mike. The friend has good sales skills, but Mike intentionally does not bring him into his own vendor network (low social capital). Ann: Knows she can obtain office space from a neighbor, her “second father,” whenever she decides needs it (low dyadic economic interaction). FULL EMBEDDEDNESS Full High Personal Relationship High Dyadic Econ Interaction High Social Capital Trust: Personal Goodwill Personal Competency Social Matt: Serves a client from previous job who followed him to his new venture. She is much older than Matt, functioning as both a mother figure and a mentor. As a very “big player” in his industry, she has brought him many new clients and contacts. She knows his wife and children and is concerned about his career, his firm’s success, and his health. She will not go to anyone else for her data management needs because she thinks Matt’s work is the best. Matt gives her “tons of extras” and keeps her on the cutting edge. On his birthday, she sends cards; on her birthday, he sends flowers. Figure 1 Hierarchical Tree Structure Element Element Attribute Component Element Element Attribute Figure 2 Typology of Relational Embeddedness Social Capital Trust: Social (3rd party) Controls: Reputation HOLLOW Embeddedness Personal Relationship Trust: Personal /Good-will Controls: Maintenance of Personal Relationship LATENT Embeddedness FULL PERSONAL Embeddedness FUNCTIONAL Embeddedness Embeddedness ISOLATED Embeddedness COMPETENCY Embeddedness Dyadic Economic Interaction Trust: Personal /Competency Controls: Value of Relationship History REFERENCES Alba, J. D. (1982). Taking stock of network analysis: A decade's results. Research in the Sociology of Organizations, 1, 39-74. Aldrich, H. (1989). Networking among women entrepreneurs. In O. Hagan & C. Rivchun & D. Sexton (Eds.), Women-Owned Businesses (pp. 103-131). New York: Praeger. Aldrich, H. E., Elam, A. B., & Reese, P. R. (1996). Strong ties, weak ties and strangers: Do women owners differ from men in their use of networking to obtain assistance? In S. Birley & I. C. MacMillan (Eds.), Entrepreneurship in a Global Contest (pp. 1-25). London: Routledge Ltd. Aldrich, H. E., & Zimmer, C. (1986). Entrepreneurship through social networks. In D. L. Sexton & R. W. Smilor (Eds.), The Art and Science of Entrepreneurship (pp. 2-23). Cambridge, MA: Ballinger. Barney, J. (1991). Firm resources and sustained competitive advantage. Journal of Management, 17(1), 99120. Barney, J. B., & Hansen, M. H. (1994). Trustworthiness as a source of competitive advantage. Strategic Management Journal, 15, 175-190. Baum, J. A. C. (1996). Organizational ecology. In S. Clegg & C. Hardy & W. Nord (Eds.), Handbook of Organization Studies (pp. 77-114). London: Sage. Baum, J. A. C., & Oliver, C. (1992). Institutional embeddedness and the dynamics of organizational populations. American Sociological Review, 57, 540-559. Berg, B. L. (1995). Qualitative research methods for the social sciences. Boston: Allyn and Bacon. Bhide, A. (2000). The origin and evolution of new business. Oxford: Oxford University Press. Borch, O. J., & Arthur, M. B. (1995). Strategic networks among small firms: Implications for strategy research methodology. Journal of Management Studies, 32(4), 419-441. Bourdieu, P. (1986). The forms of capital. In J. G. Richardson (Ed.), Handbook of theory and research of the sociology of education (pp. 241-258). New York: Greenwood. Bradach, J. L., & Eccles, R. G. (1991). Price, authority and trust: From ideal types to plural forms. In G. Thompson & J. Frances & R. Levacic & J. Mitchell (Eds.), Markets, hierarchies and networks: The coordination of social life (pp. 277-292). London: Sage Publications. Bruderl, J., Preisendorfer, P., & Ziegler, R. (1992). Survival chances of newly founded business organizations. American Sociological Review, 57, 227-242. Burt, R. S. (1982). A