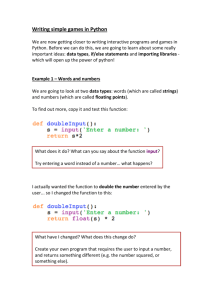
Faculty of Computer Studies Information Technology and Computing
advertisement

Arab Open University- Lebanon
Faculty of Computer Studies
Information Technology and Computing
Department
NetSec
Bilal M. Issa 008156
Nadim H. Al-Awar 007397
T471: Final Year Project, May 2010
Supervisor:
Dr. Nouhad Amaneddine
1
Table of Contents
Table of Contents
Chapter 1: Introduction........................................................................................................3
1.1 Purpose......................................................................................................................3
1.2 Scope.........................................................................................................................3
1.3 Network Security Overview......................................................................................4
1.3.1 Network Security Views....................................................................................4
1.3.2 How Secure Are You?.......................................................................................5
1.3.3 Types of Network Attacks.................................................................................5
Chapter 2: Background Information....................................................................................7
2.1 Why Linux?...............................................................................................................7
2.2 Why Python?.............................................................................................................9
Chapter 3: NetSec..............................................................................................................12
3.1 NetSec SDLC(Software Development Life Cycle)................................................12
3.2 Port Scanning..........................................................................................................16
3.2.1 NetSec Port Scanner .......................................................................................18
3.2.1.1 Design......................................................................................................18
3.2.1.2 Implementation........................................................................................20
3.3 Network Scanning...................................................................................................24
3.3.1 OS FingerPrinting............................................................................................25
3.3.2 NetSec Network Scanner.................................................................................25
3.3.2.1 Design......................................................................................................27
3.3.2.2 Implementation........................................................................................29
3.4 Vulnerability Checking and Analysis.....................................................................31
3.4.1 Vulnerability Assessment................................................................................31
3.4.2 Types of Vulnerability Assessment.................................................................32
3.4.3 Assessment Phase............................................................................................34
3.4.4 Vulnerability Analysis Stages.........................................................................36
3.4.5 Vulnerability Report Model............................................................................37
3.4.6 NetSec Vulnerability Checking.......................................................................38
3.5 Testing.....................................................................................................................39
Chapter 4: Exploits And Securing Your Code In Network Programming........................41
4.1 Exploits...................................................................................................................41
4.2 Half-Open Sockets..................................................................................................42
Chapter 5: Conclusion........................................................................................................43
5.1 Learning Outcomes.................................................................................................43
5.2 Summary.................................................................................................................44
5.3 Future Extenstion....................................................................................................44
Chapter 6: References........................................................................................................44
Appendix A........................................................................................................................46
2
Chapter 1: Introduction
With an average of 310 new operating systems and application vulnerabilities announced
each and every month the need to do active network scanning is essential. An automated,
ongoing vulnerability assessment and management solution is your best option for the
assessment and management of corporate network vulnerabilities. Organizations now
need proactive network scanning to keep up with internal changes and external
developments, which is required up to daily frequency due to the increasing complexity
of vulnerabilities and the speed at which they can now be exploited, and should be
performed as a specialized service. With the increasing complexity of networks, the
number of vulnerabilities being discovered daily, the speed at which exploits can launch
malicious code and the ease of installation of rogue devices, performing vulnerability and
network security assessments annually, biannually or even quarterly is no longer a viable
risk mitigation strategy. Similarly, the challenge of staying up to date with the current
vulnerabilities is now a specialist task. It should now be assigned to a dedicated solution.
1.1 Purpose
When you're planning to launch your business, security must be your primary concern.
But in today's computing environments, network security is a horrible game of numbers.
Consider the facts: Hundreds of new vulnerabilities are being discovered annually,
dozens of new patches are being released monthly, and thousands of networks are already
behind the security eight ball. Compounding matters, when opening your perimeter for
consumers and business partners, network-level security becomes even more critical as it
forces an increase in exposure points. Make no mistake, the odds are not in your favor
you have to patch every hole, but an attacker need find only one to get into your
environment. Attack tools are getting more user friendly, more automated. Tools that
automate the vulnerability discovery process. Tools that help you secure your systems.
Tools that give the administrator the edge. While Intrusion Detection and Prevention
Systems still play an important role, doing an active network scanning on your internal
network for the latest vulnerabilities every day or even every hour, brings your network
protection to a new level. NetSec will be the ultimate must-have toolkit that provides all
essential utilities for Information Systems specialists, system administrators, Network
Security Officers or individuals.
1.2 Scope
Our project basically is an advanced network IP/PORT scanner along with an integrated
tool to perform WEB server scanner which performs comprehensive tests against web
servers for multiple items, including over 6100 potentially dangerous files/CGIs, checks
for outdated versions of over 950 servers, and version specific problems on over 260
servers. It also checks for server configuration items such as the presence of multiple
index files, HTTP server options, and will attempt to identify installed web servers and
3
software. NetSec will map your alive hosts on the network, scan the available open ports
on the servers inside your network and will try to identify vulnerabilities over a WEB
server. NetSec will NOT attempt to fix your security holes; it will only give back reports
and recommendations based on the analysis. The main goal behind this project is to
handle Network Security Officers a system that is capable of helping and guiding them
towards security breaches inside their network. NetSec will be an abbreviation for
Network Security.
1.3 Network Security Overview
If you were to talk with someone whose job it is to implement network security, you
would hear a lot about buffer overflows, vendor patches, denial of service attacks, and so
on. But network security is much broader than the details of attacks and defenses against
them. A good network security scheme begins at the top of an organization, with
extensive planning to determine where the organization should be concentrating its
security efforts and money.
Network security is a very broad term. In its fullest sense, it means protecting data that
are stored on or that travel over a network against both accidental and intentional
unauthorized disclosure or modification. The most often overlooked part of this definition
is that it includes accidental occurrences, such as an inadequately debugged application
program that damages data.
Many people view network security as having three goals:
•
Confidentiality: Ensuring that data that must be kept private, stay private.
•
Integrity: Ensuring that data are accurate. For a security professional, this
means that data must be protected from unauthorized modification and/or
destruction.
•
Availability: Ensuring that data are accessible whenever needed by the
organization. This implies protecting the network from anything that would
make it unavailable, including such events as power outages.
1.3.1 Network Security Views
The popular media would have you believe that the cause of most network security
problems is the “hacker.” However, if you ask people actually working in the field, they
will tell you that nearly half the security breaches they encounter come from sources
internal to an organization, and, in particular, employees. This means that it won’t be
sufficient to secure a network against external intrusion attempts; you must pay as much
attention to what is occurring within your organization as you do to external threats.
4
1.3.2 How Secure Are You?
Probably the most important thing to realize before you start developing a security
scheme for an organization is that you can never be 100 percent secure. There will always
be someone who can find a way into your system, either from the inside or outside.
Therefore, instead of setting a goal of making the system totally uncrackable, you want to
ensure that you make it as secure as you can for a reasonable amount of money.
The trick is to balance security risk with the amount of money you are going to spend.
For example, let’s say that you can make your network 80 percent secure for $125,000.
To make it 90 percent secure, you must spend $200,000. Is the extra 10 percent security
worth another $75,000 to your organization? The answer depends on the amount of risk
that you are willing to tolerate. The point at which additional security becomes more
expensive than it is worth can be determined only by each organization.
You also need to evaluate your security measures in a practical sense. From a security
point of view, for example, it would be great to require 12-character passwords that were
to be changed every day. But that simply isn’t practical for users. They won’t be able to
remember their passwords and will either resort to writing them down (and leaving them
in easily accessible places) or choosing passwords that are easy to guess. Therefore, such
a rule isn’t workable and shouldn’t be part of your security plan. For each security
measure that you adopt, you need to ask yourself whether it is practically feasible and
whether, given a reasonable amount of training, technical staff and users will be able and
likely to adhere to the requirements.
1.3.3 Types of Network Attacks
Securing the code is important; however it is also important to understand the common
vulnerabilities that lead to the exploitation of program functionality and data alike. Many
of these attacks have something in common: Someone who isn’t necessarily physically
present at either end of the communication can carry them out.
As traffic travels across the internet, it may pass through a dozen or more different
networks. Each network is controlled by a different company, and isn’t necessarily
trustworthy. Networks that are physically near a client or a server, such as the LAN at a
workplace or university, may also be vulnerable to attacks by disgruntled staff or
students. Certain broadband services, especially cable modems and wireless internet
access, have been notorious for exposing network traffic to anyone.
Even if all the networks are trusted, outside attackers can sometimes find ways to breach
security and divert or intercept connections. Here are some of the ways that outside (or
inside) attackers can cause security problems. Many of the attacks are known as man-inthe-middle (MITM) attacks, since the attacker would normally reside on a network
somewhere between the client computer and the remote one.
Sniffing:
Sniffing occurs when an outsider is able to read network traffic as it travels to its
destination. A sniffer doesn’t modify the traffic or interrupt it; you’ll generally have no
idea that any sort of security breach is occurring.
5
Traffic sniffing allows an attacker to carry out illicit activities such as stealing passwords
and credit card numbers, reading e-mail, and essentially watching every network-oriented
task you carry out. Once these resources are obtained, they can be exploited to cause
more damage. For instance, someone in possession of a stolen password could use it to
access systems and order merchandise on someone else’s account, or use it to read mail
or attempt to gather other passwords.
