Final Exam Answer Key MCIS 503 Dr. Jerry A. Smith 10 problems
advertisement

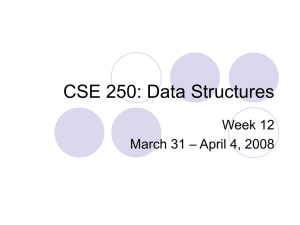
Final Exam Answer Key MCIS 503 Dr. Jerry A. Smith 10 problems, each worth 10 points. Problem 1) Give asymptotic upper and lower bounds to T (n) = 16T (n / 4) + n 2 . Make your bounds as tight as possible and justify your answer. This is a divide-and-conquer recurrence with a = 16, b = 4, f(n) = n2, and n logb a = n log 4 16 = n 2 . Since n 2 = !(n log 4 16 ) , case 2 of the master theorem applies, and T (n) = !(n 2 lg n) . Problem 2) Give asymptotic upper and lower bounds to T (n) = T ( n ) + 1 . Make your bounds as tight as possible and justify your answer. Let m = lg n and S(m) = T(2m), thus T(2m) = T(2m/2)+1 and S(m) = S(m/2)+1. Using the Master Theorum, n log 2 1 = n 0 = 1 and f(n) = 1. Since 1 = Θ(1), case 2 applies and S(m) = Θ(lg m). Therefore, T(n) = Θ(lg lg n). Problem 3) Using figure 6.3 as a model, illustrate the operation of Build-Max-Heap on the array <4, 2, 15, 55, 34, 32, 9, 22, 3> 1 4 2 3 2 i 4 5 55 34 8 22 15 9 3 6 32 7 9 1 4 2 3 2 15 4 5 55 34 8 i 6 7 32 9 9 22 3 1 4 2 i 3 2 32 4 5 55 34 8 6 7 15 9 9 22 3 1 i 4 2 3 55 4 5 22 34 8 2 32 9 3 6 15 7 9 1 55 2 3 34 32 4 5 22 6 4 8 7 15 9 9 2 3 Problem 4) Using CLRS figure 8.4 as a model, illustrate the operation of Bucket-Sort on the array <0.10, 0.15, 0.34, 0.67, 0.54, 0.59, 0.45, 0.11>. Length[A] = 8 A B 1 .10 0 .10 2 .15 1 .15 / 3 .34 2 .34 / 4 .67 3 .45 / 5 .54 4 .54 6 .59 5 .67 7 .45 6 / 8 .11 7 / .11 / .59 / Problem 5) Draw a picture of a sequence <15, 2, 22, 10, 19, 3, 1> stored as a doubly linked list using the multiple-array representation. Do the same for the single-array representation. 1 next 1 2 3 4 5 6 7 8 2 3 4 5 6 7 / / 22 10 19 3 1 2 5 6 15 2 key prev / 1 3 4 1 1 2 3 4 5 6 7 15 4 / 2 7 1 2 key 8 9 10 11 12 10 4 10 13 7 13 14 15 19 16 10 16 17 18 19 20 21 3 19 13 1 / 16 prev next Problem 6) Consider inserting the keys <22, 14, 10, 88, 44, 47, 50, 9, 31, 18 > into a hash table of length m = 9 using open addressing with auxiliary hash function h’(k) = k mod m. Illustrate the result of inserting these keys using linear and quadratic probing with c1= 1 and c2=5. Linear Probing: m 9 h(k) 0 1 2 3 4 5 6 7 8 9 10 Hash(k) Key 22 4 4 14 5 5 10 1 1 88 7 7 keys 44 8 8 47 2 2 50 5 5 6 9 0 0 31 4 4 5 6 7 8 0 1 2 3 0 9 1 10 2 47 3 31 4 22 5 14 6 50 7 88 8 44 18 0 0 1 2 3 4 5 6 7 8 Error Error 18 overflow Quadratic Probing: m c1 c2 Quadratic 9 1 5 h(k) 0 1 2 3 4 5 6 7 8 9 10 Hash(k) Key 22 4 4 14 5 5 10 1 1 88 7 7 keys 44 8 8 47 2 2 50 5 5 2 0 9 0 0 6 31 4 4 1 8 7 7 8 1 4 8 4 error 0 50 1 10 2 47 3 18 4 22 5 14 6 9 7 88 8 44 18 0 0 6 4 3 Problem 7) Demonstrate the insertion of keys <5, 10, 27, 38, 21, 16, 9, 4> into a hash table with collision resolution by chaining. Let the table have 11 slots, and let the hash function be h(k) = k mod 11. A 0 / 1 / 2 / 3 / 4 4 5 5 6 / 7 / 8 / 9 10 9 10 / 27 / 21 38 16 / Problem 8) For the set of keys < 2, 4, 1, 23, 17, 3, 10, 9>, show the binary search tree of height 3, 4, and 5. Height 3: 4 2 10 1 3 9 17 23 Height 4: 2 1 10 9 3 23 4 Height 5: 17 1 1 3 4 9 17 10 23