advance cryptography ch 2
advertisement

Chapter 2
Mathematics
M
th
ti off
Cryptography
Part I: Modular Arithmetic, Congruence,
and Matrices
2.1
2.2.5 Continue
P35 Additive Inverse
In Zn, two numbers a and b are additive inverses of each
other if
Note
In modular arithmetic
arithmetic, each integer has
an additive inverse. The sum of an
integer and its additive inverse is
g
to 0 modulo n.
congruent
2.2
2.2.5 Continued
P35 Example 2.21
Find all additive inverse pairs in Z10.
Solution
The six pairs of additive inverses are (0, 0), (1, 9), (2, 8),
(3 7),
(3,
7) (4,
(4 6),
6) and (5,
(5 5).
5)
2.3
2.2.5 Continue
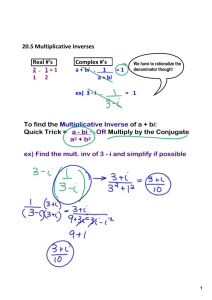
P36 Multiplicative Inverse
In Zn, two numbers a and b are the multiplicative
inverse of each other if
Note
In modular arithmetic, an integer may or
may not have a multiplicative inverse
inverse.
When it does, the product of the integer
and its multiplicative inverse is congruent
to 1 modulo n
n.
2.4
2.2.5 Continued
P36 Example 2.22
Find
i d the
h multiplicative
l i li i inverse
i
off 8 in
i Z10.
Solution
Th
There
i no multiplicative
is
lti li ti inverse
i
b
because
gcd
d (10
10,, 8) = 2 ≠ 1.
In other words, we cannot find any number between 0 and 9
such that when multiplied by 8, the result is congruent to 1.
P36 Example 2.23
Find all multiplicative inverses in Z10.
Solution
There are only three pairs: (1, 1), (3, 7) and (9, 9). The
numbers 0, 2, 4, 5, 6, and 8 do not have a multiplicative
2.5 inverse.
2.2.5 Continued
P36 Example 2.24
Fi d all
Find
ll multiplicative
lti li ti inverse
i
pairs
i in
i Z11.
Solution
We have seven pairs:
pairs: (1, 1), (2, 6), (3, 4), (5, 9), (7, 8), and (10,
10,
10)).
10
2.6
2.2.5 Continued
Note
The extended Euclidean algorithm finds
f
the
p
inverses of b in Zn
multiplicative
when n and b are given and
gcd (n
(n, b) = 1.
1
The multiplicative inverse of b is the value
of t after being mapped to Zn.
2.7
2.2.5 Continued
Figure 2.15
2 15 Using extended Euclidean
algorithm to find multiplicative inverse
2.8
2.2.5 Continued
P37 Example 2.25
Find the multiplicative inverse of 11 in Z26.
Solution
The gcd (26
26,, 11
11)) is 1; the inverse of 11 is 7 or 19
19..
2.9
2.2.5 Continued
P38 Example 2.26
Find the multiplicative inverse of 23 in Z100.
Solution
The gcd (100
100,, 23
23)) is 1; the inverse of 23 is 13 or 87
87..
2.10
2.2.5 Continued
P38 Example 2.27
Find the inverse of 12 in Z26.
Solution
The gcd (26,
26, 12
12)) is 2; the inverse does not exist.
exist.
2.11
2.2.6 Addition and Multiplication Tables
P39 Figure 2.16 Addition and multiplication table for Z10
2.12
2.2.7 Different Sets
Figure 2.17 Some Zn and Zn* sets
N
Note
We need to use Zn when additive
inverses are needed; we need to use Zn*
when multiplicative inverses are needed.
needed
2.13
2.2.8 Two More Sets
Cryptography often uses two more sets:
Zp and Zp*.
The modulus in these two sets is a prime
number.
2.14
2.3.2 Continued
P42 Example 2. 29
It shows the product of a row matrix (1 × 3) by a
column
l
matrix
i (3 × 1).
1) The
Th result
l is
i a matrix
i off
size 1 × 1. Figure 2.21 Multiplication of a row matrix by a column matrix
2.15
2.3.2 Continued
P42 Example 2. 30
It shows the product of a 2 × 3 matrix by a
3 × 4 matrix. The result is a 2 × 4 matrix.
Figure 2.22 Multiplication of a 2 × 3 matrix by a 3 × 4 matrix
2.16
2.3.3 Determinant
The determinant
Th
d
i
off a square matrix
i A off size
i m×
m denoted as det (A) is a scalar calculated
recursively as shown below:
Note
The determinant is defined only for a
square matrix.
ti
2.17
2.3.3 Continued
Example 2. 32
Figure 2.24 shows how we can calculate the
determinant of a 2 × 2 matrix based on the
determinant of a 1 × 1 matrix
matrix..
Figure 2.24 Calculating the determinant of a 2 ´ 2 matrix
2.18
2.3.3 Continued
Example 2. 33
Figure 2.25 shows the calculation of the determinant
of a 3 × 3 matrix
matrix..