Even if you take precautions and never use your credit card number or send a password
unless a site is secure, sniffers can still gather information. For instance, if they monitor
your web-browsing traffic, they could discover what collage you attend (from the visits to
the websites that are most frequent), what your interests are, and what shopping online
stores you visit. From that, they may attempt to breach security, and sniffing is probably
the most common type of attack.
Insertion Attacks:
An insertion attack occurs when someone adds unwanted data to a network stream.
Consider, for instance, an application such as FTP that has access to files on a remote
system. Once the client is logged on, an attacker with control of some network between
the client and the server could insert a command to delete files from the server, even if
the attacker ha no knowledge of the password.
Deletion Attacks:
A deletion Attack is similar to the insertion attack, except this one removes information
from the network stream rather than adding. For instance, if the administrator sent a
command “rm *.txt” to a UNIX machine, intending to delete all text files, someone
attempting a deletion attack may be able to delete the .txt part, leaving just “rm *” where
this command results in deleting all files, not just text files. Deletion attacks aren’t
frequently seen, but remain a matter of concern.
Replay Attacks:
A replay attack occurs when someone has been sniffing network traffic and later replays
it. This is one reason why a simple password-based encryption scheme isn’t a good idea.
Consider, for instance, what happens if you log on to an FTP server and issue a command
to delete all files. A sniffer may be able to capture all that traffic. But perhaps the sniffer
is unable to get passwords from that capture, maybe the communication was encrypted.
However, if the attacker wishes to harm you, he might wait a few days and then connect
back to the server. Even though your password isn’t known, the encrypted traffic could
be sent back, and the command to delete all the files on the FTP server will be issued
again, resulting in deleting the files on the FTP server.
Session Hijacking:
Session hijacking occurs when you have opened up a connection to a remote service, but
while that connection is still open, an attacker is able to impersonate you wile
communicating with the remote server. This is similar to an insertion or deletion attack.
With session hijacking, the attacker will completely take over your session, effectively
6
impersonating you. The attacker will then be able to run any command you could, and
see any data you would be able to see.
Fake Server (Traffic Redirection):
An attacker could sometimes set up a server that mimics real one. For instance, if you
attempt to visit your bank’s website, an attacker may set up a fake website that looks like
your bank’s website. Then the attacker may be able to redirect your network traffic away
from the real website to the fake one. You may have no idea that you are not
communicating with the real bank until you have already supplied your password. Then
the attacker can use the stolen password to access the real bank’s website.
Chapter 2: Background Information
In this chapter we will talk about what are the reasons behind choosing linux as a
development environment and a host operating system, along with Python for
development of the project.
2.1 Why Linux?
If your computer shuts itself down without asking you, if strange windows with text you
don't understand and all kinds of advertisements appear when you don't ask for them, if
emails get sent to all your contacts without your knowing it, then your computer probably
has a virus. The main reason for this is because it runs Windows.
Linux hardly has any viruses. And that's not like "Oh well, not very often, you know".
Of course, a Linux virus is not impossible to get. However, Linux makes it very hard for
this to happen, for several reasons:
• Most people use Microsoft Windows, and pirates want to do as much damage (or
control) as possible: therefore, they target Windows. But that's not the only
reason; the Apache web server (a web server is a program located on a remote
computer that sends web pages to your browser when you ask for them), which is
open source software, has the biggest market share (against Microsoft's IIS
server), but it still suffers from much fewer attacks/flaws than the Microsoft one.
• Linux uses smart authorization management. In Windows you (and any program
you install) usually have the right to do pretty much anything to the system. If you
feel like punishing your PC because it just let your precious work disappear, you
can go inside the system folder and delete whatever you want: Windows won't
complain. Of course, the next time you reboot, trouble begins. But imagine that if
you can delete this system stuff, other programs can, too, or just mess it up. Linux
doesn't allow that. Every time you request to do something that has to do with the
system, an administrator password is required (and if you're not an administrator
on this system, you simply can't do it). Viruses can't just go around and delete or
modify what they want in the system; they don't have the authorization for that.
7
•
More eyes make fewer security flaws. Linux is Open source software, which
means that any programmer in the world can have a look at the code (the "recipe"
of any program), and help out, or just tell other developers.
Moreover, have you ever lost your precious work because Windows crashed? Do you
always shut down your computer the proper way, or do you sometimes just switch it off
because Windows has gone crazy and doesn't let you do anything anymore? Have you
ever gotten the "blue screen of death" or error messages telling you that the computer
needs to be shut down for obscure reasons?
The latest versions of Windows, especially the "Professional" ones are becoming more
stable than before. Nevertheless this kind of problem still happens fairly often.
Of course, no operating system is perfect, and people who tell you that theirs can never
ever crash are lying. However, some operating systems can be so stable that most users
never see their systems crash, even after several years. This is true for Linux. Here's a
good way to see this. When a system crashes, it needs to be shut down or restarted.
Therefore, if your computer can stay up and running for a long time, no matter how much
you use it, then you can say the system is stable. Well, Linux can run for years without
needing to be restarted (most internet servers run Linux, and they usually never restart).
Of course, with heavy updates, it still needs to be restarted (the proper way). But if you
install Linux, and then use your system as much as you want, leaving your computer on
all the time, you can go on like that for years without having any trouble.
Most of the time, you won't leave your computer on for such a long time, but this shows
how stable Linux is.
One main reason that makes the computer slower is fragmented files, and you probably
use windows defragmenter once every month, well if you were a linux user, you probably
didn’t worry for defragmenting, simply because linux doesn't need defragmenting.
How come linux doesn’t need defragmenting?
Imagine your hard disk is a huge file cabinet, with millions of drawers. Each drawer can
only contain a fixed amount of data. Therefore, files that are larger than what such a
drawer can contain need to be split up. Some files are so large that they need thousands of
drawers. And of course, accessing these files is much easier when the drawers they
occupy are close to one another in the file cabinet.
Now imagine you're the owner of this file cabinet, but you don't have time to take care of
it, and you want to hire someone to take care of it for you. Two people come for the job,
a woman and a man.
• The man has the following strategy: he just empties the drawers when a file is
removed, splits up any new file into smaller pieces the size of a drawer, and
randomly stuffs each piece into the first available empty drawer. When you
mention that this makes it rather difficult to find all the pieces of a particular file,
8
•
the response is that a dozen boys must be hired every weekend to put the chest
back in order.
The woman has a different technique: she keeps track, on a piece of paper, of
contiguous empty drawers. When a new file arrives, she searches this list for a
sufficiently long row of empty drawers, and this is where the file is placed. In this
way, provided there is enough activity, the file cabinet is always tidy.
Without a doubt, you should hire the woman (you should have known it, women are
much better organized) .Well, Windows uses the first method; Linux uses the second one.
The more you use Windows, the slower it is to access files; the more you use Linux, the
faster it is.
More and more reasons why using linux instead of Microsoft, so why one have to pay in
order to be unstable and vulnerable to viruses and threats, when one can purchase
stability and security for free.
2.2 Why Python?
Python is a general-purpose programming language that is often applied in scripting
roles. It is commonly defined as an object-oriented scripting language—a definition that
blends support for OOP with an overall orientation toward scripting roles. It is open
source and free.
Because there are many programming languages available today, this is the usual first
question “What is the most suitable language I can use?” Given that there are roughly 1
million Python users out there at the moment, there really is no way to answer this
question with complete accuracy; the choice of development tools is sometimes based on
unique constraints or personal preference.
But for python, the primary factors cited by Python users seem to be these:
Software quality:
For many, Python’s focus on readability, coherence, and software quality in general sets
it apart from other tools in the scripting world. Python code is designed to be readable,
and hence reusable and maintainable—much more so than traditional scripting languages.
The uniformity of Python code makes it easy to understand, even if you did not write it.
In addition, Python has deep support for more advanced software reuse mechanisms, such
as object-oriented programming (OOP).
Developer productivity:
Python boosts developer productivity many times beyond compiled or statically typed
languages such as C, C++, and Java. Python code is typically one-third to one-fifth the
size of equivalent C++ or Java code. That means there is less to type, less to debug, and
9
less to maintain after the fact. Python programs also run immediately, without the lengthy
compile and link steps required by some other tools, further boosting programmer speed.
Program portability:
Most Python programs run unchanged on all major computer platforms. Porting Python
code between Linux and Windows, for example, is usually just a matter of copying a
script’s code between machines. Moreover, Python offers multiple options for coding
portable graphical user interfaces, database access programs, web-based systems, and
more. Even operating system interfaces, including program launches and directory
processing, are as portable in Python as they can possibly be.
Support libraries:
Python comes with a large collection of prebuilt and portable functionality, known as the
standard library. This library supports an array of application-level programming tasks,
from text pattern matching to network scripting. In addition, Python can be extended with
both homegrown libraries and a vast collection of third-party application support
software. Python’s third-party domain offers tools for website construction, numeric
programming, serial port access, game development, and much more. The NumPy
extension, for instance, has been described as a free and more powerful equivalent to the
Matlab numeric programming system.
Component integration:
Python scripts can easily communicate with other parts of an application, using a variety
of integration mechanisms. Such integrations allow Python to be used as a product
customization and extension tool. Today, Python code can invoke C and C++ libraries,
can be called from C and C++ programs, can integrate with Java and .NET components,
can communicate over frameworks such as COM, can interface with devices over serial
ports, and can interact over networks with interfaces like SOAP, XML-RPC, and
CORBA. It is not a standalone tool.