note on cooptation and definitions of constraint. In P. V. Marsden & N. Lin (Eds.), Social structure and network analysis (pp. 219-233). Beverly Hills: Sage Publications. Burt, R. S. (1992). Structural Holes: The Social Structure of Competition. Cambridge: Harvard University Press. Burt, R. S. (1997). A note on social capital and network context. Social Networks, 19, 355-373. Burt, R. S. (1998). The network structure of social capital. (Unpublished working paper). Burt, R. S. (2000). The network structure of social capital. In R. I. Sutton & B. M. Staw (Eds.), Research in Organizational Behavior (Vol. 22). Greenwich, CT: JAI Press. Burt, R. S. (2002). The social capital of structural holes. In M. F. Guillén & R. Collins & P. England & M. Meyer (Eds.), New Directions in Economic Sociology (pp. Chapter 7, p. 201-251). ???: Russell Sage Foundation. Burt, R. S., & Knez, M. (1996). Trust and third-party gossip. In R. M. Kramer & T. R. Tyler (Eds.), Trust in organizations: Frontiers of theory and research (pp. 68-89). Thousand Oaks, CA: Sage. Chafetz, J. S. (1978). A primer on the construction and testing of theories in sociology. Itasca, IL: F. E. Peacock Publishers, Inc. Chandler, G. N., & Hanks, S. N. (1998). An investigation of new venture teams in emerging businesses. Gent, Belgium. Coffey, A., & Atkinson, P. (1996). Making sense of qualitative data: Complementary research strategies. Thousand Oaks, CA: Sage Publications. Coleman, J. S. (1988). Social capital in the creation of human capital. American Journal of Sociology, 94(Supplemental), S95-120. Coleman, J. S. (1990). Foundations of social theory. Cambridge, MA: Harvard University Press. Curran, J., Jarvis, R., Blackburn, R. A., & Black, S. (1993). Networks and small firms: Constructs, methodological strategies and some findings. International Small Business Journal, 11(2), 13-25. de Burca, S., Brannick, T., Fynes, B., & Glynn, L. (2001). Intimate relations--fact or fiction: An analysis of business to business relationships in Irish companies. Irish Journal of Management, 22(1), 55-71. Denzin, N. K., & Lincoln, Y. S. (1994). Handbook of Qualitative Research. Thousand Oaks, CA: Sage Publications. Dierickx, I., & Cool, K. (1989). Asset stock accumulation and sustainability of competitive advantage. Management Science, 35, 1504-1511. Doty, D. H., & Glick, W. H. (1994). Typologies as a unique form of theory building: Toward improved understanding and modeling. Academy of Management Review, 19(2), 230-251. Dubini, P., & Aldrich, H. (1991). Personal and extended networks are central to the entrepreneurial process. Journal of Business Venturing, 6(5), 305-313. Dyer, J. H., & Singh, H. (1998). The relational view: Cooperative strategy and sources of interorganizational competitive advantage. Academy of Management Review, 23(4), 660-679. Dyer, J. H., & Singh, H. (1999). On the relational view: Response to relational view commentary. Academy of Management Review, 24(2), 184-187. Eisenhardt, K. M. (1989). Building theories from case study research. Academy of Management Review, 14(4), 532-550. Emerson, R. M. (1976). Social exchange theory. Annual Review of Sociology, 2, 335-362. Erlandson, D. A., Harris, E. L., Skipper, B. L., & Allen, S. D. (1993). Doing naturalistic inquiry: A guide to methods (U. Recommended by Janeen Costa, Trans.). Newbury Park: Sage Publications. Feld, S. L. (1997). Structural embeddedness and stability of interpersonal relations. Social Networks, 19(1), 91-95. Fisher, M. (1997). Qualitative computing: Using software for qualitative data analysis. Aldershot, England: Ashgate. Glaser, B., & Strauss, A. (1967). The discovery of grounded theory: Strategies of qualitative research. London: Wiedenfeld and Nicholson. Gnyawali, D. R., & Madhavan, R. (2001). Cooperative networks and competitive dynamics: A structural embeddedness perspective. The