SDLC Security Assessment Methodology by Security Innovation
advertisement

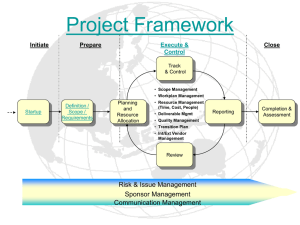
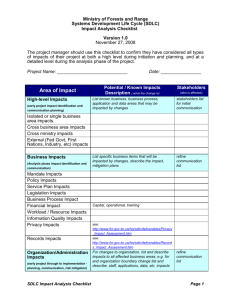
SDLC Process Assessment Methodology Identifying gaps and introducing key security activities SDLC Process Assessment Methodology 2 SDLC Assessment Overview Security Innovation’s Secure Software Development Life Cycle (SSDLC) program development service offering is built upon the widely-accepted five phases of the software development life cycle (SDLC): Requirements Design Implementation Test Deployment Our SDLC program assessment methodology consists of four phases: 1. 2. 3. 4. Assess Identify Evaluate and Plan Deploy Phase I: Assess Existing Process In the Assess Phase, our goal is to understand the software development standards and processes, including everything that is currently being done with respect to software security. Our assessments are based on security industry best practices drawn from a number of industry sources, including the ISO 27002, NIST-800, ITIL frameworks, the Microsoft SDL1, as well as SI’s own extensive database of customer secure development lifecycle engagements. We will assess: Security training program Security policies Organizational capabilities related to security Requirements and design phase security activities including security requirements objectives, threat modeling, design best practices and security design reviews Implementation phase security activities including development best practices and security code reviews Verification phase security activities including abuse case definition, threat modeling for penetration testing, and penetration testing Release and response phase security activities and preparedness including deployment best practices, security deployment review and security attack response and patching processes. In each area we will understand the state of your development processes and policies and determine the gap between what you are doing now and industry best practices in each area. 1 Security Innovation is an approved Microsoft SDL Partner SDLC Process Assessment Methodology 3 Phase II: Identify Objectives & Gaps The Identify Phase is a goal setting exercise in which we work with you to set appropriate goals to bring your security development processes to the next level. In each area we will examine the gaps between what you do and industry best practices, we will examine the technical and business risks associated with each gap, and help you set goals that will maximize your ROI while minimizing your risk. The result of this phase is a customized set of goals that we’ll use to create a remediation plan for improving your security development policies and processes. Phase III: Plan the Remediation Roadmap In the Evaluate and Plan Phase we use your goals and key risks to analyze the results of our gap analysis and prioritize the areas most in need of augmentation based on practical and proven IT risk and cost/benefit considerations. This phase also incorporates a stakeholder strategy and planning workshop session designed to review the major software risk management strategies (avoid, transfer, accept, remediate) and attach the appropriate control options to each identified threat or risk category. The final step of the Strategy phase is the creation of a software risk remediation roadmap, which in the Deploy Phase becomes the basis of specific subsequent security improvement initiatives. Examples of security components of an SDLC improvement review include software security requirements gathering, conducting the secure code design reviews, performing system design, threat and attack modeling, evaluating training levels in secure coding best practices, security testing staff assessments, secure application deployment techniques and secure software maintenance best practices. Phase IV: Implement the Remediation Roadmap In the Deploy Phase we work with you to implement the remediation roadmap. Most of these services are not priced into this project but could constitute a follow up project based upon our findings and your determination of where you need the most help. Available deploy phase options from Security Innovation include: eLearning training courses covering security design, development and testing best practices Instructor led training courses covering security design, development and testing best practices Static analysis automated code review tool deployment Attack surface analysis tool deployment Fault injection tool deployment Security best practices knowledge base and information repository Expert-led design review, threat model, code review or penetration test SDLC Process Assessment Methodology 4 Security Innovation Training Services Security Innovation has trained dozens of Fortune 1000 companies including Motorola, ING, SAP, Symantec, McAfee, Liberty Mutual, HP, FedEx, Microsoft, IBM, & Visa. Our foundation testing course “How to Break Software Security” is required reading and part of the Computer Science curriculum at more than 40 universities in the US. The Security Innovation course curriculum spans almost 25 specialized software security courses that map directly to a phase of the Software Development Lifecycle: Secure Software Design, Secure Coding and Security Testing. Security Innovation is uniquely positioned to help organizations evolve technical training curriculums to incorporate multiple training delivery technologies and methodologies – including instructor led training, e-Learning modules, and customized course offerings. Security Innovation Specialized Security Tools TeamMentor TeamMentor is a unique knowledgebase of secure development content which offers security guidance for technical teams, available on demand in an easy to use, searchable interface. TeamMentor can be licensed in multiple deployment scenarios, supporting organizations looking to build and incorporate an internal collection of resources which supports the availability of SSDLC content, guidelines and application security project notes which add more focused guidance on secure development frameworks. TeamMentor has been integrated to support predefined standards such as: Microsoft SDL Framework Standard Frameworks such as NIST, ISO, ITIL, etc. Custom SDLC Frameworks OWASP Risk Management and Risk Assessment Frameworks Checkmarx CxSuite Security Innovation has conducted thorough hands-on reviews of leading static analysis code review tools, concluding that Checkmarx CxSuite is one of the most advanced source code products available on the market today. Using analysis tools is an important part of the secure development process, and leads to the effective management of the software risk management and security review process. CxSuite is one of the fastest and most reliable tools that developers can use to create and update secure code quickly and accurately – especially for .NET and J2EE environments. False positive rates are extremely low because the entire code path, from presentation back to root cause, is verified before it is reported as a defect. “Out of the box” queries are predefined and available to allow developers to cover a wide range of known vulnerability checks with virtually zero false positives.