Dynamic typing:
Python keeps track of the kinds of objects your program uses when it runs; it doesn’t
require complicated type and size declarations in your code. There is no such thing as a
type or variable declaration anywhere in Python. Because Python code does not constrain
data types, it is also usually automatically applicable to a whole range of objects.
Automatic memory management:
Python automatically allocates objects and reclaims (“garbage collects”) them when they
are no longer used and most can grow and shrink on demand. Python keeps track of lowlevel memory details so you don’t have to.
Programming-in-the-large support:
10
For building larger systems, Python includes tools such as modules, classes, and
exceptions. These tools allow you to organize systems into components, use OOP to
reuse and customize code, and handle events and errors gracefully.
Built-in object types:
Python provides commonly used data structures such as lists, dictionaries, and strings as
intrinsic parts of the language; as you’ll see, they’re both flexible and easy to use. For
instance, built-in objects can grow and shrink on demand, can be arbitrarily nested to
represent complex information, and more.
Moreover, Python is also being applied in real revenue-generating products by real
companies. For instance:
• Google makes extensive use of Python in its web search systems, and employs Python’s
creator.
• The YouTube video sharing service is largely written in Python.
• The popular BitTorrent peer-to-peer file sharing system is a Python program.
• Google’s popular App Engine web development framework uses Python as its
application language.
• EVE Online, a Massively Multiplayer Online Game (MMOG), makes extensive use of
Python.
• Maya, a powerful integrated 3D modeling and animation system, provides a Python
scripting API.
• Intel, Cisco, Hewlett-Packard, Seagate, Qualcomm, and IBM use Python for hardware
testing.
• Industrial Light & Magic, Pixar, and others use Python in the production of animated
movies.
• JPMorgan Chase, UBS, Getco, and Citadel apply Python for financial market
forecasting.
• NASA, Los Alamos, Fermilab, JPL, and others use Python for scientific programming
tasks.
• iRobot uses Python to develop commercial robotic devices.
• ESRI uses Python as an end-user customization tool for its popular GIS mapping
products.
• The NSA uses Python for cryptography and intelligence analysis.
• The IronPort email server product uses more than 1 million lines of Python code to do
its job.
• The One Laptop Per Child (OLPC) project builds its user interface and activity model in
Python.
And so on. Probably the only common thread amongst the companies using Python today
is that Python is used all over the map, in terms of application domains. Its generalpurpose nature makes it applicable to almost all fields, not just one. In fact, it’s safe to
say that virtually every substantial organization writing software is using Python, whether
11
for short-term tactical tasks, such as testing and administration, or for long-term strategic
product development. Python has proven to work well in both modes.
Chapter 3: NetSec
In this chapter we will state how was the development process done, stating the designs
used, implementation decisions and the testing of the system.
Scanning is one of the most important phases of intelligence gathering for a security
officer. In the process of scanning, the security officer tries to gather information about
the specific IP addresses that can be accesses over the LAN, their operating systems,
system architecture, and the services running on each computer.
The idea is to discover exploitable communication channels to probe as many listeners as
possible and keep track of the ones that are responsive or useful to an attacker’s particular
needs. In the scanning phase the security officer tries to find various ways to intrude into
the target system. The security officer also tries to discover more about the target system
by finding out what operating system is used, what services are running and whether or
not here are any configuration lapses in the target system. Based on the facts that the
security officer gathers, he/she tries to form a strategy to defend the network from a likely
to happen attack. The various types of scanning is as follows:
• Port Scanning – Open ports and services
• Network Scanning – IP addresses
• Vulnerability Scanning – Presence of known weaknesses
In a traditional sense, the access points that a thief looks for are the doors and windows.
These are usually the house’s points of vulnerability because of their relatively easy
accessibility. When it comes to computer systems and networks ports are the doors and
windows of the system that an intruder uses to gain access. The more ports that are open,
the more points of vulnerability there are, and the fewer ports that are open, the more
secure the system is. This is simply a general rule. There could be cases where a system
has fewer ports open than another machine, but the ports that are open might present a
much higher level of vulnerability.
3.1 NetSec SDLC(Software Development Life Cycle)
What is Software Development Life Cycle (SDLC):
The SDLC model is a framework that describes the activities performed at each stage of a
software development project.
There are many types of SDLC models; however we chose the waterfall model in our
approach for the development phase.
Why choosing the waterfall software development life cycle:
12
First, we chose a topic for the project, and we had a clear view about the requirements of
our project. Also, we developed a good knowledge of the topic, so we thought of what
software development life cycle best applies for our project. After doing some research of
the advantages and disadvantages of each model, like Waterfall model, Structured
Evolutionary Prototyping model, Rapid Application Development model, Incremental
Software development life cycle…
We chose to use the waterfall model
The waterfall model (Fig.1):
It includes:
• Requirements: defines needed information, function, behavior, performance and
interfaces
• Design: data structures, software architecture like use case, flow charts (Fig.1),
sequence diagrams, class diagrams...
• Implementation: implementing the designs that are made in the design stage.
• Testing: testing the code written in the implementation stage, and reviewing the
code.
In the requirements stage, we proposed the requirements of the project, and they were
very clear, also we developed good knowledge in the chosen topic, so we had a clear
view of what to be done and what to do.
In the design Stage, we started designs for the whole system, we did a scenario for the
project and it was represented by use cases. Also we made flow charts for it, class
diagram for the project, i.e. we modeled all the project requirements in a design for it to
be easy for us to move to the next stage that was the implementation
In the implementation stage, we divided the implementation into modules; each module
fulfilled a certain requirement, for example: the ip scanner is a module and the port
scanner is a module… i.e. each task in the project is a separate module. However, we
applied the waterfall SDLC in the implementation, i.e. we finished each module
separately and tested it, and this helped us in validating the requirements.
The testing stage, we tested each module separately after finishing each one, and since
they are independent somehow from each other, this made the integration between these
modules easy, and the testing was successful when combined together, i.e. there was no
problem and no conflict between the ip scanner module and the port scanner module,
because they operate separately from each other, and each one can do its task without
waiting results from the other, although there is logical order for the project ( the ip
scanner should work before the port scanner in order to get the ip addresses in the
network) but the port scanner can run even if you don’t run the ip scanner, this is the case
when you already know the ip address of the machine and you want to port scan it. Also,
this applies to the check vulnerability module.
Advantages of the waterfall model:
• Easy to understand and use
• well structured, making it easy to follow up the software cycle
13
•
•
•
All requirements are well known, and easily identified
Stability of the requirements
Good for management control (plan, staff, track)
Disadvantages of the waterfall model:
• All requirements must be well known upfront
• Deliverables created for each phase are considered frozen, i.e. lack of flexibility
• Can give a false impression of progress, i.e. it takes time longer than other
development cycle models.
• No iteration between stages, i.e. after finishing each stage, the development
moves to the other stage without getting back to the previous stage.
• Integration is on big bang at the end, i.e. after finishing all the tasks or modules
separately the integration is done all by a time, and this may cause conflicts when
joining all the tasks together at a time.
When to use the waterfall software development life cycle:
• Requirements are well known
• Product definition is stable
• Technology is understood
• New version of an existing product
• porting an existing product into a new platform.
Fig.1 Waterfall model Software development life cycle
14
Schedule of the Project:
Task
Researching
Modeling/ designing
Development
Modules 1-2 -3…
Testing
Description
• Searching for a
project topic
• Searching for
Similar projects
• Adding new
functionalities
• Backup our project
with technical
documents
• Creating an initial
system functionality
design
• Searching for
suitable
programming
language
• Searching for an
IDE
• getting resources for
the programming
language
• Dividing the project
into modules
• Researching about
each module, in its
detailed
specifications,
designing and
implementation
• Modeling and
designing each
module using UML
• Implementing and
coding the modules
• Testing each module
separately
• Testing all the
modules joined
together
15
Estimated Time
3 weeks
2 weeks
2 weeks
19 weeks
4 weeks
Report
•
testing integration
issues
•
•
Writing the report
Designing the Poster
5 weeks
3.2 Port Scanning
Port scanning is checking the services running on the target computer by sending a
sequence of messages in an attempt to break in. Port scanning involves connecting to
TCP and UDP ports on the target system to determine if the services are running or in a
listening state. The listening state gives an idea of the operating system and the
application in use. Sometimes active services that are listening may allow unauthorized
user access to systems that are miss configured or running software that has
vulnerabilities.
Port scanning is used to discover which ports are open, Based on the open ports the
security officer will determine what access controls shall be used to defend the target
system, it is also used to discover the services running/listening on the target system. This
gives the security officer an indication of any vulnerability (based on the service) that can
be exploited to gain access into the target system.
There are three types of responses a port scanner can get when scanning your machine for
given ports. The first situation is when 'open ports' are being found. These ports are in
stand by mode, waiting for incoming connections; whenever such connections are
detected, an open port responds by accepting the connection and then data can be
transferred in between the local and remote computer. This also means that the computer
with open ports acts as server, while the machine connecting to it acts as client. An open
port is like a gateway for attackers, allowing them to get into your computer; it is
therefore recommended to block as many ports as possible through using a firewall,
and/or disable any unnecessary services running on the machine.