Academy of Management Review, 26(3), 431-445. Good, D. (1988). Individuals, interpersonal relations and trust. In E. Gambetta (Ed.), Trust making and breaking cooperative relations (pp. 31-48). Cambridge, MA: Basil Blackwell. Gough, S., & Scott, W. (2000). Exploring the purposes of qualitative data coding in educational enquiry: Insights from recent research. Educational Studies, 26(3), 339-354. Granovetter, M. (1985). Economic action and social structure: The problem of embeddedness. American Journal of Sociology, 91(3), 481-510. Granovetter, M. (1992). Problems of explanation in economic sociology. In N. Nohria & R. Eccles (Eds.), Networks and Organizations (pp. 25-56). Boston: Harvard Business School Press. Granovetter, M. S. (1973). The strength of weak ties. American Journal of Sociology, 78(6), 1360-1380. Granovetter, M. S. (1982). The strength of weak ties: A network theory revisited. In P. V. Marsden & N. Lin (Eds.), Social structure and network analysis (pp. 105-130). Beverly Hills, CA: Sage. Gregersen, H. B., & Black, J. S. (1992). Antecedents to commitment to a parent company and a foreign operation. Academy of Management Journal, 35(1), 65-90. Guba, E. G., & Lincoln, Y. S. (1994). Competing paradigms in qualitative research. In N. K. Denzin & Y. S. Lincoln (Eds.), Handbook of qualitative research (pp. 105-117). Thousand Oaks, CA: Sage Publications. Gummesson, E. (1991). Qualitative methods in management research. Newbury Park, CA: Sage Publications. Hansen, E. L. (1995). Entrepreneurial networks and new organization growth. Entrepreneurship Theory and Practice, 19(4), 7-20. Hennart, J. F. (1993). Explaining the swollen middle: Why most transactions are a mix of market and hierarchy. Organization Science, 4(4), 529-547. Hesterly, W. S., Jones, C., & Madhok, A. (1998). Trust: A typology and its applications in economic exchange. Hite, J. M., & Hesterly, W. S. (2001). The evolution of firm networks: From emergence to early growth of the firm. Strategic Management Journal, 22. Homans, G. (1950). The human group. New York: Harcourt Brace. Huberman, A. M., & Miles, M. B. (1994). Data management and analysis methods. In N. K. Denzin & Y. S. Lincoln (Eds.), Handbook of qualitative research (pp. 428-444). Thousand Oaks, CA: Sage Publications. Jarillo, J. C. (1989). Entrepreneurship and growth: The strategic use of external resources. Journal of Business Venturing, 4(2), 133-147. Johannisson, B., & Monsted, M. (1998). Contextualizing entrepreneurial networking: A case of Scandinavia. International Studies of Management and Organization, 27(3), 109-136. Jones, C., Hesterly, W. S., & Borgatti, S. P. (1997). A general theory of network governance: Exchange conditions and social mechanisms. Academy of Management Review, 22(4), 911-945. Jones, G. R., & George, J. M. (1998). The experience and evolution of trust: Implications for cooperation and teamwork. Academy of Management Review, 23(3), 531-546. King, G., Keohane, R. O., & Verba, S. (1994). Designing social inquiry: Scientific inference in qualitative research. Princeton, NJ: Princeton University Press. Kirzner, I. M. (1973). Competition and entrepreneurship. Chicago: University of Chicago Press. Kirzner, I. M. (1997). Entrepreneurial discovery and the competitive market process: An Austrian approach. Journal of Economic Literature, 35, 60-85. Krackhardt, D. (1992). The strength of strong ties: The importance of Philos in organizations. In N. Nohria & R. G. Eccles (Eds.), Networks and organizations: Structure, form and action (pp. 216-239). Boston: Harvard Business School Press. Krackhardt, D. (1995). Entrepreneurial opportunities in an entrepreneurial firm: A structural approach. Entrepreneurship: Theory and Practice, 19(3), 52-69. Langley, A. (1999). Strategies for theorizing from process data. Academy of Management Review, 24(4), 