Figure 2.25 Calculating the determinant of a 3 ´ 3 matrix
2.19
2.3.4 Inverses
Note
Multiplicative inverses are only defined
for square matrices
matrices.
2.20
2.3.5 Residue Matrices
Cryptography uses residue matrices:
matrices where all elements are in Zn. A
residue
id matrix
t i has
h a multiplicative
lti li ti inverse
i
if
gcd (det(A), n) = 1.
Example 2. 34
Figure 2.26 A residue matrix and its multiplicative inverse
2.21
4-2 GF(2
( n) FIELDS
In cryptography,
cryptography we often need to use four operations
(addition, subtraction, multiplication, and division). In
other words,
words we need to use fields.
fields We can work in
GF(2n) and uses a set of 2n elements. The elements in
this set are n-bit
n bit words.
words
Topics discussed in this section:
4.2.1 Polynomials
4.2.2 Using A Generator
4 2 3 Summary
4.2.3
S
4.22
4.2
Continued
P108 Example 4.14
Lett us define
L
d fi a GF(22) field
fi ld in
i which
hi h the
th sett has
h four
f
2 bit
2-bit
words: {00, 01, 10, 11}. We can redefine addition and
multiplication for this field in such a way that all properties
of these operations are satisfied,
satisfied as shown in Figure 4.8.
48
4.23
4.2
Continued
Figure 4.8 An example of GF(22) field
4.24
4.2.1
Polynomials
A polynomial of degree n − 1 is an expression of
th form
the
f
where xi is called the ith term and ai is called coefficient of
the ith term.
4.25
4.2.1
Continued
P109Example 4.15
Figure 4.9 show how we can represent the 8
8-bit
bit
word (10011001) using a polynomials.
Figure 4.9 Representation of an 8-bit word by a polynomial
4.26
4.2.1
Continued
P109 Example 4.16
To find the 8-bit
8 bit word related to the polynomial x5
+ x2 + x, we first supply the omitted terms. Since n
= 8, it means the polynomial is of degree 7. The
expanded polynomial is
This is related to the 8-bit word 00100110.
4.27
4.2.1 Continued
GF(2n) Fields
Note
Polynomials
y
representing
p
g n-bit words use
two fields: GF(2) and GF(2n).
4.28
4.2.1 Continued
Modulus
For the sets of polynomials in GF(2n), a group of
polynomials of degree n is defined as the modulus.
polynomials
y
are referred to as irreducible
Such p
polynomials.
Table 4.9 List of irreducible polynomials
4.29
4.2.1 Continued
Addition
Note
Addition and subtraction operations on
polynomials are the same operation.
4.30
4.2.1
Continued
P110Example 4.17
Lett us do
L
d (x
( 5 + x2 + x)) (x
( 3 + x2 + 1) in
i GF(28).
) We
W
use the symbol to show that we mean polynomial
addition. The following shows the procedure:
4.31
4.2.1
Continued
P110Example
P110E
l 4.18
4 18
There is also another short cut. Because the
addition in GF(2) means the exclusive-or (XOR)
operation.
p
So we can exclusive-or the two words,,
bits by bits, to get the result. In the previous
example,
l
x5 + x2 + x is 00100110
x3 + x2 + 1 is 00001101.
The result is 00101011 or in polynomial notation
x5 + x3 + x + 1.
1
4.32
4.2.1 Continued
Multliplication
1 The
1.
Th coefficient
ffi i t multiplication
lti li ti
i done
is
d
i
in
GF(2).
( )
2. The multiplying xi by xj results in xi+j.
3 The multiplication may create terms with
3.
degree more than n − 1, which means the
result needs to be reduced using a modulus
polynomial.
polynomial
4.33
4.2.1
Continued
P111 Example
E
l 4.19
4 19
Find the result of (x5 + x2 + x)
x) in GF(28)
(x7 + x4 + x3 + x2 +
with irreducible polynomial (x8 + x4 + x3 + x + 1).
Note that we use the symbol
to show the
multiplication of two polynomials.
4.34
4.2.1
Continued
P111 Example
E
l 4.19
4 19
Solution
To find the final result,, divide the p
polynomial
y
of
degree 12 by the polynomial of degree 8 (the
modulus) and keep only the remainder. Figure
4 10 shows the process of division.
4.10
division
4.35
4.2.1
Continued
Figure 4.10
4 10 Polynomial division with coefficients in GF(2)
4.36
2.1.4 Continued
Figure
g
2.8.b Extended Euclidean algorithm,
g
part
p b
4.37
4.2.1 Continued
P112 Example 4.20
In GF (24), find the inverse of (x2 + 1) modulo (x4
+ x + 1).
Solution
The answer is (x3 + x + 1) as shown in Table 4.5.
T bl 4.5
Table
4 5 Euclidean
E lid
algorithm
l ith for
f Exercise
E
i 4.20
4 20
4.38
4.2.1 Continued
P112Example 4.21
In GF(28), find the inverse of (x5) modulo (x8 + x4 +
x3 + x + 1).
Solution
The answer is ((x5 + x4 + x3 + x)) as shown in Table 4.6.
Table 4.6 Euclidean algorithm for Exercise 4.21
4.39