The second type of response that can be encountered is a closed port. This means that an
attacker cannot use this port to connect to the machine, however it has the disadvantage
of disclosing some information to the attacker: the fact that the port in closed state is
actually used on your computer, although access to it has been disabled. In this case you
enjoy better security, but indeed some information is still being disclosed.
Finally, the third type of response in case of remote TCP port scanning, is finding a
stealth port. In such a case, the machine does not provide any kind of response to the port
scanner software. It is recommended to use a firewall that puts ports into stealth mode, as
this is the most secure configuration, because in this case no information about services
running inside your computer will be disclosed.
16
What is the proper-countermeasure against port scanning?
Well, the best thing to do is to use a firewall to block access to open ports on your
computer. There are various tools that you can use for this purpose, but they usually fall
into two categories – hardware firewalls and software firewalls. A hardware firewall is
some sort of appliance that you buy from a computer store and install it at your home or
office, in between the Internet and your local network or computer. A software firewall is
a program that you install on your computer and protects it from inbound connection
attempts and other types of attacks and intrusion attempts. The best thing to do in order to
protect yourself, would be to have both if possible.
In TCP/IP terminology, a port is a software identifier that corresponds to a specific
application or protocol running on a host. For example, by default HTTP uses port 80. An
edge router typically provides the only IP address for an internal network. All packets for
hosts on the internal network are addressed to the router’s WAN IP address. Therefore,
the router determines where to deliver a packet on its local network in part by looking at
the port requested by the packet and then sending the packet to the host running the
corresponding application. An open port is any port for which packets will be accepted.
Packets for closed ports are dropped. Because packets for open ports are passed through
the edge router not an internal network, they provide an access tunnel through any
defenses the router might have. If a cracker can determine which ports are open through
an edge router, he/she has identified potential avenues for system attacks.
The port numbers used by protocols and applications are generally not kept secret. In
fact, those ports that are used by TCP/IP are called well known ports. You can find a
listing of common well-known ports in Appendix A.
As a first example of a port scan, take a look at Figure 2, which contains the result of a
port scan on a host that has open ports for the most common TCP/IP protocols. The scan
result shows the port numbers along with the protocols or applications that are listening
for traffic on each port. Today, network administrators know better than to leave unused
ports open. A port scan on an edge router, such as that in Figure 2.1, is likely to show
very few open ports. This particular router allows Web traffic through, but little else.
17
3.2.1 NetSec Port Scanner
In this section, we will show the development process of the NetSec port scanner.
3.2.1.1 Design
Class Diagram :
18
Flow Chart Diagram :
19
3.2.1.2 Implementation
In order to achieve the implementation of the port scanner we did make use of the
following classses: threading, time, sys and socket.
The time (Time access and conversions
) class provides various time-related functions. Although this class is always available,
not all functions are available on all platforms. Most of the functions defined in this class
call platform C library functions with the same name. It may sometimes be helpful to
consult the platform documentation, because the semantics of these functions varies
among platforms.
An explanation of some terminology and conventions is in order.
•
•
•
•
•
•
•
The epoch is the point where the time starts. On January 1st of that year, at 0
hours, the “time since the epoch” is zero. For Unix, the epoch is 1970.
The functions in this class do not handle dates and times before the epoch or far in
the future. The cut-off point in the future is determined by the C library; for Unix,
it is typically in 2038.
Year 2000 (Y2K) issues: Python depends on the platform’s C library, which
generally doesn’t have year 2000 issues, since all dates and times are represented
internally as seconds since the epoch.
UTC is Coordinated Universal Time (formerly known as Greenwich Mean Time,
or GMT)
DST is Daylight Saving Time, an adjustment of the timezone by (usually) one
hour during part of the year. DST rules are magic (determined by local law) and
can change from year to year. The C library has a table containing the local rules
(often it is read from a system file for flexibility) and is the only source of True
Wisdom in this respect.
The precision of the various real-time functions may be less than suggested by the
units in which their value or argument is expressed. E.g. on most Unix systems,
the clock “ticks” only 50 or 100 times a second
The time value as returned by gmtime(), localtime(), and strptime(), and accepted
by asctime(), mktime() and strftime(), may be considered as a sequence of 9
integers. The return values of gmtime(), localtime(), and strptime() also offer
attribute names for individual fields.
We did use the time class to define a function timer() which holds the operating system
time in a variable and then convert the time value returned by localtime() to a 24character string of the following form: 'Sun Jun 20 23:21:05 1993'. If t is not provided,
the current time as returned by localtime() is used. Locale information is not used by
asctime(). The timer() function was later used to display the start time of the port
scanning and the time it finished scanning.
20
The print statement evaluates each expression in turn and writes the resulting object to
standard output (see below). If an object is not a string, it is first converted to a string
using the rules for string conversions. The (resulting or original) string is then written. A
space is written before each object is (converted and) written, unless the output system
believes it is positioned at the beginning of a line. This is the case (1) when no characters
have yet been written to standard output, (2) when the last character written to standard
output is a whitespace character except ' ', or (3) when the last write operation on standard
output was not a print statement. (In some cases it may be functional to write an empty
string to standard output for this reason.) A '\n' character is written at the end, unless
the print statement ends with a comma. This is the only action if the statement contains
just the keyword print.
We did use the print statement to print out important notices and the output of the
scanner. The info() and usage() functions make use of the print statement to display a title
for the scanner and how to use the scanner respectively.
We made use of the sys class( System-specific parameters and function).This class
provides access to some variables used or maintained by the interpreter and to functions
that interact strongly with the interpreter. It is always available.
We used sys.argv function to validate the input, if the length of the input is different from
4 arguments the main() function will not execute and the usage() function will execute
followed by the sys.exit() function, else we assign the input arguments 1,2,3 into 3
variables as host,start(starting port),end(ending port) respectively. Also we validated the
input range of acceptable ports to be scanned (0 – 65536)
The sys.exit() function exits from python, This is implemented by raising
the SystemExit exception, so cleanup actions specified by finally clauses
of try statements are honored, and it is possible to intercept the exit attempt at an outer
level. The optional argument arg can be an integer giving the exit status (defaulting to
zero), or another type of object. If it is an integer, zero is considered “successful
termination” and any nonzero value is considered “abnormal termination” by shells and
the like. Most systems require it to be in the range 0-127, and produce undefined results
otherwise. Some systems have a convention for assigning specific meanings to specific
exit codes, but these are generally underdeveloped; Unix programs generally use 2 for
command line syntax errors and 1 for all other kind of errors. If another type of object is
passed, None is equivalent to passing zero, and any other object is printed
to sys.stderr and results in an exit code of 1. In
particular, sys.exit("some errormessage") is a quick way to exit a program when an error
occurs.
The thread class provides low-level primitives for working with multiple threads (also
called light-weight processes or tasks) — multiple threads of control sharing their global
data space. For synchronization, simple locks (also called mutexes or binary semaphores)
are provided. The threading class provides an easier to use and higher-level threading
API built on top of this class, it also provides an easy way to work with threads. Its
21
Thread class may be subclassed to create a thread or threads. The run method should
contain the code you wish to be executed when the thread is executed. Python manages to
get a lot done using so little. The Threading class uses the built in thread package to
provide some very interesting features that would make your programming a whole lot
easier. There are in built mechanisms which provide critical section locks, wait/notify
locks etc..
The major Components of the Threading class are:
•
•
•
•
•
•
Lock object
RLock object
Semaphore Object
Condition Object
Event Object
Thread Object
The RLock object is something new. RLock provides a mechanism for a thread to
acquire multiple instances of the same lock, each time incrementing the depth of locking
when acquiring and decrementing the depth of locking when releasing. RLock makes it
very easy to write code which conforms to the classical Readers Writers Problem.
The Semaphore Object is the general implementation of the Semaphore mooted by
Dijikstra. The Thread Object is a wrapper to the start_new_thread() function, which we
saw earlier, but with a little more functionality. The Thread object is never used directly,
but only by subclassing the threading. Thread interface. The user is supposed then to
override possibly the __init__() or run()function. Do not override the start() function, or
provide more than one argument to run. Note that you are supposed to
call Thread.__init__() if you are overriding __init__().
If you have a process that you want to do several things at the same time, threads may be
the answer for you. They let you set up a series of processes (or sub-processes) each of
which can be run independently, but which can be brought back together later and/or coordinated as they run.
Based on the above we created a subclass of thread and created an instance of it “self”
then we called its start method. We used threading to make the port scanner more faster,
imagine that the socket we created tries to connect to a specific port on the target ip and
puts the scanner in a waiting mode until a reply is received either a successful connect
(port open) or no reply (port closed). This makes the scanner really slow, but using
threads solved the waiting time, the sockets that are waiting a reply are set to a queue and
another thread instantiated to continue the checking procedure. A variable TMAX is
initialized to a value of 50 that is the maximum value of threads the scanner will
generate.
Of the various forms of IPC (Inter Process Communication), sockets are by far the most
popular. On any given platform, there are likely to be other forms of IPC that are faster,
but for cross-platform communication, sockets are about the only game in town. They
22
were invented in Berkeley as part of the BSD flavor of Unix. They spread like wildfire
with the Internet. With good reason — the combination of sockets with INET makes
talking to arbitrary machines around the world unbelievably easy (at least compared to
other schemes).