691-710. Larson, A. L. (1992). Network dyads in entrepreneurial settings: A study of the governance of exchange relationships. Administrative Science Quarterly, 37, 76-103. Larson, A. L., & Starr, J. A. (1993). A network model of organization formation. Entrepreneurship: Theory and Practice, 17(2), 5-15. Lincoln, Y., & Guba, E. (1985). Naturalistic inquiry. Beverly Hills, CA: SAGE Publications. Macaulay, S. (1963). Non-contractual relations in business: A preliminary study. American Sociological Review, 28(1), 55-69. MacLean, T. L. (2001). Thick as thieves: A social embeddedness model of rule breaking in organizations. Business and Society, 40(2), 167-196. Macneil, I. (1978). Contracts: Adjustment of long-term economic relations under classical, neo-classical and relational contract law. Northwestern University Law Review, 72, 854-906. MacQueen, K. M., McLellan, E., Kay, K., & Milstein, B. (1998). Codebook development for team-based qualitative analysis. Cultural Anthropology Methods, 10(2), 31-36. Madhok, A. (1997). Cost, value and foreign market entry mode: The transaction and the firm. Strategic Management Journal, 18(1), 39-61. Marsden, Peter V. (1981). Introducing influence processes into a system of collective decisions. American Journal of Sociology, 86, 1203-1235. McKelvey, B., & Aldrich, H. (1983). Populations, natural selection and applied organizational science. Administrative Science Quarterly, 28(2), 101-128. Miles, M. B., & Huberman, A. M. (1994). Qualitative data analysis: An expanded sourcebook (2 ed.). Newbury Park, CA: Sage. Mizruchi, M. S. (1994). Social network analysis: Recent achievements and current controversies. Acta Sociologica, 37(4), 37-52. Nahapiet, J., & Ghoshal, S. (1998). Social capital, intellectual capital, and the organizational advantage. Academy of Management Review, 23(2), 242-266. NVivo. (Version N5)(2000). Vic, Australia: QSR International Pty. Ltd. Peteraf, M. A. (1993). The cornerstones of competitive advantage: A resource-based view. Strategic Management Journal, 14, 179-192. Poppo, L., & Zenger, T. (2000, March 4, 2000). Substitutes or complements? Exploring the relationship between formal contracts and relational governance. Paper presented at the BYU Winter Strategy Conference, Brigham Young University, Provo, UT. Portes, A., & Sensenbrenner, J. (1993). Embeddedness and immigration: Notes on the social determinants of economic action. American Journal of Sociology, 98(6), 1320-1350. Powell, W. W. (1987). Hybrid organizational arrangements: New forms or transitional development. California Management Review, 30(1), 67-98. Powell, W. W. (1990). Neither market nor hierarchy: Network forms of organization. Research in Organizational Behavior, 12, 295-336. Powell, W. W., & Smith-Doerr, L. (1994). Networks and economic life. In N. J. Smelser & R. Swedberg (Eds.), The handbook of economic sociology (pp. 368-402). Princeton, NJ: Princeton University Press. Provan, K. G. (1993). Embeddedness, interdependence, opportunism in organizational supplier-buyer networks. Journal of Management, 19(4), 841-857. Reese, P. R., & Aldrich, H. E. (1995). Entrepreneurial networks and business performance. In S. Birley & I. C. MacMillan (Eds.), International entrepreneurship (pp. 124-144). London: Routledge. Richards, T. J., & Richards, L. (1994). Using computers in qualitative research. In N. K. Denzin & Y. S. Lincoln (Eds.), Handbook of qualitative research (pp. 445-462). Thousand Oaks, CA: Sage Publications. Ring, P., & Van de Ven, A. (1989). Formal and informal dimensions of transactions. In A. Van de Ven & H. Angle & R. S. Poole (Eds.), Research on the management of the innovation (pp. 171-192). Cambridge, MA: Ballinger Press. Robinson, V. M. J. (1993). Problem based methodology: Research for the improvement of practice. Oxford: Pergamon. Romanelli, E. (1989). Environments and strategies of