Socket addresses are represented as follows: A single string is used for
the AF_UNIX address family. A pair (host, port) is used for the AF_INETaddress family,
where host is a string representing either a hostname in Internet domain notation
like 'daring.cwi.nl' or an IPv4 address like'100.50.200.5', and port is an integral port
number. For AF_INET6 address family, a four-tuple (host, port, flowinfo, scopeid) is
used, where flowinfo and scopeid represents sin6_flowinfo and sin6_scope_id member
in struct sockaddr_in6 in C. The address format required by a particular socket object is
automatically selected based on the address family specified when the socket object was
created.
For IPv4 addresses, two special forms are accepted instead of a host address: the empty
string represents INADDR_ANY, and the
string'<broadcast>' represents INADDR_BROADCAST. The behavior is not available
for IPv6 for backward compatibility, therefore, you may want to avoid these if you intend
to support IPv6 with your Python programs.
If you use a hostname in the host portion of IPv4/v6 socket address, the program may
show a nondeterministic behavior, as Python uses the first address returned from the DNS
resolution. The socket address will be resolved differently into an actual IPv4/v6 address,
depending on the results from DNS resolution and/or the host configuration. For
deterministic behavior use a numeric address in host portion.
Linux-only support for TIPC is also available using the AF_TIPC address family. TIPC is
an open, non-IP based networked protocol designed for use in clustered computer
environments. Addresses are represented by a tuple, and the fields depend on the address
type. The general tuple form is (addr_type, v1, v2, v3 [, scope]), where:
•
addr_type is one of TIPC_ADDR_NAMESEQ, TIPC_ADDR_NAME, or
TIPC_ADDR_ID.
• scope is one of TIPC_ZONE_SCOPE, TIPC_CLUSTER_SCOPE, and
TIPC_NODE_SCOPE.
• If addr_type is TIPC_ADDR_NAME, then v1 is the server type, v2 is the port
identifier, and v3 should be 0.
• If addr_type is TIPC_ADDR_NAMESEQ, then v1 is the server type, v2 is the
lower port number, and v3 is the upper port number.
• If addr_type is TIPC_ADDR_ID, then v1 is the node, v2 is the reference,
and v3 should be set to 0.
All errors raise exceptions. The normal exceptions for invalid argument types and out-ofmemory conditions can be raised; errors related to socket or address semantics raise the
error socket.error.
We defined a method Scan(ip,port) which takes two arguments ip and port, and then we
created a socket using the given address family, socket type and protocol number. The
address family is AF_INET and the socket type is SOCK_STREAM
23
sk = socket(AF_INET, SOCK_STREAM) and then a try statement is invoked, at first the
socket instance will try to connect to remote socket at the target ip address. If the value of
the getservbyport(port) is empty the service name of the checked port will not be printed
out, and if the value of the getservbyport(port) is not empty the service name along with
the opened port will be printed out, after that the socket is closed. Then if exception
occurs which does not match the exception named in the except clause, it is passed on to
outer try statement “except:pass”
The getservbyport(port[, protocolname] translates an Internet port number and protocol
name to a service name for that service. The optional protocol name, if given, should
be 'tcp'or 'udp', otherwise any protocol will match.
At last the main() function was created, several things happen in this function, start time
is printed out along with some titles, then thread variable is assigned to an empty array
and a counter assigned to an integer to hold the number of threads. Then a “for loop” is
performed to create a new thread each time a socket attempts to connect to a remote port
at the target ip, and to assure that the number of threads does not exceed the allowed
number of threads previously assigned “50”.
The __main__ — Top-level script environment represents the scope in which the
interpreter’s main program executes — commands read either from standard input, from
a script file, or from an interactive prompt. It is this environment in which the idiomatic
“conditional script” stanza causes a script to run:
if __name__ == "__main__":
main()
3.3 Network Scanning
Network scanning is a procedure for identifying active hosts on a network, either to
attack them or as a network security assessment. Such a task is done by the security
officer to detect the live systems on the network and subsequent identification of the
target system and to discover the IP addresses of the target system. All required
information about a system can be gathered by sending ICMP packets to it. Since ICMP
doesn’t have a port abstraction, this cannot be considered a case of port scanning.
However it is useful to determine what hosts in a network are up by pinging them all.
ICMP can be used to find out which time zone the system is in by sending an ICMP type
13 message (TIMESTAMP). The netmask on a particular system can also be determined
with ICMP type 17. After finding the netmask of a network card, one can determine all
the subnets in use. After getting knowledge about the subnets, the security officer can
target only one particular subnet and avoid hitting the broadcast addresses.
24
3.3.1 OS FingerPrinting
OS fingerprinting is the method to determine the operating system that is running on the
target system. It is an important scanning method, as the security officer will have a
greater probability of success if he/she knows the OS of the target system (the
vulnerabilities are OS specific). The security officer can then formulate a defense strategy
based on the OS of the target system. Determining the OS on a remote host was
originally carried out with a technique known as “banner grabbing”. Banner grabbing can
be carried out in two ways: either by spotting the banner while trying to connect to a
service such as FTP, or downloading the binary file/bin/ls to check the architecture with
which it was built. A more advanced fingerprinting technique depends on stack querying,
which transfers the packets to the network host and evaluates packets based on the reply.
The first stack querying method was designed considering the TCP mode of
communication, in which the response of the connection requested is evaluated. The next
method was known as ISN (initial sequence number) analysis. This identifies the
differences in the random number generators found in the TCP stack. A new method
using the ICP protocol is known as ICMP response analysis. It consists of sending the
ICMP messages to the remote host and evaluating the reply. The latest ICMP messaging
is known as the temporal response analysis. Like others, this method uses the TCP
protocol. Temporal response analysis looks at the retransmission timeout (RTO)
responses from a remote host.
3.3.2 NetSec Network Scanner
The technique used for the network discovery is the ICMP Echo request/reply.
ICMP Echo Request (Type 8) and Echo Reply (Type 0):
ICMP messages are sent in IP packets. Although ICMP uses IP as if it were a higherlevel protocol, ICMP is an internal part of IP, and must be implemented in every IP
module.
It is important to note that the ICMP protocol is used to provide feedback about some
errors (non-transient) in a packet processing, not to make IP reliable. Packets may still be
undelivered without any report of their loss. If a higher level protocol that use IP need
reliability he must implement it.
RFC 792 defines the IP protocol ID for ICMP to be 1. It also states that the IP Type-ofService field value and the Precedence Bits value should be equal to zero. According to
RFC 1812, Routers will use the value of 6 or 7 as their IP Precedence bits value with
ICMP Error messages.
There are different ICMP message types, the message type identifies what sort of ICMP
message it is (echo request for ping vs. router solicitation vs. redirect...). Each ICMP
message type also has a message code that let us know the exact meaning. So an ICMP
packet with a message type 3 (Destination Unreachable) and a message code 3 (Port
Unreachable) means that the machine.
25
You can find the complete ICMP message types table in Appendix A.
The ICMP Echo Request packet is used to determine whether a target IP address is active
or not, by simply sending an ICMP Echo (ICMP type 8) packet to the targeted system
and waiting to see if an ICMP Echo Reply (ICMP type 0) is received. If an ICMP Echo
reply is received, it would indicate that the target is alive; No response means the target is
doesn’t exist or offline.
The sending side initializes the identifier (used to identify Echo requests aimed at
different destination hosts) and sequence number (if multiple Echo requests are sent to
the same destination host), adds some data (arbitrary) to the data field and sends the
ICMP Echo to the destination host. In the ICMP header the code equals zero. The
recipient should only change the type to Echo Reply, recalculate the ICMP header
Checksum, and return the packet to the sender.
The data received in the Echo message must be returned in the Echo Reply message
unchanged.
Fig 3. ICMP ECHO Request & Reply message format
The expected behavior from a router/host when handling an ICMP Echo type message
(from RFC 1122 requirements for Internet Hosts) is:
•
A router should have a configuration option that, if enabled, causes the router to
silently ignore all ICMP Echo requests; if provided, this option must be default to
allowing responses.
•
Every host/router must implement an ICMP Echo server function that receives
Echo requests and sends corresponding Echo Replies.
•
A host/router should implement an application-layer interface for sending an Echo
request and receiving an Echo reply, for diagnostic purposes.
•
If we send an ICMP Echo request to an IP Broadcast or IP Multicast address it
may be silently discarded by a host/router.
•
If a Record Route or Timestamp option is received in an ICMP Echo request, this
option (these options) should be updated to include to current router/destination
26
host and included in the IP header of the Echo Reply message, without truncation.
Thus, the record route will be for the entire round trip.
•
If a Source Route option is received in an ICMP Echo request, the return route
must be reversed and used as a source route option for the Echo Reply message. A
router will not perform this if it is aware of a policy that would prevent the
delivery of the message.
The amount of data used in the data field within the ICMP Echo request will vary from
one implementation to another (and between one family of operating systems to another).
For example, the ‘ping’ utility with UNIX and UNIX-like operating systems will use an
ICMP data field of 56 bytes, adding that to the 20 bytes of the IP header and to the ICMP
header (8 bytes) will result in a packet size of 84 bytes.
However, the ‘ping’ utility with Microsoft Windows operating systems will build, by
default, an ICMP Echo request packet with the size of 60 bytes. This is since the ‘ping’
utility is using a data field of 32 bytes only.
3.3.2.1 Design
Class Diagram:
27
Flow Chart Diagram:
28
3.3.2.2 Implementation
Implementation of the ip scanner:
When the network address is entered with the subnet mask in the following format
“192.168.0.0/24” this address means that the first usable host in this network is
192.168.0.1 and the last usable host is 192.168.0.254 with a broadcast address
192.168.0.255. So for the ip scanner to get this information, the ip scanner has a module
called “netconvert” that process the address “192.168.0.0/24” it will compare the subnet
mask and the network address in order to get all the usable hosts on the network using the
function “hostenum” and they are saved in a list. So the first usable host will be at the
first index of the list, and the last host is at the last index of the list.
Then, we get the size of this list, in order to loop over all the hosts of this network, in
order to send an ICMP echo request to each host to check if it is alive or not.
For the ICMP echo request to be done, we invoke the function “verbose_ping” that will
send 1 ICMP echo request packet with a timeout 1 second.
If the host is alive, the address of this host will be saved in a text file in order to log all
the live hosts.
The os and sys modules are the core of much of Python's system-related tool set. They
contain all of the usual operating-system calls, i.e. they are the libraries for the input and
output and for handling files.
The class struct: contain functions to convert between binary strings and python tuples.
• The path function takes a format string and one or more arguments, and returns a
binary string
• The unpack function takes a string and returns a tuple.
• The calcsize function takes a format string and returns the size of the struct.
The class select: it is used to check for incoming data on one or more sockets, pipes, or
other stream objects.
You can pass one or more sockets to the select function, to wait for them to become
readable, writable, or signal an error.
• A socket becomes ready for reading when:
1) Someone connects after a call to listen (which means that accept won’t
block)
2) Data arrives from the remote end.
3) The socket is closed or reset (in this case, recv will return an empty string)
• A socket becomes ready for writing when:
1) The connection is established after a non-blocking call to connect.
2) Data can be written to the socket.
• A socket signals an error condition when the connection fails after a non-blocking
call to connect.
29
The class time: it provides a number of functions to deal with dates and within a day. It’s
a thin layer on the top of the C runtime library.
• The time function returns the date and the time as a floating point value (it returns
the number of seconds (float number) since a reference date (1 January 1970))
So we used the time function to record the time when the ICMP Echo Request is sent and
record it again when the ICMP Echo Reply is received, because arithmetic calculations
(calculating the delay) is much easier with floats than to deal with strings.
The class re: it provides a set of powerful regular expressions. A regular expression is a
string pattern written in a compact syntax, and allows us quickly to check whether a
string matches a given string (the match function) or contains a given string (search
function)
• The search function scans through a string looking for a match to the pattern,
returning a match object, or None if no match was found.
• The sub function is used to replace patterns with another string, and we used it to
convert from string (the network address entered by the user) into an IPv4 format.
The class socket: it provides an interface to the socket communication layer, i.e. in order
to be able to communicate through the network.
• The socket function is used to create a communication link on the network.
• The AF_INET function is used to specify that the network protocol used is the ip
protocol.
• The SOCK_STREAM function is used to identify that the connection created is
connection oriented, i.e. using the TCP protocol.
• The recvfrom function is used to read the incoming data, i.e. the ICMP Echo
Replies.
• The sendto function is used to send the data into specified destination, i.e. we
used it to send the ICMP Echo Requests.
• The gethostbyname function is used to get the ip address of a host in form of a
string.
• The getprotobyname is used to get the protocol number for the named protocol
(ICMP) and returns an integer.
• The error function is used to raise an error if the socket fails to be created due to
wrong input (it contains predefined error messages), it is used in a try and except
statement (error handling).
• The htons function is used to convert a 16-bit integer from host to network byte
order.
• The gaierror function is used to raise error for address-related errors; it takes two
arguments (error and string). The error represents an error returned by a library
call, and the string represents the description of the error.
The class Netconvert: it is used to convert the network address with the subnet mask
provided by the user from a string to a list containing all usable hosts.
30
•
•
•
•
•
•
•
The ip function returns the ip address.
The network function returns the network address.
The cidr function returns a CIDR-Style ip representation (Classless Inter Domain
Routing).
The broadcast function returns the broadcast address of the network.
The mask function represents returns the subnet mask in form of “255.255.255.0’.
The bits function returns the width of the network in bits, i.e. if we have an IPv4
address it will return the integer 32, and if we have IPv6 address it will return the
integer 128 (however we are only going to use the IPv4 addressing).
The function hostenum returns a list of all usable hosts in the network, i.e.
excluding the network address and the broadcast address.
3.4 Vulnerability Checking and Analysis
Vulnerability checking is the automatic method used to identify the vulnerabilities
present in the system and the network that is used for checking whether the system has
been exploited. A vulnerability scanner consists of a scanning engine and a catalog. The
catalog consists of a list of common files with known vulnerabilities and common
exploits for a range of servers. For example, the vulnerability scanner may look for
backup files or directory traversal exploits. The scanning engine maintains logic for
reading the exploit list, transferring the request to the web server and analyzing the
requests to ensure the safety of the server. These tools generally target vulnerabilities that
are easily fixed by secure host configurations, updated security patches and a clean WEB
document.
3.4.1 Vulnerability Assessment
In today’s world, organizations depend heavily on information technology. It is necessary
for them to protect their vital information. This information can be related to various
departments such as finance research and development, personnel, legal and security
issues. A vulnerability assessment is performed on this critical data to safeguard it. The
vulnerability assessment can be defined as the test where a system or an application is
subjected to test. The security procedures and controls are also put to the test in order to
find whether they can withstand the assult.
The vulnerability assessment process involves recognizing, measuring, and prioritizing
vulnerabilities in a system. It helps an organization know the threats and vulnerabilities of
the system's infrastructure. Before starting a penetration test, it is essential to identify the
vulnerabilities using a vulnerability scanner. Performing a vulnerability scan helps you
evaluate whether the penetration test can be performed or not and identify areas where
you need to perform a penetration test. Try to identify the weaknesses of a system and
use hacking tools to exploit the vulnerabilities.
31
The steps involved in vulnerability assessment are:
• Checking whether the target is alive: Use the Internet Control Message
Protocol(ICMP) to get connected to the target system and check whether the
target is alive.
• Scanning the ports: Check for the open ports that can be attacked. Perform the
scan in stealth mode for a particular period of time. Test the ports by sending
some harmful information.
• Identifying the potential vulnerabilities and report generation: Use a network
vulnerability scanner to identify the potential vulnerabilities and to obtain the
report of vulnerabilities and patches.
• Classifying of vulnerabilities and building responses: Classify vulnerabilities and
build responses accordingly. Many times, the response chosen for vulnerability is
non-actionable because of complexities and risks. The assessment process gives
the complete information about these issues in the document decision process and
this information is helpful while performing the risk management process.
• Classifying of key assets and risk management process: The vulnerability
assessment process classifies they key assets and makes a hierarchy of the key
assets, which helps to drive the risk management process.
• Providing follow-up documentation/reports: A vulnerability assessment provides
follow-up documentation and reports and additional consulting whenever required
after the assessment process.
3.4.2 Types of Vulnerability Assessment
The following are the different types of vulnerability assessment techniques;
• Active assessments:
Active assessment is a type of vulnerability assessment that uses network scanners to
scan the network and to identify the host, services and vulnerabilities present in that
network. Active network scanners have the capability to reduce the intrusiveness of the
checks they perform.
• Passive assessments:
Passive assessment means sniffing the traffic present on the network to identify the list of
working systems, network services, applications, and vulnerabilities. Passive assessment
provides the correct list of the users who are currently using the network. Passive
assessment is performed by using sniffers which give complete information of the
network
• Host-based assessments:
Host-based assessment is a type of security check that carries out a configuration level
check through a command line. This assessment checks the security of a particular
network or server. Host-based assessment is carried out through host—based scanners
and these scanners identify system vulnerabilities like incorrect registry and file
32
permission as well as software configuration error. Many commercial and open source
scanning tools are used for host-base assessment such as Security-Expressions scanner.
• Internal assessments:
An internal assessment means scrutinizing the internal network to find out the exploits
and vulnerabilities. It helps to exploit the vulnerabilities, which are inside the firewall, on
the LAN and on private IP addresses.
The following are the various internal assessment options:
o Specify the open ports and related services on network devices, servers, and
systems.
o Check for route configurations and firewall rule sets.
o List the internal vulnerabilities of the operating system and server.
o Scan for the Trojans that may be present in the internal environment
o Check the patch levels on organization internal network devices, servers, and
systems.
o Check for the existence of malware, spyware, and virus activity and document
them.
o Evaluate the physical security.
o Identify and review the remote management process and events.
o Assess the file sharing information and access( for example: NFS and
SMB/CIFS shares)
o Examine anti-virus implementation and events.
• External assessments:
This type of assessment is based on external devices such as firewalls, routers and servers
to assess the vulnerabilities present in the external devices. This assessment estimates the
threat of network security attacks external to the organization. It determines how secure
the external network and firewall are.
The following are the various external assessment options:
Determine the set of rules or firewall and router configurations for the external network.
o Check whether external server devices and network devices are mapped.
o Identify open ports and related services on the external network.
o Examine patch levels on the server and external network devices.
o Review modem and war-dialing
o Review detection system such as IDS,firewall, and application layer
protection systems.
o Get information on DNS zone.
o Scan the external network through a variety of proprietary tools available on
the internet.
o Examines web applications such as e-commerce and shopping cart for
vulnerabilities.