organization start-up: Effects on early survival. Administrative Science Quarterly, 34, 369-387. Rowley, T., Behrens, D., & Krackhardt, D. (1999). Redundant governance structures: An analysis of structural and relational embeddedness in the steel and semiconductor industries. Paper presented at the Strategic Management Journal, Northwestern University, Evanston, IL. Rowley, T., Behrens, D., & Krackhardt, D. (2000). Redundant governance structures: An analysis of structural and relational embeddedness in the steel and semiconductor industries. Strategic Management Journal, 21(3), 369-386. Saxenian, A. (1990). Regional networks and the resurgence of silicon valley. California Management Review, 33(1), 89-111. Schein, E. H. (1987). The clinical perspective in fieldwork (Vol. 5). London: Sage Publications. Shan, W., Walker, G., & Kogut, B. (1994). Interfirm cooperation and startup innovation in the biotechnology industry. Strategic Management Journal, 15, 387-394. Shimizu, K., & Dacin, T. (1998). Social capital dynamics: A multi-level, embeddedness perspective. Paper presented at the Academy of Management Annual Meeting. Shuman, J. C., & Buono, A. (1992). Network organizations and venture creation: A case study of Model American Computer Corporation. Frontiers of Entrepreneurship Research, 303-317. Siegel, R., Siegel, E., & MacMillan, I. C. (1993). Characteristics distinguishing high-growth ventures. Journal of Business Venturing, 8(2), 169-180. Staber, U. (1994). Friends, acquaintances, strangers: Gender differences in the structure of entrepreneurial networks. Journal of Small Business and Entrepreneurship, 11(1), 73-82. Staber, U., & Aldrich, H. E. (1995). Cross-national similarities in the personal networks of small business owners: A comparison of two regions in North America. Canadian Journal of Sociology, 20(4), 441-467. Starr, J. A., & MacMillan, I. C. (1990). Resource cooptation via social contracting: Resource acquisition strategies for new ventures. Strategic Management Journal, 11, 79-92. Steier, L., & Greenwood, R. (1998, May 21-23, 1998). The evolution of "angel" networks. Paper presented at the Babson Entrepreneurial Conference, Gent, Belgium, May 20-23, 1998. Strauss, A. L., & Corbin, J. (1990). Basics of qualitative research: Grounded theory procedures and techniques (1st ed.). Newbury Park, CA: Sage Publishing. Strauss, A. L., & Corbin, J. (1994). Grounded theory methodology. In N. K. Denzin & Y. S. Lincoln (Eds.), Handbook of qualitative research (pp. 273-285). Thousand Oaks, CA: Sage Publications. Ulrich, D., & McKelvey, B. (1990). General organizational classification: An empirical test using the United States and Japanese electronics industries. Organization Science, 1(1), 99-118. Uzzi, B. (1996). The sources and consequences of embeddedness for the economic performance of organizations: The network effect. American Sociological Review, 61, 674-698. Uzzi, B. (1997). Social structure and competition in interfirm networks: The paradox of embeddedness. Administrative Science Quarterly, 42, 35-67. Uzzi, B. (1999). Embeddedness in the making of financial capital: How social relations and networks benefit firms seeking financing. American Sociological Review, 64(4), 481-505. Van de Ven, A. H. (1993). The development of an infrastructure for entrepreneurship. Journal of Business Venturing, 8(3), 211-230. Weick, K. E. (1979). The social psychology of organizing (2nd ed.). New York: McGraw-Hill, Inc. Wernerfelt, B. (1995). The resource-based view of the firm: Ten years after. Strategic Management Journal, 16(3), 171-174. Williamson, O. (Ed.). (1994). The economics and sociology of organization: Promoting a dialogue. New York: Plenum Press. Williamson, O. E. (1985). The economic institutions of capitalism. New York: The Free Press. Yin, R. K. (1994a). Case study research: Design and methods. Thousand