•
Application Assessments:
33
An application assessment focuses on the transactional web applications, traditional
client-server applications, and hybrid systems. It depends on the type of application being
assessed. It analyzes all elements of an application infrastructure, including how every
element communicates with the client and the server. Both commercial and open-source
tools are used to perform such assessment.
• Network Assessment:
Network assessments determine the possible network security attacks that may occur on
the organization’s system. It evaluates the organization’s system for vulnerabilities that
are related to the organization’s network, such as missing patches, needless services,
weak authentication, and weak encryption. Network assessment is performed through
firewall and network scanners such as Nessus Security Scanner. These scanners find open
ports, recognize the services running on those ports, and also find vulnerabilities
associated with these services. They focus on the weak authentication mechanisms
subjected to attacks.
The assessment helps the organizations to determine how vulnerable systems are to
internet and intranet attacks and how an attacker can gain access to important information
It conducts the following tests on the network:
o Checks the network topologies for inappropriate firewall configuration.
o Examines the router filtering rules.
o Specifies the inappropriately configured database servers.
o Tests individual services and protocols like HTTP, SNMP, and FTP
o Indentifies those database servers that are not improperly configured.
o Reviews the HTML page source code for unnecessary information.
o Bounds checking of the variables.
Earlier, wireless networks were built with weak and basically, defective data encryption
mechanisms. But now, wireless network standards have evolved and many networks
initially deployed are still active and ripe for attack. Wireless network assessments try to
attack the wireless authentication mechanisms and get unauthorized access. This
assessment tests the authorized business wireless networks and also identifies rogue
wireless network that may exist within your organization’s perimeter.
These assessments are performed on client-specified sites where wireless networks have
been installed. They follow the wireless network traffic and try to crack encryption keys.
If the network can be accessed, the other network access is tested. The entire linked
network is tested
3.4.3 Assessment Phase
Following tasks are performed in the assessment phase:
• Examination of the network architecture:
It involves the analysis information assurance feature of the information network linked
with the organization’s systems. Analysis contains checking of the network topology and
connectivity, communication protocol, and function of hardware and software
components.
• Evaluation of the threat environment:
34
Threat may come into the organization’s network from individual persons or
organizations that are influenced by financial gain. Good knowledge of threat
environment forms the basis of risk management. The assessment phase identifies these
threats and its trends.
• Penetration testing is allowed:
Penetration testing is performed to exploit the vulnerabilities that are found in the
organization’s system. It contains the processes such as setting up rules of engagement
for the test, developing a test methodology, performing a test, and creating a final report.
• Examination and evaluation of physical security:
Examination and evaluation of physical security is important to identify possible
progresses in this area for the sites evaluated. This assessment focuses on the sites that
are directly linked to critical facilities.
• Carrying out a physical asset analysis:
The main purpose of this analysis is to check the organizational systems and physical
operational assets to find out whether vulnerabilities exist. It checks for the asset
utilization, system redundancies, and crisis operating procedures. This assessment
determines organization and industry trends regarding these physical assets.
• Assessment of operations security:
This assessment involves identification and controlling of non-sensitive activities and
execution of sensitive activities. It examines the security training, alertness programs, and
also examines procedures and methods employed for denying adversary access to
sensitive and non-sensitive information.
• Observation of policies and procedures:
Observation of policies and procedures is important to develop a complete understanding
of how a facility defends its critical assets through the development and implementation
of policies and procedures.
• Impact analysis:
Impact analysis is conduced to find the influence that misuse of unauthorized access to
information systems might have on an organization’s operations.
• Assessment of infrastructure interdependencies:
This assessment determines the direct infrastructure connections among the different
infrastructures that support vital services as recognized by the company.
• Carrying out a risk characterization:
This task gives the support for prioritizing recommendations across all task areas. It first
judges the recommendations for every task area and helps the organization to determine
the proper action. It also provides a framework for reviewing vulnerabilities and threats.
35
3.4.4 Vulnerability Analysis Stages
Any organization needs to handle and process large volumes of data in order to carry out
business. These large volumes of data contain the information of that particular
organization for which access is denied to unauthorized users. Hackers try to find certain
vulnerabilities they can exploit and use to gain access to the critical data for illegal
purposes. Vulnerability analysis performs a study on the risk-prone areas of the
organizational network. This analysis is done using various tools. The vulnerability
analysis reports on the weak areas in the network. These vulnerability penetration
capabilities can be broken down into three steps:
• Locating nodes
• Performing service discoveries on them
• Testing those services for known security holes
Vulnerability Assessment Reports:
The vulnerability assessment report discloses the risks that are detected after scanning the
network. The report alerts the organization to possible attacks and suggests
countermeasures. The report generated provides details of the possible attack with regard
to the company’s security policies.
36
3.4.5 Vulnerability Report Model
37
Vulnerability report covers the following elements :
Scan Alert:
It provides the scanning result of the system. Scanning of the target computer or network
is done with the help of scanning tools. It consists of two parts that are as follows:
• Scan information:
This part of the report provides the information such as name of scanning tool, its
version, and port of the network which has to be scanned.
Target Information:
This part of the report contains the information about the target system;s name and
address.
Results:
This section gives the complete report of the scanning. It contains the classes such as
target, services, vulnerability, classification and assessment.
• Target:
This class is used to get a standard format for representing the host’s specific
information. It contains the following classes:
o <Node> : It contains the address and name element of the host.
o <OS> : It shows the operating system type.
o <Date> : It gives the date.
• Service:
This class defines the network services by its name and ports.
• Vulnerability:
This class describes the vulnerability by its name, category of attack, and service
affected. It contains classification and assessment classes.
• Classification:
This class allows the system administrator to obtain additional information about the
scanning such as origin of the source, name and URL.
• Assessment:
This class provides the information regarding scanner’s assessment of the vulnerability.
3.4.6 NetSec Vulnerability Checking
In the integration module we used the os library, and we used the function os.system that
executes any command in the environment that is installed on the system, so any tool can
be integrated all it have to be is installed on the system, or if it is not installed, let us
suppose that a python tool is to be integrated, the tool should be in the same directory in
the NetSec directory, and it should be preceded by the argument python. For example, let
us say that the tool name is tool.py, in order to integrate this tool, the command should be
in the following format os.system(“python tool.py [enter here the arguments but without
38
the braces]” ) and the tool will be integrated successfully, the same for a tool written in
another language, for example in perl, the same command should be used but instead we
type: os.system(“perl tool.pl [enter here the arguments but without the braces]” ).
3.5 Testing
In order to achieve the testing process successfully we managed to use 2 laptop
computers having linux kernel 2.6.x installed, one laptop had the NetSec project installed
on it and the other was acting as a target system. The 2 laptops were connected using a
cross cable connection. The ip address of the web server was set to 192.168.0.1, and the
ip address of NetSec laptop was set to 192.168.0.2.
Testing of the NetSec IP scanner:
First of all a bash terminal was launched and logged in as a super user (root)
laptop@NetSec:~$ su - # to log in as super user
Password:
root@NetSec:~# pwd # Print working directory
/root
then we changed directory into the NetSec directory
root@NetSec:~# cd /NetSec # to change directory into NetSec.
We did run the IP scanner of NetSec,
root@NetSec:~/NetSec# python ipNetSec.py
Please enter the ip address with the subnet mask: 192.168.0.0/29
checking host: 192.168.0.1 Host is alive
checking host: 192.168.0.2 Host is alive
checking host: 192.168.0.3 Host doesn’t exist or offline
checking host: 192.168.0.4 Host doesn’t exist or offline
checking host: 192.168.0.5 Host doesn’t exist or offline
checking host: 192.168.0.6 Host doesn’t exist or offline
As a result the goal behind the ip scanner was achieved the ip scanner did find the
alive/dead ip addresses inside the given network.
Testing of the NetSec PORT scanner:
We managed to install the following services on the target system
[bind9(DNS),mysql(DBMS),ftpd(FTP),apache(WEB),webmin(CMS), openSSH(SSH
server)].
Repeating the previous steps to gain super user access, and changing directory into the
NetSec project, we then launched the port scanner to check for open ports/running
services on the target system
root@NetSec:~/NetSec# python pNetSec.py
A how to use will appear
39
pNetSec - Port Scanner
usage: pNetSec.py <host> [start port] [end port]
root@NetSec:~/NetSec# python pNetSec.py 192.168.0.2 1 40000
pNetSec - Port Scanner
=== Process Start : Thu Apr 22 17:12:57 2010
[X] OPEN : smtp : 25
[X] OPEN : domain : 53
[X] OPEN : www : 80
[X] OPEN : webmin : 10000
=== Process end : Thu Apr 22 17:13:05 2010
As a result the output showed the open ports on the target system along with their service
names.
Testing of integrated vulnerability checking tool:
After checking the live hosts and checking the open ports and running services, we can
notice from the tests done before that the target system “192.168.0.1” is running a WEB
server (port 80 is open). Upon that we executed the integration tool which will assess the
vulnerabilities upon that WEB server.
Repeating the previous steps to gain super user access, and changing directory into the
NetSec project.
root@NetSec:~/NetSec# python integration.py
('Linux', 'laptop-laptop', '2.6.31-16-generic', '#53-Ubuntu SMP Tue Dec 8 04:01:29 UTC
2009', 'i686')
Thu Apr 22 18:05:58 2010
please enter an ip address: 192.168.0.1
--------------------------------------------------------------------------+ Target IP:
192.168.0.1
+ Target Hostname: 192.168.0.1
+ Target Port:
80
+ Start Time:
2010-04-23 17:34:15
--------------------------------------------------------------------------+ Server: Apache/2.2.9 (Ubuntu) PHP/5.2.6-bt0 with Suhosin-Patch
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-0: Retrieved X-Powered-By header: PHP/5.2.6-bt0
+ PHP/5.2.6-bt0 appears to be outdated (current is at least 5.2.6RC4)
+ OSVDB-877: TRACE / : TRACE option appears to allow XSS or credential theft. See
http://www.cgisecurity.com/whitehat-mirror/WhitePaper_screen.pdf for details
+ OSVDB-12184: GET /index.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000
: PHP reveals potentially sensitive information via certain HTTP requests which contain
specific QUERY strings.
40
+ OSVDB-3093: GET /db.php : This might be interesting... has been seen in web logs
from an unknown scanner.
+ OSVDB-3268: GET /icons/ : Directory indexing is enabled: /icons
+ OSVDB-3233: GET /icons/README : Apache default file found.
+ 3577 items checked: 7 item(s) reported on remote host
+ End Time:
2010-04-23 17:34:21 (6 seconds)
--------------------------------------------------------------------------+ 1 host(s) tested
Test Options: -h 192.168.0.1 -o result.txt
Chapter 4: Exploits And Securing Your Code In Network
Programming
In this chapter, we will explain what exploits are and we will talk about a technique used
in securing network programming (Socket Programming)
4.1 Exploits
Exploits; In most information technology circles these days, the term exploits has become
synonymous with vulnerabilities or in some cases, buffer overflows. It is not only a scary
word that can keep you up at night wondering if you purchased the best firewalls,
configured your new host-based intrusion prevention system correctly, and have patched
your entire environment, but can enter the security water-cooler discussions faster than
McAfee’s new wicked anti-virus software or Symantec’s latest acquisition.
Exploits are proof that the computer science, or software programming, community still
does not have an understanding (or, more importantly, firm knowledge) of how to design,
create, and implement secure code.
Like it or not, all exploits are a product of poorly constructed software programs and
talented software hackers – and not the good type of hackers that trick out an application
with interesting configurations. These programs may have multiple deficiencies such as
stack overflows, heap corruption, format string bugs, and race conditions—the first three
commonly being referred to as simply buffer overflows. Buffer overflows can be as small
as one misplaced character in a million-line program or as complex as multiple character
arrays that are inappropriately handled. Building on the idea that hackers will tackle the
link with the least amount of resistance, it is not unheard of to think that the most popular
sets of software will garner the most identified vulnerabilities. While there is a chance
that the popular software is indeed the most buggy, another angle would be to state that
the most popular software has more prying eyes on it.
41
Software engineering is an extremely difficult task and of all software creation-related
professions, software architects have quite possibly the most difficult task. Initially,
software architects were only responsible for the high-level design of the products. More
often than not this included protocol selection, third-party component evaluation and
selection, and communication medium selection. We make no argument here that these
are all valuable and necessary objectives for any architect, but today the job is much more
difficult. It requires an intimate knowledge of operating systems, software languages, and
their inherent advantages and disadvantages in regards to different platforms.
Additionally, software architects face increasing pressure to design flexible software that
is impenetrable to wily hackers. A near impossible feat in itself.
4.2 Half-Open Sockets
One of the major security techniques in network programming is to use the half-open
sockets.
Normally, sockets are bidirectional, i.e. Data can be sent across them in both directions.
Sometimes, we may want to make a socket unidirectional, so data can be sent only in one
direction. A socket that is unidirectional is said to be half-open socket.
A socket is made half-open by calling the method “shutdown()”, and the procedure is
irreversible for that socket.
Half-Open sockets are useful when:
• We want to ensure that all data written has been transmitted. When shutdown() is
called to close the output channel of a socket, it will not return until all buffered
data has been successfully transmitted.
• We want to have a way to catch potential programming errors that may cause the
program to write to a socket that shouldn’t be written to, or read from a socket
that shouldn’t be read from.
• The program uses fork() or multiple threads, and want to prevent other processes
or threads from doing certain operations, or want to force a socket to be closed
immediately.
The socket.shutdown() call is used to accomplish all of these tasks. So, using
socket.shutdown() helps in making sure that the code is correct. For instance, if the
writing was completed and then shutdown() was invoked to prevent future writing, an
exception will be generated if we try to write to the socket in the future. An exception is
usually easier to track down than deadlock or protocol miscommunication, so getting one
could be very useful.
Another situation arises when the program uses fork() or multiple threads. When using
fork(), calling close() on a socket only makes it unavailable to that particular process. The
connection isn’t actually closed until all processes that use it have either called close(), or
had the socket go out of scope or deleted, or terminated. When the communication is
done between the client and the server, we can force the socket shut by invoking the
shutdown in both directions.
42
The method shutdown() requires a single argument that tells the socket to stop future
reading/writing:
• 0 to prevent future reads.
• 1 to prevent future writes.
• 2 to prevent future reads and writes.
Once the shut down in a given direction, the socket can never be re-opened in that
direction. Calls to shutdown() are cumulative; calling shutdown(0) followed by
shutdown(1) will achieve the same effect as calling shutdown(2).
Chapter 5: Conclusion
In this chapter, we will state what we have learned and experienced for the NetSec
project, and the summary of our work.
5.1 Learning Outcomes
Technically speaking, this project gave us the opportunity to develop our network
development skills, deep understanding on how the network communication occurs, and
what are the vulnerabilities that might face us in the real life. We also developed skills in
python programming language, and development for linux-like operating systems.
We also developed experience in linux administration, and get to know better how the
linux operating system work, and what are the differences between linux-like operating
systems and Microsoft windows operating systems.
We also developed a good knowledge in tackling tools written in the c programming
language, and be able to read and understand the code and use it in python.
On the other side, this project gave us the opportunity to develop our team work skills,
and how to manage the tasks assigned to us, and how to collaborate as a team. Also, it
enabled us to be able to deliver on time the tasks that are assigned to us, and the
importance of doing a schedule and sticking to it.
Moreover, it enabled us to develop our research skills; developing new research
techniques, that is how to evaluate information from the search, and what to consider as a
reference, and how to validate the extracted information, and how to use these
information to support our work or develop our technical experience.
Also, we experienced how the software development life cycle is done, from placing the
requirements of the software, to the design stage, to the implementation stage, to the
testing stage, and finally in documenting our software (that is writing the report).
So, we managed to apply what we have learnt from previous courses in the university like
the M301 course for the software engineering process, and we got use of our previous
experience that we developed through out the years of the university especially in the
networking area.
43
5.2 Summary
Nowadays with the increasing number of exploits/vulnerabilities, organizations should
take into consideration the process of vulnerability assessment to ensure the maximum
level of security. NetSec is a freeware software, that will help somehow in vulnerability
checking for WEB servers. Compared to other vulnerability assessment tools, i.e.
CoreImpact product which is not cheap (be prepared to spend tens of thousands of
dollars) the NetSec provides some of the important functionalities needed to assess
vulnerabilities.
5.3 Future Extenstion
We are seeking forward to make NetSec an automated, comprehensive penetration testing
software that will spot a large, regularly updated database of professional exploits, and
will do neat tricks like exploiting one machine and then establishing an encrypted tunnel
through that machine to reach and exploit other boxes.
Chapter 6: References
[1] James M. Stewart, Ed Tittel, Mike Chapple. (July 2008) CISSP: Certified Information
Systems Security Professional Study Guide, 4th Edition. Sybex
ISBN: 9780470276884
[2] David L. Cannon. (March 2008) CISA Certified Information Systems Auditor Study
Guide, 2nd Edition. Sybex.
ISBN: 9780470231524
[3]Kimberly Graves. (February 2007) CEH: Official Certified Ethical Hacker Review
Guide: Exam 3125.
Sybex.
ISBN: 9780782144376
[4] Emmett Dulaney, James M. Stewart, David R. Miller, Michael Gregg. (January 2009)
CompTIA Security+ Certification Kit: SY0201
, 2nd Edition. Sybex.
ISBN: 9780470404867
[5] Angela Orebaugh, Becky Pinkard. (2008) Nmap In The Enterprise Your Guide to
Network Scanning. Syngress Publishing, Inc.
ISBN: 9781597492416
[6] IEEE Std 8301998 IEEE Recommended Practice for Software Requirements
Specifications.
[7] Mark Lutz, (August 2006), Programming Python, 3rd Edition. O'Reilly.
ISBN: 9780596009250
[8] Mark Lutz, (September 2009), Learning Python 4th Edtition,. O’Reilly.
ISBN: 9780596158064
44
[9] John Goerzen, (February 2004), Foundations of Python Network Programming.
Apress.
ISBN: 1590593715
[10] Jan L. Harrington, (March 2005), Network Security: A Practical Approach.
ELSEVIER
ISBN: 0123116333
45
Appendix A
List of well known and registered ports.
46
47
48
49
50
51
ICMP Types, Names, and Code
52
53