Oaks, CA: Sage Publications. Yin, R. K. (1994b). Evaluation: A singular craft. In C. S. Reichardt & S. F. Rallis (Eds.), The qualitativequantitative debate: New perspectives (pp. 71-84). San Francisco, CA: Jossey-Bass. Zaheer, A., McEvily, B., & Perrone, V. (1998). Does trust matter? Exploring the effects of interorganizational and interpersonal trust on performance. Organization Science, 9(2), 141-159. Zaheer, A., & Venkataraman, S. (1995). Relational governance as an interorganizational strategy: An empirical test of the rate of trust in economic exchange. Strategic Management Journal, 16, 373-392. Zhao, L., & Aram, J. D. (1995). Networking and growth of young technology-intensive ventures in China. Journal of Business Venturing, 10(5), 349-370. Zucker, L. G. (1986). Production of trust: Institutional sources of economic structure, 1840-1920. In B. M. Staw & L. L. Cummings (Eds.), Research in organizational behavior (Vol. 8, pp. 53-111). Greenwich, CT: JAI Press. Zukin, S., & DiMaggio, P. (1990). Structures of capital: The social organization of the economy. New York: Cambridge University Press. AUTHOR BIO Julie Melville Hite is an Assistant Professor in Educational Leadership at Brigham Young University (julie_hite@byu.edu). Her current research focuses on the structure and evolution of internal and external strategic networks as well as their role on resource acquisition, innovation and leadership in educational organizations. A current study examines the role of network structure and content on the resource acquisition of private secondary school headmasters in Uganda. She has previously published in Strategic Management Journal (SMJ), Journal of International Business Studies (JIBS) and Best Paper Proceedings for the Academy of Management. She received her Ph.D. in Strategic Management from the University of Utah. ENDNOTES: For emerging firms, the social network of the entrepreneur is virtually synonymous with the firm’s network, as network ties initially exist on the interpersonal level (Bhide, 2000; Hite & Hesterly, 2001; Zaheer, McEvily, & Perrone, 1998). 1 2 In addition to relational embeddedness, the broader concept of embeddedness encompasses at least five additional theoretical perspectives on the potential sources of influence and constraint on the firm. First, structural embeddedness refers to the “extent of overlap of social relations between two individuals” (Feld, 1997, p. 91) and the architecture of this ongoing social structure (Marsden, 1981; Zukin & DiMaggio, 1990). Second, cognitive embeddedness refers to the routinization and structure of mental models and processes that direct economic logic (e.g. Shimizu & Dacin, 1998; Zukin & DiMaggio, 1990). Third, cultural embeddedness suggests that shared beliefs and values shape economic aims and actions (Zukin & DiMaggio, 1990). Fourth, political embeddedness focuses attention toward how “economic institutions and decisions are shaped by a struggle for power that involves economic actors and nonmarket institutions” (Zukin & DiMaggio, 1990, p. 20). Finally, institutional embeddedness posits that the firm is embedded within a larger institutional environment that provides legitimating effects for both growth and survival (Baum & Oliver, 1992). 3 Although license dates often lag behind the start of operations, economic research (Bruderl, Preisendorfer, & Ziegler, 1992; Uzzi, 1996) uses license registration dates to determine organizational age; thus the working definition of organizational age equals the number of months the firm has been in business based on the firm’s business license date. 4 References to direct quotations from interview text indicate the case number and network tie number followed by the test line. For example, (5-8:623) refers to a quotation from Case #5 regarding the 8 th network tie and can be found on text line 623.